This topic describes the security system of Alibaba Cloud Container Service (ACS) from three dimensions: runtime security, trusted software supply chain, and infrastructure security. The security system includes security inspection, policy management, runtime monitoring and alerts, image scanning, image signing, cloud-native application delivery chain, default security, identity management, and fine-grained access control.
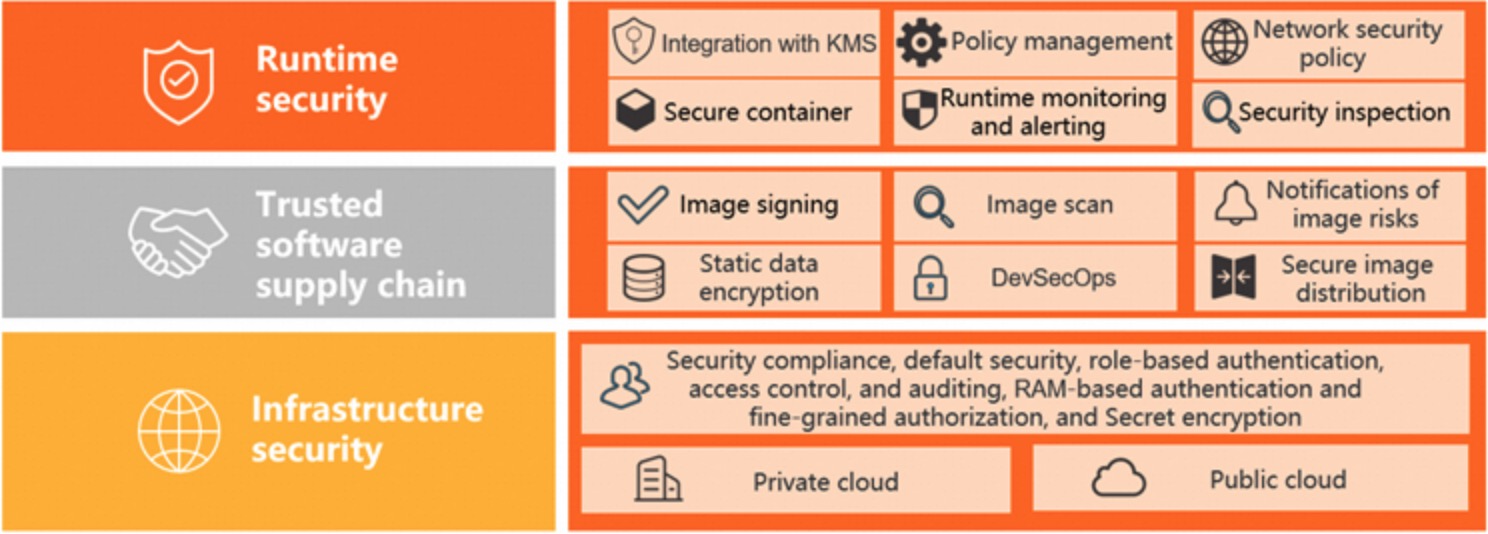
Runtime security
Secure sandbox management: The secure sandbox provides a new option of the container runtime that allows your applications to run in a lightweight virtual machine sandbox environment. This environment has an independent kernel and provides better security isolation. The secure sandbox is particularly suitable for scenarios such as untrusted application isolation, fault isolation, performance isolation, and multi-user load isolation. It has minimal impact on performance and offers the same user experience as Docker containers, such as logging, monitoring, and elasticity.
Trusted software supply chains
Image scanning
Container Registry supports security scanning for all Linux-based container images, which can identify known vulnerabilities within the images. You can receive corresponding vulnerability assessments and fix suggestions that reduce security risks. Container Registry also integrates with the cloud security scan engine. It supports the identification of system vulnerabilities, application vulnerabilities, and malicious samples in images.
Image signing
In container image management, the security and integrity of image sources can be guaranteed through a content trust mechanism. Image creators can apply a digital signature to the image, and this signature is stored in Container Registry. By verifying the signatures of container images before deployment, you can ensure that only trusted container images are deployed in the cluster. This reduces the risk of running unexpected or malicious code in your environment and ensures the security and traceability of application images throughout the deployment process.
Cloud-native application delivery chains
In secure and efficient delivery scenarios of the container, you can use the cloud-native application delivery chain of Container Registry to configure image building, image scanning, global image synchronization, image deployment, and customize fine-grained security policies to achieve full-link observable and traceable secure delivery. This ensures that code is submitted once and securely distributed and efficiently deployed across multiple regions globally, fully upgrading the DevOps delivery pipeline to DevSecOps. For more information, see Create a delivery chain.
Infrastructure security
Default security
The security of ACS cluster nodes and ControlPlane components are enhanced based on CIS Kubernetes Benchmarks. All system components within the cluster are hardened according to best practices of container security, which ensure that system component images do not have critical Common Vulnerabilities and Exposures (CVE) vulnerabilities.
The principle of least privilege is followed on the Worker nodes of managed clusters. Resource Access Management (RAM) users are granted minimal permissions to access other cloud resources. For more information, see ACS authorization best practices.
Identity management
All communication links between components within the ACS cluster require TLS certificate verification to ensure the security of data transmission across the entire link. ACS is responsible for the automatic update of certificates for cluster system components. RAM users or roles can obtain a kubeconfig file to connect to the specified cluster API Server through the console or OpenAPI. For specific operations, see Obtain cluster KubeConfig and connect to the cluster using kubectl. ACS is responsible for maintaining the identity information issued in the access credentials, and can revoke credentials. For specific operations, see Revoke the kubeconfig file of a cluster.
Fine-grained access control
Access control for Kubernetes resources within the ACS cluster is implemented based on the Role-Based Access Control (RBAC), which is a basic and necessary hardening measure to protect application security. ACS provides fine-grained RBAC authorization capabilities for the namespace on the Authorization management page in the console, which includes the following points.
RBAC permission templates: The system presets RBAC permission templates corresponding to administrators, operations, developers based on differernt permission requirements.
Batch authorization: Batch authorization for multiple clusters and multiple sub-accounts is supported.
RAM roles: The authorization for RAM roles is supported.
Custom ClusterRoles: Binding users to custom ClusterRoles within the cluster is supported. For more information, see Configure RBAC permissions for RAM users or RAM roles.
Secret Model encryption
The native Secret model of K8s is only encoded with Base64 when sensitive data is stored in etcd (Distributed Consistent Key-Value Store). However, in ACS clusters, the Secret Model of K8s can be encryted by using keys created in Alibaba Cloud Key Management Service (KMS) to achieve encryption of sensitive application data in disks.