This topic describes how to create a trusted isolation space by using the Alibaba Cloud Enclave feature to protect your applications and data.
Background information
Data is classified into data at rest, data in transit, and data in use.
The security of data at rest and data in transit can be ensured by using encryption.
The security of data in use is difficult to ensure. Confidential computing is commonly used to protect this data.
The Enclave feature provides an enclave as a trusted isolation space within Elastic Compute Service (ECS) instances and encapsulates secure operations of legitimate software in the enclave to guarantee the confidentiality and integrity of your code and data against malware attacks. It is suitable for business that requires strong protection for sensitive and confidential data, such as those in finance, Internet, and healthcare industries.
How Enclave works
Computing resources (including vCPUs and memory) within an ECS instance (the primary VM) are split to create an Enclave VM (EVM), which serves as a trusted execution environment. The following factors contribute to EVM security:
The underlying virtualization technology provides isolation for security. The EVM is isolated from the primary VM and other ECS instances.
The EVM runs an independent, customized, and trusted operating system (OS). It has no persistent storage, interactive connections, or external network channels and communicates with the primary VM only through a local secure channel based on vsock to minimize the attack surface. You can run applications that involve confidential data in the EVM and securely interact with applications that run within the primary VM.
The following figure shows how the Enclave feature works.

The Enclave feature provides multi-layer security. At the underlying layer, the third-generation SHENLONG architecture, together with Trusted Platform Module (TPM) or Trust Cryptography Module (TCM) chips, provides the EVM with vTPM or vTCM devices to enhance security and trusted capabilities. At the upper layer, highly compatible SDKs are provided to help you quickly build and use an Enclave environment. For attestation capabilities, you can verify code running in the confidential execution environment, such as by using SDKs. Confidential applications can generate attestation materials, including platform data, application information, and signatures, at runtime and verify them by using a remote attestation server, which may work with Key Management Service (KMS). When the primary VM allocates resources to the EVM and the EVM starts to run, the underlying layer isolates resources to ensure that the primary VM cannot access the EVM's vCPU or memory resources. This secures EVM operations and privacy.
The following figure shows the architecture of the Enclave feature.

Limitations
Only instance types with four or more vCPUs in the hfg9i, hfc9i, hfr9i, g8i, c8i, and r8i instance families support the Enclave feature.
You can create only one enclave for each ECS instance.
Before you use an enclave, reserve at least one physical processor core and some memory for the primary VM. The rest can be flexibly allocated to the enclave. If Hyper-Threading is enabled, two hyperthreads from the same physical processor core are reserved. Therefore, an ECS instance for which the Enclave feature is enabled must have at least four vCPUs.
For information about other limits, see Limits.
Create an Enclave-enabled instance
The procedure to create an ECS instance for which the Enclave feature is enabled in the ECS console is similar to that to create a regular ECS instance. However, you must pay attention to specific parameters. This section focuses on the parameters related to Enclave-enabled instances on the instance buy page. For information about other parameters, see Create an instance on the Custom Launch tab.
Go to ECS console - Instance.
In the top navigation bar, select the region and resource group of the resource that you want to manage.

Click Create Instance and configure the parameters in the following table.
Parameter
Description
Instance Type
Select an instance type with four or more vCPUs in the hfg9i, hfc9i, hfr9i, g8i, c8i, or r8i instance family.
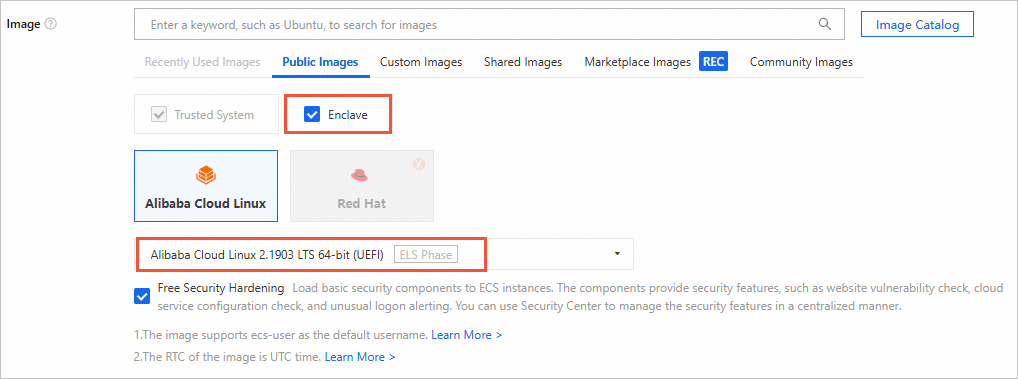
Image
Select Enclave and then select the Alibaba Cloud Linux 2.1903 LTS 64-bit (UEFI) image.
NoteWhen you select Enclave, a trusted operating system is automatically installed.
Instance RAM Role
Select AliyunECSInstanceForYundunSysTrustRole, which is a service-linked role provided by Alibaba Cloud.
Install the Enclave CLI
Use Workbench to connect to the Enclave-enabled instance over SSH.
Install the RPM Package Manager (RPM) package of the Enclave CLI.
Download the RPM package of the Enclave CLI.
wget https://enclave-cn-beijing.oss-cn-beijing.aliyuncs.com/download/linux/enclave-cli/x86_64/2.1903/enclave-cli-1.0.8-1.x86_64.rpmInstall the Enclave CLI.
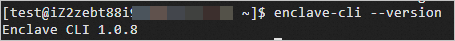
sudo rpm -ivh enclave-cli-1.0.8-1.x86_64.rpmCheck the version of the Enclave CLI.
enclave-cli --versionIf the version is returned, the Enclave CLI is installed.
Add the current user to the
deanddockergroups.Run the following command to add the current user to the
degroup:sudo usermod -aG de <username>NoteReplace
<username>with the actual username. Example:test.Add the current user to the
dockergroup.sudo usermod -aG docker <username>NoteReplace
<username>with the actual username. Example:test.Reconnect to the instance for the settings to take effect.
Pre-allocate vCPUs and memory to the enclave.
Open the
allocator.yamlconfiguration file.sudo vim /etc/ali-enclaves/allocator.yamlPress the
ikey to enter Insert mode.Modify the following parameters:
memory_mib: the amount of memory to allocate to the enclave. Unit: MiB.
cpu_count: the number of vCPUs to allocate to the enclave.
The following sample code snippet indicates that the enclave is allocated 1,024 MiB of memory and 2 vCPUs.
# Enclave configuration file. # # How much memory to allocate for enclaves (in MiB). memory_mib: 1024 # # How many CPUs to reserve for enclaves. cpu_count: 2Press the
Esckey, enter:wq, and then press theEnterkey to save and close the file.
Start the enclave resource allocation service and configure the service to run on instance startup.
sudo systemctl start ali-enclaves-allocator.service && \ sudo systemctl enable ali-enclaves-allocator.serviceThe resource allocation service generates a vCPU pool for the enclave based on the specified number of vCPUs. The vCPU pool is available only to the enclave, not the ECS instance to which the enclave belongs.
NoteTo change the resources allocated to the enclave, modify the
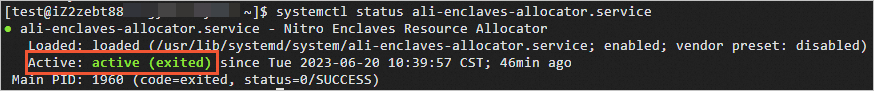
allocator.yamlconfiguration file and run the following command to restart the enclave resource allocation service:sudo systemctl restart ali-enclaves-allocator.serviceCheck the status of the enclave resource allocation service.
systemctl status ali-enclaves-allocator.serviceThe following output shows that the service is started.
Start Docker and configure it to run on instance startup.
sudo systemctl start docker && sudo systemctl enable dockerNoteIf you no longer need the Enclave feature, run the
sudo yum remove enclave-clicommand to uninstall the Enclave CLI.Restart the instance to apply the changes.
Reference
For information about how to use the Enclave CLI, see Quickly use the Enclave CLI.