Data Security Center (DSC) dynamically checks the configurations in your data assets. For example, DSC checks each configuration item in your databases on Alibaba Cloud, such as the authentication, access control, encryption, backup, and recovery configurations. The security baseline check feature of DSC consists of check policies and check items. The security baseline check feature helps you continuously monitor the configurations in your databases on Alibaba Cloud. This topic introduces the security baseline check feature and describes how to use this feature.
Prerequisites
DSC Free Edition is activated or a paid edition of DSC is purchased. DSC Free Edition supports specific baseline check items. The paid editions support all baseline check items. For more information, see DSC Free Edition and Purchase DSC.
DSC is authorized to access data assets. For more information, see Asset authorization.
About the security baseline check feature
In compliance with the Information Security Technology - Data Security Capability Maturity Model (GB/T 37988-2019), DSC supports the following security baselines: the China Personal Information Protection Law (PIPL) and the best practices of Alibaba Cloud for data security. The preceding security baselines are intended for complex database environments in the cloud and different types of structured and unstructured data. DSC provides seven types of check policies and check items, an overview and a list of configuration risks by type and level, and suggestions on how to handle the detected configuration risks. The actual check items that are displayed on the Policies tab of the page shall prevail. We recommend that you handle configuration risks at the earliest opportunity based on the suggestions. This helps enhance the security of your data assets and protect the assets against attacks.
Security baselines
The China PIPL: provides full-lifecycle security monitoring for personal information and data assets based on the PIPL.
You can perform baseline checks on the database instances and Object Storage Service (OSS) buckets that contain personal information or sensitive personal information scanned by data identification tasks.
Best practices of Alibaba Cloud for data security: provide full-lifecycle security monitoring for data assets based on the best practices of Alibaba Cloud for data security.
You can perform baseline checks on the database instances and OSS buckets that DSC is authorized to access.
Check policies
Policy | Description |
Log auditing and monitoring | Full-lifecycle recording and monitoring of data processing help ensure the auditability and traceability of the data processing procedure. Log auditing or log storage is recommended for data assets. This policy checks whether log auditing or log storage is enabled for your databases. |
Identity and permission management | The least privilege principle shall apply to data access and usage. Only authorized users can access your data assets. This policy checks whether permission control is implemented on your databases, for example, whether standard accounts are authorized to log on to your databases to perform routine tasks. |
Sensitive data protection | Strict access control is required for sensitive data assets to prevent data leaks. This policy checks whether your databases allow public reads and writes and whether access control is implemented on your projects that contain sensitive data. Note This policy takes effect only on database instances and OSS buckets that contain personal information or sensitive personal information scanned by data identification tasks. If you do not perform data scanning and detection on the database instances and OSS buckets, or the scan result does not contain personal information or sensitive personal information, the check items of this policy pass the baseline check. |
Access control | Access to your data assets needs to be restricted to authorized users. Public exposure of your data assets must be avoided. This policy checks whether your databases are publicly accessible. |
Data backup and recovery: | Backing up and restoring your data assets on a regular basis are beneficial to the availability and redundancy of your data assets. This policy checks whether data backup is enabled for your databases. |
Data storage security | Security measures for data storage, such as encryption, are critical to the confidentiality and integrity of the stored data. This policy checks whether encryption is enabled for your databases. |
Data transmission encryption | Security measures for data transmission, such as encryption, are critical to the security of the transmitted data. This policy checks whether data transmission is encrypted for your databases. |
Supported data types
The security baseline check feature can scan for configuration risks only for Alibaba Cloud databases that are connected to DSC. The following Alibaba Cloud database services are supported by the security baseline check feature.
Category | Database engine |
Relational database | RDS MySQL |
RDS SQL Server | |
RDS PostgreSQL | |
RDS MariaDB | |
ApsaraDB for OceanBase in MySQL mode | |
ApsaraDB for OceanBase in Oracle mode | |
PolarDB-X 1.0 | |
PolarDB for MySQL | |
PolarDB for PostgreSQL | |
PolarDB for Oracle | |
Non-relational database | MongoDB |
Redis | |
Big data | TableStore |
MaxCompute | |
AnalyticDB for MySQL | |
AnalyticDB for PostgreSQL | |
Unstructured database | OSS |
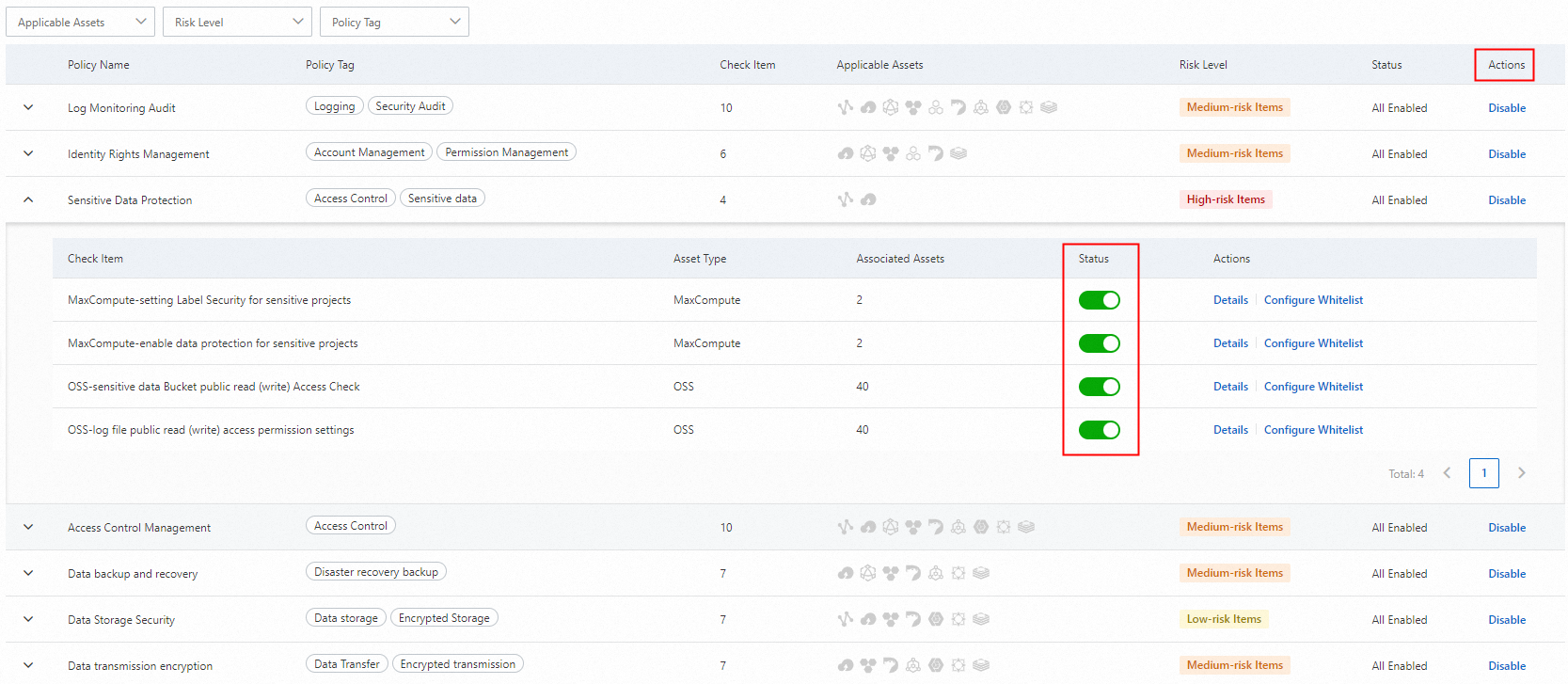
Enable or disable the check items in check policies
By default, all check items in the check policies are enabled in the DSC console. You can enable or disable check items based on your business requirements.
- Log on to the DSC console.
In the left-side navigation pane, choose .
On the Alibaba Cloud Data Security Best Practices or PIPL-based Security Baseline Check tab of the Policies tab, view the baseline check policies.
In the check policy list, select a check item and turn on or off the switch in the Status column to enable or disable the check item.
You can also enable or disable a check policy to enable or disable all check items of the policy.
Perform checks
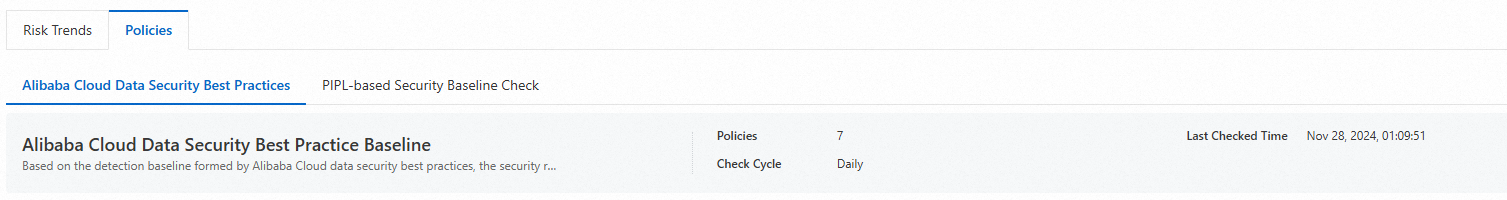
View the time when the last check was performed.
On the Policies tab, click the Alibaba Cloud Data Security Best Practices or PIPL-based Security Baseline Check tab to view the value of the Last Checked Time parameter.
Automatically perform checks
By default, DSC automatically performs a check on the databases connected to DSC at approximately 01:00:00 (UTC+8) every day.
Manually perform checks
When a new data asset is connected to DSC or the database configurations are modified, you can click Re-check in the DSC console to immediately perform a check. A re-check takes about 10 minutes.
In the left-side navigation pane, choose .
On the Risk Trends tab, click the Alerts tab, find the required policy, and click Details in the Actions column.
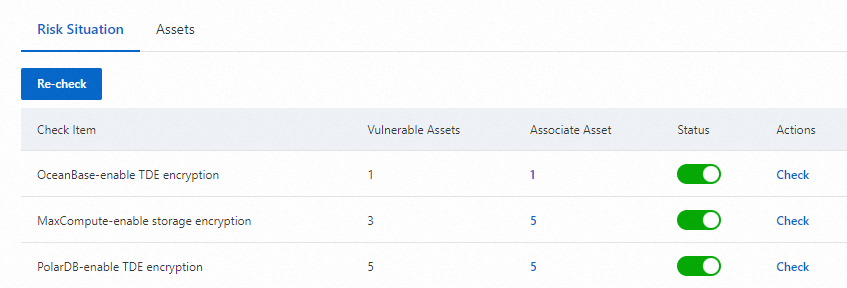
On the Risk Situation or Assets tab, click Re-check to perform a re-check based on check items or data assets.
View the trend of asset risks
DSC integrates security baseline checks and sensitive data detection results to provide charts that display the security risks in data assets of different sensitivity levels, the security risks in personal and private data, the risk scan progress, and sensitive data detection results. The information helps you learn about the trend of your asset risks.
In the left-side navigation pane, choose .
On the Risk Trends tab, select a baseline type from the drop-down list on the right.
On the Asset Risks tab, view the following information:
Data Asset Sensitivity Situation
A column chart that displays the numbers of detected high-risk assets, medium-risk assets, and low-risk assets.
Security Situation of Sensitive Data
A column chart that displays the numbers of detected high-risk assets, medium-risk assets, and low-risk assets of sensitive personal information, personal information, and general information.
Risk governance progress
The number displayed in the Progress column indicates the number of passed check items and the total number of check items for each asset. For example, if 2/3 is displayed for an asset, it means that a total of 3 check items apply to the asset and the asset has passed 2 check items. If Completed is displayed in the Progress column, it means that the asset has passed all applied check items.
The Risk Level column displays the risk levels of failed check items. If multiple levels of risks are detected in a failed check item, only risks of the highest level are displayed.
Handle asset risks
DSC allows you to view and handle asset risks from different perspectives. You can view information about asset risks from different perspectives on different pages. The details of risks on different pages are consistent. You can choose a perspective based on your business requirements.
We recommend that you handle configuration risks at the earliest opportunity based on the suggestions. This helps prevent data leaks and security events.
From the asset perspective
To view risks from the asset perspective, go to the DSC console, choose in the left-side navigation pane, and then click the Asset Risks tab on the Risk Trends tab. You can view the list of datasets that can be scanned by DSC. This tab also provides entries to the scan result and risk handling.
In the left-side navigation pane, choose .
On the Asset Risks tab of the Risk Trends tab, handle the configuration risks.
Handle risks
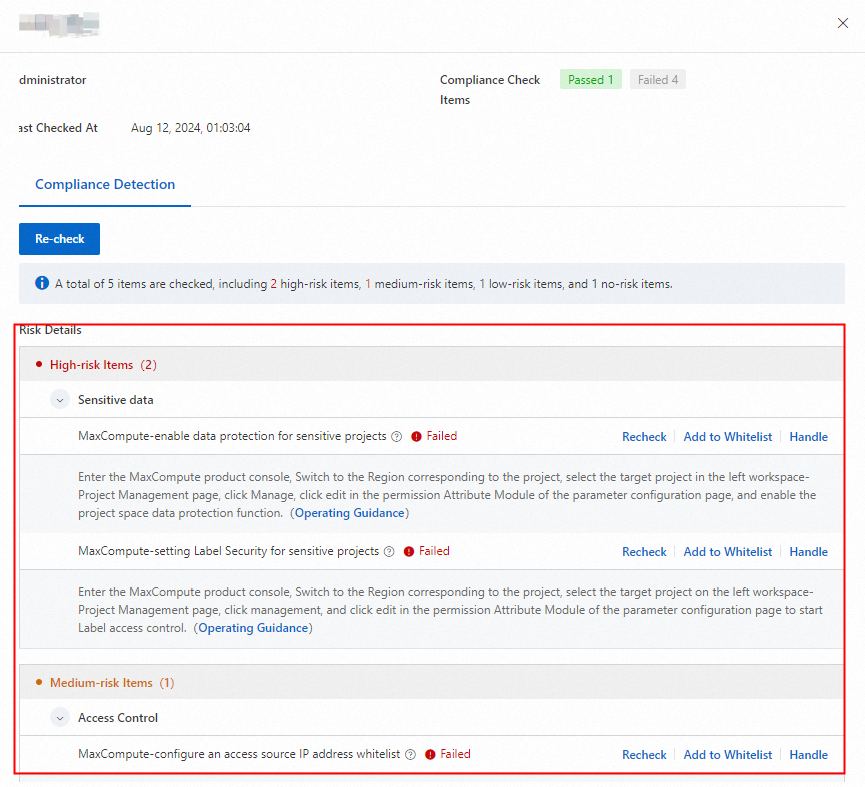
DSC provides suggestions for risk handling. You need to manually handle the detected risks. Select a data asset and click Handle in the Actions column to view the failed check items and the suggestions for risk handling.
In the Risk Details section, click Handle to handle the risk on the page that appears.
Add an asset to the scan whitelist
If security baseline checks are not required for a database according to the evaluation result of the security engineer, you can click Add to Whitelist in the Actions column to add all check items that apply to the database to the scan whitelist. After you add the asset to the whitelist, Completed is displayed in the Progress column.
Add a specific check item that applies to a data asset to the whitelist
If a specific check item is not required for a database according to the evaluation result of the security engineer, click Handle in the Actions column. In the Risk Governance panel, select the check item and click Add to Whitelist on the right side of the check item. After you add the check item to the whitelist, Added to Whitelist is displayed for the check item.
From the check policy perspective
To view risks from the check policy perspective, go to the DSC console, choose in the left-side navigation pane, and then click the Alerts tab on the Risk Trends tab. You can view various check policies on the tab. On the details page of a check policy, you can view the check items of the check policy and the assets to which the check items apply.
In the left-side navigation pane, choose .
On the Alerts tab of the Risk Trends tab, view the check policy list.
The Number of alarms column displays the number of assets that fail the check items of the check policy.
The Associate Asset column displays the number of assets to which the check items of the check policy apply. Each asset is counted multiple times when multiple check items apply to the asset.
Select a check policy and click Details in the Actions column.
On the Details page, you can view information on the Risk Situation tab and the Assets tab.
The Risk Situation tab displays all check items in the check policy and details of each check item, including the number of risky assets, the number of assets to which the check item applies, and the status of the check item. If you want to perform a re-check based on a check item, click Check in the Actions column.
The Assets tab displays the assets to which all check items of the check policy apply. You can rescan an asset based on a check item, add an asset to the whitelist, or remove an asset from the whitelist. You can also click Handle to handle risks.
From the check item perspective
To view risks from the check policy perspective, go to the DSC console, choose in the left-side navigation pane, and then click the Policies tab. You can perform the following steps to view the details of a check item.
Select the check policy that you want to view and click the
 icon to view the check items of the check policy.
icon to view the check items of the check policy. Select the check item that you want to view and click Details or Configure Whitelist in the Actions column to view and manage the assets to which the check item applies in the Details panel.
You can perform the following operations:
After you verify that the check item is not required for an asset, you can click Add to Whitelist in the Actions column to add the asset to the whitelist of the check item.
Select an asset and click Handle in the Actions column to handle the risks in the asset.
After you handle the risks, click Verification in the Actions column to check whether the risks are handled.