A service-linked role is a RAM role whose trusted entity is an Alibaba Cloud service. Service-linked roles can implement authorized access across Alibaba Cloud services. If you want to use Hologres to access MaxCompute, you must create the service-linked role AliyunServiceRoleForHologresIdentityMgmt. This topic describes how to create the service-linked role AliyunServiceRoleForHologresIdentityMgmt and grant permissions to the service-linked role. This topic also describes how to view and delete the service-linked role.
For more information, see Service-linked roles.
Introduction to AliyunServiceRoleForHologresIdentityMgmt
Description
Service name: identity.hologres.aliyuncs.com.
Role name: AliyunServiceRoleForHologresIdentityMgmt.
Role description: Hologres uses the service-linked role to access your resources in MaxCompute.
Create the service-linked role AliyunServiceRoleForHologresIdentityMgmt and grant permissions to the role
You can use one of the following methods to create the service-linked role AliyunServiceRoleForHologresIdentityMgmt and grant permissions to the role:
If you want to use a RAM user to create the service-linked role AliyunServiceRoleForHologresIdentityMgmt, you must grant the CreateServiceLinkedRole permission to the RAM user. For more information, see the "Permissions required to create and delete a service-linked role" section in Service-linked roles.
New instances
On the Hologres instance buy page, click Create Service-linked Role and grant permissions to the service-linked role.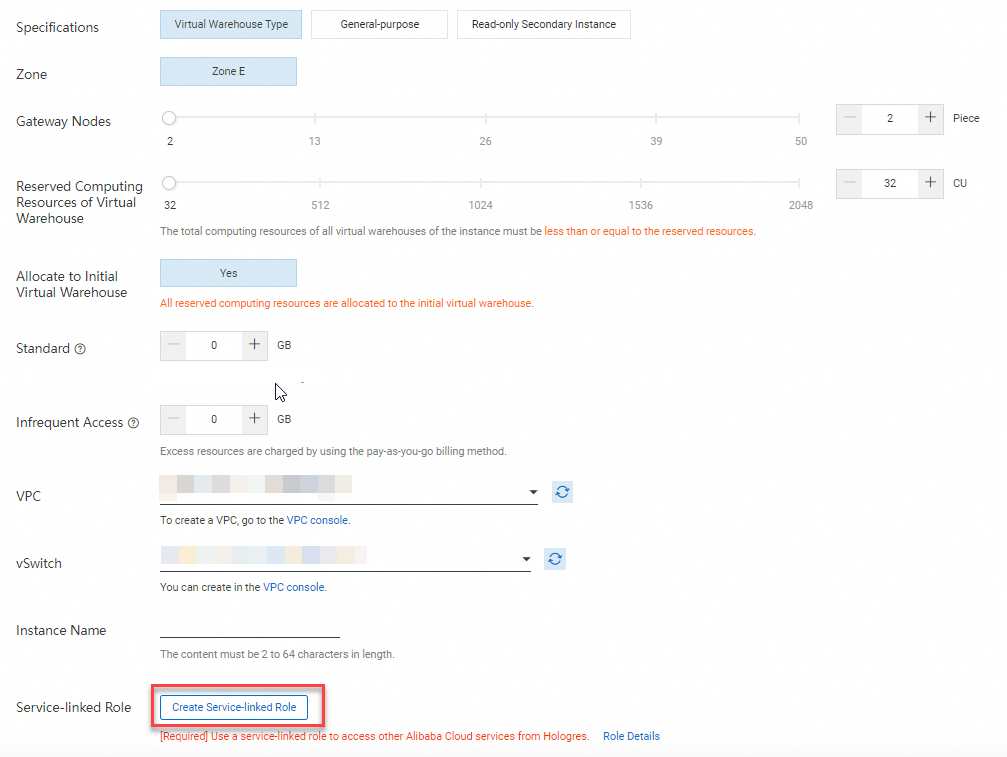
Existing instances
If you do not need to purchase an instance or upgrade an instance, you can go to the RAM Quick Authorization page or call an API operation to create the service-linked role and grant permissions to the role.
Log on to the Hologres console and go to the RAM Quick Authorization page to grant permissions to the service-linked role.
Call an API operation.
Log on to OpenAPI Portal.
On the Parameters tab, set ServiceName to identity.hologres.aliyuncs.com.
Click Initiate Call.
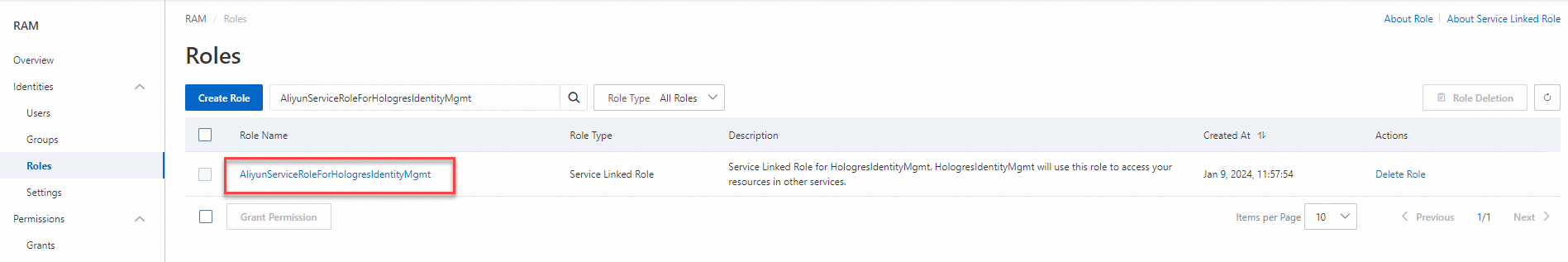
After the API operation is successfully called, you can view the service-linked role in the Resource Access Management (RAM) console.
View permissions
You can perform the following steps to view the permissions of the created service-linked role AliyunServiceRoleForHologresIdentityMgmt.
Log on to the RAM console by using your Alibaba Cloud account or as a RAM user that has administrative permissions.
In the left-side navigation pane, choose Identities > Roles.
On the Roles page, search for AliyunServiceRoleForHologresIdentityMgmt and click the name of the role.
On the Permissions tab, click the policy that is displayed.
On the Policy Document tab, view details of the policy.
NoteYou can only view the policy for the service-linked role AliyunServiceRoleForHologresIdentityMgmt. You cannot modify the policy.
Delete the service-linked role
To prohibit Hologres from accessing MaxCompute, you can delete the service-linked role AliyunServiceRoleForHologresIdentityMgmt in the RAM console. For more information, see Delete a RAM role.
When you delete the service-linked role AliyunServiceRoleForHologresIdentityMgmt, the permissions that are granted to the service-linked role are also revoked.
If you want to use a RAM user to delete the service-linked role, you must grant the DeleteServiceLinkedRole permission to the RAM user. For more information, see the "Permissions required to create and delete a service-linked role" section in Service-linked roles.
FAQ
Question 1: When I click Create Service-linked Role on the Hologres instance buy page, the following message is displayed: "The user does not have the permissions to create service-linked roles. Contact the Alibaba Cloud account or the permission administrator to authorize the user." What do I do?
Solution: Use your Alibaba Cloud account to grant the CreateServiceLinkedRole permission to the RAM user. For more information, see Service-linked roles.
Question 2: When I access MaxCompute foreign tables in Hologres, one of the following error messages is displayed. What do I do?
Error message 1:
ERROR: Fail to access foreign data as user 1063806044629636, AliyunServiceRoleForHologresIdentityMgmt does not exist.Error message 2:
ErrorMessage=ODPS-0420095: Access Denied - Authorization Failed [4111], You have NO privilege \'odps:ActOnBehalfOfAnotherUser\' on {acs:odps:regions_id:xxxxxx:users/default/aliyun/xxxxxx. Not pass by ram permission check.
Solution: Grant permissions to the service-linked role AliyunServiceRoleForHologresIdentityMgmt again. You can follow the steps of granting permissions for existing instances in the Hologres console in Create the service-linked role AliyunServiceRoleForHologresIdentityMgmt and grant permissions to the role of this topic.