Integrate the ID Verification service into your application by selecting a product solution, testing APIs, following the integration guide, and configuring access permissions.
Prerequisites
Before you begin, make sure that you have:
An activated ID Verification service. For activation steps, see Activate ID Verification service
Step 1: Select a product solution
Review the available product solutions in What is ID Verification? and choose the one that fits your business requirements. Each solution targets a different verification scenario, so match your use case to the appropriate solution before you proceed.
Step 2: Debug and test APIs with OpenAPI Portal
OpenAPI Portal provides API debugging and code samples for all ID Verification APIs. Use it to test API calls and generate sample code for your server-side integration.
For detailed instructions, see Use OpenAPI to debug and integrate server-side APIs.
Each API reference page includes an Online debugging and integration section with direct links to the API debugging page and the code samples page for that specific API:
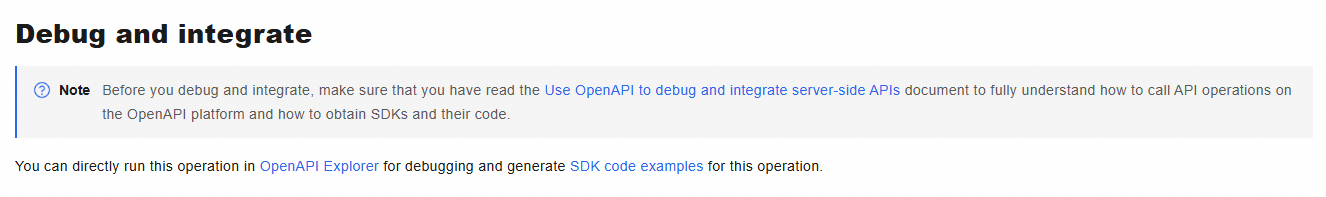
Step 3: Follow the integration guide
Based on the product solution you selected in Step 1, follow the integration instructions in the Developer Guide.
The directory page for each solution describes the available product features, integration methods, and supported regions:
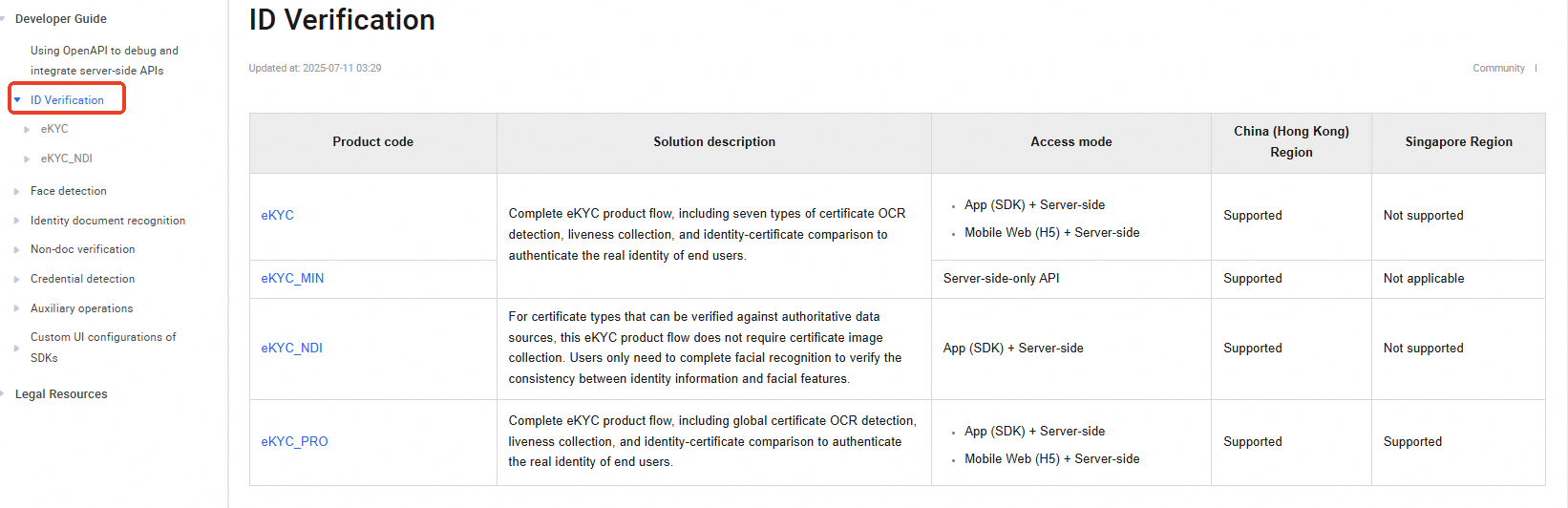
Step 4: Configure RAM user access
If multiple users share your Alibaba Cloud account, create Resource Access Management (RAM) users and assign each user only the permissions they need. For setup instructions, see Authorize RAM users to access the service.
An Alibaba Cloud account has full access and control permissions over all cloud products. If the account credentials are compromised, all resources face a significant security risk. Create RAM users and follow the principle of least privilege to minimize exposure.