Edge Security Acceleration (ESA) allows you to upload only certificates and private keys in the PEM format. The requirements for certificate upload vary with the certificate authority (CA).
Certificates issued by root CAs
Certificates issued by root CAs, such as Apache, IIS, NGINX, and Tomcat, are unique. ESA uses NGINX certificates, each of which contains a certificate file suffixed with .crt and a private key file suffixed with .key.
To view the content of a certificate, you can open the NGINX folder and use a text editor to open the .crt file. The following figure shows an example of certificate content.
Figure 1. Certificate in the PEM format 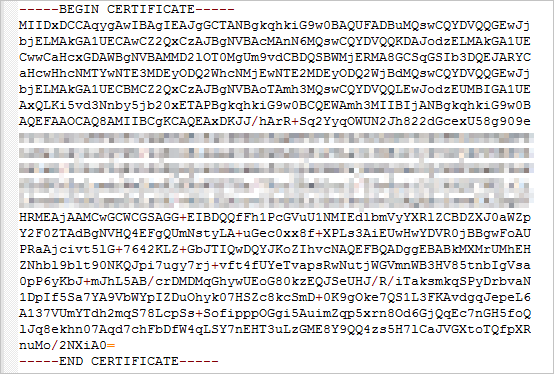
Requirements for certificate upload
You need to upload all content of the certificate that starts with "-----BEGIN CERTIFICATE-----" and ends with "-----END CERTIFICATE-----".
Each line contains 64 characters, except for the last line, which can contain fewer than 64 characters.
Certificates issued by intermediate CAs
A certificate file that is issued by an intermediate CA contains multiple certificates. When you configure HTTPS, you need to combine the intermediate certificates and server certificate into a complete certificate before you upload the certificate. The following figure shows an example of a complete certificate.
Figure 2. A complete certificate in the PEM format
Format of certificate chains
The certificates that are issued by an intermediate CA are in the following format:
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
Combination rules
Use a text editor to open all *.PEM certificate files. When you combine the certificates, the first certificate must be the server certificate and the intermediate certificates follow the server certificate. No empty lines are allowed between certificates. In most cases, the CA that issues the certificates may provide instructions. Take note of the instructions.
Formats of RSA private keys
The extension of a private key file is .pem or .key. To view the content of a private key, you can use a text editor to open the private key file. The following figure shows an example of a private key file.
Figure 3. Format of an RSA private key
Private key in the PEM format
The private key must start with "-----BEGIN RSA PRIVATE KEY-----" and end with "-----END RSA PRIVATE KEY-----".
Each line contains 64 characters, except for the last line, which can contain fewer than 64 characters.
Requirements for private key upload
Before you upload an RSA private key, run the openssl genrsa -out privateKey.pem 2048 command on your local PC to generate a private key. The privateKey.pem file is the private key file.
The private key must start with "-----BEGIN RSA PRIVATE KEY-----" and end with "-----END RSA PRIVATE KEY-----".
Each line contains 64 characters, except for the last line, which can contain fewer than 64 characters.
If the private key you obtain starts with "-----BEGIN PRIVATE KEY-----" and ends with "-----END PRIVATE KEY-----", run the following command in OpenSSL to convert the format. Then, upload the content of the new_server_key.pem file and the certificate.
openssl rsa -in old_server_key.pem -out new_server_key.pemConvert certificate formats
The HTTPS feature supports only PEM certificates. If your certificates are not in the PEM format, you must convert the certificate to PEM. We recommend that you use OpenSSL to convert certificate formats. The following section describes how to convert certificates to the PEM format.
The CRT file name extension is short for certificate. The certificate may be in the PEM or DER format. Before you convert the format of a certificate, check whether the conversion is necessary.
PEM is a text format. It starts with " -----BEGIN ***-----" and ends with "-----END ***-----". The content between these lines is Base64-encoded. Certificates and private keys can be saved in this format. To distinguish a certificate from a private key, the extension of a private key file that is in the PEM format is
.key.
Convert a certificate from DER to PEM
In most cases, the DER format is used for Java.
Convert the certificate format:
openssl x509 -inform der -in certificate.cer -out certificate.pemConvert the private key format:
openssl rsa -inform DER -outform pem -in privatekey.der -out privatekey.pem
Convert a certificate from P7B to PEM
In most cases, the P7B format is used for Windows Server and Tomcat.
Convert the certificate format:
openssl pkcs7 -print_certs -in incertificat.p7b -out outcertificate.cerOpen the
outcertificate.cerfile. Then, copy and upload the content that starts with "-----BEGIN CERTIFICATE-----" and ends with "-----END CERTIFICATE-----".Convert the private key format:
A certificate in the P7B format does not include a private key. When you configure a P7B certificate in the ESA console, you need to specify only the certificate information.
Convert a certificate from PFX to PEM
In most cases, the PFX format is used for Windows Server.
Convert the certificate format:
openssl pkcs12 -in certname.pfx -nokeys -out cert.pemConvert the private key format:
openssl pkcs12 -in certname.pfx -nocerts -out key.pem -nodes