In Windows, you can view network traffic metrics by using tools, such as Task Manager, Resource Monitor, or Wireshark. This topic describes how to use these tools to monitor the network traffic loads of a Windows Elastic Compute Service (ECS) instance and troubleshoot and resolve the high network bandwidth utilization issue.
Problem description
When you use a Windows ECS instance, the following issues may occur:
Slow service responses or timeout errors.
High network bandwidth utilization is displayed in the ECS console. Network bandwidth utilization that exceeds 80% is considered high.
Alerts are generated indicating that the network bandwidth utilization exceeds the specified threshold.
Causes
The preceding issue may occur due to the following reasons:
Frequent access to services causes high bandwidth consumption.
Network traffic is triggered by viruses or Trojans.
NoteThird-party malicious programs disguise themselves as svchost.exe or tcpsvcs.exe in the operating system, causing high bandwidth usage for these processes.
Windows built-in services, such as Windows Update services, generate high network traffic.
Troubleshoot the issue
Use Resource Monitor to view network metrics
You can use various tools to identify the high bandwidth utilization issue on Windows instances, including Task Manager, Resource Monitor, Performance Monitor, and Process Explorer. You can also use Wireshark to capture network packets for further analysis.
In Windows Server 2008 and later versions, the built-in Resource Monitor tool is used to monitor bandwidth.
In the search box on the taskbar, enter Resource Monitor and then press the
Enterkey.In the Resource Monitor dialog box, view the processes that have high bandwidth utilization on the Network tab.
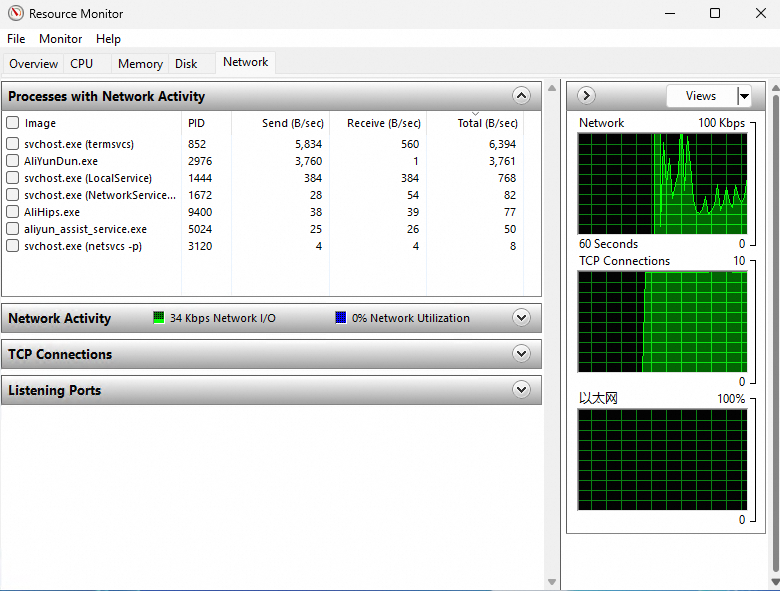 Note
NoteTo view detailed information about a process, use Task Manager. On the Processes tab of Task Manager, find the abnormal process that you identified in Resource Monitor. Right-click the process name, select Properties, Go to details, or Open file location, and then view process information to determine whether the process belongs to a malicious program.
(Optional) Use TCPView to view network connection information
If you do not find processes with high bandwidth utilization in Resource Monitor but the instance bandwidth utilization remains high, external services may access the instance. In this case, use Microsoft TCPView for further analysis. This tool displays a detailed list of all TCP and UDP network connections on the instance, including local and remote IP addresses and the status of TCP connections.
Download and decompress the TCPView tool.
Download the TCPView tool from the Microsoft website and decompress the downloaded package.
Double-click to open TCPView and view the network bandwidth details.
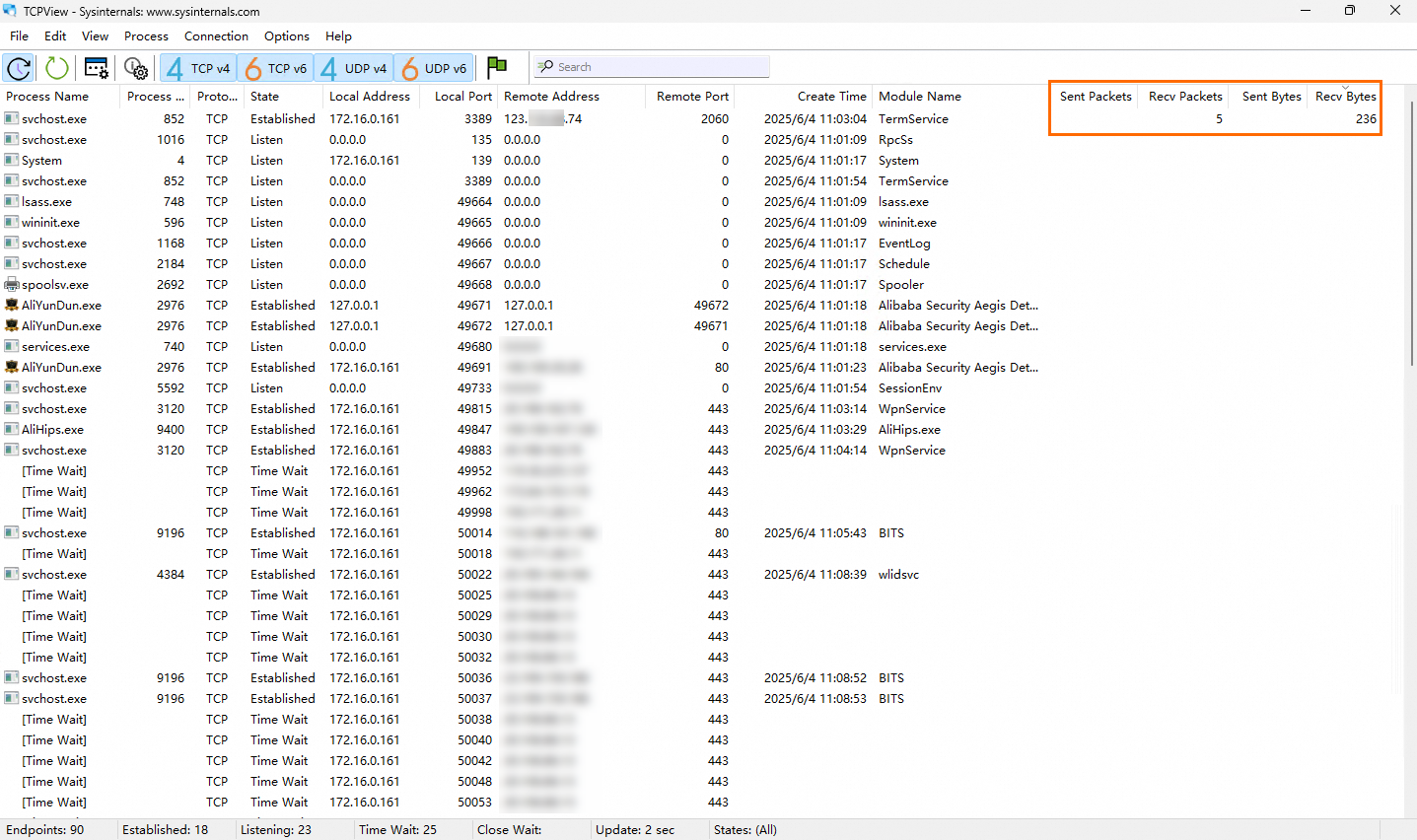
As shown in the preceding figure, the remote IP address 123.xxx.xxx.74 transmits data to the instance and occupies excessive network bandwidth resources.
(Optional) Use Wireshark to analyze traffic
To perform in-depth analysis of traffic data packets, use Wireshark to capture and analyze data packets.
Install and start the Wireshark tool.
Visit the Wireshark official website, obtain the Wireshark installation package, and then install the Wireshark tool.
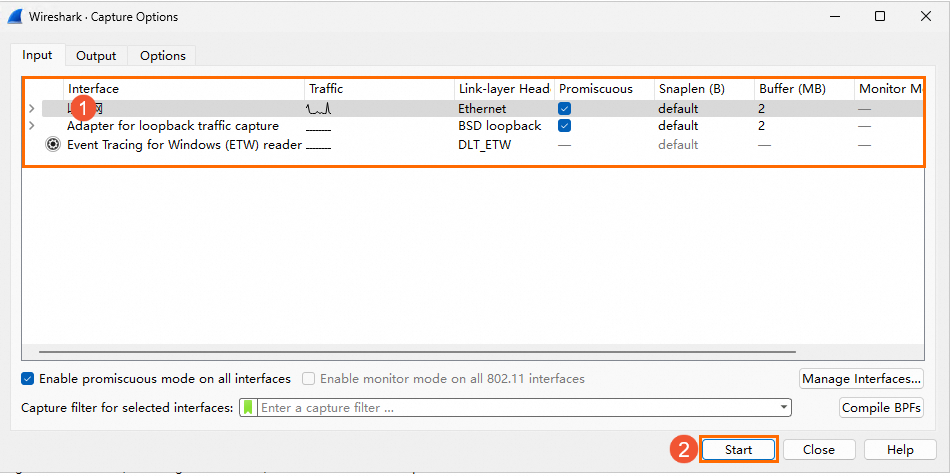
Choose Capture> Options.
On the Wireshark Capture Options page, select a network interface for packet capture based on the interface name or IP address and click Start.
In the Wireshark toolbar, choose Statistics > Conversations.
On the Conversations page, view all network communication information. The traffic details and communication between the two endpoints are provided from the data link layer, IP layer, and TCP layer. By capturing network packets for a period of time, you can analyze which connections and ports have high traffic.
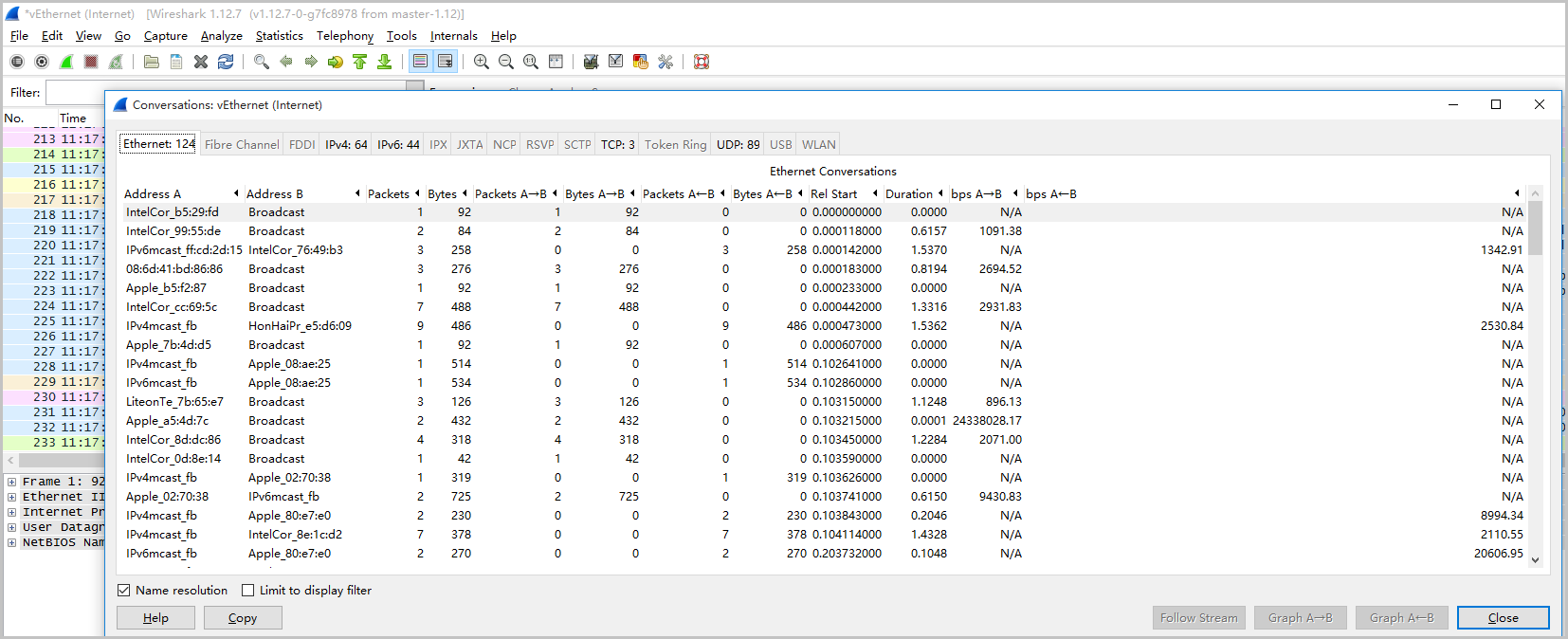
You can further analyze network packets by capturing packets. For more information, see Use the Wireshark tool in Windows instances.
Resolve the issue
The following table describes the common causes of high network bandwidth utilization issues and their solutions.
Problem description | Cause | Solution |
An abnormal user program or process occupies excessive network resources for an extended period, or unauthorized IP addresses maliciously access services, resulting in high network loads. | The program is an abnormal program or process that occupies excessive network resources at runtime. |
|
A normal user program or process occupies excessive network resources for an extended period, or specific IP addresses access services, resulting in high network loads. | The program is a normal business program or process that occupies excessive network resources at runtime. | Services that are frequently accessed and Windows built-in services, such as update services, may cause high network traffic or high CPU load. If the instance has a network performance bottleneck, resolve the issue by using one of the following methods based on your business scenario:
|
A single business program or process occasionally occupies excessive network resources for a short period. | The business program needs to be optimized for special business scenarios, such as large file uploads or downloads. | Optimize the business program. Optimize business code and modify application parameters, such as the number of connections, cache configuration, and Web and database configuration parameters. |
No program or process occupies network resources, but the overall network load is high. | Network resources required for the normal operation of the instance's services exceed the instance's network bandwidth. | If the instance has a network performance bottleneck, upgrade the instance's bandwidth. Note If the instance bandwidth reached the upper limit and cannot meet the bandwidth requirements of the normal business, we recommend that you separate applications on different instances. For example, you can use RDS to host database services to reduce resource consumption and internal calls on the ECS instance. |
References
For information about how to troubleshoot and resolve high network bandwidth utilization in Linux systems, see Resolve high network bandwidth usage on a Linux instance
To collect network metrics in advance for anomaly analysis, you can use the atop utility. For more information, see Use the atop tool to monitor Linux metrics.