This topic describes how to enable Hive in Ranger and how to configure the related permissions.
Prerequisites
A DataLake cluster is created and the Ranger service is selected for the cluster. For more information about how to create a cluster, see Create a cluster.
Precautions
- Access methods that require permission verification
- Use the Beeline client to access HiveServer2.
- Use a Java Database Connectivity (JDBC) URL to access HiveServer2.
- Access methods that do not require permission verification
- Use the Hive client to access the Metastore service.
- Use the Hive client API to access the Metastore service.
Enable Hive in Ranger
- Go to the Services tab.
- Log on to the E-MapReduce (EMR) console. In the left-side navigation pane, click EMR on ECS.
- In the top navigation bar, select the region in which your cluster resides and select a resource group based on your business requirements.
- On the EMR on ECS page, find the desired cluster and click Services in the Actions column.
- Enable Hive in Ranger.
- On the Services tab of the page that appears, click Status in the Ranger-plugin section.
- In the Service Overview section of the Status tab, turn on enableHive.
- In the message that appears, click OK.
- Restart HiveServer.
- On the Services tab, click the
 icon and select Hive.
icon and select Hive. - In the Components section of the Status tab, find HiveServer and click Restart in the Actions column.
- In the dialog box that appears, configure the Execution Reason parameter and click OK.
- In the Confirm message, click OK.
- On the Services tab, click the
Configure permissions
Overview
Before you configure permissions in Ranger, you must access the web UI of Ranger. For more information about how to access the web UI of Ranger, see Overview.
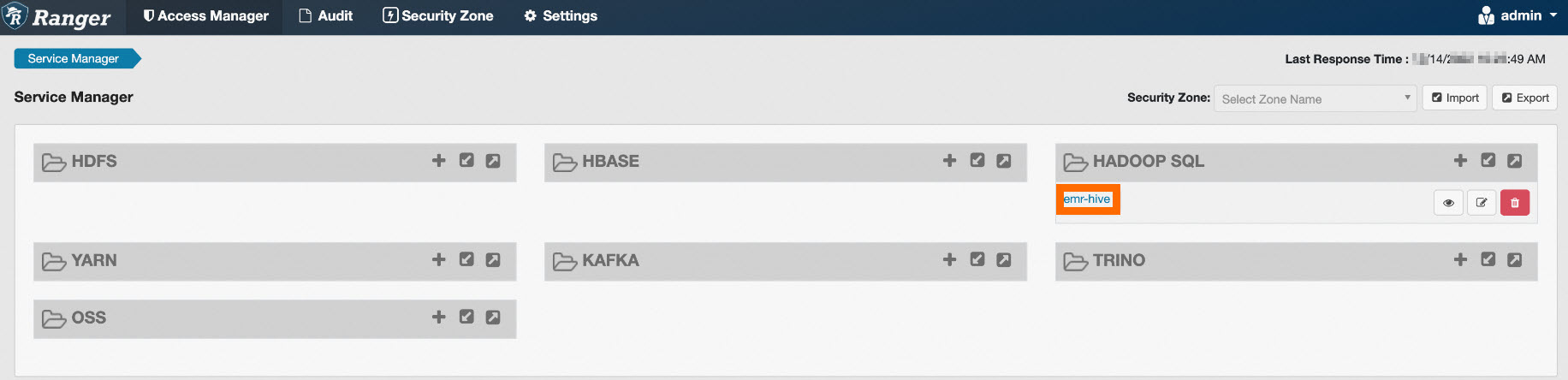
On the emr-hive page, you can view the list of all policies that are configured. Some default policies are configured in Ranger. For example, the hive user can start the HiveServer component and access all resources such as databases, tables, columns, user-defined functions (UDFs), and URLs. All users have the Create permission on databases, and all users to which the default database tables columns policy is attached have the Create permission.
Add a policy
- Policy Resource
The Hive plug-in of Ranger supports the following types of resources: databases, tables, columns, URLs, and UDFs. By default, the database, table, and column resources are displayed. You can click the name of a resource to change the resource.
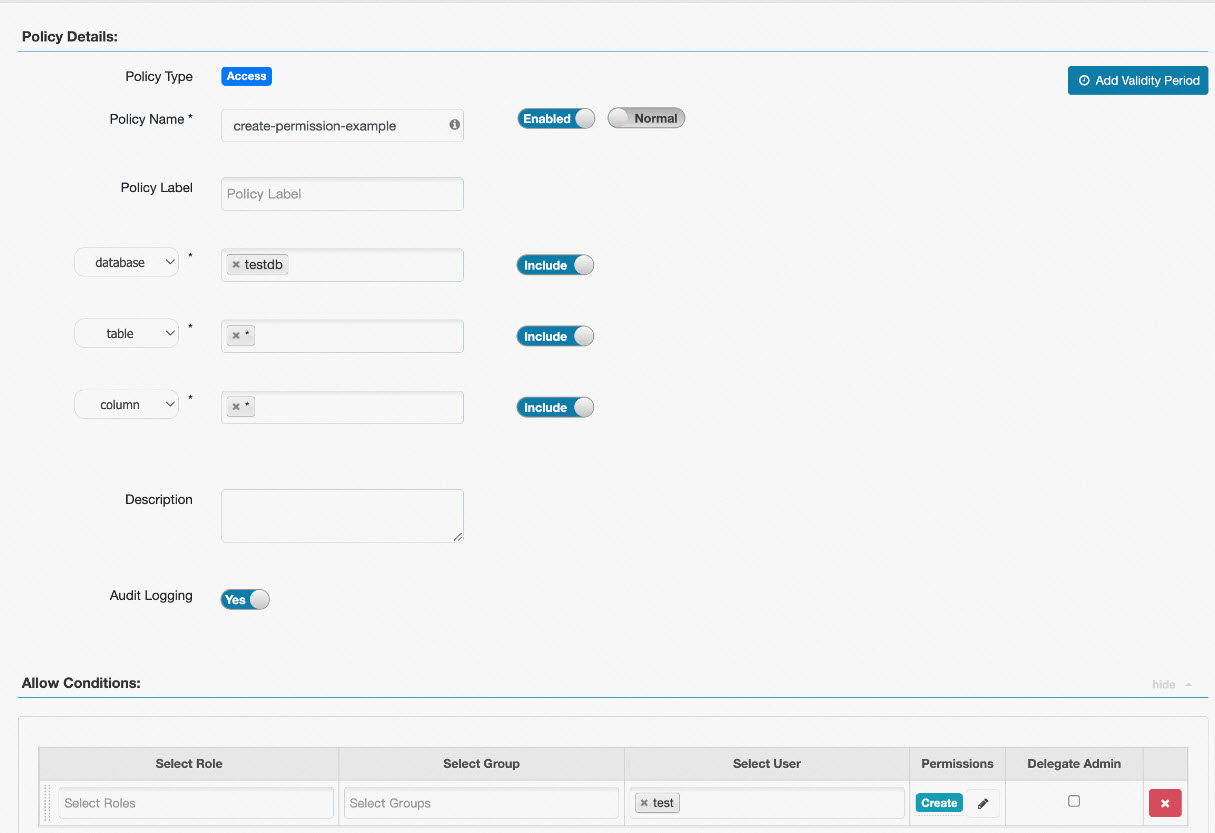
When you configure a policy, you must specify the name of a resource in the Resource field. For example, you can set the database parameter to testdb, the table parameter to test, the column parameter to id, and the url parameter to oss://test-bucket/test/tmp. You can also enter an asterisk (*) to specify all resources, as shown in the following figure.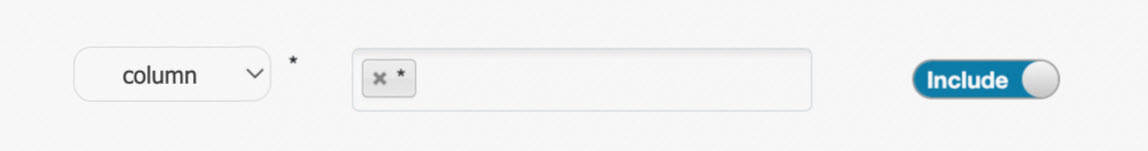
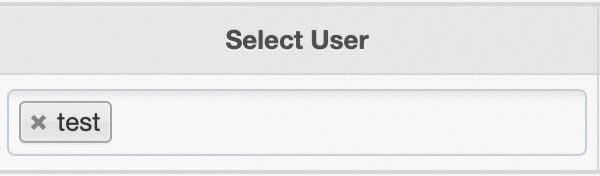
- Policy UserWhen you add a policy, you must select a user to which you want to attach the policy from the Select User list.
- Policy PermissionAfter you click Add Permissions, the add/edit permissions drop-down list appears. You can select permissions based on your business requirements.
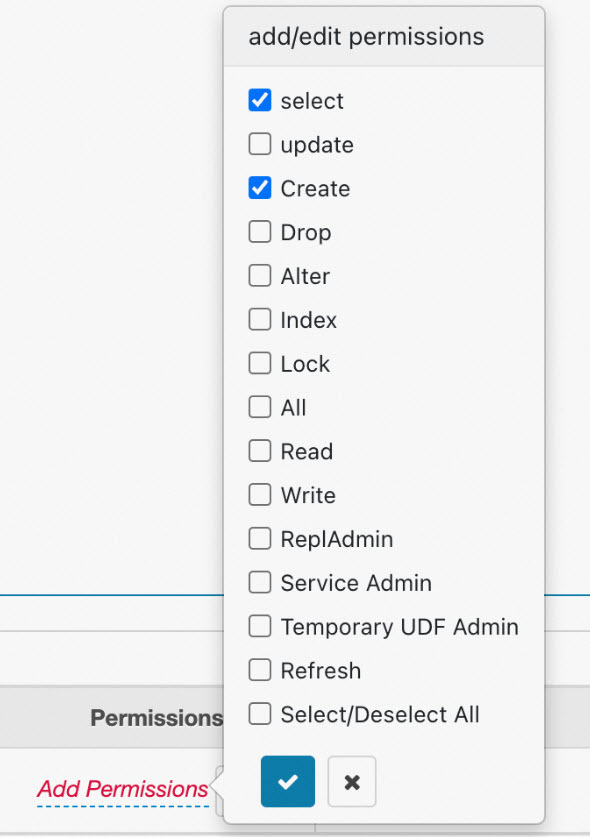
Example 1: Configure permissions on columns
select columns from table statement to query data. The following figure shows the configurations that are used to grant the Select permission to a specific user.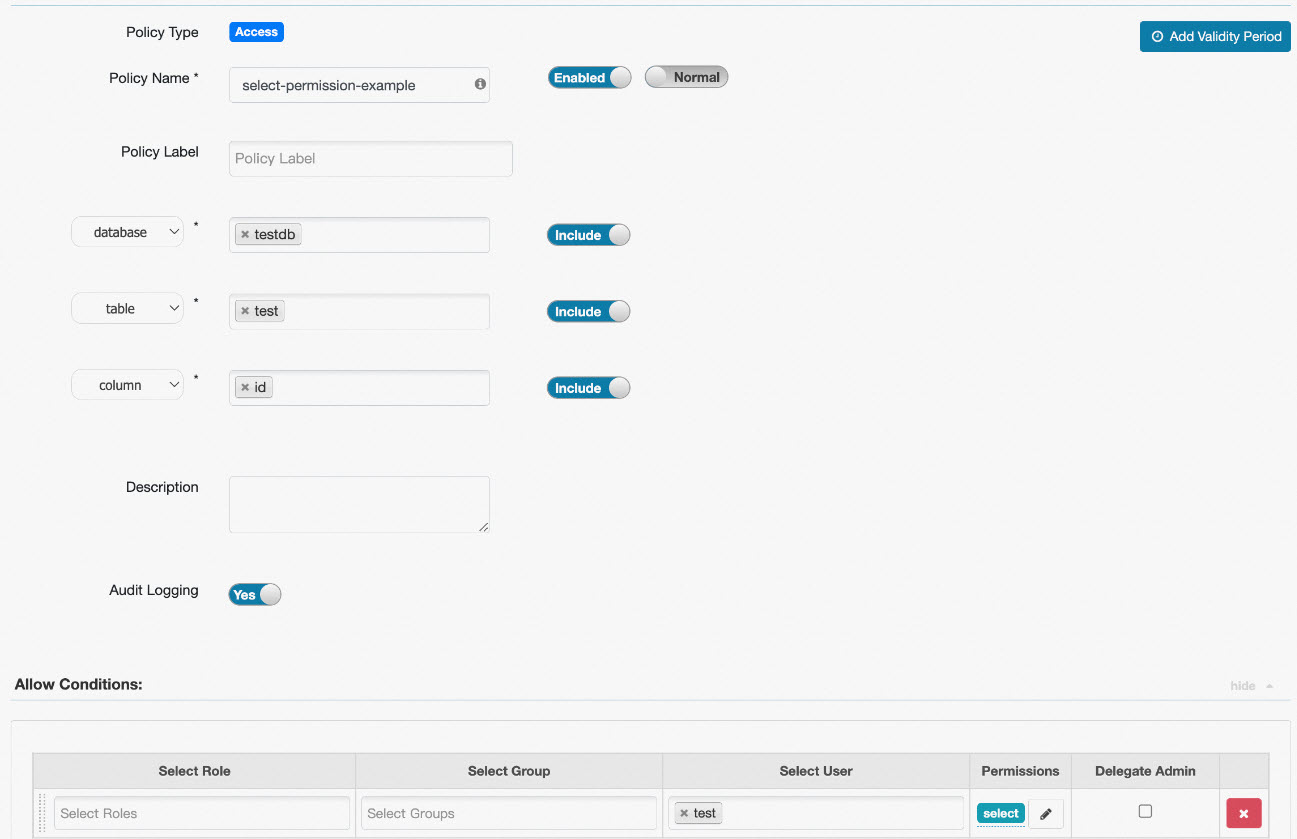
In this example, the user test is granted the select permission on the id column of the test table in the testdb database. This way, the user test can execute the select id from testdb.test statement to query data in the specified column. If you want the user to query data in all columns of the test table in the testdb database, you can set the column parameter to *. This way, the user test can execute the select * from testdb.test statement to query data in all columns.
Example 2: Configure permissions on tables
Example 3: Configure permissions on URLs
If the statement that you execute contains location information and the scheme of the location is oss, the system checks whether you have the Write and Read permissions on the location. For example, when you execute the create external table test(id int, name string) location 'oss://test-bucket/test' statement, the system checks whether you have the Write permission on oss://test-bucket/test.
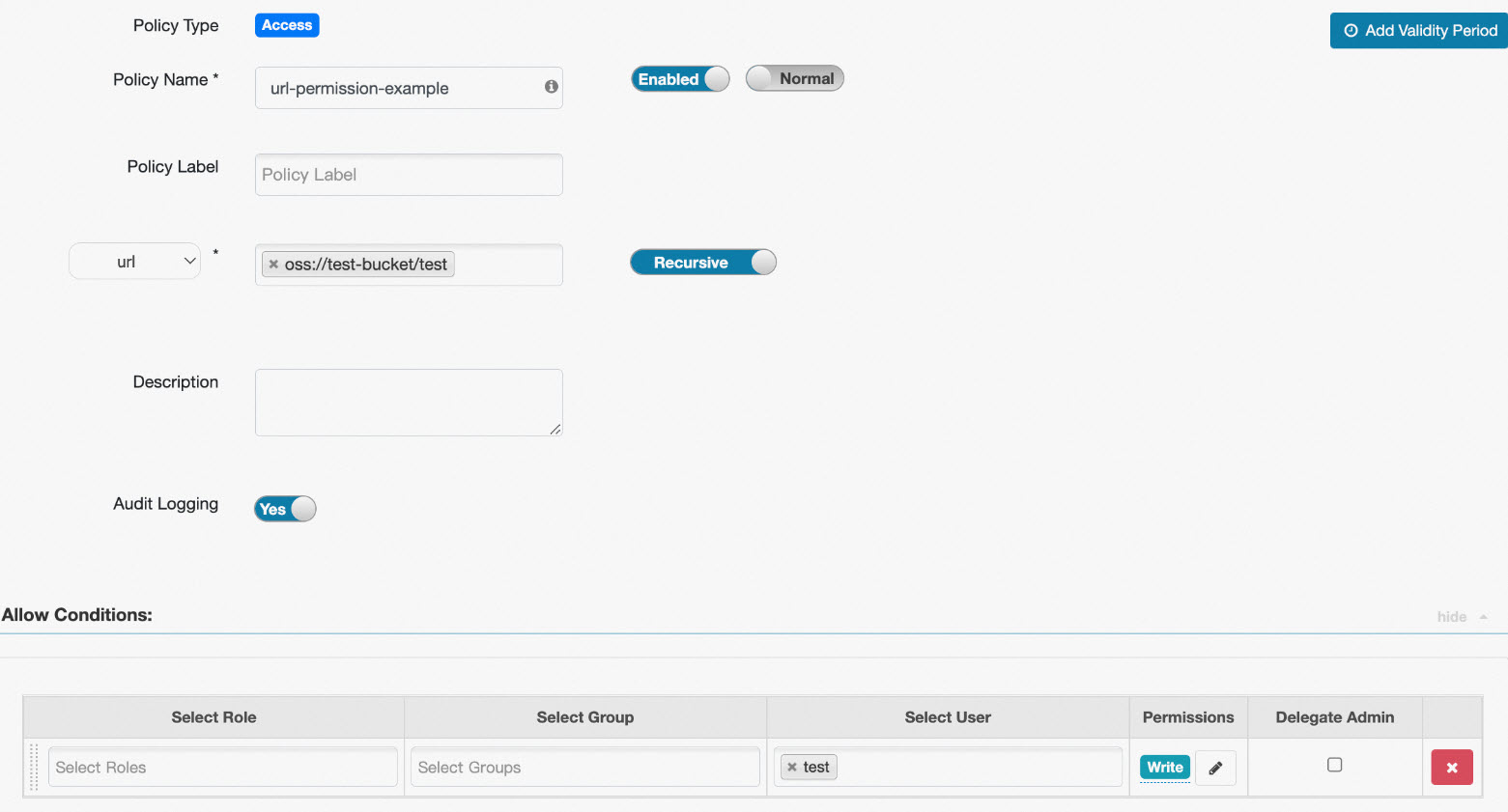
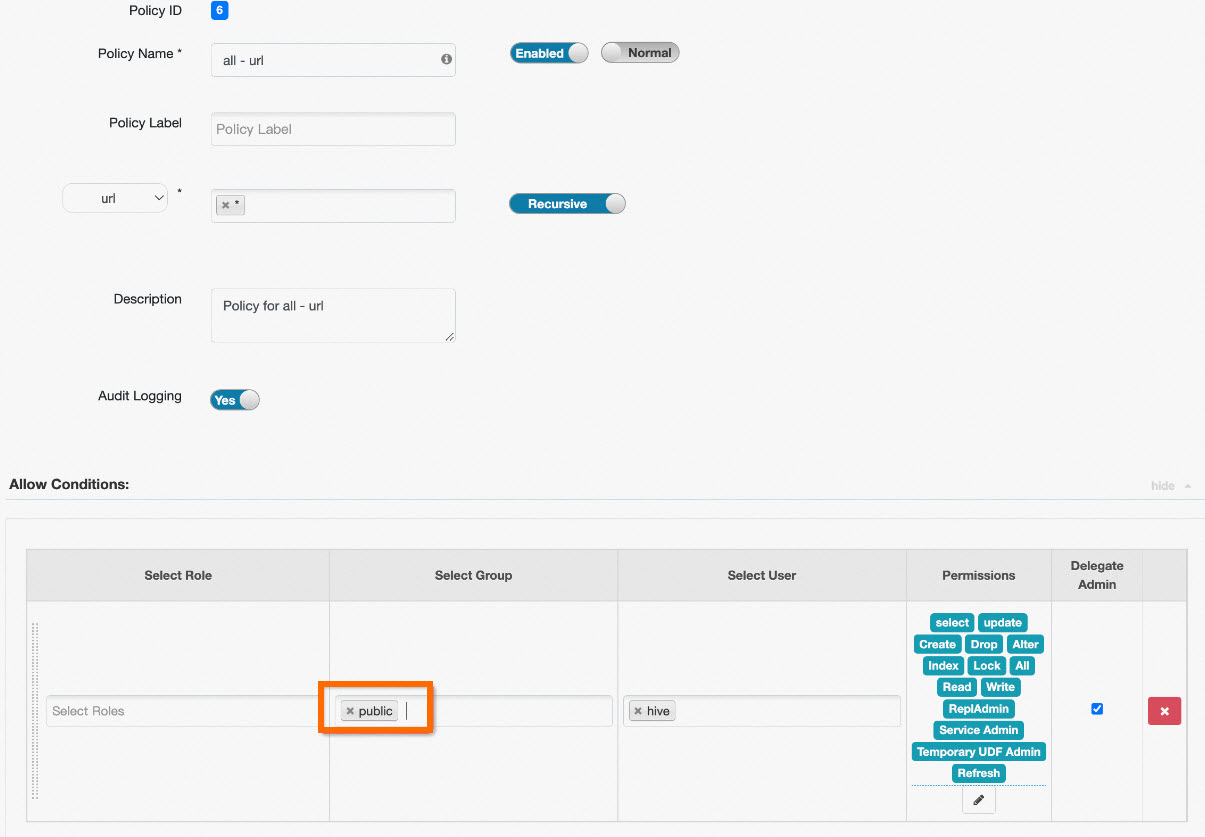
If you do not need to manage the permissions on URLs, you can set the Policy Name parameter to all - url and the Select Group parameter to public. This way, all users have the Read and Write permissions on all URLs. The following figure shows the configurations.