This topic describes how to use Data Management (DMS) to help you sail through the challenges during large-scale events. You can use DMS to evaluate the performance and security of your database. Then, you can take preventive measures to ensure the stability of your business during large-scale events and prevent economic losses due to a system breakdown caused by database overload.
Prerequisites
The instance to which the database belongs is managed in Security Collaboration mode. For more information, see Control modes.Background information
Business volume may surge during large-scale events. This poses significant challenges to database usage and data security. The following scenario is used as an example.
During large-scale events, traffic spikes can affect the performance of databases. When you prepare for large-scale events, evaluate the usage of your databases and estimate the access traffic from your customers and developers in your company.
- An operator executed slow queries to collect data generated during large-scale events. This results in business failures.
- A developer executed a schema change statement, which affected an event in another line-of-business that uses the same database.
Performance security
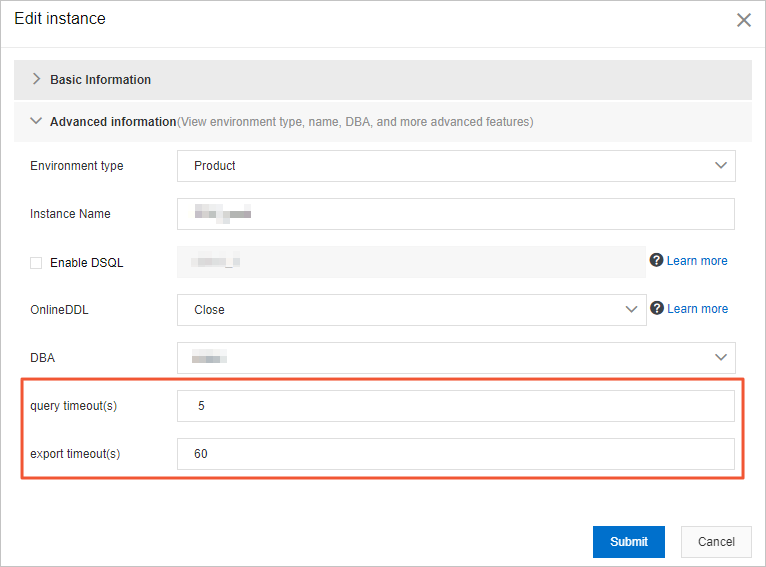
Configure timeout periods for queries and export tasks
To prevent SQL statements from being executed over a long period, specify a query timeout period and an export timeout period for your database instance in the Edit dialog box of the DMS console. Slow queries may affect your business.
During normal business periods, we recommend that you set the query timeout period to 60s and the export timeout period to 600s. During large-scale events, we recommend that you set the query timeout period to 5s and the export timeout period to 60s.
For more information, see Modify a database instance.
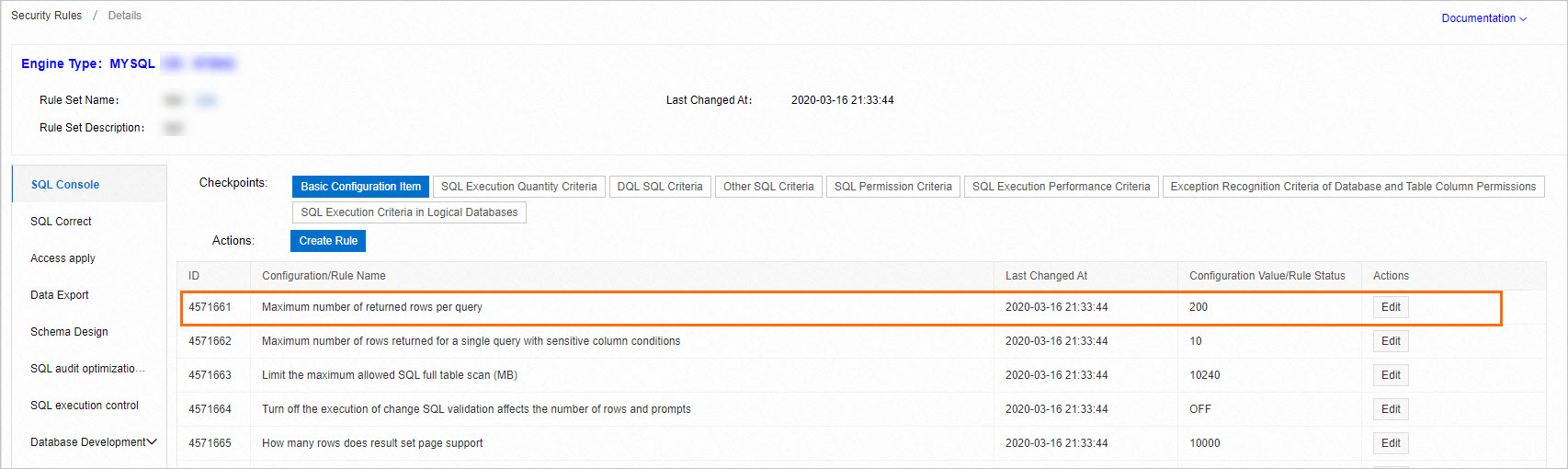
Configure the maximum number of rows returned per query
You can configure the Maximum number of returned rows per query rule to specify the maximum number of rows that can be returned for a query. This prevents the response time for business requests from being affected when large amounts of data are returned.
During normal business periods, we recommend that you set the value of the Maximum number of returned rows per query rule to 200. During large-scale events, we recommend that you set the value to 10. For more information, see Security rules on the SQL Console tab.
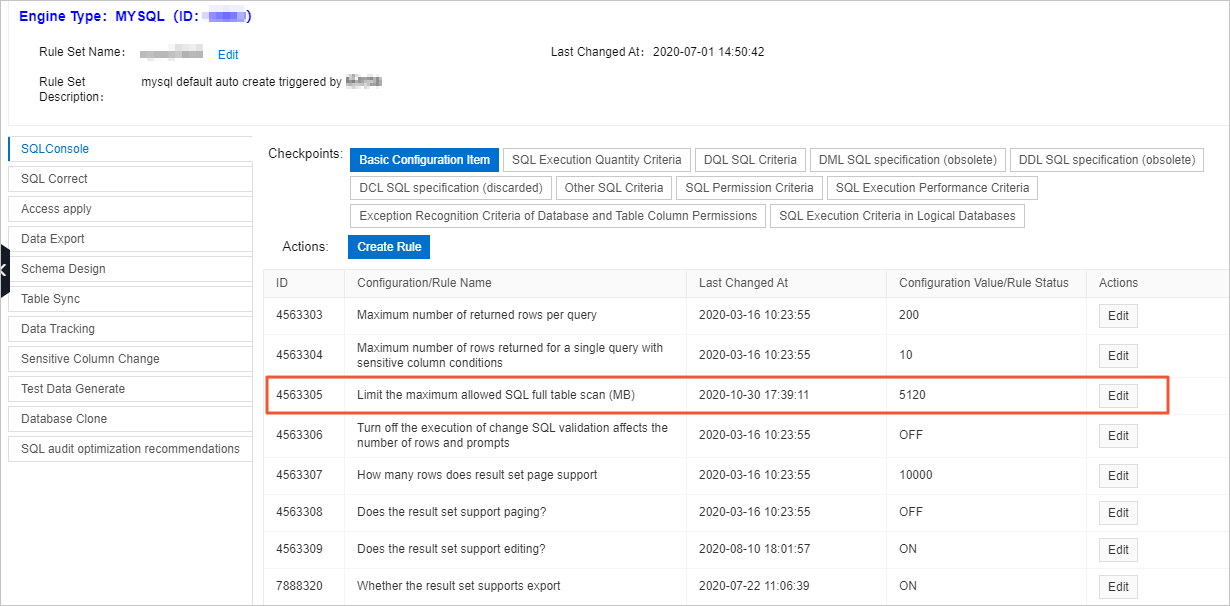
Configure the maximum size of tables on which full scans are performed
On the Security Rules page of the DMS console, set the Limit the maximum allowed SQL full table scan (MB) rule to prevent business interruptions caused by full scans on large tables during large-scale events.
During normal business periods, we recommend that you set the value of the Limit the maximum allowed SQL full table scan (MB) rule to 10240. During large-scale events, we recommend that you set the value to 1024. For more information, see Security rules on the SQL Console tab.
Data change security
Block high-risk SQL statements
To prevent high-risk SQL statements from being executed, manage high-risk SQL statements, such as data query language (DQL), DDL, DML, and data control language (DCL), on the Security Rules page of the DMS console. High-risk SQL statements may affect your business.
During normal business periods, we recommend that you allow high-risk SQL statements based on your business requirements. During large-scale events, we recommend that you block high-risk SQL statements such as DDL. For more information, see Security rules on the SQL Correct tab.
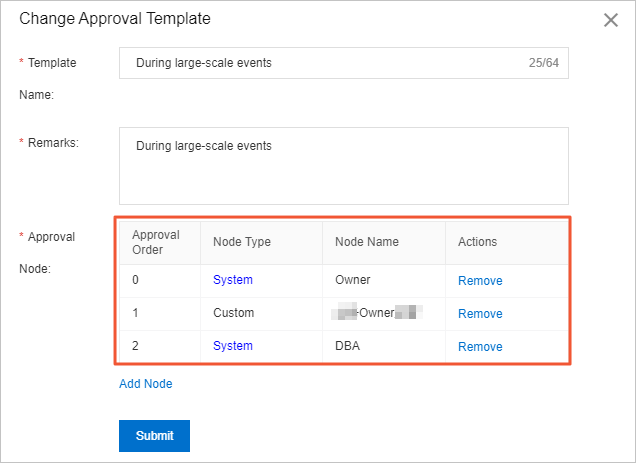
Modify approval processes
During large-scale events, we recommend that you add a supervisor or a business-related member to approval processes.
During normal business periods, we recommend that you configure R&D engineers, data owners, and database administrators (DBAs) in the approval process as needed. During large-scale events, we recommend that you configure R&D engineers, data owners, supervisors of the data owners, and DBAs in the approval process. For more information, see Approval processes.
Manage data change periods
You can allow or forbid data changes to database instances in the specified periods of time in the underlying execution engine.
During large-scale events, we recommend that you configure periods of time during which SQL statements cannot be executed, such as DDL, DML, and SELECT statements.
Data security
Increase the security levels of sensitive fields
Increase security levels of sensitive fields, such as personal information, mobile phone numbers, ID card numbers, and money. Mask these fields to improve data security. For more information, see Adjust field security levels.
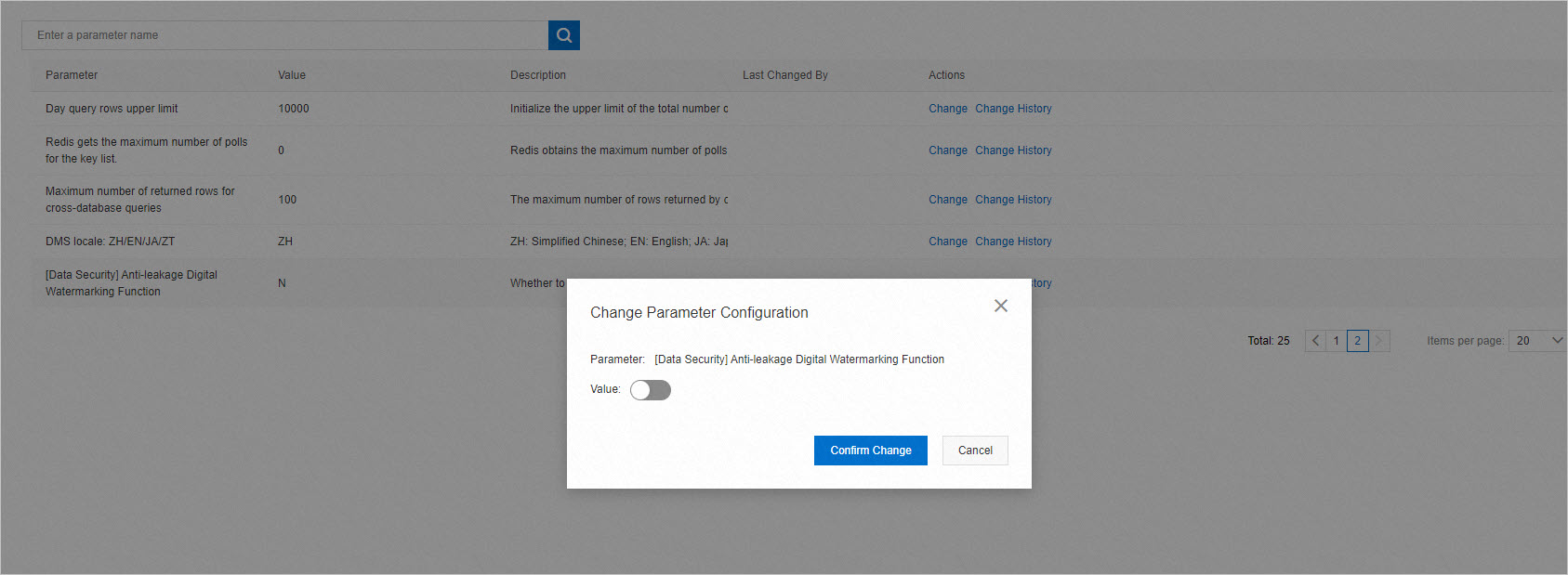
Enable the digital watermark feature
You can enable the digital watermark feature in the DMS console. After you enable this feature, DMS adds watermarks to the DMS console. Watermarks discourage users from sharing screenshots which may lead to data leaks. For more information, see Add digital watermarks.
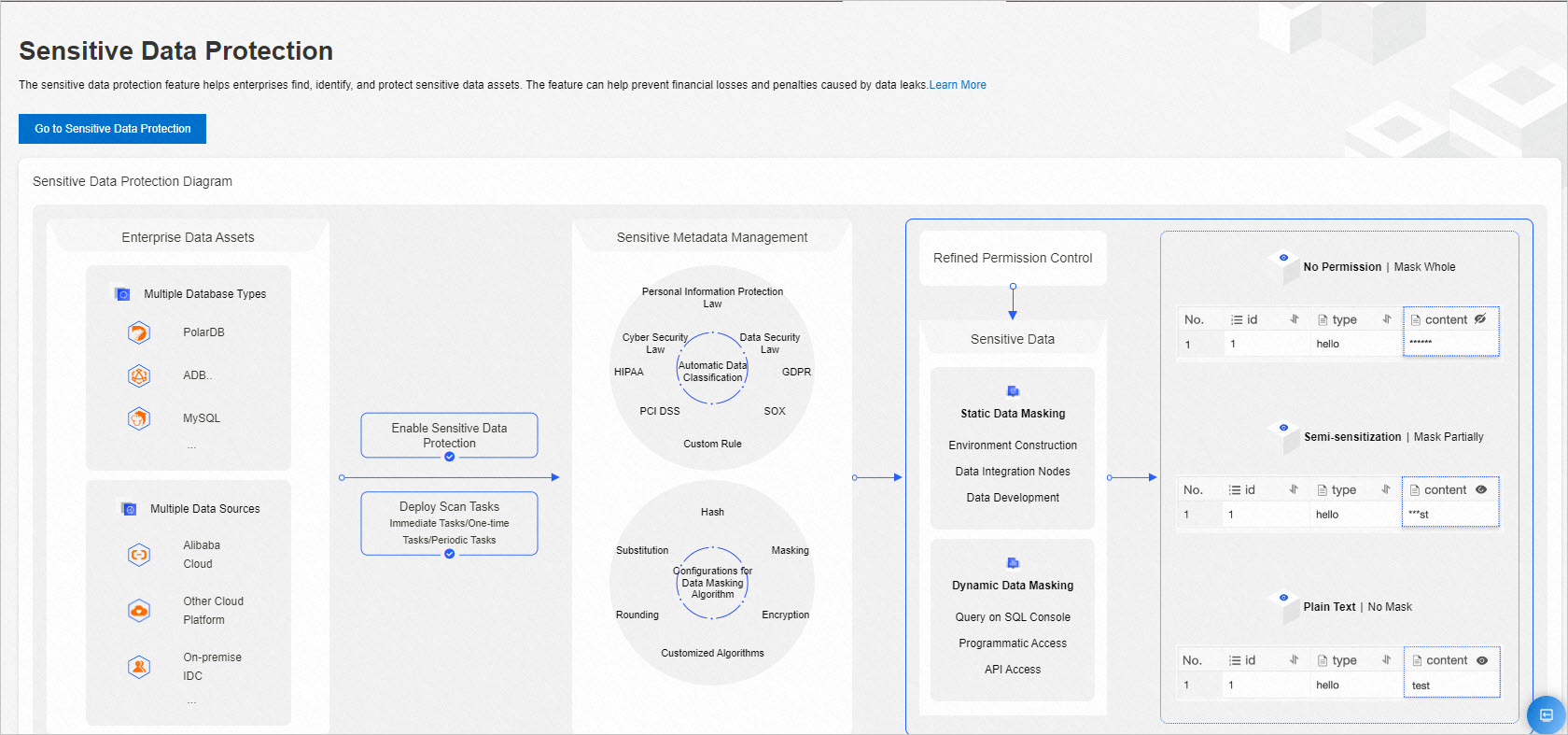
Manage sensitive data
DMS efficiently identifies sensitive data and displays its distribution. You can perform fine-grained access control for sensitive data, mask sensitive data, and manage permissions on sensitive data based on the principle of least privilege. For more information, see Manage sensitive data.
Configure row-level access control
You can manage permissions on data rows in a table. This way, different users can access only specified rows in the same table. For more information, see Configure row-level access control.
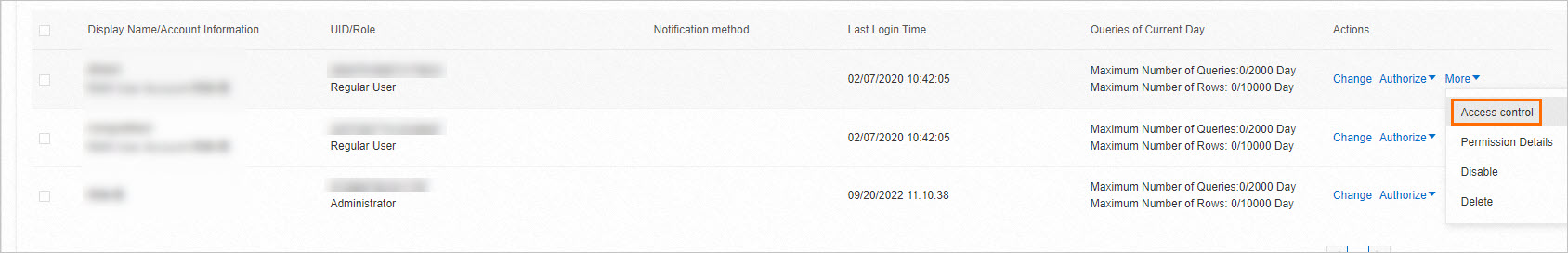
Configure access control for users
You can configure access control for specific users so that users can access only the metadata on which they have the required permissions. The metadata includes databases, instances, and tables. For more information, see Metadata access control.
Configure the visibility range of the metadata
You can configure the visibility range of the metadata. This way, users who do not have the required permissions cannot view or access the metadata. For more information, see Metadata access control.
Emergency response
Audit operation records
DMS provides the operation audit feature. This allows you to check whether changes are made to specific databases or tables within a specified period of time in a quick manner. For more information, see Audit operations.
Track data
DMS provides the data tracking feature. This allows you to recover data in a quick manner if data is deleted or updated by accidental operations. For more information, see Data tracking.
Perform lock-free DML operations
In urgent situations, you can modify data by using large amounts of SQL statements that do not use indexes, such as the UPDATE and DELETE statements. For more information, see Perform lock-free DML operations.
Perform lock-free DDL operations
In urgent situations, you can perform lock-free DDL operations to resize a field of a table or create an index for a table. For more information, see Enable the lock-free schema change feature.
To better understand and use DMS, you can search for the DingTalk group number 21991247 to join the group.