If your Internet-facing asset directly accesses the Internet, risks may occur. For example, data of your core business may be leaked, and your business system may be attacked. To prevent unauthorized access between the Internet-facing asset and the Internet, you can configure access control policies for the Internet firewall. This helps protect against potential data leaks and exposure of the asset on the Internet. This topic describes how to configure access control policies to allow traffic from a server only to a specific website.
Example scenario
In the following example, your asset is an Elastic Compute Service (ECS) instance with which the elastic IP address (EIP) 47.100.XX.XX is associated. To ensure the security of the ECS instance, you must configure access control policies to allow traffic only to the website www.aliyun.com.

Prerequisites
Cloud Firewall is activated, and the Internet Firewall feature is enabled. For more information, see Purchase Cloud Firewall and Internet Firewall.
Procedure
Log on to the Cloud Firewall console.
In the left-side navigation pane, choose .
On the Outbound tab, click Create Policy. In the Create Outbound Policy panel, click the Create Policy tab.
Configure an access control policy that allows traffic from the ECS instance to www.aliyun.com and has the highest priority and an access control policy that denies traffic from the ECS instance to all public IP addresses and has the lowest priority.
Configure the access control policy that allows traffic from the ECS instance to www.aliyun.com. The following table describes the parameters.
Parameter
Description
Example
Source Type
The initiator of network traffic. You must select a source type and enter source addresses based on the selected source type.
IP
Source
47.100.XX.XX/32, which is the public IP address of the ECS instance
Destination Type
The receiver of network traffic. You must select a destination type and enter destination addresses to which network traffic is sent based on the selected destination type.
Domain Name
Destination
www.aliyun.com, which is the website that you allow the ECS instance to access
NoteYou can also resolve the domain name into an IP address.
Protocol Type
The transport layer protocol. Valid values: TCP, UDP, ICMP, and ANY. If you do not know the protocol type, select ANY.
TCP
Port Type
The port type and port number of the destination.
Port
Port
0/0, which indicates all ports
Application
The application type of the traffic.
ANY
Action
The action on the traffic if the traffic meets the preceding conditions that you specify for the access control policy. Valid values:
Allow: The traffic is allowed.
Deny: The traffic is denied, and no notifications are sent.
Monitor: The traffic is recorded and allowed. You can filter traffic logs by specifying related fields and observe the traffic for a period of time. Then, change the policy action to Allow or Deny based on your business requirements.
Allow
Description
The description of the access control policy. Enter a description that can help identify the policy.
Allow traffic to www.aliyun.com
Priority
The priority of the access control policy. Default value: Lowest.
Highest
Policy Validity Period
The validity period of the access control policy. The policy can be used to match traffic only within the validity period. Valid values:
Always.
Single Time Range: If you select this option, specify a single time range.
Recurrence Cycle: If you select this option, specify the time range and date on which you want the policy to take effect.
NoteThe start date must be earlier than the end date. The policy requires 3 to 5 minutes to take effect.
If you select Indefinite Recurrence, the end date is automatically set to Dec 31, 2099.
Always
Enabling Status
Specify whether to enable the policy. If you turn off Status when you create an access control policy, you can enable the policy in the list of access control policies.
Enabled
Configure the access control policy to deny traffic from the ECS instance to all public IP addresses. The following list describes the parameters.
Source: Enter 47.100.X.X/32.
Destination: Enter 0.0.0.0/0, which indicates the IP addresses of all servers.
Protocol Type: Select ANY.
Port: Enter 0/0, which indicates all ports of servers.
Application: Select ANY.
Action: Select Deny.
Priority: Select Lowest.
After you create the access control policies, make sure that the priority of the policy that allows traffic from the ECS instance to www.aliyun.com is higher than the priority of the policy that denies traffic from the ECS instance to all public IP addresses.
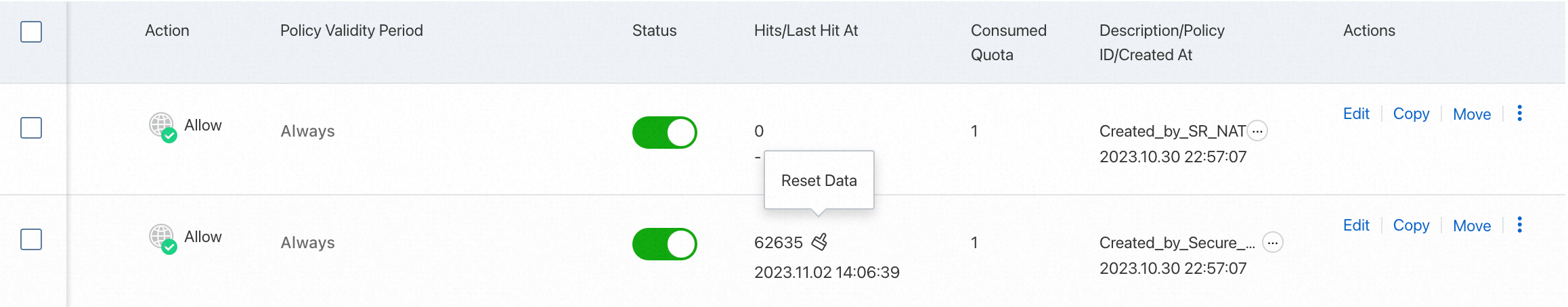
View the hit details about an access control policy
After your service runs for a period of time, you can view the hit details about an access control policy in the Hits/Last Hit At column in the list of access control policies.
You can click the number of hits to go to the Log Audit page to view traffic logs. For more information, see Log audit.
References
For more information, see Create inbound and outbound access control policies for the Internet firewall.
For more information, see Configure access control policies.
For more information about how to configure and use access control policies, see FAQ about access control policies.