This topic describes how to use tags to manage the permissions of a RAM user. This topic also describes how to use tags to authenticate a RAM user.
Background information
Tags are used to identify and categorize cloud resources. Resource Access Management (RAM) manages the access and operation permissions of RAM users on cloud resources based on permission policies. You can use tags as conditions in RAM policies to implement fine-grained access control on resources.
The following figure shows how to use tags to manage the permissions of a RAM user.
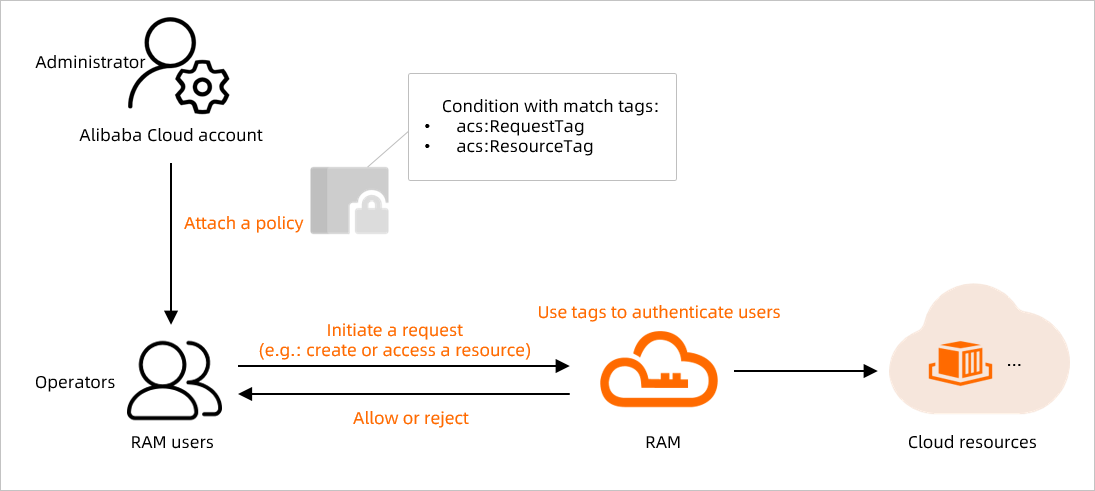
You can bind tags to the following Elastic Container Instance resources: elastic container instances, image caches, and virtual nodes. You can bind tags to the resources only when you create or update the resources. For more information, see Use tags to manage elastic container instances.
Configuration example
Scenario
The scenario in this topic is used to describe how to perform tag-based authentication.
For example, you want to grant a RAM user the permissions only on the Elastic Container Instance resources that have the env:test tag, as shown in the following figure: 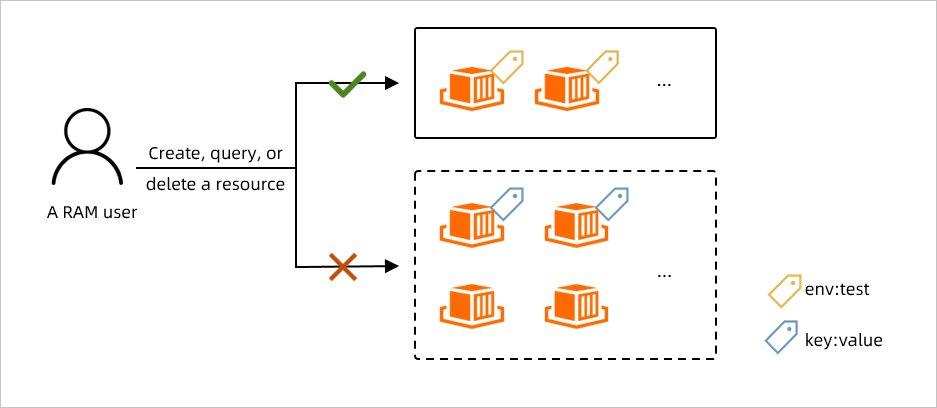
You have the following specific requirements:
Requirement 1: The RAM user can successfully create Elastic Container Instance resources only if the RAM user binds the
env:testtag to the resources.Requirement 2: The RAM user can operate only the Elastic Container Instance resources that are created by the RAM user. The resources must have the
env:testtag.Requirement 3: The RAM user can view only the Elastic Container Instance resources that are created by the RAM user. The resources must have the
env:testtag.
Step 1: Create a custom policy and attach the policy to the RAM user
Use your Alibaba Cloud account to log on to the RAM console.
In the left-side navigation pane, choose Permissions > Policies.
On the Policies page, click Create Policy.
Configure the parameters to create a custom policy.
Click the Import Policy tab.
In the dialog box that appears, select System Policy from the Policy Template drop-down list, enter AliyunECIFullAccess in the "Filter templates" search box, select the AliyunECIFullAccess policy, and then click Import.
AliyunECIFullAccess is the default policy for managing Elastic Container Instance resources. AliyunECIFullAccess contains the permissions to operate Elastic Container Instance resources, query resources such as security groups and virtual private clouds (VPCs), and create the service-linked role for Elastic Container Instance.
Click the JSON tab.
Modify the policy document in the code editor and then click Next to edit policy information.
NoteA policy contains a set of permissions. Each policy includes a version number and authorization statements. Each statement includes the following elements: Effect, Action, Resource, and Condition. The Condition element is optional. For more information, see Policy structure and syntax and Policy elements.
You can specify authentication tags in the
Conditionelement of a policy to restrict the operation permissions of the RAM user. The following table describes the conditions that can be specified in a policy.Tag-based authentication condition
Description
acs:RequestTagSpecifies that an API request must contain a tag.
You can use the
acs:RequestTagcondition in an API request only if the API request contains tag-related parameters.acs:ResourceTagSpecifies that the resource specified in an API request must have a tag.
You can use the
acs:ResourceTagcondition in an API request only if the API request contains resource ID-related parameters.NoteWhen you configure a policy, you can use the
acs:RequestTagoracs:ResourceTagcondition based on whether the API request supports tags or requires resource IDs. For more information, see Authenticate a RAM user when the RAM user initiates an API request.You can configure the following policies to meet your business requirements for the preceding scenario:
Requirement
Policy
The RAM user can successfully create Elastic Container Instance resources only if the RAM user binds the
env:testtag to the resources.{ "Effect": "Allow", "Action": "eci:Create*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/env": "test" } } }The RAM user can operate only the Elastic Container Instance resources that have the env:test tag.
{ "Effect": "Allow", "Action": "eci:*", "Resource": "*", "Condition": { "StringEquals": { "acs:ResourceTag/env": "test" } } }The RAM user can view only the Elastic Container Instance resources that have the env:test tag.
{ "Effect": "Allow", "Action": "eci:Describe*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/env": "test" } } }The following example shows a complete policy that contains the permissions provided by AliyunECIFullAccess.
{ "Version": "1", "Statement": [{ "Effect": "Allow", "Action": "eci:Create*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/env": "test" } } }, { "Effect": "Allow", "Action": "eci:*", "Resource": "*", "Condition": { "StringEquals": { "acs:ResourceTag/env": "test" } } }, { "Effect": "Allow", "Action": "eci:Describe*", "Resource": "*", "Condition": { "StringEquals": { "acs:RequestTag/env": "test" } } }, { "Action": [ "ecs:DescribeSecurityGroups" ], "Resource": "*", "Effect": "Allow" }, { "Action": [ "vpc:DescribeVSwitches", "vpc:DescribeVpcs", "vpc:DescribeEipAddresses" ], "Resource": "*", "Effect": "Allow" }, { "Action": "ram:CreateServiceLinkedRole", "Resource": "*", "Effect": "Allow", "Condition": { "StringEquals": { "ram:ServiceName": [ "eci.aliyuncs.com", "vnode.eci.aliyuncs.com" ] } } } ] }NoteIf you want the RAM user to operate Elastic Container Instance resources by calling API operations, you can grant the RAM user the permissions provided by the AliyunECIFullAccess policy. If you want the RAM user to operate Elastic Container Instance resources by using the Elastic Container Instance console, you must grant the RAM user the permissions provided by the AliyunECIFullAccess policy and the permissions provided by other policies. For more information, see Grant permissions to RAM users.
Enter a name for the policy and click OK.
Attach the custom policy to the RAM user.
In the left-side navigation pane, choose Identities > Users.
Create a RAM user.
Create a RAM user based on your management requirements. For more information, see Create a RAM user. If you already created a RAM user, skip this step.
Grant permissions to the RAM user.
Attach the custom policy that you created to the RAM user. For more information, see Grant permissions to a RAM user.
Step 2: Check whether the policy is in effect
Log on to the OpenAPI Explorer console as a RAM user.
Check whether the policy is in effect.
An elastic container instance is used in the following tests:
Create an elastic container instance
If you bind the
env:testtag to an instance when you create the instance, the instance can be created.If you do not bind the env:test tag to an instance or you bind another tag to the instance when you create the instance, the instance cannot be created. The system prompts that you do not have the permissions to create the instance.
Delete an elastic container instance
If the instance that you want to delete has the
env:testtag, the instance can be deleted.If the instance that you want to delete does not have the
env:testtag, the instance cannot be deleted. The system prompts that you do not have the permissions to delete the instance.
Query an elastic container instance
If you specify an instance that has the
env:testtag but you do not specify the tag in the request, the specified instance is queried.If you specify an instance that does not have the
env:testtag in the request, the query result is empty.If you do not specify an instance but you specify the
env:testtag in the request, all instances that have theenv:testtag are queried.If no instances and tags are specified, the query result is empty.
Authenticate a RAM user when the RAM user initiates an API request
The following table describes how the system authenticates a RAM user after a policy that contains an authentication tag is attached to the RAM user and then the RAM user initiates an API request.
API operation | Authentication description |
API operations that are used to create resources, such as CreateContainerGroup and CreateImageCache | You do not need to specify resource IDs in the API requests. When no resource IDs are specified in the API requests, the requests are matched against the
|
API operations that are used to query resources, such as DescribeContainerGroups and DescribeImageCaches | You must specify resource IDs or tags in the API requests based on the requirements of the API operations. The requests are matched against the
Note For API operations that are used to query resources, the system returns an empty result and does not report an error if the authentication fails. |
API operations that are used to update resources, such as UpdateContainerGroup and UpdateImageCache | You must specify resource IDs in the API requests. The requests are matched against the
Note If a tag is updated, the RAM user must have the permissions of the original tag and the new tag. You must attach the following custom policies to the RAM user: a policy that contains the original tag-based authentication condition and a policy that contains the new tag-based authentication condition. |
Other API operations such as RestartContainerGroup and ExecContainerCommand | You must specify resource IDs in the API requests. The requests are matched against the
|