You can use the Data Detection and Response service of Data Security Center (DSC) to detect plaintext AccessKey pairs in Object Storage Service (OSS) data and abnormal access that uses AccessKey pairs. An AccessKey pair consists of an AccessKey ID and an AccessKey secret. If DSC detects an abnormal access event, it triggers a warning. You can view information about abnormal AccessKey pairs and alert events to promptly identify and handle the risks of AccessKey pair leaks and abnormal access to OSS data. This helps prevent AccessKey pair leaks and misuse, which can lead to unauthorized access and data breaches.
Overview
This topic uses an example to show how to use the Data Detection and Response service. In the example, a plaintext AccessKey pair is detected in an OSS bucket, and an alert is reported when the leaked AccessKey pair is used to access a file with public-read permissions. This topic describes how to detect and manage alert events for AccessKey pair leaks and abnormal access in OSS buckets to improve the security of your OSS data.

To implement alerting and handling for abnormal access to OSS data that uses AccessKey pairs, perform the following five steps:
Create an OSS bucket and upload files: Create an OSS bucket and upload sample files. The files include a file that contains AccessKey pair information and a sample folder that contains a sample file. These files are used to simulate an AccessKey pair leak and abnormal access to OSS data.
Connect an OSS bucket to DSC: Connect an OSS bucket to the Data Detection and Response service of DSC. This allows DSC to detect AccessKey pair leaks and abnormal access to the OSS bucket.
Configure risk event levels and alert notifications: Configure settings to detect alert events and receive alert notifications.
View alert notifications for abnormal AccessKey pair leaks: Simulate abnormal access to a file in an OSS bucket and view the resulting alert event. Handle the alert event promptly.
View and handle risk events of AccessKey pair leaks: Detected AccessKey pair leaks generate risk events. You can then view the event details and handle them promptly.
Prerequisites
Your Alibaba Cloud account has purchased a Data Security Center instance and granted Data Security Center the permissions to access other Alibaba Cloud resources.
The Data Detection and Response service is a value-added service of Data Security Center. To audit alerts for abnormal access to OSS buckets that use an AccessKey pair, the service consumes OSS protection capacity and log storage capacity. In this example, when you purchase Data Security Center, you only need to set Edition to Value-added Plan, enable Data Detection and Response and Log Storage, and purchase sufficient Data Detection and Response - OSS Protection Capacity and Extended Log Storage Capacity. You can choose whether to purchase other services as needed.
Object Storage Service (OSS) is activated. For more information, see Activate OSS.
This example simulates an AccessKey pair leak and an abnormal access alert. You need to prepare a Resource Access Management (RAM) user under your account and its AccessKey ID and AccessKey Secret. For more information, see Create a RAM user and View the AccessKey information of a RAM user.
Step 1: Create an OSS bucket and upload files
Create an OSS bucket
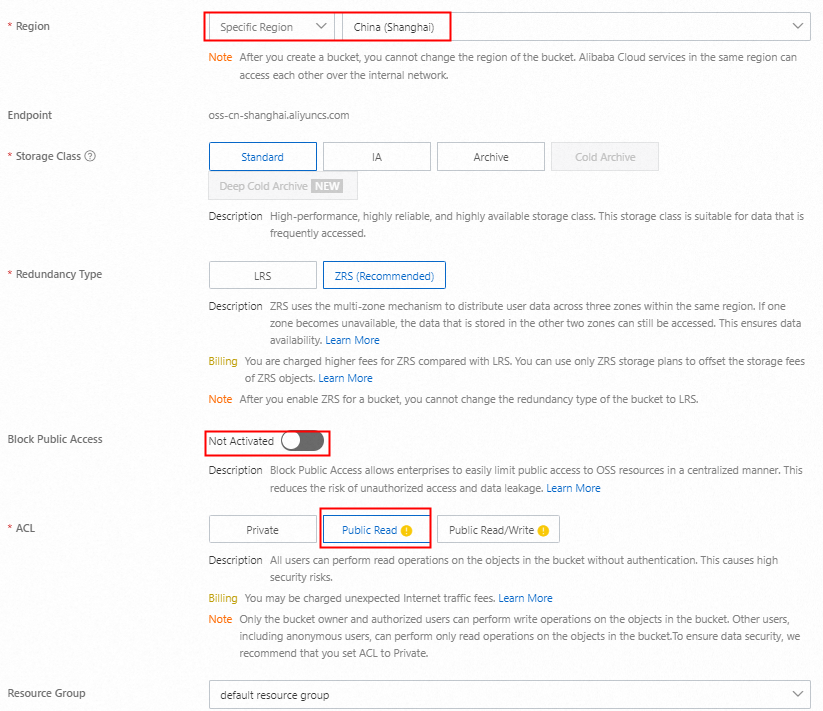
On the Buckets page of the OSS console, click Create Bucket.
In the Create Bucket panel, configure the following parameters, use the default settings for the other parameters, and then click Create.
Upload files to the OSS bucket
Create a file named test.txt, enter the AccessKey ID and AccessKey Secret of the prepared RAM user, and then save the file.
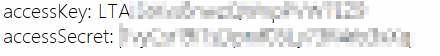
On the Buckets page of the OSS console, click the name of the OSS bucket.
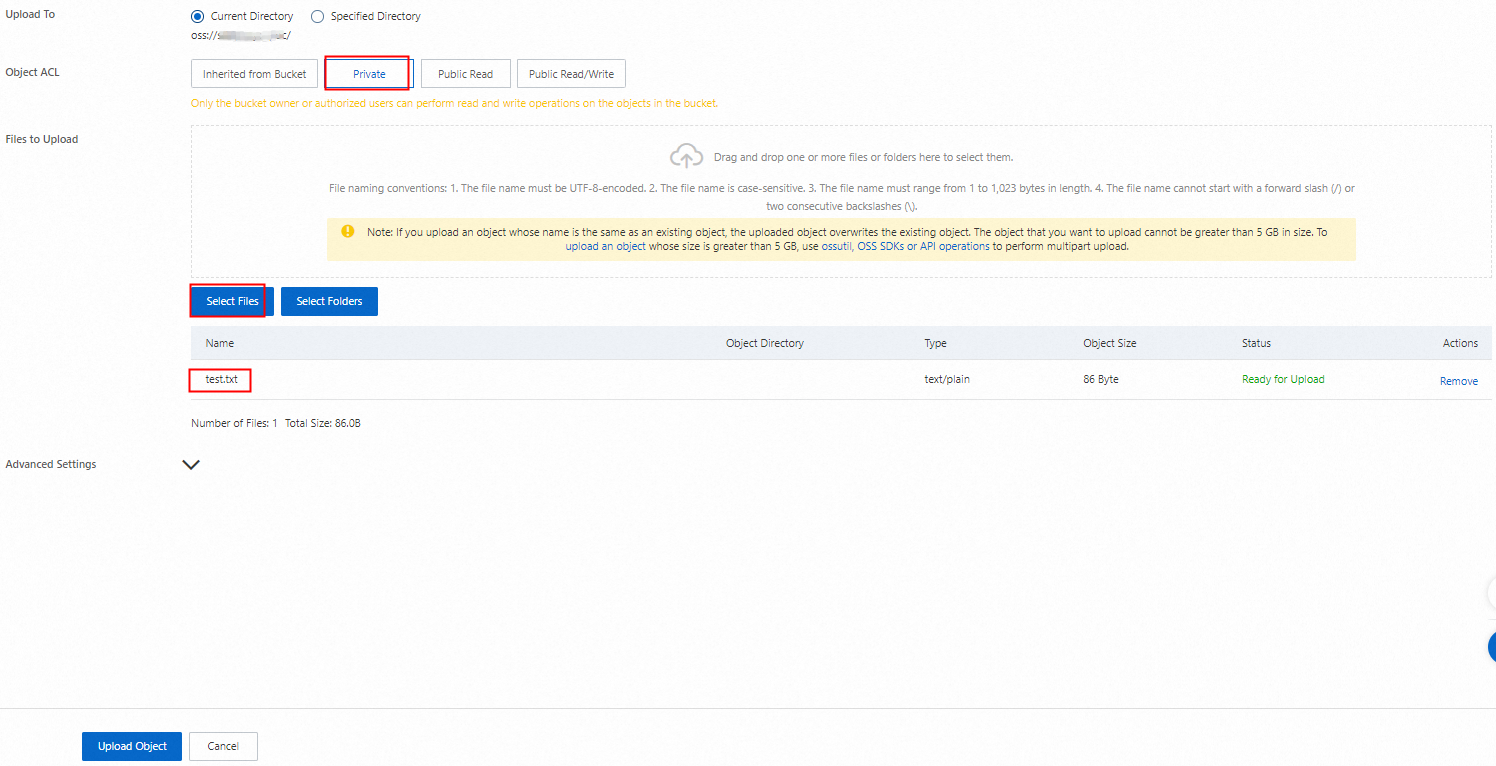
On the Objects tab, click Upload Object.
Set Object ACL to Private, click Select Files, select the saved test.txt file, and then click Upload. Wait until the file is uploaded.
On the Objects tab, click Create Directory, enter a Directory Name such as
exampledir, and then click OK.Go to the
exampledirdirectory and click Upload Object.Click Select Files, select a sample file such as userdata.csv from your computer, and then click Upload. Wait until the file is uploaded.
Step 2: Connect an OSS bucket to DSC
Log on to the Data Security Center console.
In the navigation pane on the left, choose .
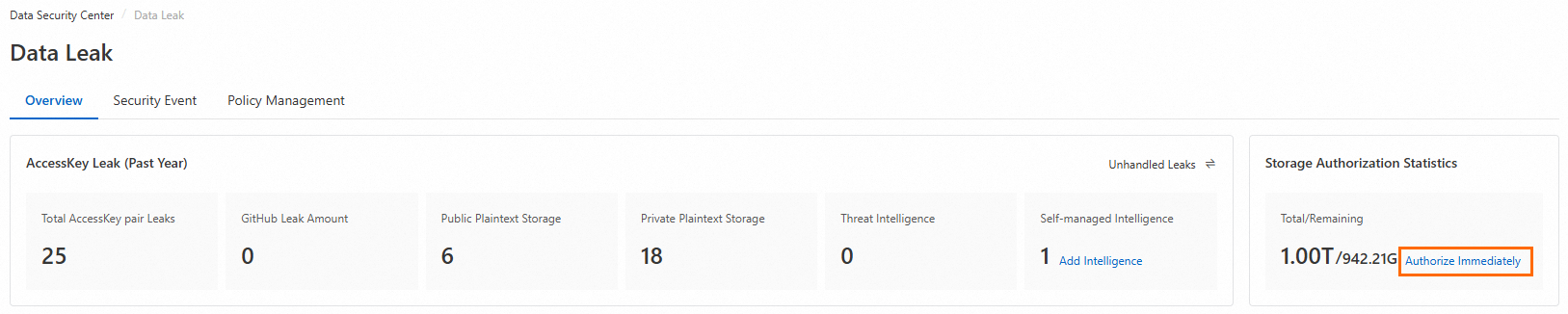
On the Overview tab, in the Storage Authorization Statistics section in the upper-right corner, click Authorize.
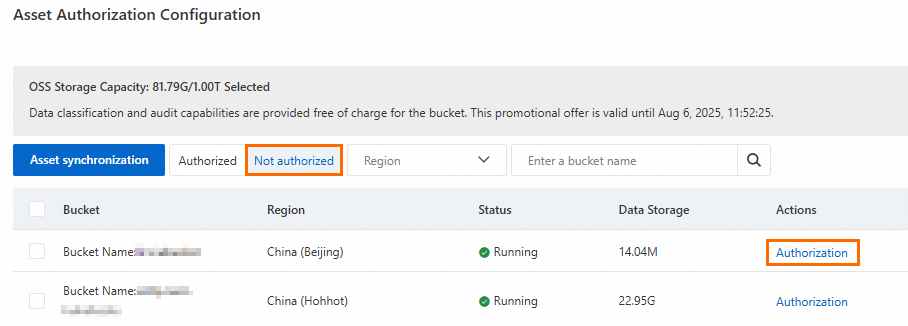
In the Asset Authorization Configuration panel, click Asset synchronization.
On the Not authorized tab, find the target bucket in the bucket list and click Authorization in the Actions column.
During the first month after you enable the Data Detection and Response service, DSC creates and immediately runs a sensitive data identification scan task. The primary template, which is the Internet Industry Classification and Categorization Template by default, is used to classify and categorize sensitive information.
Step 3: Configure risk event levels and alert notifications
Policy configuration
DSC detects risk events related to AccessKey pair leaks. For DSC to detect these events, you must enable detection for the event type and configure its risk level.
In the navigation pane on the left, choose .
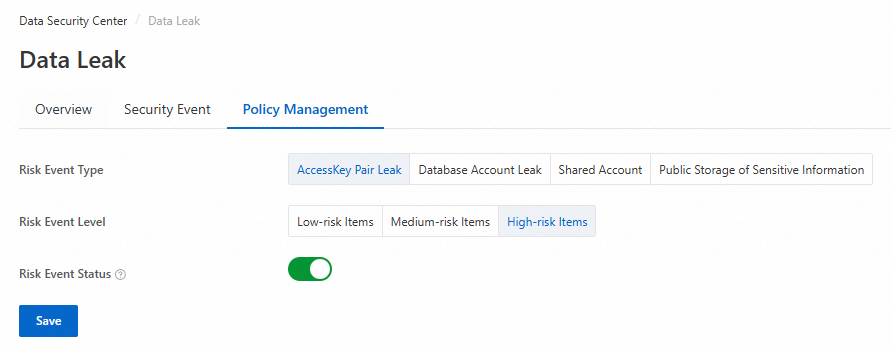
On the Policy Management tab, select AccessKey Pair Leak for Risk Event Type, set the Risk Event Level, enable Risk Event Status, and then click Save.
 Note
NoteRisk events are enabled by default, and the risk level for AccessKey Pair Leak events is set to High-risk Items by default.
If you disable a risk event, no new alert events are generated. Existing events are not affected.
After you change the risk level of an event, the risk levels of existing events are updated.
Configure alert notifications for abnormal AccessKey pair-based access
In the navigation pane on the left, choose .
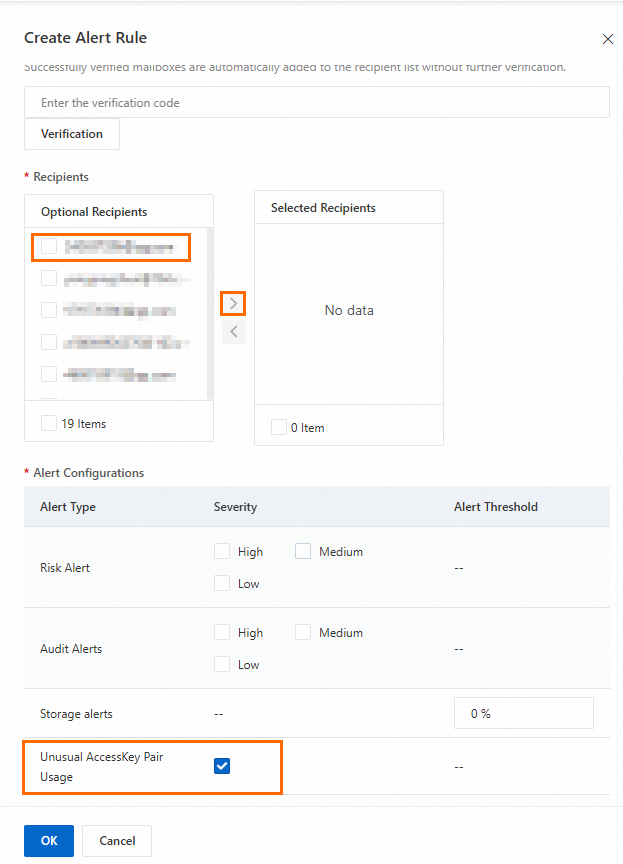
On the Alert Notification tab, click Create Alert Configuration.
In the Create Alert Rule panel, select Mailbox or Text Message as the alert method, configure the parameters as needed, and then click OK. For more information, see Configure email, text message, and phone call alert notifications.
Step 4: View alert notifications for abnormal AccessKey pair leaks
After you successfully access the OSS bucket using the AccessKey pair, you can view and receive the alert event and notification for the abnormal access on the following day.
Use an AccessKey pair to download an object from an OSS bucket
This topic uses the installation of ossutil in a Linux environment as an example to describe how to use the ossutil command line interface (CLI) to access an object in an OSS bucket. For more information about the installation, see Install ossutil.
Install and configure ossutil.
In a Linux operating system, run the following command to download and install ossutil.
sudo -v ; curl https://gosspublic.alicdn.com/ossutil/install.sh | sudo bashNoteDuring the installation, you must use a decompression tool, such as unzip or 7z, to decompress the package. Install one of these tools in advance.
After the installation is complete, ossutil is installed in the /usr/bin/ directory.
Run the configuration command:
ossutil config.Press Enter as prompted to set the configuration file path to the default path and set the tool language to EN.
Set the Endpoint, AccessKey ID, STSToken, and AccessKey secret parameters as prompted.
On the OSS bucket's Overview page, in the Access Port section, you can find the Endpoint. The AccessKey ID and AccessKey secret are the AccessKey information for the prepared RAM user.
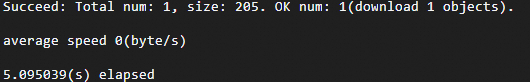
Run the following command to access the
/exampledir/userdata.csvobject in the target OSS bucket.ossutil cp oss://examplebucket/exampledir/userdata.csv /optIf the following information is returned, the object was successfully accessed and downloaded.
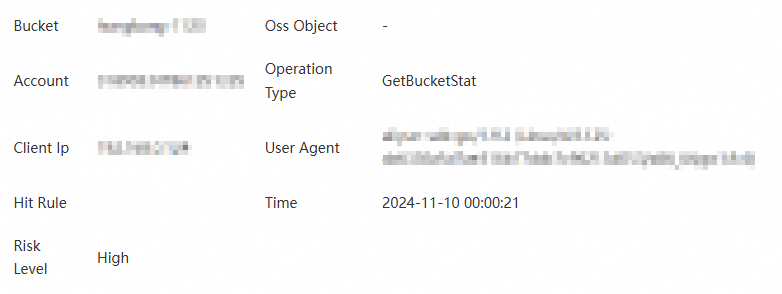
View email alert notifications
The contact for alert notifications receives an email notification similar to the one shown in the following figure:
Step 5: View and handle risk events of AccessKey pair leaks
In the navigation pane on the left, choose .
In the Risk Type section, click AccessKey Pair Leak.
Find the target risk event and click Details in the Actions column.
On the Details page, view the details of the risk event and handle it.
AccessKey information
View information such as AccessKey ID, Account of AccessKey Pair, AccessKey Pair Status, First Detection Time, Latest Detection Time, and Intelligence Source.

Click Handle.
In the Manage AccessKey Pair panel, perform Disable or Rotate operations.
Disable: Redirects to the Resource Access Management (RAM) console to disable the AccessKey for the current primary account and its RAM users. For more information, see Disable an AccessKey pair of a RAM user.
Rotate:
KMS Integrated: After clicking Confirm, KMS will perform rotation, delete the existing AccessKey pair, and create a new one.
WarningThis operation cannot be undone once executed. Please proceed with caution.
KMS Not Integrated: Redirects to the Key Management Service console to host your AccessKey credentials in KMS. If you have not activated KMS, you must first purchase and enable a KMS instance.
AccessKey leak details
View AccessKey leak information from the following intelligence sources. You can process or whitelist risk events based on different intelligence sources.
GitHub Leak Amount: AccessKey information contained in public source code on the GitHub platform.
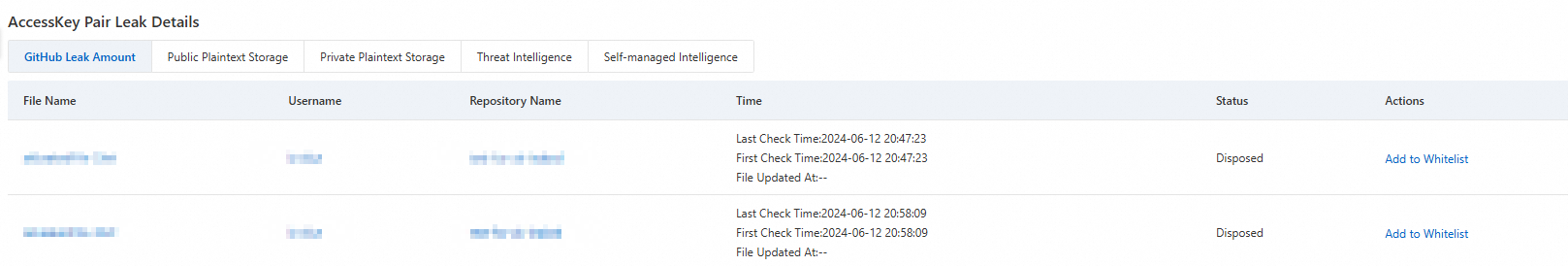
Click File Name, Username, or Repository Name to jump to the GitHub platform to view related information.
Click Add to Whitelist in the Actions column to whitelist the target file. This file will not generate AccessKey leak risk events in the future.
Public Plaintext Storage/Private Plaintext Storage: Detects AccessKey information stored in plaintext in public/private files in authorized OSS buckets.
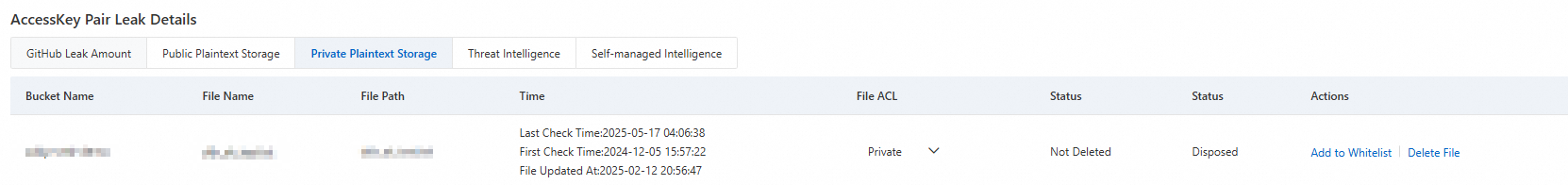
Modify ACL: Click the dropdown button in the File ACL column to modify the ACL of the corresponding file.
Delete: Click Delete File in the Actions column to delete the file from the corresponding bucket.
Add to allowlist: In the Actions column, click Add to Whitelist to add the target file to the allowlist. The file will no longer generate AccessKey pair leak threat events.
Threat Intelligence/Self-managed Intelligence: For AccessKey leak events from threat intelligence or custom intelligence, you can whitelist related threat sources or intelligence entry users.
NoteAfter a file is deleted, the Status will automatically update to Deleted on T+1 day, and the Status will update to Disposed.
After a file is whitelisted, the Status will automatically update to Added to Whitelist on T+1 day.
AccessKey bucket access details
For leaked AccessKeys accessing buckets, you can not only view specific file access lists but also configure bucket access permissions and set POP gateway interception policies to effectively protect data security.
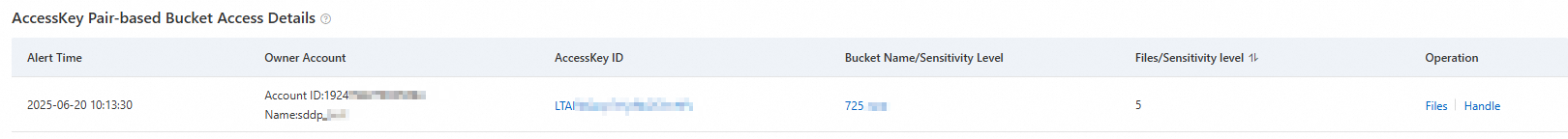
Threat Tracing: Click the target AccessKey ID or Bucket Name/Sensitivity Level to view the visualization path of AccessKey and bucket access behavior.
View Files: Click Files in the Actions column to view information about accessed files. You can also directly modify the file ACL.
Handle: Click Handle in the Actions column to configure bucket access permissions and set POP gateway interception policies.
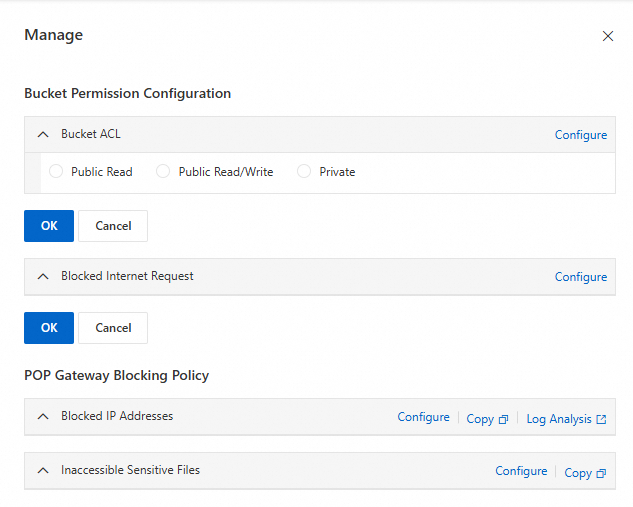
Bucket Permission Configuration: Click Configure to set up Bucket ACL and public network request interception, then click OK.
POP Gateway Blocking Policy: Click Configure to jump to the Resource Access Management (RAM) console to create policies that restrict IP access and sensitive file access permissions. For more information, see Create a custom policy.
References
In addition to detecting AccessKey Pair Leak in OSS buckets, DSC also supports detecting risk events such as Database Account Leak, Shared Account, and Public Storage of Sensitive Information. For more information, see Risk overview and custom intelligence.