Dynamic Content Delivery Network (DCDN) allows you to configure a whitelist to allow requests that have specific characteristics based on your business requirements. This way, the requests can bypass the checks of specific or all protection modules, such as basic protection rules and custom protection rules.
Prerequisites
Web Application Firewall (WAF) is enabled. For more information, see Getting started with WAF (new edition).
The domain name that you want to protect is added to WAF. For more information, see Add a domain name for protection.
Create a protection policy
Log on to the DCDN console.
In the left-side navigation pane, choose .
On the Protection Policies page, click Create Policy.
On the Create Policy page, configure the parameters. The following table describes the parameters.
Section
Parameter
Description
Policy Information
Policy Type
The type of the protection policy. Select Whitelist.
Policy Name
The name of the protection policy. The name can be up to 64 characters in length and can contain letters, digits, and underscores (_).
Make Default
Specifies whether the current policy is the default policy of the current policy type.
NoteYou can specify only one default policy for each policy type. After you specify a default policy, you cannot change the default policy.
If you have specified the default policy for the current policy type, this switch is unavailable.
Rule Information
Rule
The information about the current whitelist rule. For more information, see Whitelist rule parameters .
NoteYou can add up to 10 rules. To increase the quota, contact your account manager or contact us by other means. For more information, see Contact us.
Protected Domain Names
Select Association Mode
You can associate a protected domain name with multiple policies of the same type. If you have associated a domain name with a policy of the same type, you can add the current policy or replace the existing policy with the current policy. You can only replace the existing policy with the current policy for domain names that are associated with the default policy. Valid values:
Add and replace the original associated policy: disassociates the associated policy and replaces the policy with the current policy.
Add and keep the original associated policy: adds the current policy and retains the associated policy.
Protected Domain Names
The domain names that you want to associate with the current protection policy.
Click Create Policy.
By default, the protection policy that you created is enabled.
Whitelist rule parameters
You can create a whitelist rule when you create a whitelist. You can also create a whitelist rule for an existing whitelist. The following table describes the parameters.
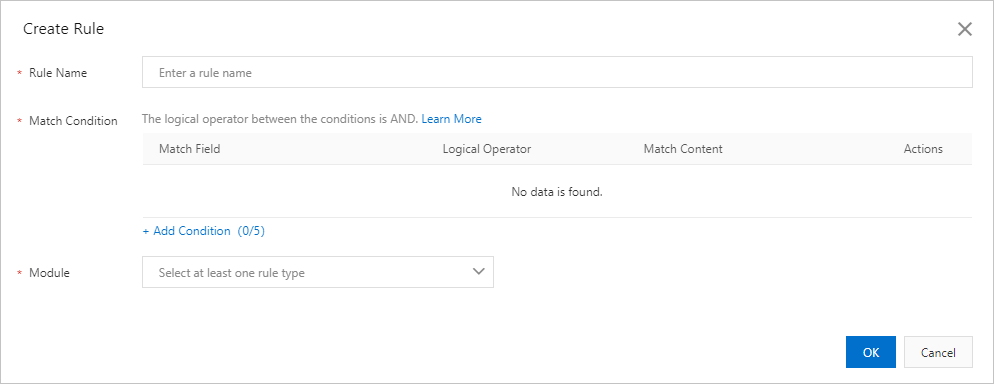
Parameter | Description |
Rule Name | The name of the rule. The name can be up to 64 characters in length and can contain letters, digits, and underscores (_). |
Match Condition | The request characteristics for matching. Click Add Condition to add a match condition. You can add up to five match conditions to a rule. If you add multiple match conditions, the rule is considered matched only if all match conditions are met. Each match condition consists of Match Field, Logical Operator, and Match Content. For information about examples on how to configure match conditions, see Match conditions. For information about match fields and logical operators, see Match conditions. |
Module | The protection modules that do not check requests that match the specified match conditions. Valid values:
|