Cloud Firewall is a security component for your workloads after you migrate to the cloud. It provides core features such as network-wide traffic identification, unified policy management, and intrusion detection. Cloud Firewall not only protects inbound traffic from the internet to your workloads but also controls outbound connections from your workloads to the internet and manages traffic between workloads. This topic outlines the best practices and procedures for using Cloud Firewall.
Best protection strategies
Module | Sub-category | Default status | Required Action |
Firewall Settings | Internet firewall (bidirectional) | Enabled for all resources within the quota. | None. If not all resources are enabled due to insufficient quota, you must increase the quota. |
VPC firewall | Not created, not enabled. | Manually create and enable. | |
NAT firewall | Not created, not enabled. | Manually create and enable. | |
IPS | Internet firewall | By default, Block - Medium mode. Automatically selected based on your workloads. | Adjustment is not recommended; the default configuration is sufficient. |
VPC firewall | None | Set the IPS block mode when you create the VPC firewall. It is automatically enabled when you enable the VPC firewall. | |
Access Control | Internet firewall | Allow all traffic. | Manually configure based on your workload requirements. |
VPC firewall | None | After enabling the VPC firewall, manually configure policies based on your workload requirements. | |
NAT firewall | None | After enabling the NAT Firewall, manually configure policies based on your workload requirements. | |
ECS firewall | None | Can be configured manually. | |
Alert Notification | Alert nNotification | Enabled, but recipients must be configured. | You must configure recipients. |
Multi-account Management | Multi-account management | None | Requires manual creation. |
Procedure

Prerequisite
You have purchased Cloud Firewall. For more information, see Purchase Cloud Firewall.
Step 1: Enable Cloud Firewall protection
Cloud Firewall is the umbrella term for Internet firewall, VPC firewall, ECS firewall, and NAT firewall. After you purchase the Cloud Firewall service, if you have not configured any access control policies or enabled the IPS in Block Mode, Cloud Firewall does not protect your service traffic.
Firewall Type | Description | Related documentation |
Internet firewall | Centrally manages traffic between public IP assets. | To enable the Internet firewall, seeInternet firewall. |
VPC firewall | Centrally manages traffic between network instances connected through Cloud Enterprise Network (CEN) and Express Connect. For the specific protection scope, see VPC firewall Firewall overview. Note VPC firewall is supported only by the Enterprise and Ultimate editions of Cloud Firewall. | To enable the VPC firewall, see Configure a VPC firewall for an Enterprise Edition transit router. |
ECS firewall | Controls inbound and outbound traffic between ECS instances to restrict unauthorized access. After you publish access control policies for the ECS firewall, they are automatically synchronized to ECS security groups and take effect. You do not need to enable the ECS firewall separately. Note ECS firewall is supported only by the Enterprise and Ultimate editions of Cloud Firewall. | To configure access control policies for the ECS firewall, see Create an access control policy for an internal firewall. |
NAT Firewall | Controls and protects traffic from private IP addresses to the public internet. | To enable the NAT Firewall, see NAT Firewall. |
After you enable or disable a firewall, the Firewall Status changes to Protected (indicates that protection is in effect) or Unprotected (indicates that protection is disabled). The Firewall Status change may take a few seconds. Please wait.
Step 2: Configure IPS capabilities
(Optional) Configure protection rules
Cloud Firewall includes a built-in Intrusion Prevention System (IPS) that issues real-time alerts or blocks intrusions and common attacks. It detects and protects against malicious files such as trojans and backdoors, detects malicious payload requests, and provides precise virtual patches to intelligently block intrusion risks. Its detection mechanism uses threat intelligence, intrusion detection rules, intelligent models, and virtual patching for comprehensive detection. For more information, see IPS configuration.
The IPS supports Monitor Mode (alerts only) and Block Mode (alerts and automatically blocks attack payloads). For different types of attacks, Cloud Firewall uses different strategies. Block Mode includes the following options:
Block-Loose: Blocks attacks using a conservative ruleset with a low false positive rate. This level is suitable for businesses that need to minimize false positives.
Block-Medium: Blocks attacks using standard common rules, providing a lower false positive rate than the Strict level; suitable for daily operations.
Block-Strict: Blocks attacks using all rules, minimizing false negatives, but may result in a higher false positive rate than the Medium level; suitable for businesses with strict security needs.
When changing protection settings, first enable Monitor Mode to allow for a trial period and false positive analysis before you enable Block Mode.
For more best practices on intrusion prevention, see:
View protection results
In the Cloud Firewall console, navigate to Detection & Response > IPS. On the Internet Protection or VPC Protection tab, you can view the intrusion blocking details for your assets, including the source IP, destination IP, blocked application, block source, and block event details. For more information, see Intrusion Prevention.
Step 3: View network traffic analysis
The Traffic Analysis feature provides real-time details about your hosts' outbound connections, internet exposure, and VPC-to-VPC access. Use this feature for visual traffic management and to troubleshoot abnormal traffic.
Outbound connections (outbound traffic)
The outbound connections page displays the domains and IP addresses your cloud assets are connecting to. Combined with threat intelligence tags, access details, and logs, you can identify and fill gaps in your outbound access control policies. For more information, see Outbound Connections.
Internet exposure (inbound traffic)
You can view your publicly exposed services, ports, public IP addresses, and cloud product information. This information, along with intelligent policy recommendations, helps you strengthen the security of your inbound access control policies. For more information, see Internet Exposure.
VPC access (internal traffic)
The VPC access page shows traffic trends, sessions, and open ports between VPCs. You can view and troubleshoot abnormal traffic to strengthen your VPC access control policies. For more information, see VPC Access.
Fully understand your assets' traffic patterns before you configure access control policies, as traffic analysis provides the necessary foundation.
Step 4: Configure access control policies
Cloud Firewall supports fine-grained access control for traffic from the internal network to the internet, from the internet to the internal network, and between internal networks, reducing the risk of asset intrusion.
By default, Cloud Firewall allows all traffic if no policies are configured. To configure access control policies, see the following topics:
Access control policy best practices
To enhance security, in addition to allowing necessary outbound connections, set all other outbound traffic to Deny.
If the source address of an outbound policy is a private IP address, ensure that a NAT Firewall has been created; otherwise, the outbound policy will not take effect. For more information, see NAT Firewall.
Type | Direction | Best practice | Related documentation |
Internet firewall | Outbound | Internet firewall policies control outbound traffic from cloud assets to the internet. The recommended approach is to configure a high-priority policy to allow necessary internet access, then add a low-priority policy to deny all other outbound traffic. This practice ensures controlled external connections, allowing only specific assets to access the internet. Before you configure an Internet firewall policy, ensure the firewall switch is enabled; otherwise, the policy will not take effect. First, create an outbound access control policy to allow trusted internal source IPs, and set its priority to the highest. Then, create a second outbound access control policy to deny all other source IPs from accessing the internet, and set its priority to the lowest. If there are multiple source IPs, destination IPs, or ports, use address books or create multiple policies. | Configure an access control policy to only allow inbound traffic on a specific port |
Inbound | Internet firewall access control policies for external-to-internal traffic control inbound traffic to your cloud services. The recommended practice is to first configure a policy to allow access to your cloud services, and then configure a policy to deny all other sources, protocols, ports, and applications. This allows trusted traffic while denying suspicious or malicious traffic, ensuring controlled risk management. Before you configure an Internet firewall policy, ensure the firewall switch is enabled; otherwise, the policy will not take effect. First, create an inbound access control policy to allow trusted external source IPs, and set its priority to the highest. Then, create a second inbound access control policy to deny all other source IPs from accessing the internal network, and set its priority to the lowest. If there are multiple source IPs, destination IPs, or ports, use address books or create multiple policies. | ||
NAT firewall | Outbound | After you enable the NAT Firewall, it inspects all outbound traffic from private resources within a VPC (including resources in the same VPC and across VPCs) that flows through the NAT gateway. The NAT Firewall matches traffic elements such as source, destination address, port, protocol, application, and domain against your configured access control policies and the built-in threat intelligence library. It determines whether the traffic meets the criteria to be allowed, thereby restricting unauthorized access from private resources to the internet. | Policy configuration tutorial to only allow private hosts to access specified domains |
VPC firewall | Inter-VPC | VPC firewall access control policies manage traffic between two VPCs. The recommended practice is to first configure a policy to allow trusted IP access to the VPC, and then configure a policy to deny access from other addresses. The VPC firewall is used to inspect and control traffic between two VPCs. After it is enabled, it allows all traffic by default. First, create a VPC firewall policy to allow trusted traffic, and set its priority to the highest. Then, create a second VPC firewall deny policy to block all other sources from accessing the internal network, and set its priority to the lowest. | |
ECS firewall | Inbound/Outbound | The ECS firewall provides access control for inbound and outbound traffic between ECS instances, enabling more granular restriction of unauthorized access. After ECS firewall access control policies are published, they are automatically synchronized to ECS security groups and take effect. The general recommendation is to first configure policies to allow access to cloud services, and then configure policies to deny all other sources, protocols, ports, and applications. Policy groups are divided into Basic Security Groups and Enterprise Security Groups. If you have a small number of ECS instances, you can use Basic Security Groups, which are the standard ECS security groups. If you have a large number of ECS instances, use Enterprise Security Groups. They offer significant advantages over basic groups: they can include more instances, have no limit on the number of private IP addresses within the group, and provide a more streamlined rule configuration for easier maintenance. This is suitable for enterprise users with high demands on scale and operational efficiency. | Firewall (between ECS instances) policy configuration example |
View access control policy hits
After an access control policy is configured, it takes effect immediately by default. Go to the Cloud Firewall console, navigate to the Access Control > Internet Border page, and view the policy's hit status in the Hits/Last Hit Time column of the access control policy list. For more information, see Configure Internet firewall access control policies.
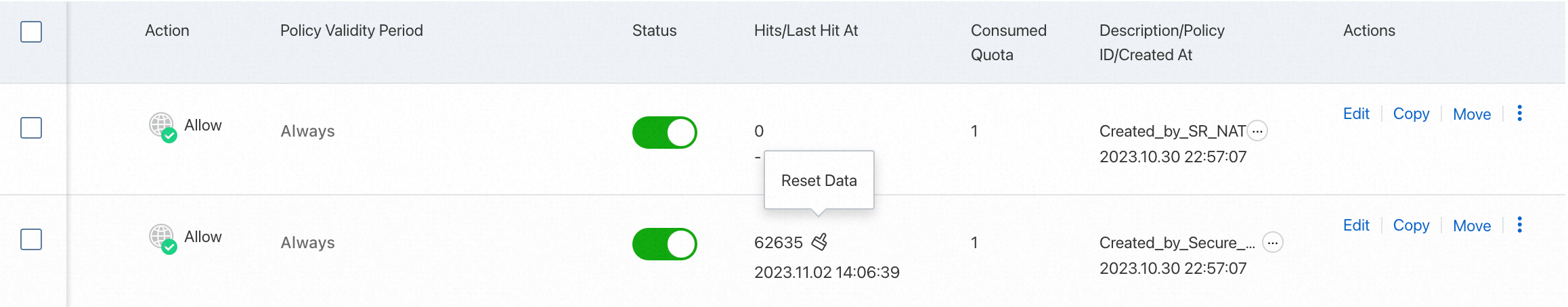
If the Hits/Last Hit Time column displays a hit count and time, it means that traffic has matched the policy. You can click the hit count to go to the Traffic Log page for detailed data. For more information, see Log audit.
Step 5: Configure alert notifications
To stay informed and respond quickly to protect your assets, configure alert notifications to receive timely alerts when asset risks occur or new assets are added.
For the alert types supported by Cloud Firewall and how to set them up, see Alert Notification.
Related topics
Having issues with abnormal events in Traffic Analysis? See the Traffic Analysis FAQ for troubleshooting guidance.
How can I troubleshoot abnormal IPS events? Refer to the IPS FAQ for common solutions.
Log analysis provides a one-stop service for real-time collection, query, analysis, processing, and consumption of traffic logs from protected assets. For more information, see Log Analysis.
Multi-account Management enables centralized management of resources. For more information, see Multi-account Management.