Elastic Compute Service (ECS) instances do not have a default password. If you forget the password, you can reset it. If you do not set a username when creating an instance, the system uses a default username.
Operating system | Default username | Description |
Linux |
| The superuser for Linux. |
Windows |
| The superuser for Windows. |
The root user has high-level permissions, and using it directly is a security risk. To mitigate this risk, use ecs-user and obtain temporary root privileges with sudo for sensitive operations.
Password management
Reset a password
Try the online password reset method first because it does not require an instance restart.
Online password reset (no restart required)
Go to the ECS console - Instance. select a region and resource group, and then find the target instance.
Open the Reset Instance Password dialog box.
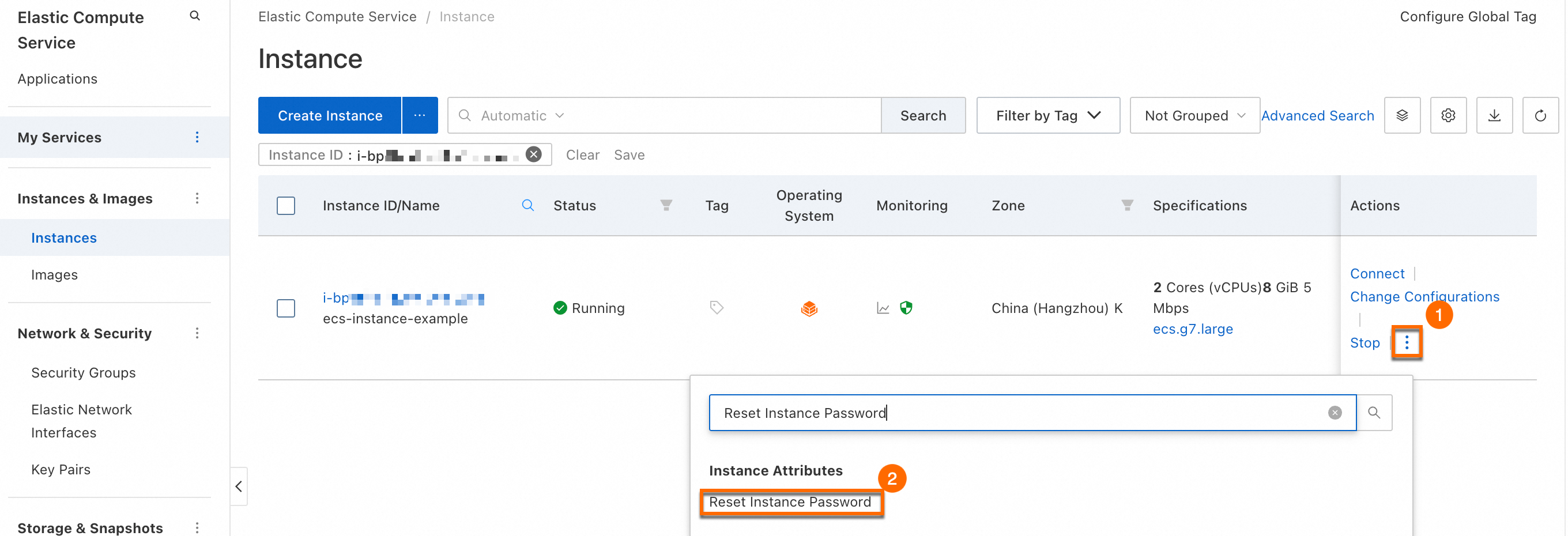
In the Reset Instance Password dialog box, configure the following parameters and click OK. Wait for the password to be reset. Keep the default values for other parameters.
New Password/Confirm Password: Enter a new password for the instance. For security, create a strong password that contains uppercase letters, lowercase letters, digits, and special characters.
For Password Reset Method, select Online Reset.
ImportantIf Online Reset is unavailable, use another method: Offline password reset (restart required).
If the password reset fails, use another method: Offline password reset (restart required).
Offline password reset (restart required)
An offline password reset requires you to restart the instance for the change to take effect. A restart may interrupt services that are running on the instance. Plan the restart time accordingly.
Go to the ECS console - Instance. Select a region and resource group, and then find the instance that you want to manage.
Follow the on-screen instructions to open the Reset Instance Password dialog box.

In the Reset Instance Password dialog box, configure the following parameters and click OK. Wait for the password to be reset.
New Password/Confirm Password: Enter a new password for the instance. For security, create a strong password that contains uppercase letters, lowercase letters, digits, and special characters.
For Password Reset Method, select Offline Reset.
You must restart the instance for the new password to take effect. To ensure service stability, restart the instance during off-peak hours.
Connect to the instance by using VNC.
A successful VNC logon indicates that the password was successfully reset in the operating system.
If you can log on to the instance using VNC but cannot log on using tools such as Workbench, the password was reset successfully. The issue may be with the SSH configuration. For more information, see Troubleshoot connection failures to a Linux instance.
Change a password
You can change the password online from the console.
Online password reset
Go to the ECS console - Instance. Select a region and resource group, and then find the instance that you want to manage.
Depending on your console version, open the Reset Instance Password dialog box.

In the Reset Instance Password dialog box, configure the following parameters and click OK. Wait for the password to be reset. Keep the default values for other parameters.
New Password/Confirm Password: Enter a new password for the instance. Create a strong password that contains uppercase letters, lowercase letters, digits, and special characters.
Password Reset Method: Select Online Reset.
ImportantIf Online Reset is unavailable, change the password manually within the instance.
If the password reset fails, change the password manually within the instance.
Change the password manually within the instance
Windows instances
This example uses a Windows Server 2019 instance.
Right-click the Start icon
 , click Run (R), enter
, click Run (R), enter compmgmt.msc, and then pressEnter.In the navigation pane on the left, choose .
Right-click the username for which you want to change the password, such as Administrator, and then click Set Password.
In the Set Password for Administrator dialog box, click Proceed. Enter a new password in the New Password and Confirm Password fields.
ImportantCreate a strong password. It must contain uppercase letters, lowercase letters, digits, and special characters.
Click OK. A confirmation message appears, indicating that the password has been set.
Linux instances
This example uses an Alibaba Cloud Linux 3 instance.
Run the following command to change the password for a specified user:
Replace
<username>with the actual username.sudo passwd <username>Enter the new password and press
Enter. Re-enter the new password and pressEnteragain.ImportantCreate a strong password. It must contain uppercase letters, lowercase letters, digits, and special characters.
If the password is changed, a message similar to the following is returned:
passwd: all authentication tokens updated successfully.
Key pair management
When creating an instance, you can bind a key pair that has been created in or imported to Alibaba Cloud to log on to the instance. You can also bind or replace a key pair later.
A key pair is a more secure credential that can effectively defend against brute-force and dictionary attacks. It consists of a public key, which is stored on the instance, and a private key, which you must keep secure. To log on to the instance, provide the private key for authentication.
To use a key pair with a Windows instance, enable the SSH service on the instance. The console does not support managing key pairs for Windows instances.
Create or import a key pair
Console
Create a key pair
Go to the ECS console - Key Pairs page. In the upper-left corner, select a region and resource group.
An ECS instance can only be bound to a key pair in the same region.
Click Create SSH Key Pair and select Auto-create as the creation method.
Click OK.
After the key pair is created, the private key file (key_pair_name.pem) is automatically downloaded to your local machine.
Import a key pair
View the public key for a private key
Local machine runs Linux or macOS
Use the
ssh-keygencommand to extract and display the public key from an existing private key file.Replace
<path_to_key_pair>with the path to your private key file, for example,/path_to_key_pair/my-key-pair.pem.ssh-keygen -y -f <path_to_key_pair>The public key information is returned:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABA****+GF9q7rhc6vYrExwT4WU4fsaRcVXGV2Mg9RHex21hl1au77GkmnIgukBZjywlQOT4GDdsJy2nBOdJPrCEBIPxxxxxxxxxx/fctNuKjcmMMOA8YUT+sJKn3l7rCLkesE+S5880yNdRjBiiUy40kyr7Y+fqGVdSOHGMXZQPpkBtojcxxxxxxxxxxx/htEqGa/Jq4fH7bR6CYQ2XgH/hCap29Mdi/G5Tx1nbUKuIHdMWOPvjxxxxxxxxxx+lHtTGiAIRG1riyNRVC47ZEVCxxxxxxLocal machine runs Windows
Perform the following steps to view the public key:
Start PuTTYgen.
Click Load.
Select a
.ppkor.pemfile.PuTTYgen displays the public key.
Import a key pair (public key)
Go to the ECS console - Key Pairs page. In the upper-left corner, select a region.
An ECS instance can only be bound to a key pair in the same region.
Click Create SSH Key Pair, select Import as the creation method, and enter the Public Key.
Click OK to complete the import.
API
Create a key pair: For more information, see CreateKeyPair.
Import the public key of a key pair: For more information, see ImportKeyPair.
Bind or replace a key pair
Console
Only Linux instances support binding, unbinding, and replacing key pairs in the console.
Bind a key pair when creating an instance
When you create an instance using the Custom Launch method, you can set Logon Credential to Key Pair and then select an existing Key Pair.
Bind or replace a key pair
Binding or replacing a key pair in the console requires an instance restart for the change to take effect. Restarting the instance may interrupt your services. Plan this operation for a time that minimizes impact.
You can bind a maximum of one key pair to each instance in the console. To bind multiple key pairs, manually bind on the instance (no restart required).
Bind or replace in the console (restart required)
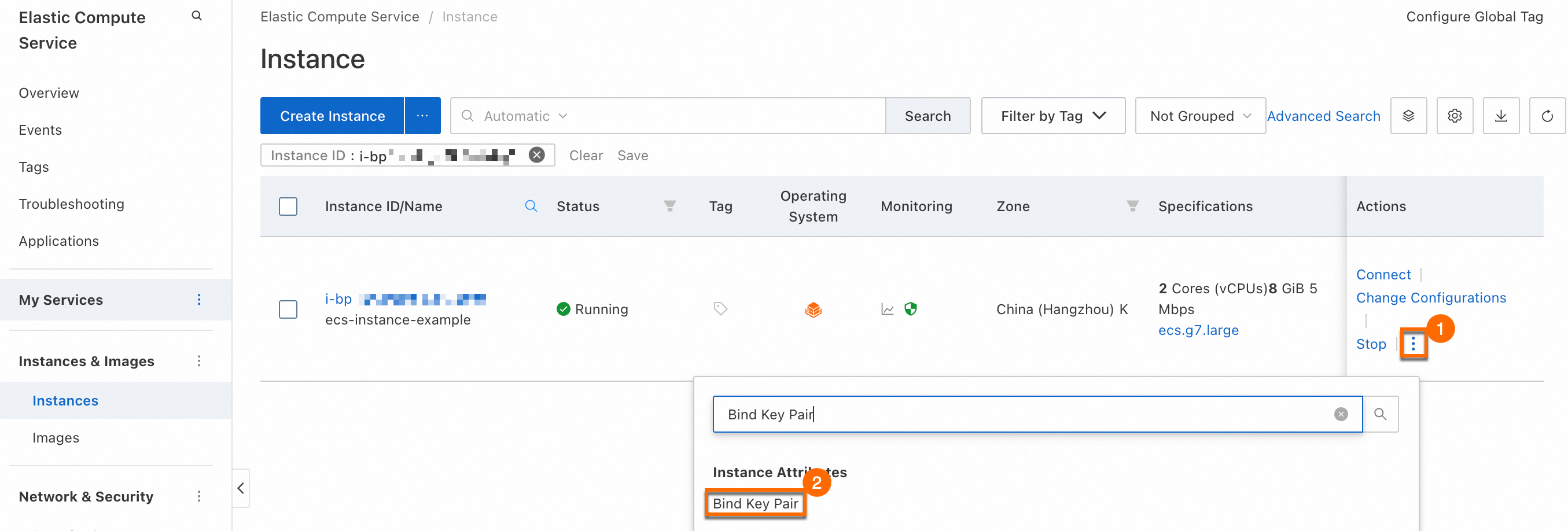
Go to the ECS console - Instance. In the upper-left corner, select a region and resource group. Find the ECS instance and follow these instructions:
In the Actions column, click . Select an existing key pair and click OK. The change takes effect after you restart the instance.
Manually bind on the instance (no restart required)
Generate a key pair
The steps to generate a key pair vary depending on the tool. This example uses the
ssh-keygentool.Run the following command to generate a key pair.
ssh-keygen -t rsa -b 2048 -f id_rsaParameters:
-t rsa: Specifies the key type asrsa.-b 2048: Specifies the key length as 2048 bits.-f id_rsa: Specifies the filename and save location for the key pair.
The system prompts you to enter a passphrase. This passphrase protects your private key. Setting a passphrase is a recommended security measure. If you do not need a passphrase, press
Enterto continue.After the command runs successfully, two files are generated in the current directory:
id_rsa: Your private key.id_rsa.pub: Your public key.
ImportantKeep your private key secure and do not share it with others.
Bind the public key to the instance
After you log on to the instance using Workbench, follow these steps.
The procedure differs for root and non-root users. Choose the appropriate steps based on your needs.
Set the public key for the root user
Create the
authorized_keysconfiguration file.If the
/root/.sshdirectory or theauthorized_keysfile does not exist, run the following commands to create them.sudo mkdir /root/.ssh sudo touch /root/.ssh/authorized_keysAdd the public key.
Open the
authorized_keysfile with a text editor such as Vim.sudo vim /root/.ssh/authorized_keysPaste your public key content into the file. You can add multiple public keys, with each public key on a new line. Save and close the file.
Set file permissions.
SSH requires strict permission settings. Incorrect permissions can cause SSH logon to fail.
Run the following commands to set the correct permissions.
sudo chmod 700 /root/.ssh sudo chmod 600 /root/.ssh/authorized_keys
Set the public key for a non-root user
Create the
authorized_keysconfiguration file.If the
/root/.sshdirectory or theauthorized_keysfile does not exist, run the following commands to create them.In the commands,
<username>represents the username for which you want to bind the public key.sudo mkdir /home/<username>/.ssh sudo touch /home/<username>/.ssh/authorized_keysAdd the public key.
Open the
authorized_keysfile with a text editor such as Vim.sudo vim /home/<username>/.ssh/authorized_keysPaste your public key content into the file. You can add multiple public keys, with each public key on a new line. Save and close the file.
Set file permissions.
SSH requires strict permission settings. Incorrect permissions can cause SSH logon to fail.
Run the following commands to set the correct permissions.
sudo chown -R <username>:<username> /home/<username>/.ssh sudo chmod 700 /home/<username>/.ssh sudo chmod 600 /home/<username>/.ssh/authorized_keys
Enable public key authentication for the SSH service
After configuring the public key, enable SSH public key authentication on the server. Otherwise, key-based logon will fail.
Back up the SSH configuration file
/etc/ssh/sshd_config.sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bak
Open the
/etc/ssh/sshd_configfile with a text editor such as Vim. Find thePubkeyAuthenticationparameter and set its value toyesto enable public key authentication.sudo vim /etc/ssh/sshd_configRestart the SSH service to apply the changes.
For Alibaba Cloud Linux 3:
sudo systemctl restart sshdOn some operating systems, such as Ubuntu and Debian, the SSH service is named
sshinstead ofsshd. Adjust the command accordingly.ImportantIf you are connected to the instance over SSH, restarting the service may disconnect you. You can reconnect after the service restarts.
API
Only Linux instances support binding, replacing, and unbinding key pairs using the API.
Set a key pair when creating an instance: When you call RunInstances to create an instance, set the
KeyPairNameparameter to the name of the key pair.Bind or replace a key pair: Call AttachKeyPair and specify the key pair name
KeyPairNameand instance IDsInstanceIds.unbind a key pair: Call DetachKeyPair and specify the key pair name
KeyPairNameand instance IDsInstanceIds.
Unbind a key pair
Unbinding a key pair in the console requires an instance restart for the change to take effect. Restarting the instance may interrupt your services. Plan this operation for a time that minimizes impact.
Unbind in the console (restart required)
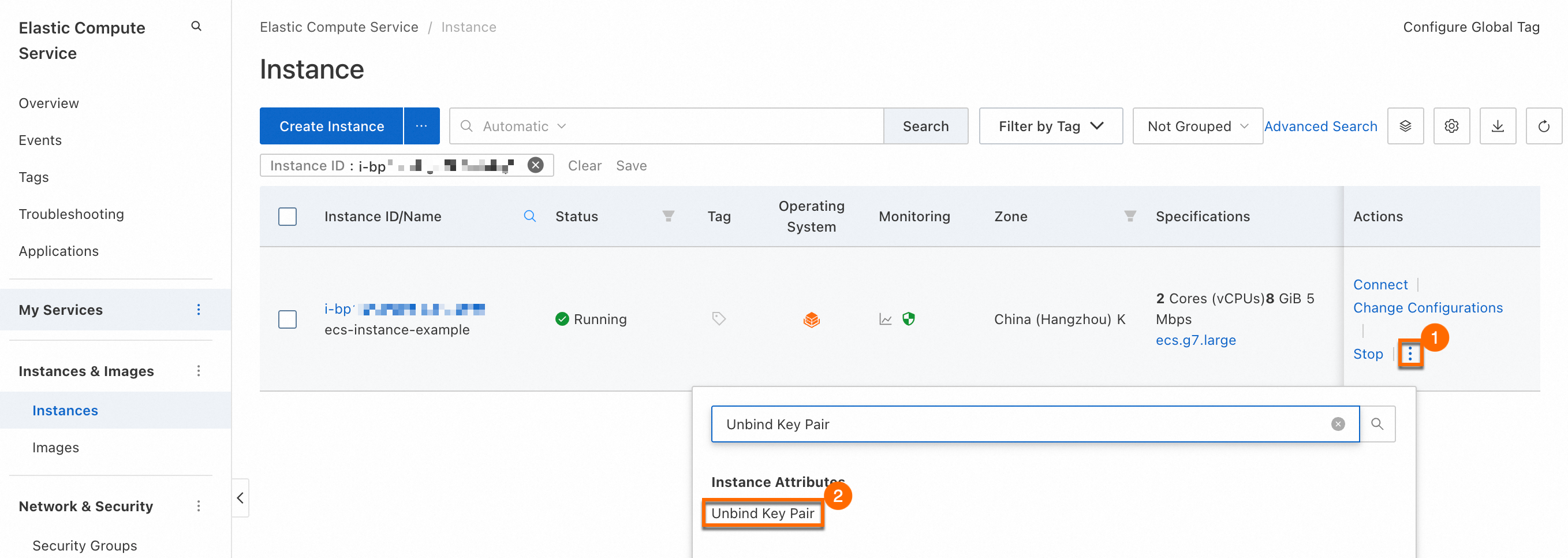
Go to the ECS console - Instance. In the upper-left corner, select a region and resource group. Find the ECS instance and follow these instructions:
In the Actions column, click , and then click Unbind. The change takes effect after you restart the instance.
Manually unbind on the instance (no restart required)
You can manually purge the public keys stored in the authorized_keys file on the instance to unbind a key pair. The path to the authorized_keys configuration file varies depending on the user:
root user:
/root/.ssh/authorized_keysNon-root user:
/home/<username>/.ssh/authorized_keysHere,
<username>represents the non-root username.
Delete a key pair
Console
You cannot delete a key pair that is bound to an instance.
Go to the ECS console - Key Pairs page. In the upper-left corner, select a region and resource group.
Find the key pair that you want to delete and click Delete in the Actions column.
API
Call DeleteKeyPairs and specify the KeyPairNames parameter with the names of the key pairs that you want to delete.
Multi-user remote logon
To allow multiple users to access an ECS instance, follow these steps to create a standard user and enable remote access.
Linux
Log on to the instance using Workbench and follow these steps to create a user:
Create a user
Replace <username> in the command with the desired username. For example, to create a user named
exampleuser, runsudo useradd -m exampleuser.sudo useradd -m <username>Set a password or key pair
Bind a key pair
Generate a key pair file on your local machine.
ImportantFor security reasons, do not create a key pair using ssh-keygen on the instance. Do not save the generated private key on the ECS instance that you want to connect to.
The steps to generate a key pair vary depending on the tool. This example uses the
ssh-keygentool.Run the following command to generate a key pair.
ssh-keygen -t rsa -b 2048 -f id_rsaParameters:
-t rsa: Specifies the key type asrsa.-b 2048: Specifies the key length as 2048 bits.-f id_rsa: Specifies the filename and save location for the key pair.
The system prompts you to enter a passphrase. This passphrase protects your private key. Setting a passphrase is a recommended security measure. If you do not need a passphrase, press
Enterto continue.After the command runs successfully, two files are generated in the current directory:
id_rsa: Your private key.id_rsa.pub: Your public key.
ImportantKeep your private key secure and do not share it with others.
Bind the public key to the user.
Create the
authorized_keysconfiguration file.If the
/root/.sshdirectory or theauthorized_keysfile does not exist, run the following commands to create them.In the commands,
<username>represents the username for which you want to bind the public key.sudo mkdir /home/<username>/.ssh sudo touch /home/<username>/.ssh/authorized_keysAdd the public key.
Open the
authorized_keysfile with a text editor such as Vim.sudo vim /home/<username>/.ssh/authorized_keysPaste your public key content into the file. You can add multiple public keys, with each public key on a new line. Save and close the file.
Set file permissions.
SSH requires strict permission settings. Incorrect permissions can cause SSH logon to fail.
Run the following commands to set the correct permissions.
sudo chown -R <username>:<username> /home/<username>/.ssh sudo chmod 700 /home/<username>/.ssh sudo chmod 600 /home/<username>/.ssh/authorized_keys
Enable public key authentication for the SSH service.
After configuring the public key, enable SSH public key authentication on the server. Otherwise, key-based logon will fail.
Back up the SSH configuration file
/etc/ssh/sshd_config.sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.bak
Open the
/etc/ssh/sshd_configfile with a text editor such as Vim. Find thePubkeyAuthenticationparameter and set its value toyesto enable public key authentication.sudo vim /etc/ssh/sshd_configRestart the SSH service to apply the changes.
For Alibaba Cloud Linux 3:
sudo systemctl restart sshdOn some operating systems, such as Ubuntu and Debian, the SSH service is named
sshinstead ofsshd. Adjust the command accordingly.ImportantIf you are connected to the instance over SSH, restarting the service may disconnect you. You can reconnect after the service restarts.
Set a password
Run the following command:
Replace
<username>with the username for which you want to set the password.sudo passwd <username>Enter the new password and press
Enter. Re-enter the new password to confirm and pressEnter.If the change is successful, a message similar to the following is displayed:
passwd: all authentication tokens updated successfully.(Verification) Log on to the ECS instance as the new user.
Windows
By default, Windows supports a maximum of two concurrent remote connections over Remote Desktop Protocol (RDP). If you need more than two users to log on to a Windows instance at the same time, you must use Microsoft's Remote Desktop Services.
Log on to the instance using Workbench and follow these steps:
Create a user
Open Control Panel, find User Accounts, and click Change account type.
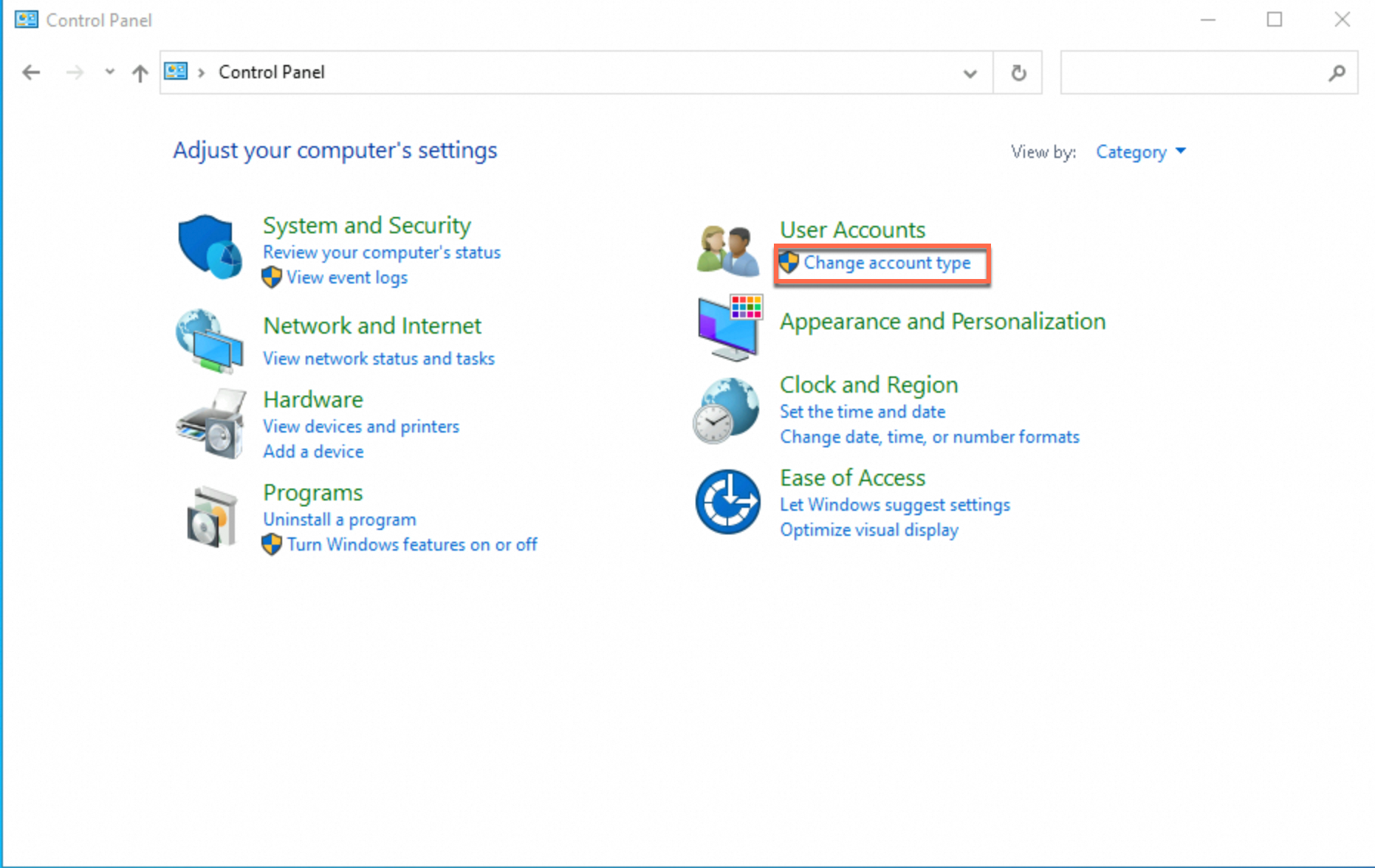
On the Manage Accounts page, click Add a user account to go to the Add a user page.
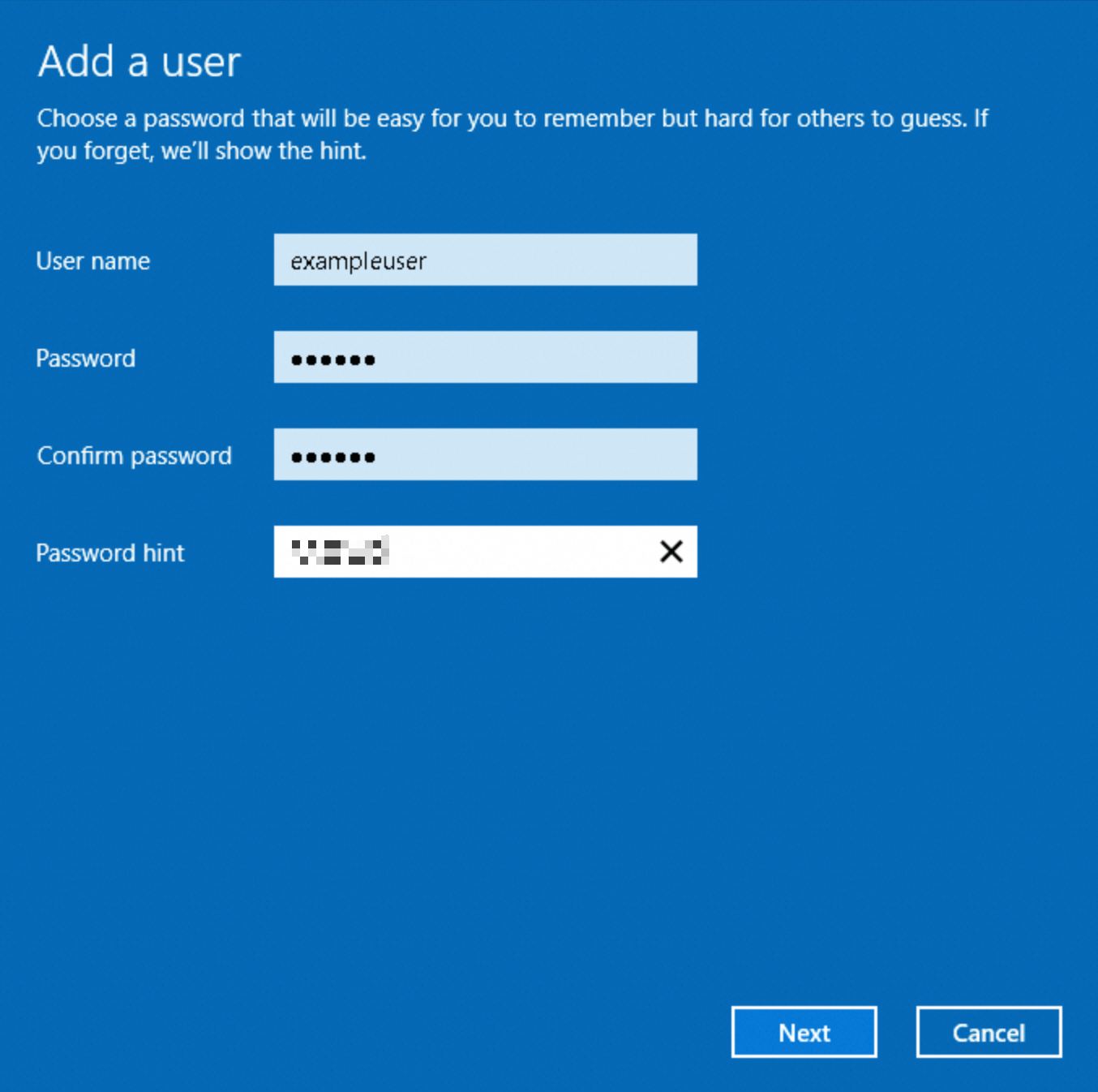
On the Add a user page, follow the on-screen instructions to set the username and password for the new user.
This example creates a user named exampleuser. Set the User name as needed.
Click Next, and then click Finish. The new user is created.
Add the new user to the
Remote Desktop UsersgroupOnly users in the Remote Desktop Users group can log on to the instance remotely.
In the search box on the taskbar, search for Computer Management and click to open the Computer Management window.
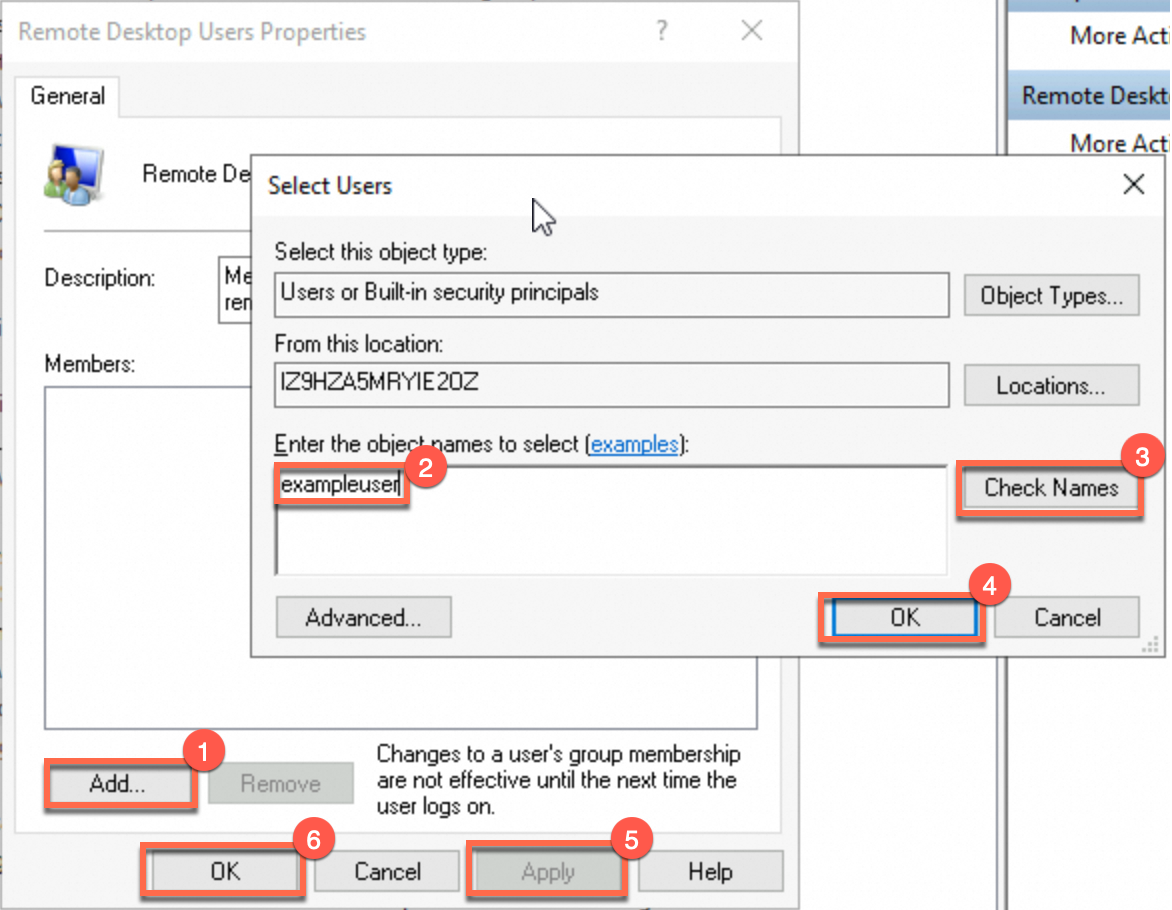
Under , find the Remote Desktop Users group. Double-click it to open the Remote Desktop Users Properties page.
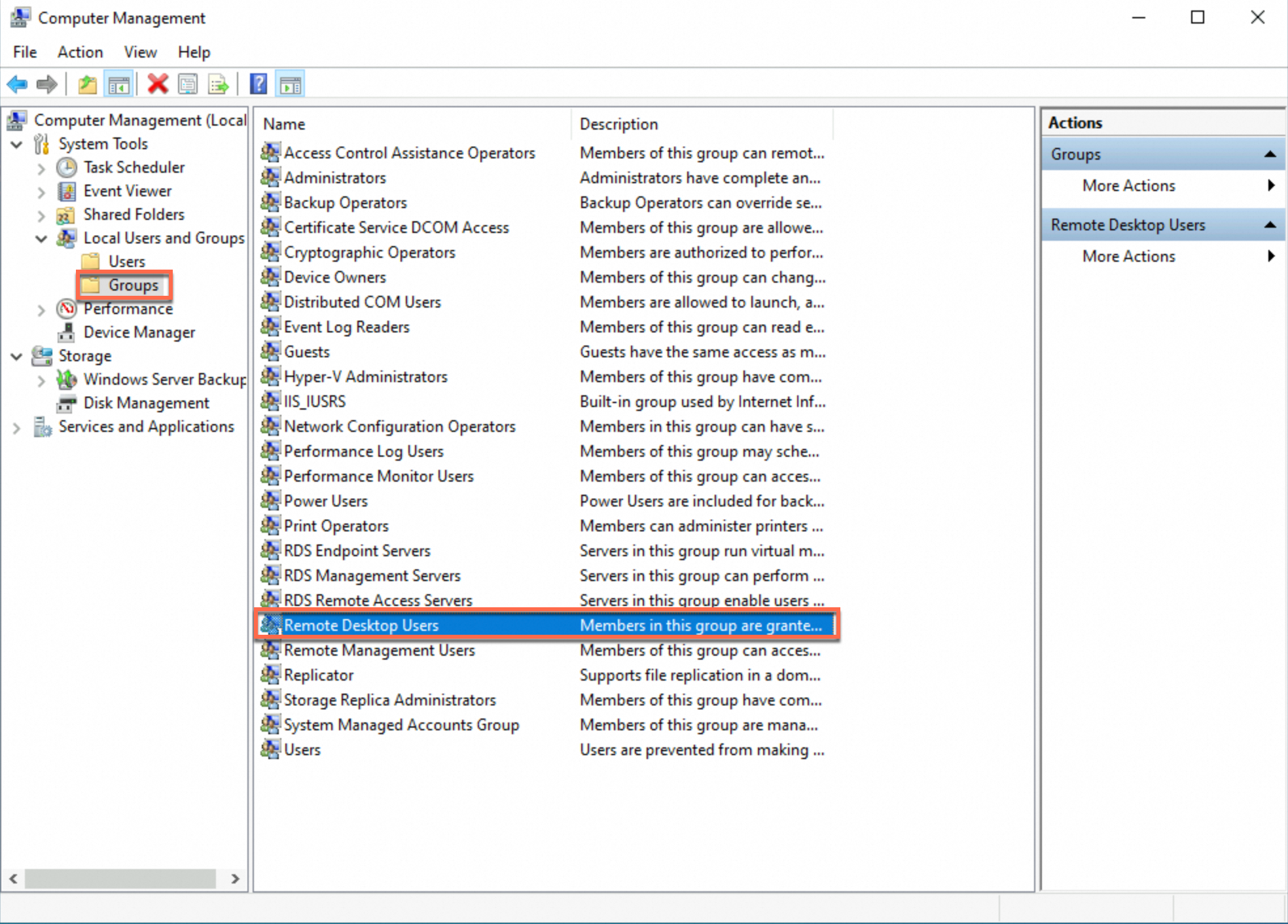
Follow the steps shown in the figure.
On the Remote Desktop Users Properties page, click Add.
Enter the username of the user created in Step 2 and click Check Names. The input box will automatically complete the full name of the user.
Click OK. On the Remote Desktop Users Properties page, click Apply and then OK. The user is added to the group.
(Verification) Remotely log on to the ECS instance as the new user.
FAQ
Q1: What is the default or initial username for an ECS instance?
Linux instances: The default username is
root. If you selectedecs-userduring creation, the username isecs-user.Windows instances: The default username is
Administrator.
Q2: What is the default or initial password for an ECS instance?
There is no default password.
For security purposes, Alibaba Cloud does not assign a default or initial password to ECS instances. If you did not set a password when creating the instance, you must reset a password.
Q3: How can I view the instance password?
Alibaba Cloud does not store your instance password and therefore cannot retrieve them for you.
Q4: How do I recover credentials if I forgot my username or password?
Forgot username: You can find your username using the reset password feature in the console. The username set during instance creation is displayed at the top of the Reset Instance Password dialog box.
Forgot password: Reset a password.
Q5: Why does the online password reset fail?
Most failures occur because security software on the instance blocks the password change command sent by Cloud Assistant. Use Offline password reset method instead.
Q6: How do I switch between the root and ecs-user accounts?
Switching from root to ecs-user
The option to use
ecs-useris only available when you create an instance from specific Linux images using the custom purchase method.After an instance is created, you cannot directly switch the default user to
ecs-user. As a workaround, you can create a new user namedecs-user, grant itsudopermissions, and then configure it for remote logon.Switching from ecs-user to root
Continue using
ecs-userand execute privileged commands withsudoinstead of logging in directly as therootuser.If you must switch to therootuser within a logged-in session, log in asecs-userand run thesudo sucommand.
Console features such as offline password reset and binding key pairs only apply to the username that was set when the instance was created.
Q7: How can I enable both SSH key pair and password authentication for a Linux instance?
You can configure this by modifying the SSH service's /etc/ssh/sshd_config file.
Enable SSH key pair authentication (recommended, more secure): This is controlled by the
PubkeyAuthenticationoption. Set its value toyesto enable key pair authentication. Restart the SSH service for the change to take effect.Enable SSH password authentication (not recommended, less secure): This is controlled by the
PasswordAuthenticationoption. Set its value toyesto enable password authentication. Restart the SSH service for the change to take effect.
Q8: How do I set the ECS logon username when creating an instance using Terraform?
The default username for an ECS instance is determined by its image. For example, the default username is root for Linux and Administrator for Windows. When you Create and use an ECS instance using Terraform, you can configure the instance to log on as a non-root user using the login_as_non_root parameter in the image_options block.
Parameter:
login_as_non_root(Boolean value).Method: Set this parameter to
true.Result: The instance logon username is set to
ecs-user.
