After you activate Data Security Center (DSC), authorize it to detect sensitive data in your databases and OSS and SLS assets, and enable data security audit. You can then view information on the DSC console. This information includes the authorization status of data assets, sensitive data identification results, risk trends from security baseline checks, and audit alert statistics.
Data assets
Currently, DSC supports data detection in relational databases, non-relational databases, big data platforms, unstructured data sources, and self-managed databases. For more information about the supported data asset types, see Supported data asset types.
To protect your privacy, DSC performs only necessary sensitive data processing, such as tagging, static data masking, and auditing. DSC does not save your data files.
View statistics
On the Overview page in the Data Security Center console, you can view the following statistics:
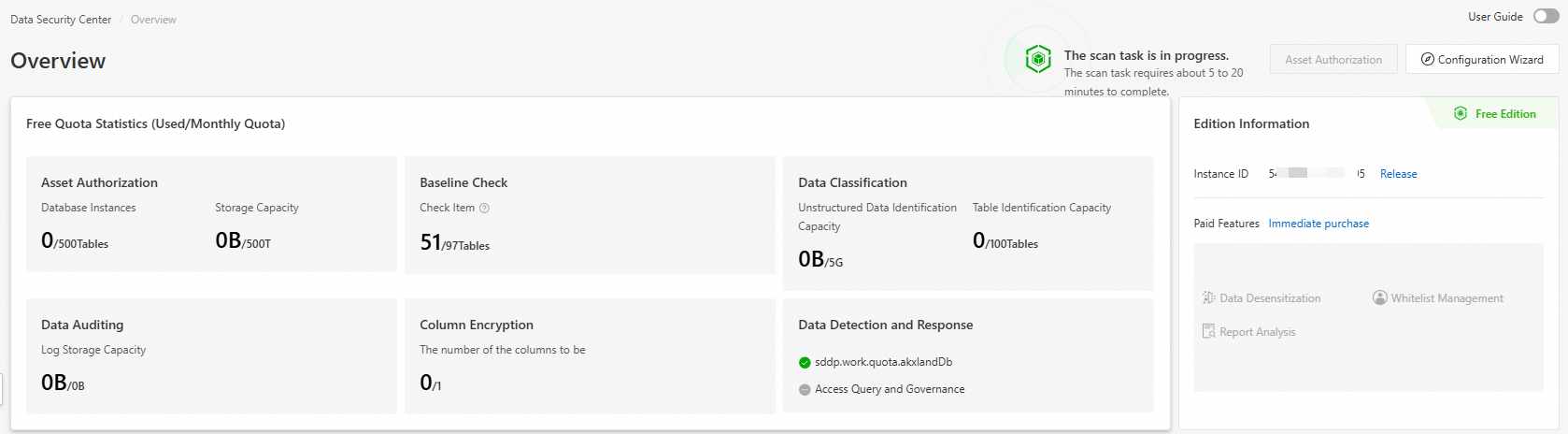
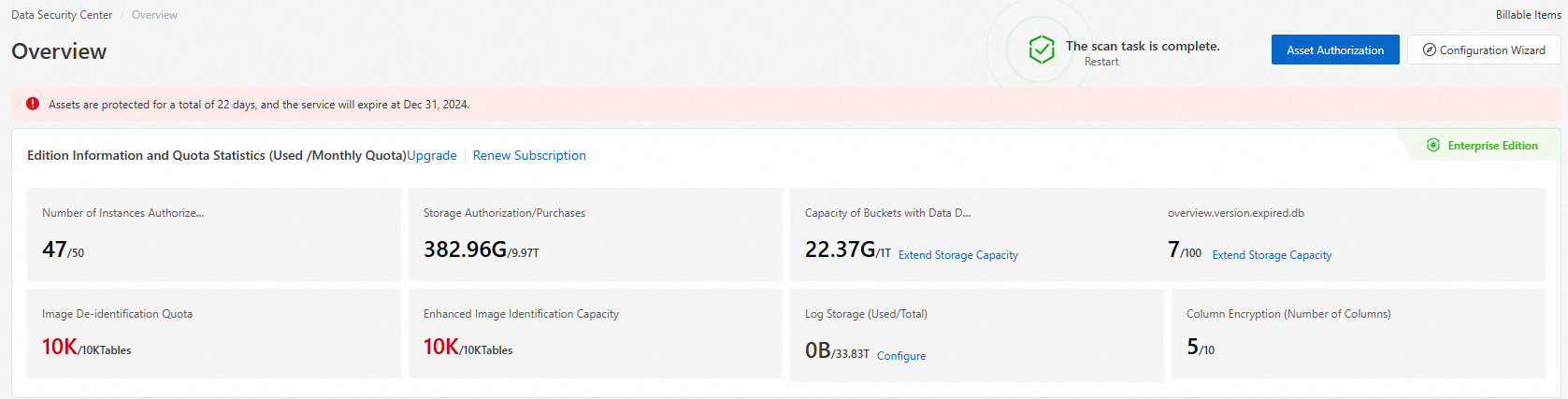
Edition information and quota statistics
In the Version and Quota Statistics (Used/Monthly Quota) section, you can view your current edition and resource usage. This includes the remaining days of protection, the number of authorized databases, and storage usage.
Free Edition
You cannot upgrade or renew DSC Free Edition. If the free resource specifications cannot meet your business requirements, we recommend that you purchase DSC to ensure continuous data security. For more information, see Purchase DSC.
Paid edition
To upgrade or renew your instance, click Upgrade or Renew Subscription. For more information, see Upgrade an instance and Renew subscription DSC.
Asset configuration statistics
In the Asset allocation statistics section, you can view statistics about your data assets, including their authorization and data identification status.
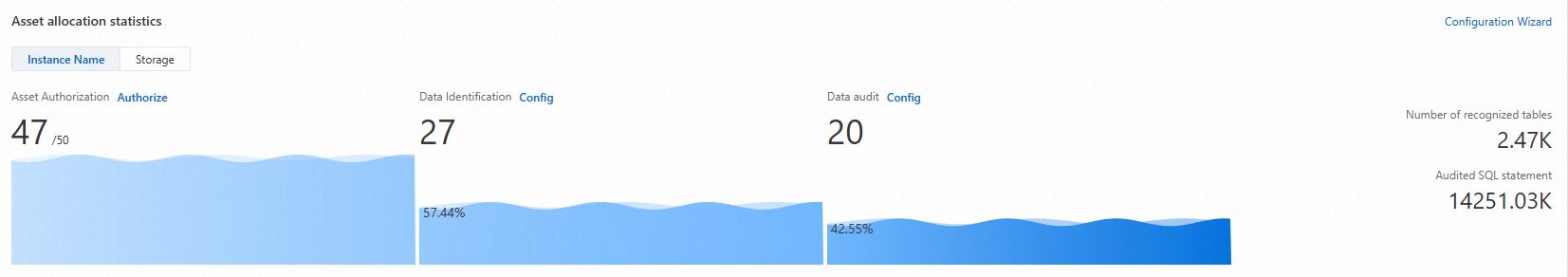
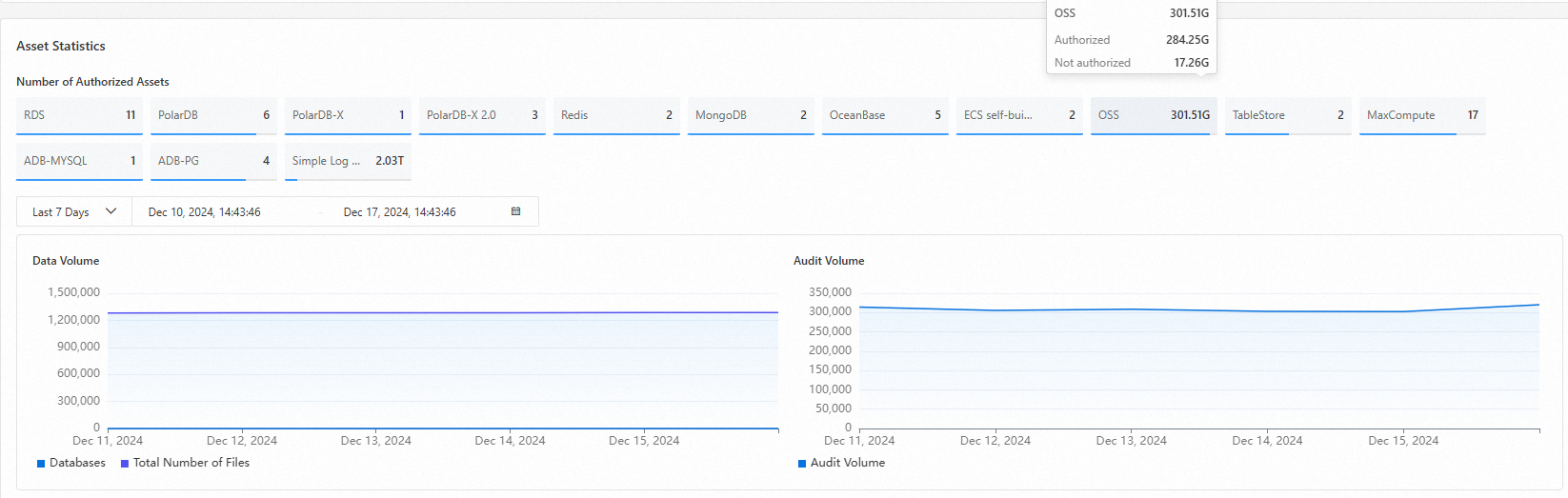
Authorized asset statistics
In the Asset Statistics section, you can view the number of authorized assets. You can also view the trends of the total number of assets and the audit volume over the last 12 hours, 1 day, 7 days, or 30 days.
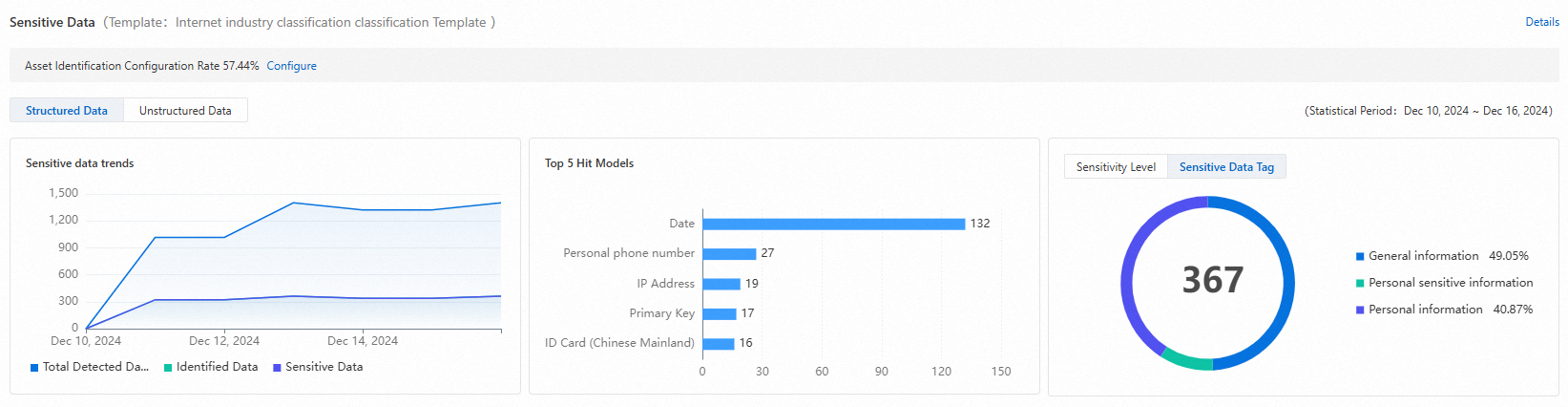
Sensitive data identification statistics
In the Sensitive Data section, you can view statistics about the identification results for structured and unstructured data in scanned data assets.
DSC identifies sensitive files and data based on configured sensitive data identification templates. Sensitive data identification templates are categorized into built-in and custom templates. DSC uses these templates to identify sensitive data tables, fields, and files, and classify them by sensitivity level. For more information, see View and configure identification templates.
The Overview page displays statistics from scans that use the New National Standard Template.
In the upper-right corner of the Sensitive Data section, click Details to navigate to the page. On this page, you can view the detailed identification results for sensitive data. For more information, see View sensitive data identification results.
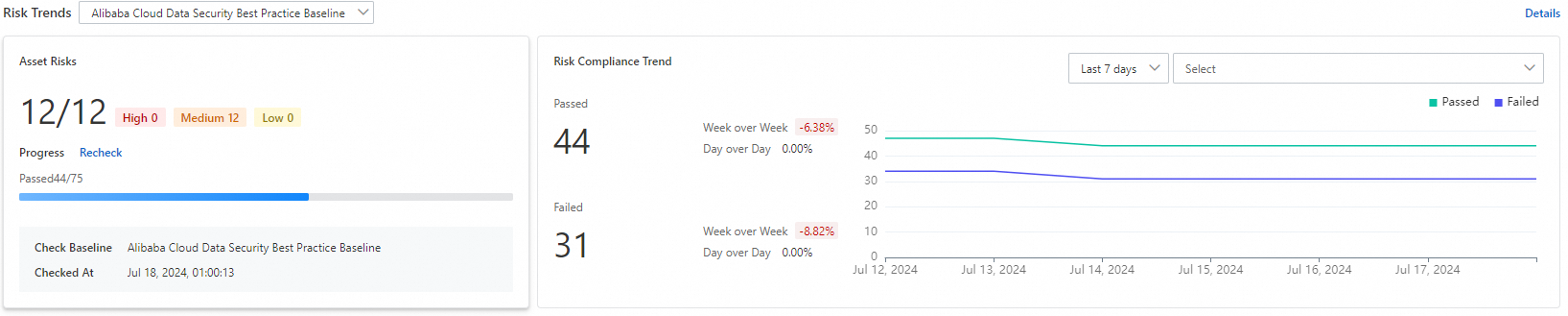
Risk trend statistics
In the Risk Trends section, you can view the risk trends from security baseline checks over the last 7 or 30 days.
Click Recheck to run a configuration risk check on all authorized assets. Refresh the page later to view the results.
In the upper-right corner of the Risk Trends section, click Details to navigate to the page. On this page, you can view the detailed results of the security baseline checks.
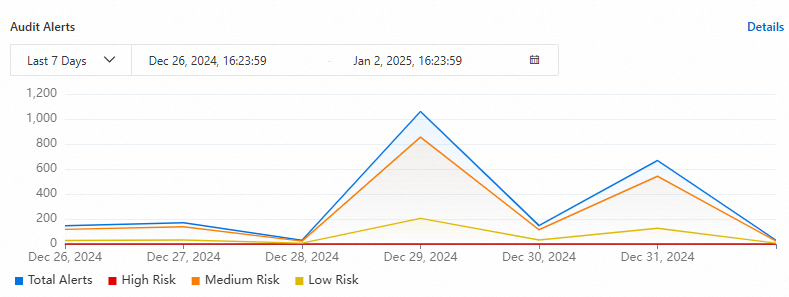
Threat trend statistics
In the Threat Trends section, you can view the trend in the number of data audit alerts over the last 12 hours, 1 day, 7 days, or 30 days.
In the Threat Trends section, click Details for Audit Alerts to go to the page and view the corresponding alert details.