Usage notes
Category | Description |
Automatically add the CIDR blocks of DBS to the security settings of a data source | If the data source that you want to add or back up is an ApsaraDB instance, such as an ApsaraDB RDS instance, a PolarDB instance, or an ApsaraDB for MongoDB instance, or a self-managed database hosted on an Elastic Compute Service (ECS) instance, DBS automatically adds the CIDR blocks of DBS to the IP address whitelist of the ApsaraDB instance or the security group rules of the ECS instance. No manual configurations are required. Note If you use DBS as a Resource Access Management (RAM) user, make sure that the AliyunDBSFullAccess and AliyunOSSFullAccess policies are attached to the RAM user. Otherwise, DBS fails to add the CIDR blocks of DBS to the IP address whitelist of an ApsaraDB instance or the security group rules of an ECS instance due to insufficient permissions. For more information, see Grant permissions to a RAM user. If you revoke the access permissions of DBS on ECS instances, the CIDR blocks of DBS fail to be automatically added to the security group rules of ECS instances. To resolve this issue, you must manually add the CIDR blocks of DBS to the security group rules of ECS instances.
|
Manually add the CIDR blocks of DBS to the security settings of a data source | If the type of the data source that you want to add or back up is User-Created Database with Public IP Address <IP Address:Port Number> and security settings such as firewall settings are configured for the self-managed database, you must manually add the CIDR blocks of DBS to the security settings of the self-managed database. |
If the type of the data source that you want to add or back up is Express Connect DB/VPN Gateway/Intelligent Gateway, you must add the CIDR blocks of DBS as the destination for the virtual private cloud (VPC) to which the data source is connected. For more information, see Back up a self-managed database in a data center connected to Alibaba Cloud over Express Connect to OSS or DBS and Back up a self-managed database in an on-premises data center connected to Alibaba Cloud through VPN Gateway or Smart Access Gateway to OSS or DBS. |
Warning
If the data source is a self-managed database, you must manually add the public CIDR blocks of DBS to the security settings of the self-managed database to allow access from DBS servers. However, security risks may arise if public access is allowed to a self-managed database. We recommend that you strengthen authentication with accounts and passwords, restrict the allowed ports, or use the internal access methods of Express Connect, VPN Gateway, or Smart Access Gateway.
Procedure
When you add or back up a data source, click Set Whitelist.
This example shows how to view the CIDR blocks of DBS on the Data Source page. Other pages also provide similar buttons.
In the message that appears, copy all CIDR blocks of DBS.
The CIDR blocks of DBS that are displayed in the message vary based on the region that you select.
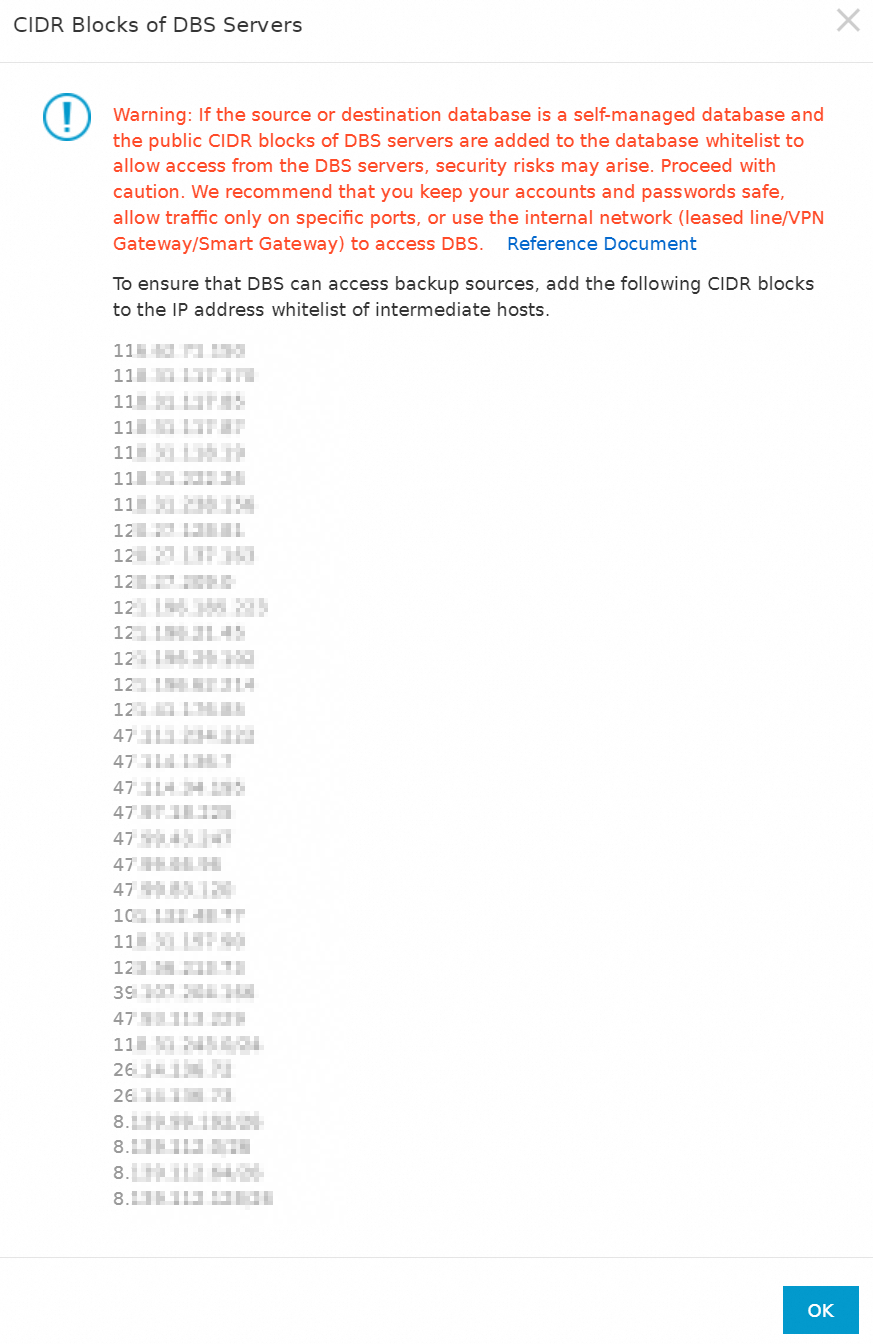
Add the CIDR blocks of DBS to the security settings of the data source. For example, add the CIDR blocks of DBS to the firewall settings of the on-premises server, the firewall settings of the data source, or the security group rules of the ECS instance that hosts the data source.
After the CIDR blocks of DBS are added to the security settings of the data source, DBS can access the data source by using the database account and password that you specify.
Note
Security settings may be configured to allow the database account to access the data source only from specified IP addresses. For example, username'@'localhost specifies that the username account can access the data source only from the local host. In this case, DBS cannot connect to the data source by using the username account. To resolve this issue, change the administrator permissions of the username account or specify another database account.
To add the CIDR blocks of DBS to the security group rules of an ECS instance, perform the following steps:
On the Instances page of the ECS console, click the ECS instance that you want to manage.
On the instance details page, click the Security Groups tab and then click the security group that you want to configure.
On the Inbound tab, click Quick Add.
In the Quick Add dialog box, paste the copied CIDR blocks to the Authorization Object field. In the Port Range section, select All (1/65535) and click OK.
The CIDR blocks of DBS are added to the security group rules of the ECS instance.
Note
By default, the outbound rules of a security group allow ECS instances to access all IP addresses. If you disable the outbound traffic for a security group, you must add the CIDR blocks of DBS to the outbound rules of the security group.
 Elastic Compute Service (ECS)
Elastic Compute Service (ECS)
 Lingma
Lingma