If you want to use HTTP/2 to improve the performance of an HTTPS service that is configured with a Global Accelerator (GA) instance, you can configure HTTP/2 for the GA instance. After you enable HTTP/2, the HTTPS service can benefit from the advantages of HTTP/2 to greatly improve service performance, reduce network latency and overheads, and improve access experience.
What is HTTP/2
HTTP/2 connection negotiation
During the negotiation process of an HTTPS connection, a TLS connection must be established between the client and server before application data can be transmitted. HTTP/2 uses the Application-Layer Protocol Negotiation (ALPN) mechanism to allow the client and server to negotiate on which protocol version to use.
After you enable HTTP/2 for a Global Accelerator instance, the Global Accelerator instance specifies h2 as the protocol version in the ALPN fields of the ClientHello message sent by the client. In addition, the GA instance ignores the protocol version in the ALPN fields of the ServerHello message returned by the server and forcefully uses HTTP/2 to connect to backend services.
Examples
The following scenario is an example. An enterprise headquartered in the US (Silicon Valley) region deploys an HTTPS website on an Elastic Compute Service (ECS) instance in a virtual private cloud (VPC). Most users of the application access the application from the China (Hong Kong) region. The enterprise has purchased a Global Accelerator instance to address network issues, such as network latency, network jitter, and packet loss, that may occur due to the unstable cross-border network.
To further improve the website performance and optimize access to the website, the enterprise decides to configure HTTP/2 listeners for the GA instance.
If the backend service of the Global Accelerator instance uses HTTPS, HTTP/1.1 is used to connect to backend services. In this case, the enterprise needs to modify the configurations of the Global Accelerator instance to use HTTP/2 to connect to backend services. This way, the enterprise can benefit from the advantages of HTTP/2 in performance optimization.

Limits
When you configure HTTP/2 for a GA instance, the following limits apply:
By default, the protocol version selection feature is disabled. To use this feature, contact your account manager.
The WebSocket protocol is not supported.
The Server Push feature in the HTTP/2 protocol is not supported.
gRPC requests based on HTTP/2 cannot be accelerated.
Prerequisites
A server certificate is purchased or uploaded in the Certificate Management Service console. For more information, see Purchase an official certificate and Upload, sync, and share SSL certificates.
The certificate is uploaded to the backend servers. For more information, see Use Cloud Assistant to upload a file to ECS instances.
An HTTPS service that uses port 443 is deployed and HTTP/2 is enabled.
Make sure that the security groups to which the backend servers belong allow access to TCP port 443. For more information, see Add a security group rule.
A Global Accelerator instance is created. The ECS instance on which the NGINX service is deployed is specified as an endpoint of the GA instance. The backend service protocol is set to HTTPS. For more information, see Create and manage Standard Global Accelerator instances.
The domain name associated with the certificate is mapped to the CNAME that is allocated by Global Accelerator. For more information, see Add a CNAME record for a domain name.
Configure HTTP/2
This section describes only the key parameters. For more information about other endpoint group parameters, see Add and manage endpoint groups for intelligent routing listeners.
Log on to the GA console.
On the Instances page, find the GA instance and click Modify Listener in the Actions column.
On the Listeners tab, find the listener that you want to manage and click Edit Endpoint Group in the Actions column.
In the Configure Listener & Protocol step, click Next.
In the Configure Endpoint Group step, select HTTP/2 for Protocol Version and click Next.

In the Confirm step, check the configurations and click Submit.
Verification
Before and after you set the protocol version to HTTP/2 in the endpoint group configurations, you can perform the following steps to check whether HTTP/2 takes effect:
Open a browser on a client in the China (Hong Kong) region and type
https://<Accelerated domain name>. Then, press Enter to check whether the backend service can be accessed.Log on to the backend server in the US (Silicon Valley) region. Open the CLI and run the following command to view the record of the most recent visit.
You can view the protocol version used to send the request to the backend server in the details of the record.
tail -n 1 /var/log/nginx/access.logThe following figure shows the record returned before the protocol version is set to HTTP/2.
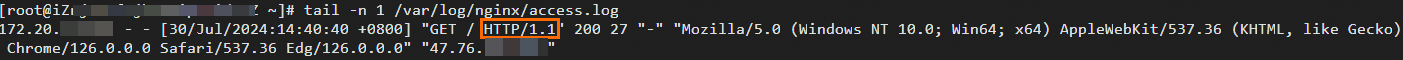 The following figure shows the record returned after the protocol version is set to HTTP/2.
The following figure shows the record returned after the protocol version is set to HTTP/2.
References
Tutorials
For more information about how to configure endpoint groups, see Add and manage endpoint groups for intelligent routing listeners.
To upgrade from HTTP to HTTP/3 to improve service quality and system performance, you can set the maximum HTTP version used by clients to HTTP/3. For more information, see Enable HTTP/3 for GA.
API references
CreateEndpointGroup: creates an endpoint group. You can use
EndpointProtocolVersionto specify the HTTP version used to connect to backend services.UpdateEndpointGroup: modifies an endpoint group. You can use
EndpointProtocolVersionto specify the HTTP version used to connect to backend services.DeleteEndpointGroup: deletes an endpoint group.