This topic explains how to troubleshoot the "error: Unable to load host key: /etc/ssh/ssh_host_rsa_key" error when you connect to a Linux Elastic Compute Service (ECS) instance over SSH.
Problem description
You cannot connect to a Linux ECS instance by using SSH. After logging in to the instance using Virtual Network Computing (VNC) and running the cat /var/log/secure or cat /var/log/messages command, the logs show an error message similar to the following.
error: @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
error: @ WARNING: UNPROTECTED PRIVATE KEY FILE! @
error: @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
error: Permissions 0777 for '/etc/ssh/ssh_host_rsa_key' are too open.
error: It is required that your private key files are NOT accessible by others.
error: This private key will be ignored.
error: Unable to load host key "/etc/ssh/ssh_host_rsa_key": bad permissions
error: Unable to load host key: /etc/ssh/ssh_host_rsa_keyerror: Unable to load host key "/etc/ssh/ssh_host_rsa_key": invalid format
error: Unable to load host key "/etc/ssh/ssh_host_rsa_key": invalid format
error: Unable to load host key: /etc/ssh/ssh_host_rsa_key
error: Unable to load host key "/etc/ssh/ssh_host_ecdsa_key": invalid format
error: Unable to load host key "/etc/ssh/ssh_host_ecdsa_key": invalid format
error: Unable to load host key: /etc/ssh/ssh_host_ecdsa_keyCause
This issue can occur if the SSH key files on the ECS instance are invalid. Invalid key files prevent the sshd daemon from loading the correct SSH host keys. Common reasons include:
The permissions for the SSH host key files are incorrect.
For example, the default permission for a private key file is
600. If the permission is set to a more permissive value, such as777, other users can access the file. The SSH service considers this a security risk and ignores the key. Consequently, the sshd daemon cannot load the key, and connection attempts fail.The SSH host key files are corrupted, deleted, or have been tampered with.
Solution
To resolve this issue, regenerate the SSH host key files.
Connect to the Linux ECS instance using VNC.
For more information, see Choose a connection method.
Regenerate the SSH host key files.
sudo rm -f /etc/ssh/ssh_host_* sudo /usr/bin/ssh-keygen -A sudo chmod 600 /etc/ssh/ssh_host_* sudo chmod 644 /etc/ssh/*.pubTo verify that the key files were generated, run the following command.
ls -l /etc/ssh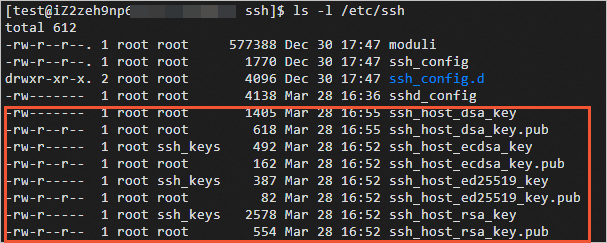
Restart the SSH service.
sudo systemctl restart sshd.service
What to do next
After regenerating the host key, you may encounter the following error when connecting to the instance with SSH. This occurs because your local machine has cached the old host key fingerprint. To resolve this issue, see The system prompts "Host key verification failed" when logging on to the ECS instance over SSH.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that the RSA host key has just been changed.
The fingerprint for the RSA key sent by the remote host is
ae:6e:68:4c:97:a6:91:81:11:38:8d:64:ff:92:13:50.
Please contact your system administrator.
Add correct host key in /root/.ssh/known_hosts to get rid of this message.
Offending key in /root/.ssh/known_hosts:70
RSA host key for x.x.x.x has changed and you have requested strict checking.
Host key verification failed.