This topic describes the Resource Access Management (RAM) policies that are related to Enterprise Distributed Application Service (EDAS).
Resource variables in policies
In a policy, the following variables are used to define a resource:
$regionid: the ID of the region where the resource is deployed, such as cn-shanghai. For more information, see Regions and zones.
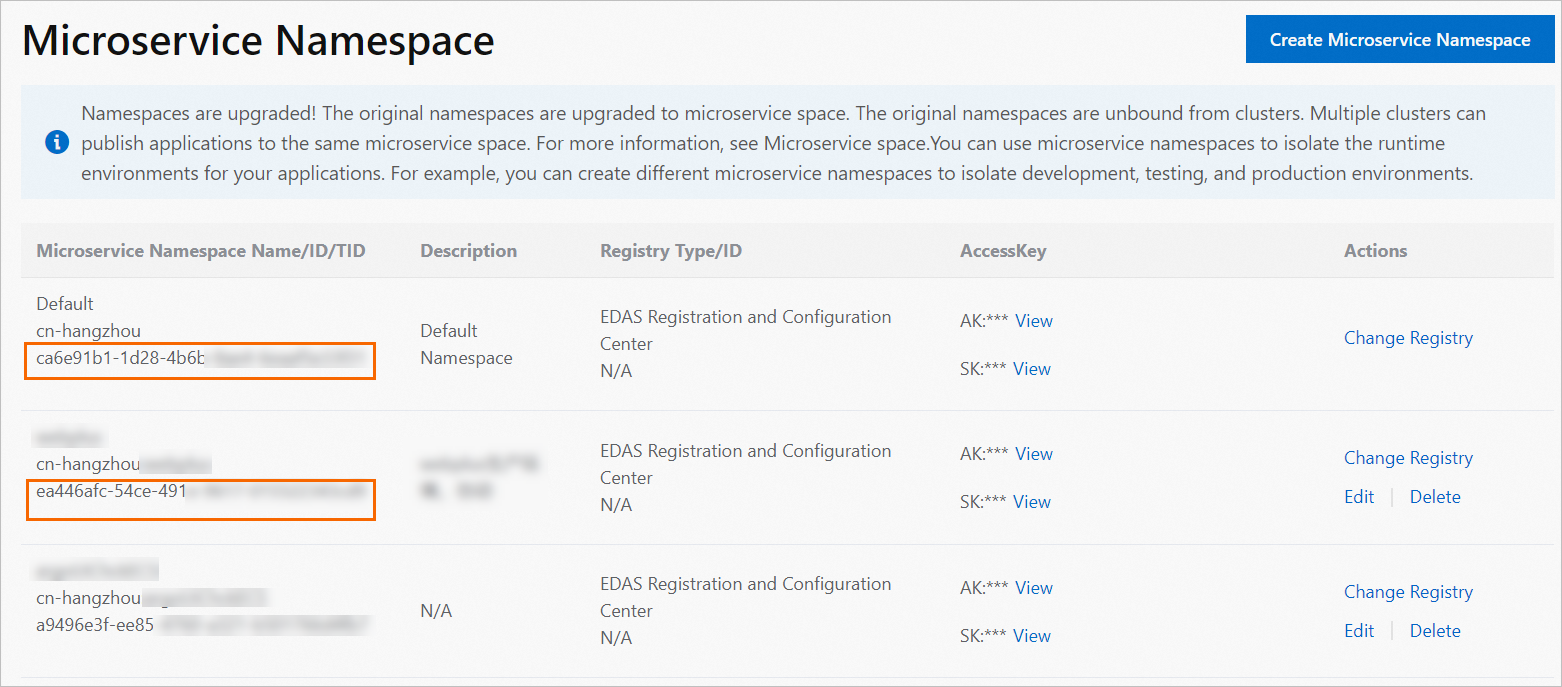
$namespace: the ID of the microservices namespace. The following figure shows the ID of a microservices namespace.
To view microservices namespace IDs, log on to the EDAS console. In the left-side navigation pane, choose . On the Microservices Namespace page, you can view the ID of each microservices namespace.
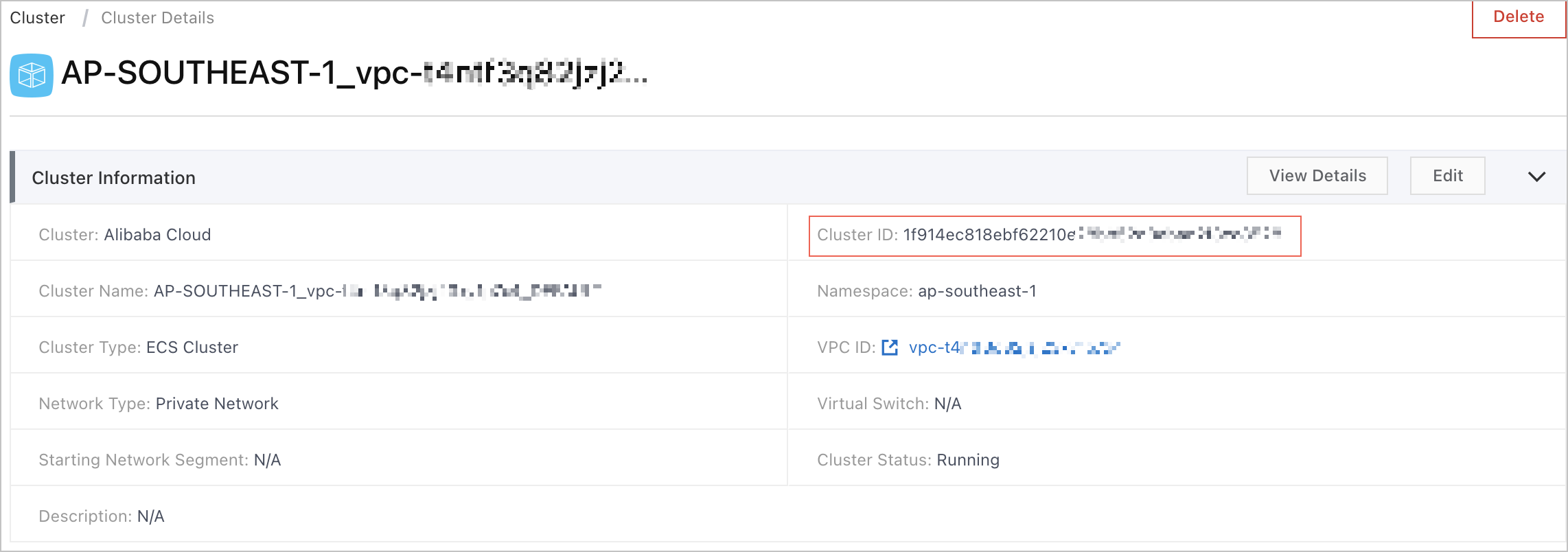
$clusterId: the ID of the cluster. Example: 8c349f69-505c-436f-8dc7-**********. The following figure shows the ID of a cluster.
To view cluster IDs, log on to the EDAS console. In the left-side navigation pane, choose . On the ECS Cluster page, click the desired cluster ID in the Cluster ID/Name column to go to the Cluster Details page to view the ID of the cluster.
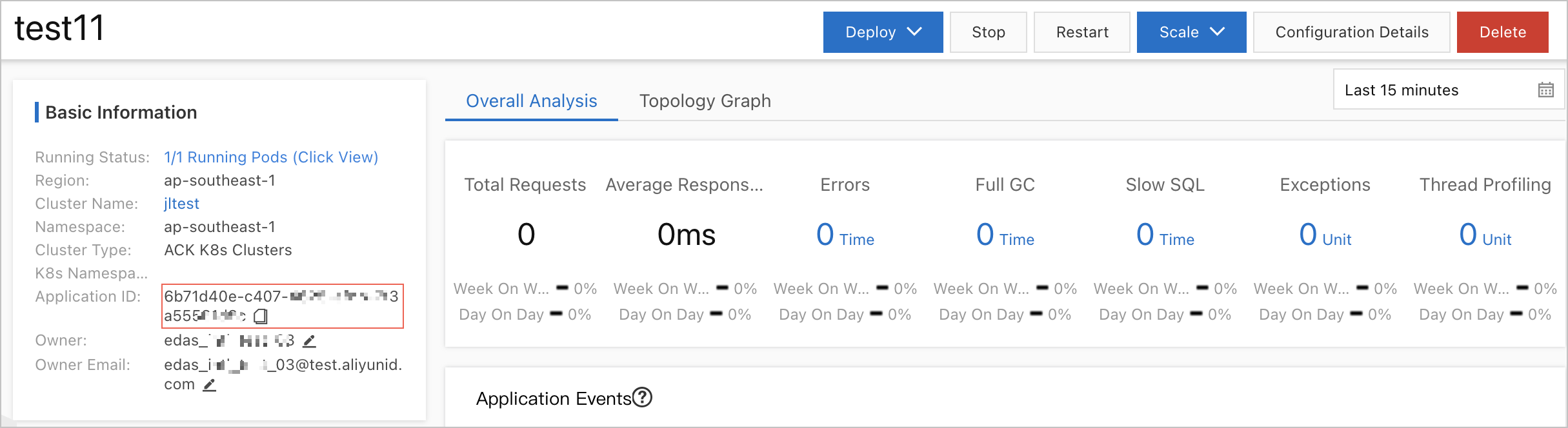
$applicationId: the ID of the application. Example: ec8e38a3-3dca-47a7-b6f9-5**********. The following figure shows the ID of an application.
To view application IDs, log on to the EDAS console. In the left-side navigation pane, choose . On the Applications page, click the name of the desired application in the Application Name column to go to the application details page. On the Basic Information tab of the application details page, you can view the ID of the application.
Details about policies
This section describes how an EDAS-defined permission corresponds to a RAM policy.
Microservices namespace management
Table 1. Microservices namespace management
Code | Description | Dependency action | Resource |
1.1 | Create microservices namespaces. | edas:CreateNamespace | acs:edas:$regionid:$accountid:namespace/* |
1.2 | Delete microservices namespaces. | edas:ReadNamespace | acs:edas:$regionid:$accountid:namespace/$namespace |
edas:DeleteNamespace | |||
1.4 | Modify microservices namespaces. | edas:ManageNamespace | acs:edas:$regionid:$accountid:namespace/$namespace |
edas:ReadNamespace | |||
1.5 | View microservices namespaces. | edas:ReadNamespace | acs:edas:$regionid:$accountid:namespace/$namespace |
Table 2. Cluster management
Code | Description | Dependency action | Resource |
2.1 | Create clusters. | edas:CreateCluster | acs:edas:$regionid:$accountid:namespace/$namespace/cluster/* |
2.2 | Delete clusters. | edas:ReadCluster | acs:edas:$regionid:$accountid:namespace/$namespace/cluster/$clusterId |
edas:DeleteCluster | |||
2.4 | Manage clusters. | edas:ReadCluster | acs:edas:$regionid:$accountid:namespace/$namespace/cluster/$clusterId |
edas:ManageCluster | |||
2.3 | View clusters. | edas:ReadCluster | acs:edas:$regionid:$accountid:namespace/$namespace/cluster/$clusterId |
Table 3. Application management
Code | Description | Dependency action | Resource |
3.1 | Create applications. | edas:CreateApplication | acs:edas:$regionid:$accountid:namespace/$namespace/application/* |
3.2 | Delete applications. | edas:ReadApplication | acs:edas:$regionid:$accountid:namespace/$namespace/application/$applicationId |
edas:DeleteApplication | |||
3.3 | View applications. | edas:ReadApplication | acs:edas:$regionid:$accountid:namespace/$namespace/application/$applicationId |
3.4 | Manage applications. | edas:ManageApplication | acs:edas:$regionid:$accountid:namespace/$namespace/application/$applicationId |
edas:ReadApplication | |||
3.5 | Configure applications. | edas:ConfigApplication | acs:edas:$regionid:$accountid:namespace/$namespace/application/$applicationId |
edas:ReadApplication | |||
3.6 | Manage logs. | edas:ReadApplication | acs:edas:$regionid:$accountid:namespace/$namespace/application/$applicationId |
edas:ManageAppLog |
Table 4. Microservices management
Code | Description | Dependency action | Resource |
4.1 | View microservices. | edas:ReadService | acs:edas:$regionid:$accountid:namespace/$namespace/application/$applicationId |
4.2 | Test microservices. | edas:TestService | acs:edas:$regionid:$accountid:namespace/$namespace/application/$applicationId |
4.3 | Manage microservices. | edas:ReadService | acs:edas:$regionid:$accountid:namespace/$namespace/application/$applicationId |
edas:ManageService |
Table 5. Configuration management
Code | Description | Dependency action | Resource |
5.1 | View configurations. | acms:R | acs:acms:$regionid:$accountid:cfg/$namespace/$groupId/$configId |
5.2 | Manage configurations. | acms:* | acs:acms:$regionid:$accountid:cfg/$namespace/$groupId/$configId |
Table 6. System management
Code | Description | Dependency action | Resource |
6.1 | Manage the EDAS system. | edas:ManageSystem | acs:edas:$regionid:$accountid:* |
6.2 | View operation logs. | edas:ReadOperationLog | acs:edas:$regionid:$accountid:* |
6.3 | Perform system O&M operations. | edas:ManageOperation | acs:edas:$regionid:$accountid:* |
6.4 | Purchase Elastic Compute Service (ECS) instances. | edas:ECSPurchase | acs:edas:*:*:* |
6.5 | Purchase Server Load Balancer (SLB) instances. | edas:SLBPurchase | acs:edas:*:*:* |
6.6 | Purchase Simple Log Service projects. | edas:SLSPurchase | acs:edas:*:*:* |
Table 7. Management of EDAS features that are available for commercial use
Code | Description | Dependency action | Resource |
7 | Manage EDAS features that are available for commercial use. | edas:ManageCommercialization | acs:edas:$regionid:$accountid:* |
Cluster management
The following scenarios describe the permissions that are required for managing clusters:
Create clusters
To grant a RAM user the permissions required to create clusters, ensure that cluster/ in the value of the Resource parameter is followed by an asterisk (*).
{
"Version": "1",
"Statement": [
{
"Action": ["edas:CreateCluster"],
"Resource": ["acs:edas:$regionid:*:namespace/$namespace/cluster/*"],
"Effect": "Allow"
}
]
}View details of a cluster
Requires read-only permissions on the cluster, such as the permissions that are required to view the details about a cluster, including the instances and applications in the cluster.
You can grant a RAM user the permissions on a resource group so that the RAM user can view the details of the clusters in the resource group.
{
"Version": "1",
"Statement": [
{
"Action": ["edas:ReadCluster"],
"Resource": ["acs:edas:$regionid:*:namespace/$namespace/cluster/$clusterId"],
"Effect": "Allow"
}
]
}Manage clusters
Allows a RAM user to create a cluster, add instances to a cluster, modify a cluster, and delete a cluster.
{
"Version": "1",
"Statement": [
{
"Action": ["edas:ManageCluster"],
"Resource": ["acs:edas:$regionid:*:namespace/$namespace/cluster/$clusterId"],
"Effect": "Allow"
}
]
}The following examples show how to grant cluster management permissions to a RAM user:
Example 1: Grant cluster management permissions to the RAM user but forbid the RAM user from creating clusters.
{ "Version": "1", "Statement": [ { "Action": ["edas:ManageCluster"], "Resource": ["acs:edas:$regionid:*:namespace/$namespace/cluster/$clusterId"], "Effect": "Allow" }, { "Action": ["edas:CreateCluster"], "Resource": ["acs:edas:$regionid:*:namespace/$namespace/cluster/*"], "Effect": "Deny" } ] }NoteIf the
$clusterIdvariable is set to a specific cluster ID, the RAM user can manage only the specified cluster. If the $clusterId variable is set to an asterisk (*), the RAM user can manage all clusters in the specified microservices namespace.Example 2: Grant cluster management permissions to the RAM user but forbid the RAM user from creating or deleting clusters.
{ "Version": "1", "Statement": [ { "Action": ["edas:ManageCluster"], "Resource": ["acs:edas:$regionid:*:namespace/$namespace/cluster/$clusterId"], "Effect": "Allow" }, { "Action": ["edas:CreateCluster","edas:DeleteCluster"], "Resource": ["acs:edas:$regionid:*:namespace/$namespace/cluster/*"], "Effect": "Deny" } ] }
Delete clusters
{
"Version": "1",
"Statement": [
{
"Action": ["edas:ReadCluster","edas:DeleteCluster"],
"Resource": ["acs:edas:$regionid:*:namespace/$namespace/cluster/$clusterId"],
"Effect": "Allow"
}
]
}Microservices namespace management
The following scenarios describe the permissions that are required for managing microservices namespaces:
Create microservices namespaces
To grant a RAM user the permissions required to create microservices namespaces, ensure that namespace/ in the value of the Resource parameter is followed by an asterisk (*).
{
"Version": "1",
"Statement": [
{
"Action": ["edas:CreateNamespace"],
"Resource": ["acs:edas:$regionid:*:namespace/*"],
"Effect": "Allow"
}
]
}View microservices namespaces
{
"Version": "1",
"Statement": [
{
"Action": ["edas:ReadNamespace"],
"Resource": ["acs:edas:$regionid:*:namespace/$namespace"],
"Effect": "Allow"
}
]
}Manage microservices namespaces
To allow a RAM user to modify or rename microservices namespaces, you must grant the RAM user the permissions to manage the microservices namespaces.
{
"Version": "1",
"Statement": [
{
"Action": ["edas:ManageNamespace"],
"Resource": ["acs:edas:$regionid:*:namespace/$namespace"],
"Effect": "Allow"
}
]
}Delete microservices namespaces
{
"Version": "1",
"Statement": [
{
"Action": ["edas:ReadNamespace","edas:DeleteNamespace"],
"Resource": ["acs:edas:$regionid:*:namespace/$namespace"],
"Effect": "Allow"
}
]
}Resource purchases
To enhance the permission management capabilities of enterprise users, EDAS allows the enterprise users to grant the permissions to purchase resources. The resources include ECS, SLB, and Log Service resources.
The following scenarios describe the permissions that are required for purchasing resources:
In all resource purchasing policies, the value of the
Resourceparameter must beacs:edas:*:*:*. Finer-grained configurations are not supported.Resource purchasing policies apply only to RAM users.
Purchase ECS resources
Applicable scope:
Purchase ECS resources in an ECS cluster.
Purchase ECS resources when you create an application in an ECS cluster.
Purchase ECS resources when you scale out an application in an ECS cluster.
Sample policy:
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "edas:ECSPurchase" ], "Resource": [ "acs:edas:*:*:*" ] } ] }
Purchase SLB resources
Applicable scope: Purchase SLB resources when you bind an SLB instance to an application.
Sample policy:
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "edas:SLBPurchase" ], "Resource": [ "acs:edas:*:*:*" ] } ] }
Purchase Simple Log Service resources
Applicable scope: Purchase Log Service resources for an application.
Sample policy:
{ "Version": "1", "Statement": [ { "Effect": "Allow", "Action": [ "edas:SLSPurchase" ], "Resource": [ "acs:edas:*:*:*" ] } ] }
Application management
The following scenarios describe the permissions that are required for managing applications:
Permissions on an individual application
Manage an application: allows a RAM user to view the information about an application and manage the configurations and logs of an application, but does not allow the RAM user to create or delete applications.
{ "Statement": [ { "Action": [ "edas:*Application" ], "Effect": "Allow", "Resource": ["acs:edas:$regionid:*:namespace/$namespace/application/$applicationId"] }, { "Action": [ "edas:DeleteApplication" ], "Resource":["acs:edas:$regionid:*:namespace/$namespace/application/$applicationId"], "Effect": "Deny" }, { "Action": [ "edas:CreateApplication" ], "Resource":["acs:edas:$regionid:*:namespace/$namespace/application/*"], "Effect": "Deny" } ], "Version": "1" }Create an application
ImportantTo create an application, a user needs to use an instance in the cluster. Therefore, you must grant the RAM user the permissions to view the cluster.
{ "Statement": [ { "Action": [ "edas:CreateApplication", "edas:ReadCluster" ], "Effect": "Allow", "Resource": [ "acs:edas:$regionid:*:namespace/$namespace/application/*", "acs:edas:$regionid:*:namespace/$namespace/cluster/$clusterId" ] } ], "Version": "1" }Delete an application
ImportantTo allow a RAM user to delete an application, you must grant the RAM user the permissions to view the application. Otherwise, the RAM user cannot find the application.
{ "Statement": [ { "Action": [ "edas:DeleteApplication", "edas:ReadApplication" ], "Effect": "Allow", "Resource": ["acs:edas:$regionid:*:namespace/$namespace/application/$applicationId"] } ], "Version": "1" }Manage logs
ImportantTo allow a RAM user to manage the logs of an application, you must grant the RAM user the permissions to view the application. Otherwise, the RAM user cannot find the application.
{ "Statement": [ { "Action": [ "edas:ReadApplication", "edas:ManageAppLog" ], "Effect": "Allow", "Resource": ["acs:edas:$regionid:*:namespace/$namespace/application/$applicationId"] } ], "Version": "1" }Configure an application: allows a RAM user to set the application port, Tomcat context, load balancing parameters, health check parameters, Java virtual machine (JVM) parameters, and the Intra-zone Provider First feature.
ImportantTo allow a RAM user to configure an application, you must grant the RAM user the permissions to view the application.
{ "Statement": [ { "Action": [ "edas:ReadApplication", "edas:ConfigApplication" ], "Effect": "Allow", "Resource": ["acs:edas:$regionid:*:namespace/$namespace/application/$applicationId"] }, ], "Version": "1" }
Permissions on multiple applications
Query applications: allows a RAM user to query applications in a specified region.
NoteA region may contain one or more microservices namespaces. This permission allows a RAM user to query applications in all microservices namespaces in a specified region.
{ "Statement": [ { "Action": [ "edas:ReadApplication" ], "Effect": "Allow", "Resource": ["acs:edas:$regionid:*:namespace/*/application/*"] } ], "Version": "1" }View applications: allows a RAM user to view applications in a specified microservices namespace.
{ "Statement": [ { "Action": [ "edas:*Application", "edas:ReadCluster" ], "Effect": "Allow", "Resource": [ "acs:edas:$regionid:*:namespace/$namespace/application/*", "acs:edas:$regionid:*:namespace/$namespace/cluster/*" ] } ], "Version": "1" }
Microservices management
The following scenarios describe the permissions that are required for managing microservices:
View microservices
To grant a RAM user the permissions required to view all microservices, set the $applicationId variable in the following policy to an asterisk (*).
{
"Statement": [
{
"Action": [
"edas:ReadService"
],
"Effect": "Allow",
"Resource": [
"acs:edas:$regionid:*:namespace/$namespace/application/$applicationId"
]
}
],
"Version": "1"
}Test microservices
To grant a RAM user the permissions required to test all microservices across microservices namespaces, set the $namespace and $applicationId variables in the following policy to an asterisk (*).
{
"Statement": [
{
"Action": [
"edas:TestService"
],
"Effect": "Allow",
"Resource": [
"acs:edas:$regionid:*:namespace/$namespace/application/$applicationId"
]
}
],
"Version": "1"
}Manage microservices
To grant a RAM user the permissions required to manage all microservices, set the $applicationId variable in the following policy to an asterisk (*).
{
"Statement": [
{
"Action": [
"edas:ManageService"
],
"Effect": "Allow",
"Resource": [
"acs:edas:$regionid:*:namespace/$namespace/application/$applicationId"
]
}
],
"Version": "1"
}Remove outlier instances
The removal of an outlier instance affects applications in the microservices namespace. You can grant RAM users the permissions to remove outlier instances only in a specified microservices namespace.
{
"Statement": [
{
"Action": [
"edas:ManageService"
],
"Effect": "Allow",
"Resource": [
"acs:edas:$regionid:*:namespace/$namespace"
]
}
],
"Version": "1"
}System management
Includes the permissions to manage RAM users, view resource usage, and view operations logs.
{
"Version": "1",
"Statement": [
{
"Action": ["edas:ManageSystem"],
"Resource": ["acs:edas:*:*:*"],
"Effect": "Allow"
}
]
}System policies are not defined by specific resources. Set the Resource variable in these policies to acs:edas:*:*:*.
Perform system O&M operations
Allows a RAM user to view operation logs, perform one or more O&M tasks at a time, and manage resource groups.
{
"Version": "1",
"Statement": [
{
"Action": ["edas:ManageOperation"],
"Resource": ["acs:edas:*:*:*"],
"Effect": "Allow"
}
]
}View operation logs
{
"Version": "1",
"Statement": [
{
"Action": ["edas:ReadOperationLog"],
"Resource": ["acs:edas:*:*:*"],
"Effect": "Allow"
}
]
}