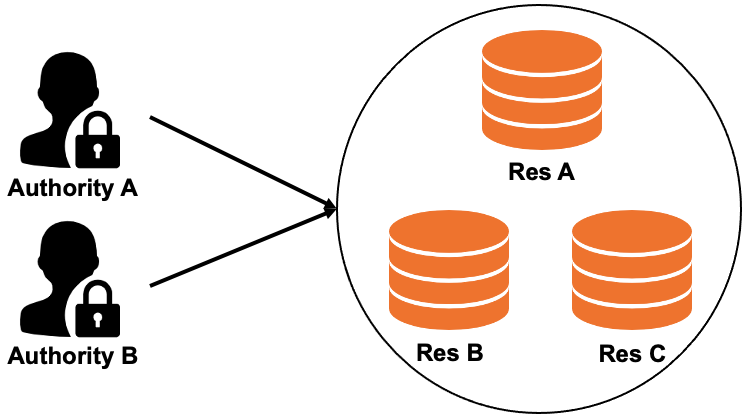
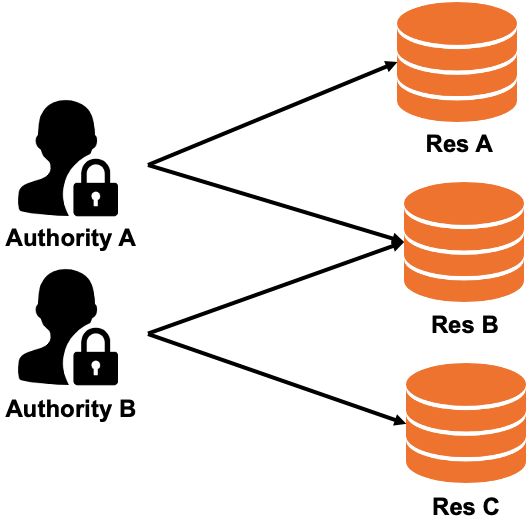
The applications that are managed in Enterprise Distributed Application Service (EDAS) may contain multiple services or subsystems, which can be developed and maintained by different teams and members. EDAS provides an enterprise-class permission management system. You can use the EDAS permission management system to isolate applications, resources, and data, and implement access control. This ensures the security of your applications.
EDAS-defined permissions and RAM policies
EDAS is developed with a permission management system, and also integrated with Resource Access Management (RAM).
For more information about how to use RAM to manage permissions, see Overview.
For more information about EDAS-defined permissions, see Manage EDAS-defined permissions (not recommended).
To manage permissions on Alibaba Cloud services including EDAS in the same system, we recommend that you use RAM. EDAS also allows you to replace EDAS-defined permissions with RAM policies. For more information, see Replace EDAS-defined permissions with RAM policies.
To manage the EDAS-defined permissions granted to a sub-account, log on to the EDAS console and specify the resources that the sub-account is allowed or not allowed to access. After you replace EDAS-defined permissions with RAM policies, you can no longer grant EDAS-defined permissions to sub-accounts. Sub-accounts are switched to RAM users. You must grant RAM users permissions on EDAS in the RAM console.
EDAS supports both EDAS-defined permissions and RAM policies. Sub-accounts and RAM users are managed by using the following rules:
Access of RAM users is controlled by RAM policies, instead of EDAS-defined permissions.
For sub-accounts:
Access of sub-accounts that are granted the AliyunEDASFullAccess permission is controlled by RAM policies, instead of EDAS-defined permissions.
We recommend that you switch sub-accounts that are regulated by EDAS-defined permissions to RAM users. For more information, see Replace EDAS-defined permissions with RAM policies. If you do not switch sub-accounts to RAM users, you can continue to use EDAS-defined permissions to control access of the sub-accounts.
Benefits of RAM
RAM is a resource access control service that is provided by Alibaba Cloud. You can use policies to control access of RAM users, such as employees, systems, or applications, and grant a RAM user specific permissions on a resource. For example, you can grant a RAM user read-only permissions on an EDAS application.
Finer-grained access control
EDAS-defined permission | RAM policy |
|
|
After an Alibaba Cloud account grants a sub-account permissions on a resource, operations on the resource are controlled by all the permissions. For example, if you grant a sub-account permissions on APP1 and APP2, and permissions to deploy and stop applications, the sub-account can deploy and stop APP1 and APP2. EDAS-defined permissions are coarser-grained than RAM policies. | RAM policies are finer-grained than EDAS-defined permissions. Each permission defines specific resources. For example, you can grant a RAM user permissions to deploy and stop applications. You can specify the resources that the RAM user is allowed to deploy as APP1 and APP2, and the resources that the RAM user is allowed to stop as APP2 and APP3. In this case, the RAM user can deploy only APP1 and APP2, but cannot deploy APP3. The RAM user can stop only APP2 and APP3, but cannot stop APP1. |
More types of syntax
RAM policies support more types of syntax than EDAS-defined permissions. For example, you can use wildcard characters in permission statements, and attach multiple policies to a RAM user to precisely regulate access control.
The following example shows the syntax of a RAM policy:
{
"Statement": [
{
"Action": [
"edas:ReadApplication"
],
"Effect": "Allow",
"Resource": ["acs:edas:*:*:namespace/*/application/*"]
},
{
"Action": [
"edas:ReadApplication"
],
"Effect": "Deny",
"Resource": ["acs:edas:cn-beijing:*:namespace/*/application/12345678"]
}
],
"Version": "1"
}The preceding policy contains two statements:
In the first statement, the effect is set to Allow, the action is set to edas:ReadApplication, which allows the RAM user to view applications, and the resource is set to a wildcard character (*), which specifies all applications. This statement specifies that the RAM user is allowed to view all EDAS applications.
In the second statement, the effect is set to Deny, and the resource is set to 12345678, which specifies the application whose ID is 12345678. This statement specifies that the RAM user is not allowed to view the application whose ID is 12345678.
Therefore, the policy that contains the preceding statements specifies that the RAM user is allowed to view all applications other than the application whose ID is 12345678.
You can also use conditional expressions to define a policy. For more information, see Policy overview.
Relationship between EDAS-defined permissions and RAM policies
EDAS-defined permissions are not equivalent to RAM policies. Therefore, you cannot directly change an EDAS-defined permission into a RAM policy. EDAS allows you to replace EDAS-defined permissions with RAM policies, which can inherit the EDAS-defined permissions in most cases. By default, the permissions that define whether a sub-account can perform a specific operation on EDAS resources such as applications and clusters are inherited by the RAM user to which the sub-account is switched.
Table 1. How EDAS-defined permissions and RAM policies are defined
EDAS-defined permission | RAM policy | Resource defined in a RAM policy |
Super Admin (full permissions) | edas:* | acs:edas:*:*:* |
Acting Alibaba Cloud account | edas:ManageSystem | acs:edas:*:*:* |
System management - View operation logs | edas:ReadOperationLog | acs:edas:*:*:* |
Application management - Modify microservice namespaces | edas:ManageNamespace | acs:edas:*:*:namespace/${namespaceId} |
Application management - Query microservice namespaces | edas:ReadNamespace | acs:edas:*:*:namespace/${namespaceId} |
Resource management - Create clusters | edas:CreateCluster | acs:edas:*:*:namespace/* |
Resource management - View clusters | edas:ReadCluster | acs:edas:*:*:namespace/*/cluster/${clusterId} |
Resource management - Manage and delete clusters | edas:ReadCluster edas:ManageCluster | acs:edas:*:*:namespace/*/cluster/${clusterId} |
Application management - Create applications | edas:CreateApplication | acs:edas:*:*:namespace/* |
Application management - Deploy, start, scale out, and delete applications | edas:ManageApplication edas:ReadApplication | acs:edas:*:*:namespace/*/application/${applicationId} |
Application management - View application information | edas:ReadApplication | acs:edas:*:*:namespace/*/application/${applicationId} |
Application management - Configure containers and set Java virtual machine (JVM) parameters for applications | edas:ConfigApplication edas:ReadApplication | acs:edas:*:*:namespace/*/application/${applicationId} |
Application management - Set log directories | edas:ManageAppLog edas:ReadApplication | acs:edas:*:*:namespace/*/application/${applicationId} |
Purchase Elastic Compute Service (ECS) resources | edas:ECSPurchase | acs:edas:*:*:* |
Purchase Server Load Balancer (SLB) resources | edas:SLBPurchase | acs:edas:*:*:* |
Purchase Log Service resources | edas:SLSPurchase | acs:edas:*:*:* |