The data masking feature can mask sensitive data in a single table that is synchronized in real time and store the masked data to a specified database.
Prerequisites
A reader node is configured. For more information, see Data source types that support real-time synchronization.
Procedure
Go to the DataStudio page.
Log on to the DataWorks console. In the top navigation bar, select the desired region. In the left-side navigation pane, choose . On the page that appears, select the desired workspace from the drop-down list and click Go to Data Development.
In the Scheduled Workflow pane of the DataStudio page, move the pointer over the
 icon and choose .
icon and choose . Alternatively, find the desired workflow in the Scheduled Workflow pane, right-click the workflow name, and then choose .
In the Create Node dialog box, set the Sync Method parameter to End-to-end ETL and configure the Name and Path parameters.
Click Confirm.
On the configuration tab of the real-time synchronization node, drag Data Masking in the Conversion section to the canvas on the right, and connect the Data Masking node to the configured reader node.
Click the Data Masking node. In the configuration panel that appears, configure the parameters.

Create a data masking rule. Click Data Masking Rule. In the Create Data Masking Rule dialog box, configure the Sensitive Data Type, Rule Name, Data Masking Method, Security Domain, and Character Set for Replacement parameters.
Create a data masking rule.
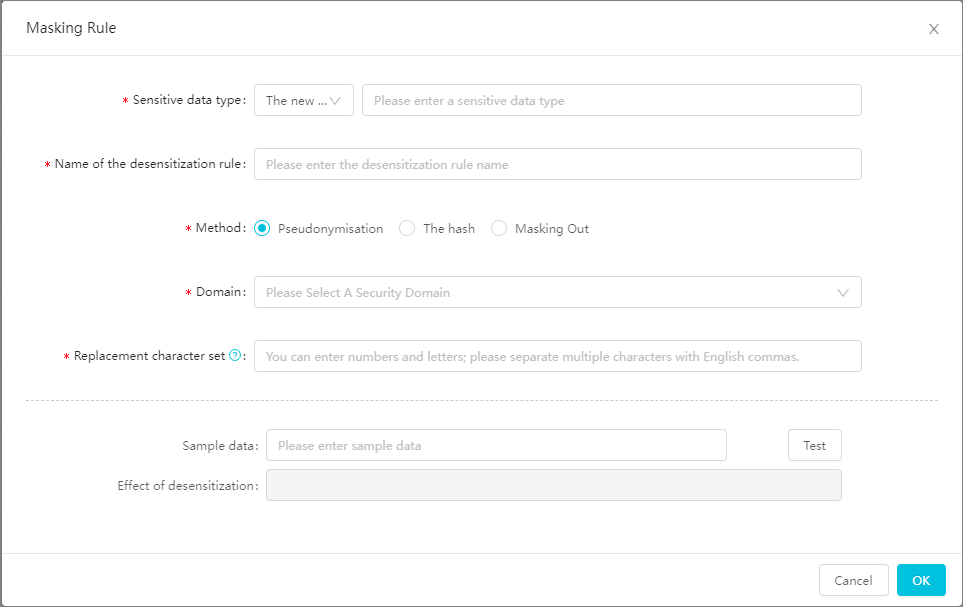
Configure basic information.
Parameter
Description
Sensitive Data Type
By default, Existing Data Type is selected from the drop-down list on the left. You can select an existing sensitive field type from the drop-down list on the right. The existing sensitive field types include the built-in sensitive field types and sensitive field types created by all users.
You can also select New Data Type from the drop-down list on the left. In the field on the right, enter a name for a new sensitive field type. The name must be 1 to 30 characters in length and can contain letters and digits.
After you enter the name of a new data type, the system checks whether the name is used by existing sensitive field types, including built-in sensitive field types and sensitive field types created by all users. If the name has been used, the message The specified sensitive field type already exists. is displayed.
NoteThe built-in sensitive field types are Mobile Phone Number, Id Card, Bank Card, Email, IP, Car No, Post Code, Seat Number, Mac Address, Address, Name, Company, Nation, Constellation, Gender, and Nationality.
Rule Name
By default, the system populates this field with the value of the Sensitive Data Type parameter. You can change the rule name. The name must be 1 to 30 characters in length and can contain letters and digits. If you enter a name that has been used by an existing rule, the message The specified rule name already exists. is displayed.
Configure the Data Masking Method parameter to specify a data masking method. Valid values of the Data Masking Method parameter: Pseudonymisation, Hashing, and Redaction.
Pseudonymisation
This method replaces the characters of a data record with an artificial pseudonym of the same characteristics. The data format of the pseudonym is the same as that of the original data record.
If you set the Sensitive Data Type parameter to a built-in sensitive field type, such as Mobile Phone Number, Id Card, Bank Card, Email, IP, Car No, Post Code, Seat Number, Mac Address, Address, Name, or Company, you must configure the Security Domain parameter for your data records.
Security Domain: You can select a digit from 0 to 9 from the Security Domain drop-down list. Data masking policies vary with the security domain. Different data masking results are returned for the same data record in different security domains. For example, if the data record is a123 and the security domain is set to 0, the data masking result is b124. If the security domain is set to 1, the data masking result is c234. In a security domain, the same data masking result is returned for a data record at all times.
If you do not set the Sensitive Data Type parameter to a built-in sensitive field type, you must configure the Character Set for Replacement parameter for your data records.
Character Set for Replacement: You can enter the characters to be replaced. Separate multiple characters with commas (,). The characters can be letters or digits. If a data record contains a character that is specified in this field, the character is replaced with another character of the same type. For example, if a data record contains digits from 0 to 3 and letters from a to d, the data masking result also contains only characters within these ranges. If a character is not included in this field, the character is not replaced.
Hashing
This method encrypts a data record to generate a hash value of a fixed length. If you select this method, you must configure the Security Domain parameter.
Security Domain: You can select a digit from 0 to 9 from the Security Domain drop-down list. Data masking policies vary based on the security domain. Different data masking results are returned for the same data record in different security domains. For example, if the data record is a123 and the security domain is set to 0, the data masking result is b124. If the security domain is set to 1, the data masking result is c234. In a security domain, the same data masking result is returned for a data record at all times.
Redaction
This method replaces each of the characters at specific positions of a data record with an asterisk (*).
Recommendation Method: You can select Show Only First and Last Character, Show Only First Three and Last Two Characters, and Show Only First Three and Last Four Characters from the Recommendation Method drop-down list. By default, Show Only First and Last Character is selected.
Custom: You can flexibly specify whether to mask the specified number of characters at the first, middle, or last segment of a data value. You can add a maximum of 10 segments and specify Remaining Digits for at most one segment.
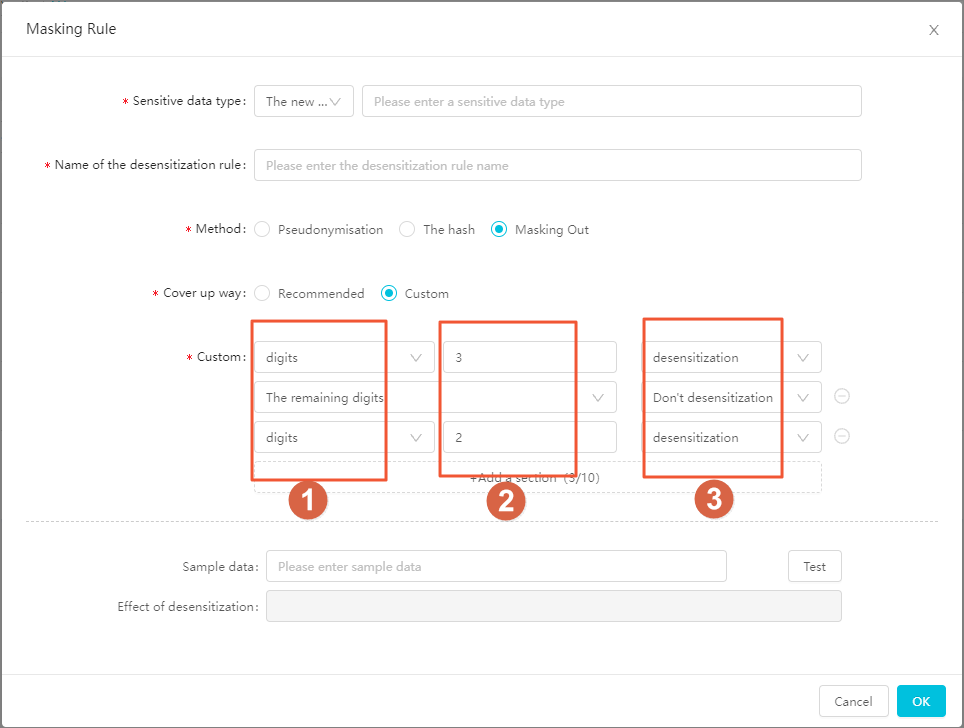
No.
Description
1
You can select Digits or Remaining Digits.
2
You can enter an integer from 1 to 100.
3
You can select Mask or Do Not Mask.
The following figure shows how to mask the first three characters and leave the remaining characters intact.
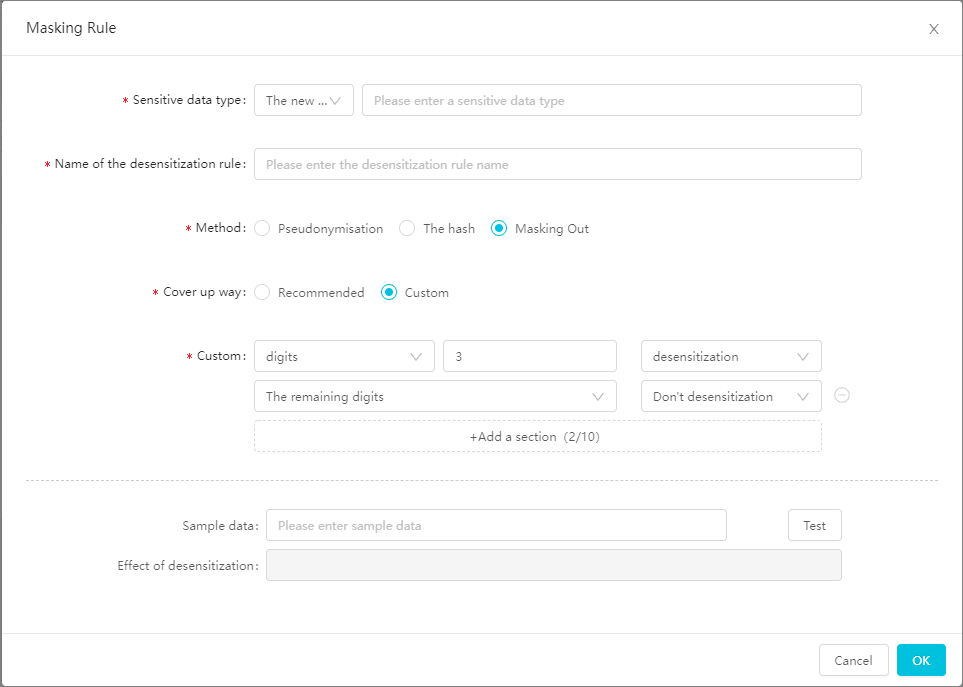
The following figure shows how to mask the last three characters and leave the remaining characters intact.
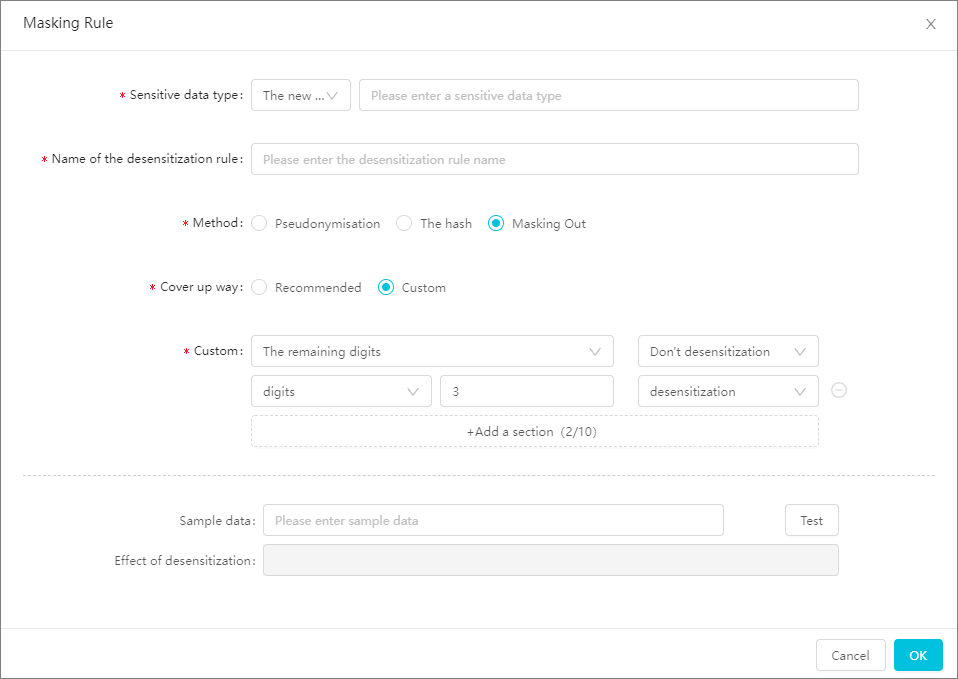
Verify the data masking rule. You can enter sample data in the Sample Data field. The sample data can be 0 to 100 characters in length. Click Test. The data masking result is displayed in the Data Masking Effect field.
Click OK. In the configuration panel, you can select this newly added rule from the Data Masking Rule drop-down list for a field to be masked. The newly created rule is also synchronized to Data Security Guard.
Click Add condition to add a row. In this row, you can configure the data masking rule for another field.
In the Field column, select an output field of the parent node of the data masking node from the drop-down list.
In the Data Masking Rule column, select a rule from the drop-down list. The rules that can be selected are those that have taken effect in Data Security Guard.
In the Actions column of a field, click the Edit icon.
If the data masking rule for this field is created by you, you can modify the rule in the Edit Data Masking Rule dialog box before you commit the real-time synchronization node. You can enter sample data to verify the rule.
If the data masking rule is not created by you, you can check the configuration details of the rule in the dialog box. You can also enter sample data to verify the rule.
In the Actions column of a field, click the Delete icon to delete the field.
In the Output Fields section, select the fields to be used as output fields from the fields of the original table.