Data Security Center (DSC) assesses the security configuration compliance of your buckets. It checks whether configurations, such as access control list (ACL) and encryption policies, are in place. DSC provides suggestions for handling any detected configuration risks. You can follow these suggestions to strengthen the security of data assets in your Object Storage Service (OSS) buckets.
Solution overview
DSC supports the following baseline risk check items for OSS buckets:
Policy Name | Check Item | Description |
Data Storage Security | OSS-enable Bucket server-side encryption | Checks whether server-side encryption is enabled for an OSS bucket. Configure data storage with security measures such as encryption to ensure data confidentiality and integrity. |
Data backup and recovery | OSS-enable Bucket version control | Checks whether versioning is enabled for an OSS bucket. Establish a versioning and recovery mechanism to manage data redundancy and protect data availability. |
Access Control Management | OSS-configure an access source IP address whitelist | Checks whether an OSS bucket is publicly exposed. Restrict data access and use by source based on business needs to avoid public exposure of data assets. |
Data transmission encryption | OSS-enable secure encrypted transmission | Checks whether encrypted transmission is enabled for OSS files during transfer. Use security measures such as encryption for data transmission activities to ensure security during the process. |
Log Monitoring Audit | OSS-enable log storage | Checks whether log storage is enabled for OSS files. The entire data processing lifecycle should have recording and monitoring capabilities to ensure traceability. Enable features such as log storage for OSS files. |
Identity Rights Management | OSS-anonymous account "read/write/full control" permission configuration | Checks whether OSS file permission management is reasonable. For example, it checks if public-read-write permissions are configured, which would allow changes to the content of stored files. Base data access and use on the principle of least privilege. Define access permissions for relevant personnel to prevent unauthorized access. |
Sensitive Data Protection | OSS-log file public read (write) access permission settings, OSS-sensitive data Bucket public read (write) Access Check | Checks for data breach risks in OSS log files, such as public-read-write permissions. It also checks whether access control is enabled for projects that contain sensitive data. In this example, sensitive data detection is not performed on the OSS bucket. The baseline check is performed directly. Therefore, the OSS-sensitive data Bucket public read (write) Access Check check item passes by default. |
You can complete the baseline security checks and handle the risks in four steps:
Create an OSS bucket: Create an OSS bucket.
Add the OSS bucket to DSC: Add the bucket in the DSC console and enable configuration risk checks.
Manually run a baseline security check: By default, DSC runs a security baseline check on connected data assets at approximately 01:00 every day. To view the baseline check results immediately, you must run the check policy manually.
View and handle security risks: View the check results and handle any detected configuration risks.
Prerequisites
Activate the Free Edition of Data Security Center and grant DSC the necessary permissions to access other Alibaba Cloud resources.
The Free Edition of Data Security Center includes the baseline check feature. It supports the check items in the Alibaba Cloud Data Security Best Practices and provides 500 TB of free OSS protection per month. For this example, you only need to activate the Free Edition of DSC.
Object Storage Service (OSS) has been activated for the current account.
Step 1: Create an OSS bucket
In the OSS console, go to the Buckets page and click Create Bucket.
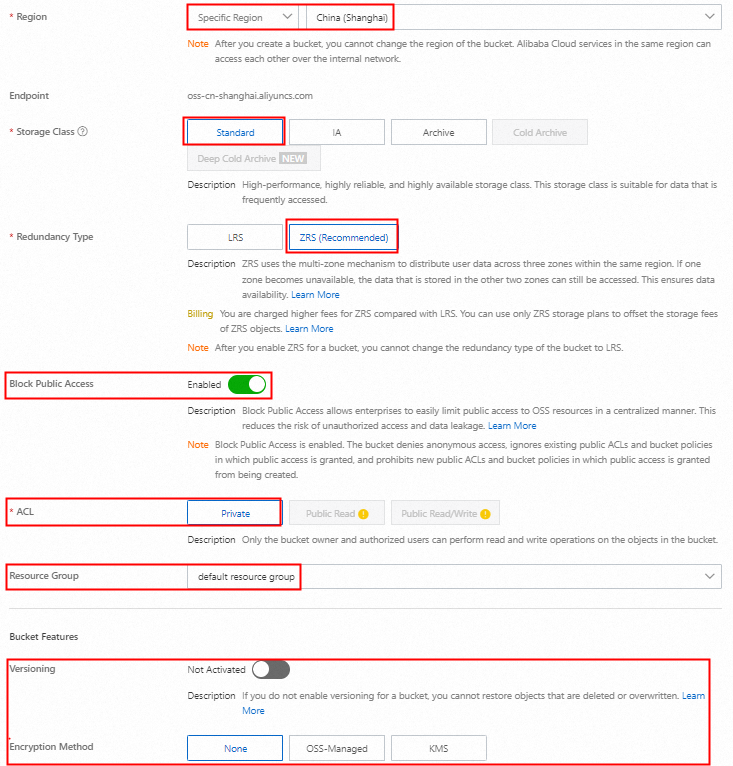
In the Create Bucket panel, configure the required parameters, use the default settings for the other parameters, and then click Create.
Step 2: Add the OSS bucket to DSC
Log on to the Data Security Center console.
In the navigation pane on the left, choose Asset Center.
Using the new Asset Center as an example, click OSS in the Unstructured Data area, and then click Asset synchronization.

After the asset synchronization is complete, find the newly created OSS bucket and turn on the Configuration Risks switch.
Wait for the Connection Status of the OSS bucket to change to Connected.

Step 3: Manually run a baseline check
3.1 View and confirm that the check policy is enabled
In the navigation pane on the left, choose .
On the tab, view the OSS-related check items and their status.
The PIPL Security Baseline requires an Enterprise instance of DSC. This example uses the Alibaba Cloud Data Security Best Practices to check the compliance of the authorized bucket.
By default, DSC enables all check items in the baseline check policy to detect risks for authorized OSS assets.

Confirm that the status column for the OSS check items shows the enabled icon
 .
.
3.2 Manually run security checks for each item
On the tab, find the target policy and click Details in the Actions column.
On the Risk Situation tab, click Check for each OSS-related check item. The detection is complete when the Detect button becomes active again. Then, close the panel.

Repeat the preceding steps to complete the detection for the check items of different check policies.
Step 4: View and handle security risks
4.1 View the check results for the target OSS bucket
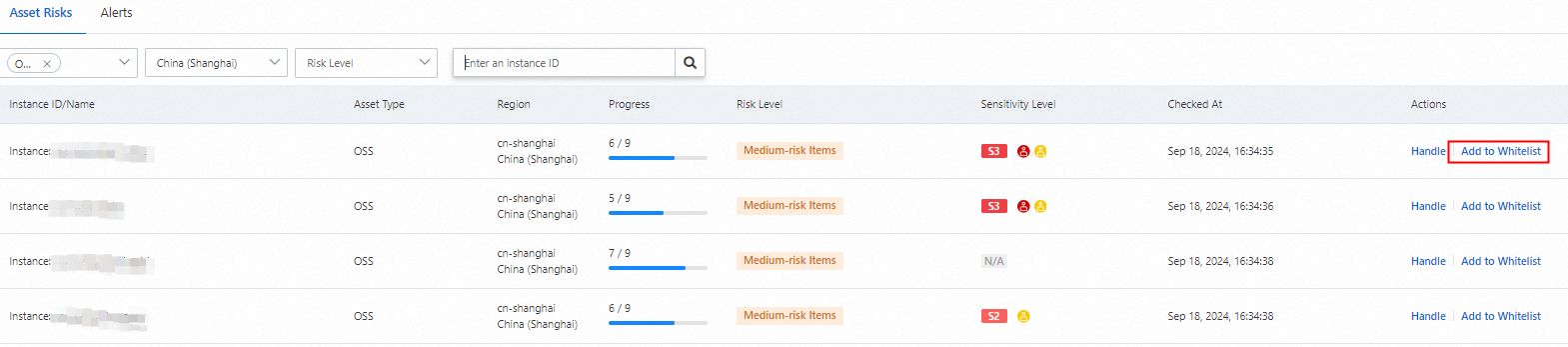
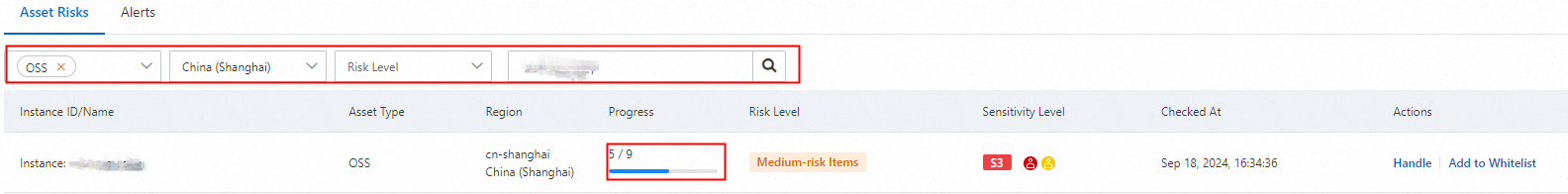
After the baseline check is complete, on the Asset Risks tab, search for the target bucket to view the check results. The detection time indicates when the last check was performed.
Click Handle in the Actions column to view the failed check items and their recommended solutions.
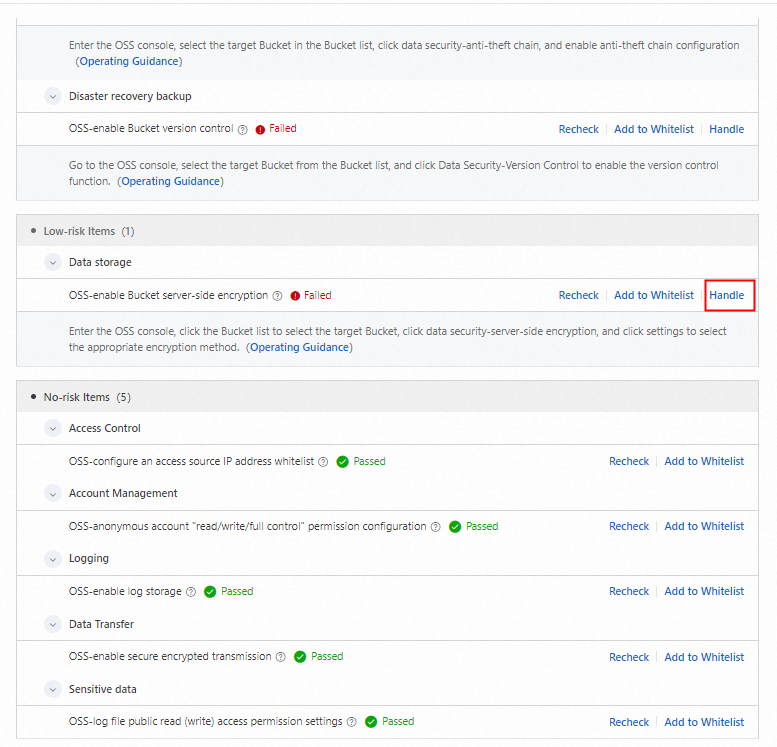
4.2 Handle risk items
In the Risk Details area, click Handle to navigate to the corresponding page and resolve the risk. For example, you can handle the OSS-enable Bucket server-side encryption risk.
You are redirected to the Server-side Encryption page for the OSS bucket. Click Settings. In this example, the encryption is set to OSS-Managed. Click Save. For more information about how to configure server-side encryption, see Server-side encryption.

4.3 Rerun the check for verification
Return to the risk details panel in DSC and click Recheck.
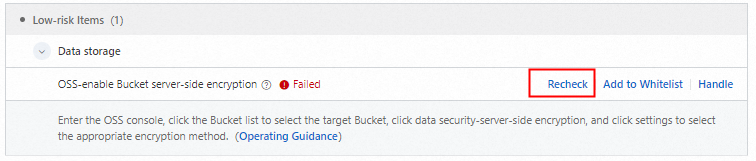
A passed check indicates that the risk item is resolved.
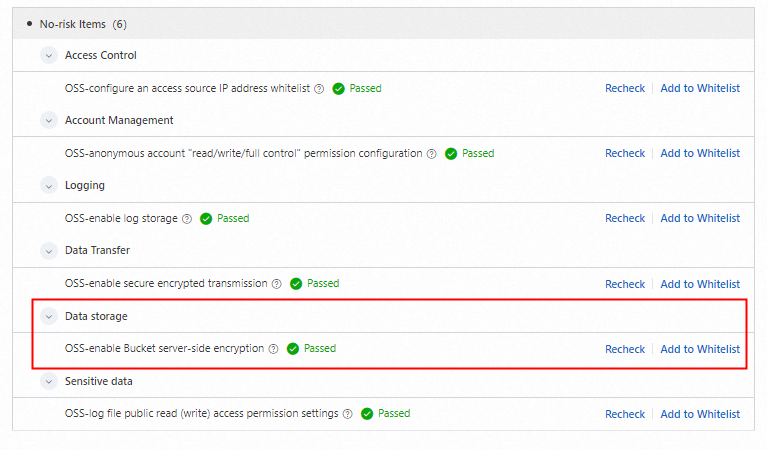
You can follow these steps to handle all risk items and improve the security configuration compliance of your OSS bucket.
Summary
Before you store data in an existing OSS bucket, complete a security configuration compliance check to enhance the security of your data storage.
Sensitive data protection policy
By default, the OSS-sensitive data Bucket public read (write) Access Check check item passes the baseline security check for any OSS bucket where sensitive data has not yet been detected. To maintain compliance after you store data in the bucket, create a sensitive data detection task. This task periodically scans the bucket for sensitive data. If sensitive data is found, DSC runs the OSS-sensitive data Bucket public read (write) Access Check baseline check. This lets you promptly handle any risks associated with this check item.
For more information about sensitive data detection tasks, see Scan for sensitive data using a detection task.
The Free Edition of Data Security Center provides 5 GB of free OSS data detection per month. If this quota does not meet your business needs, you must purchase a paid instance of Data Security Center. For more information, see Purchase DSC.
Whitelist management
If you determine that a failed check for a specific asset can be ignored, go to the Asset Risks tab. Find the target asset and click Add to Whitelist in the Actions column. This adds the asset to the whitelist for that check item.
The Free Edition of Data Security Center does not support whitelist management. You must purchase an Enterprise instance of Data Security Center to use the whitelist feature.