By default, Enterprise Edition transit routers can forward IPv6 traffic, learn IPv6 routes, and advertise IPv6 routes. This topic describes how to use Enterprise Edition transit routers to establish IPv6 communication among VPCs in different regions.
You can run the sample code with one click.
Scenario

In this example, a company created an IPv4 VPC (VPC1) in the China (Hangzhou) region and an IPv4 VPC (VPC2) in the China (Shanghai) region. Both VPCs contain Elastic Compute Service (ECS) instances on which applications are deployed. To support business development, the company plans to establish IPv6 communication between the VPCs.
Procedure
This topic provides two configuration methods: console and Terraform. Choose the method that suits your needs.
Console
Preparations
An IPv4 VPC has been created in each of the China (Hangzhou) and China (Shanghai) regions. Applications are deployed on the ECS instances in the VPCs. For more information, see Create a VPC with an IPv4 CIDR block.
A Cloud Enterprise Network (CEN) instance has been created. For more information, see Create a CEN instance.
Step 1: Enable IPv6 for VPCs
To establish IPv6 communication for a VPC, you must enable the IPv6 feature. Perform the following steps to enable IPv6 for VPC1 and VPC2:
When creating a VPC instance, you can enable IPv6 for both the VPC and vSwitches. If the VPC and vSwitches already have the feature enabled and IPv6 CIDR blocks allocated, you can skip this step.
Log on to the VPC console.
In the top navigation bar, select the region where the VPC resides.
On the VPC page, find the VPC that you want to manage and click Enable IPv6 in the IPv6 CIDR Block column.
In the Enable IPv6 dialog box, set IPv6 CIDR Block Type to Assign BGP (Multi-ISP), select Automatically Enable IPv6 for All vSwitches, and then click OK.
If you do not select Automatically Enable IPv6 for All vSwitches, you must assign an IPv6 CIDR block to each vSwitch. For more information, see Enable IPv6 for a vSwitch.
After you enable IPv6 for the VPC and the vSwitches, the system assigns IPv6 CIDR blocks to the VPC and vSwitches. You can view the IPv6 CIDR blocks in the IPv6 CIDR Block column on the VPC or vSwitch page. The figure below shows how to view the IPv6 CIDR block of a VPC. The procedure for viewing the IPv6 CIDR block of a vSwitch is similar, so it will not be detailed in this section.
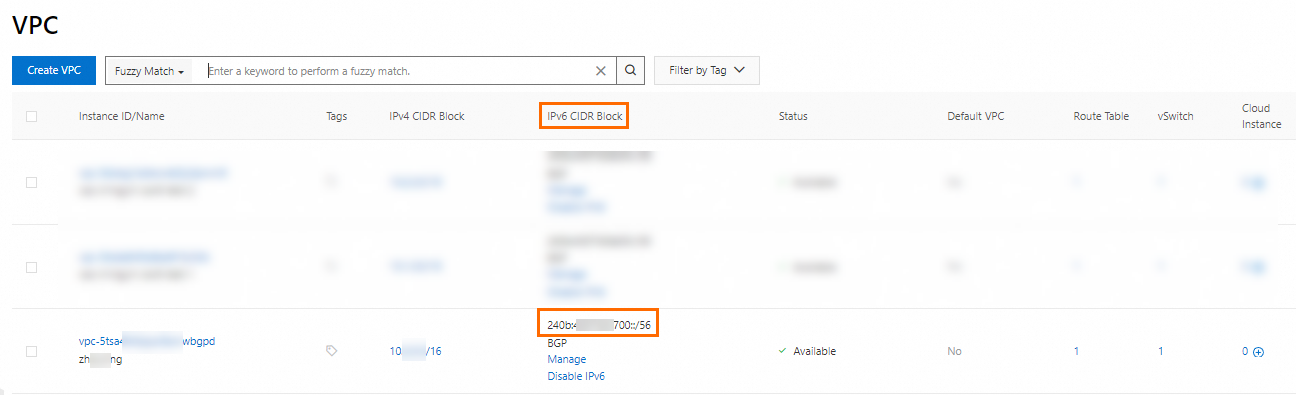
Step 2: Assign IPv6 addresses to the ECS instances
Before you establish IPv6 communication between resources, make sure that the resources are assigned IPv6 addresses. In this example, IPv6 addresses are assigned to ECS1 and ECS2, which use the 64-bit Alibaba Cloud Linux 3.2104 LTS operating system.
Assign an IPv6 address to each ECS instance. For more information, see Assign an IPv6 address to an existing instance.
NoteIf an IPv6 address has already been assigned when you create the ECS instance, you can skip this step.
Configure the IPv6 addresses for the ECS instances. For more information, see IPv6 communication.
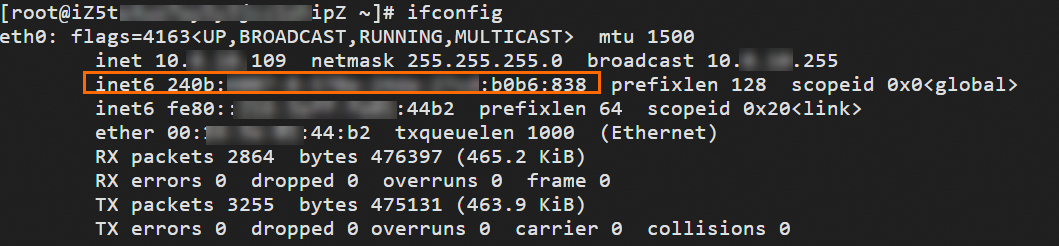
The following figure shows the IPv6 addresses of ECS1 and ECS2:
IPv6 address of ECS1
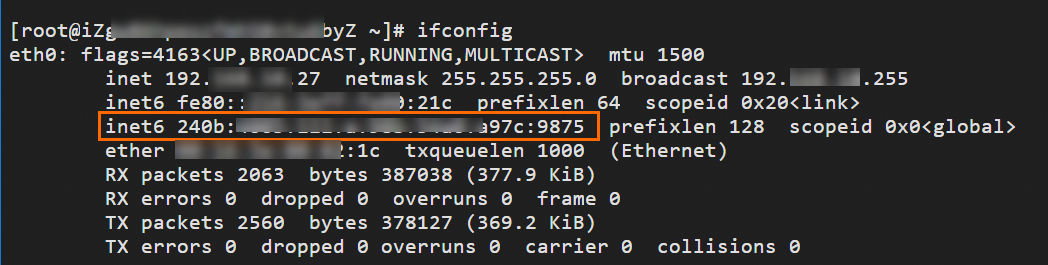
IPv6 address of ECS2
Step 3: Create transit routers
Create a transit router in each of the China (Hangzhou) and China (Shanghai) regions in the CEN instance. The transit routers are used to establish inter-region communication between the VPCs.
Log on to the CEN console.
On the Instances page, click the ID of the CEN instance that you want to manage.
Choose and click Create Transit Router.
In the Create Transit Router dialog box, configure the parameters and click OK.
Configure the Region parameter and keep other parameters at the default values. For more information, see Create a route router.
Step 4: Create VPC connections
Before you can establish communication between VPCs in different regions, you must connect the VPCs to the transit routers.
Log on to the CEN console.
On the Instances page, click the ID of the CEN instance that you want to manage.
On the tab, find the transit router created in Step 3 and click Create Connection in the Actions column.
On the Connection with Peer Network Instance page, configure the parameters and click OK.
Connect VPC1 to the transit router in the China (Hangzhou) region and VPC2 to the transit router in the China (Shanghai) region. The following table only describes parameters that are strongly related to the topic. Other parameters are kept at their default values. For more information, see Create a VPC connection.
Parameter
Description
VPC1
VPC2
Instance Type
Select VPC.
Region
Select the region of the network instance.
China (Hangzhou).
China (Shanghai).
IPv6
Specify whether to enable IPv6. IPv6 is disabled by default.
If you want to establish IPv6 communication for the VPC by using the Enterprise Edition transit router, enable IPv6.
NoteYou can enable IPv6 for existing VPC connections. For more information, see Enable IPv6 for an existing VPC connection.
Enable IPv6.
Enable IPv6.
Transit Router
The transit router in the selected region is automatically displayed.
Resource Owner ID
Select the Alibaba Cloud account to which the instance belongs.
Current Account.
Current Account.
Network Instance
Select the VPC that you want to connect to the transit router.
VPC1.
VPC2.
VSwitch
Select the vSwitches that are deployed in the zones of the transit router.
If the Enterprise Edition transit router is deployed in a region that supports only one zone, select one vSwitch in the zone.
If the Enterprise Edition transit router is deployed in a region that supports multiple zones, select at least two vSwitches. The two vSwitches must be in different zones to support zone-disaster recovery, This ensures uninterrupted data transmission between the VPC and the transit router.
We recommend that you select a vSwitch in each zone to reduce the network latency and improve network performance because data is transmitted over a shorter distance.
If there are no vSwitches in the zones, you must create vSwitches. For more information, see Create a vSwitch.
Advanced Settings
By default, the advanced features are enabled. In this example, the default settings are retained.
Step 5: Create an inter-region connection
After the VPCs are connected to the transit routers, you must create an inter-region connection to allow the VPCs to communicate with each other across regions.
Log on to the CEN console.
On the Instances page, click the ID of the CEN instance that you want to manage.
On the tab, find the transit router created in Step 3 and click Create Connection in the Actions column.
On the Connection with Peer Network Instance page, configure the parameters and click OK.
The following table describes parameters that are strongly related to the example. Other parameters are kept at their default values. For more information, see Use an Enterprise Edition transit router to create an inter-region connection.
Parameter
Description
Instance Type
Select Inter-region Connection.
Region
Select one of the regions to be connected.
In this example, China (Hangzhou) is selected.
Peer Region
Select the other region to be connected.
In this example, China (Shanghai) is selected.
Bandwidth Allocation Mode
Select the method that is used to allocate bandwidth to the inter-region connection.
In this example, Pay-By-Data-Transfer is selected. You are charged based on the amount of data transfer over the inter-region connection.
Bandwidth
Specify a maximum bandwidth value for the inter-region connection. Unit: Mbit/s.
If you select Pay-By-Data-Transfer, the Bandwidth parameter specifies the maximum bandwidth of the inter-region connection.
Default Line Type
Select a line type for the inter-region connection.
In this example, the default value is used. For more information about line types, see Line types.
Advanced Settings
By default, the advanced features are enabled. In this example, the default settings are retained.
Step 6: Enable route synchronization
By default, Enterprise Edition transit routers do not advertise IPv6 routes to VPCs. To allow the Enterprise Edition transit router to advertise IPv6 routes to VPC1 and VPC2, enable the route synchronization feature.
Log on to the CEN console.
On the Instances page, click the ID of the CEN instance that you want to manage.
On the tab, click the ID of the transit router in the China (Hangzhou) region.
On the Intra-region Connections tab, find the VPC1 connection and enable route synchronization in the Route Synchronization column.
Repeat this step to enable route synchronization for VPC2 on the transit router in the China (Shanghai) region.
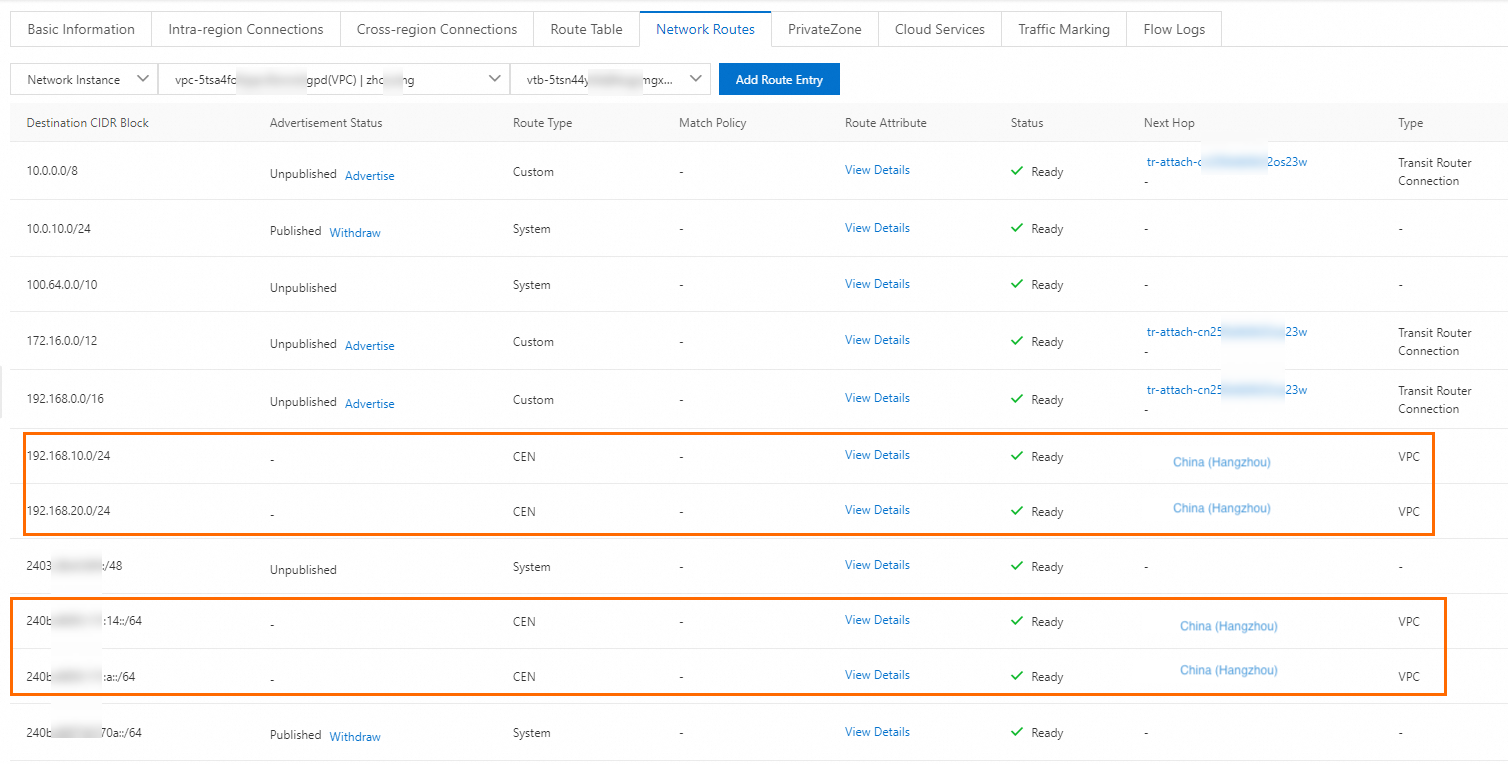
After you enable route synchronization, the Enterprise Edition transit router automatically synchronizes routes to network instances. You can click Details in the Route Synchronization column to view route synchronization details on the Network Routes tab.
Routes of VPC1
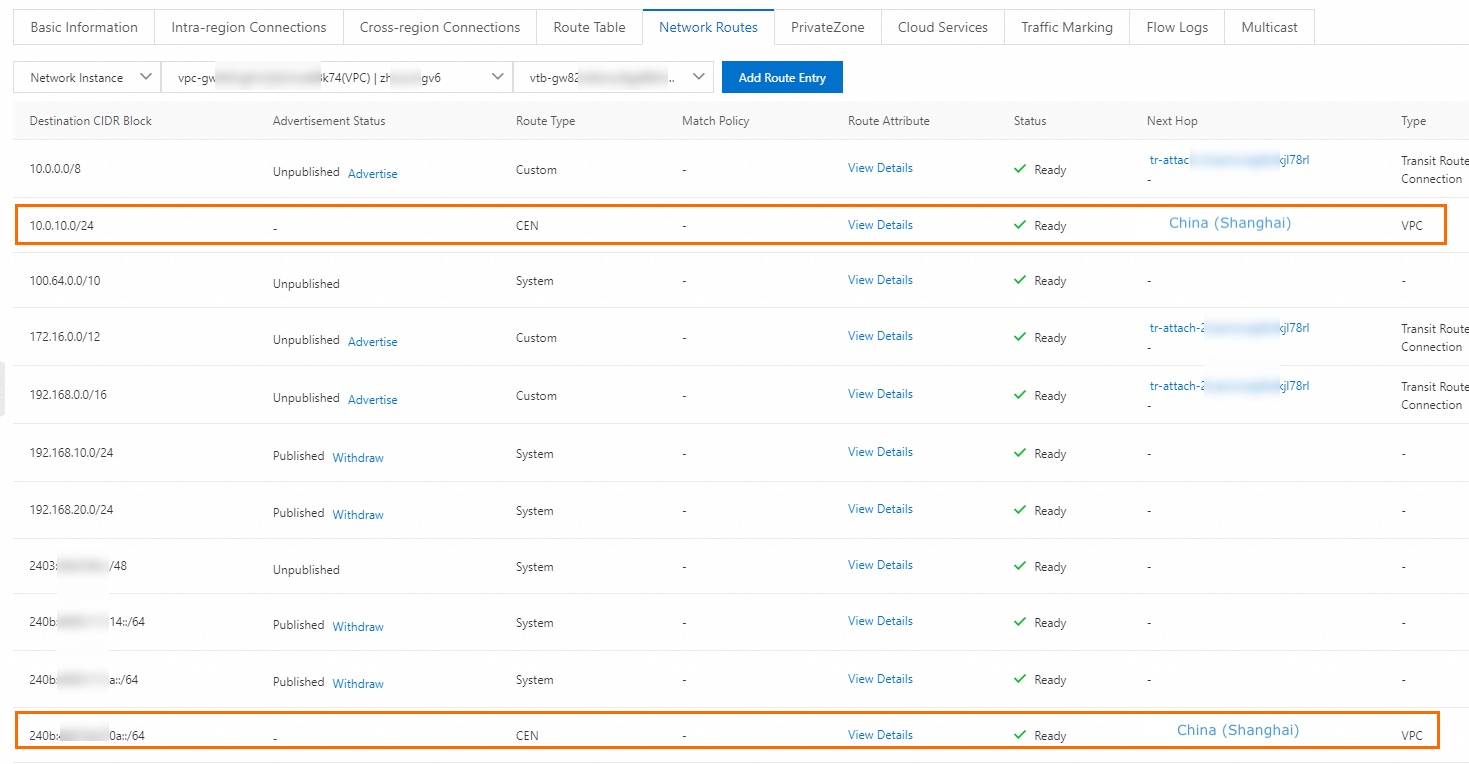
Routes of VPC2
Step 7: Test network connectivity
After you complete the preceding steps, VPC1 and VPC2 can communicate with each other over IPv6. This step tests the IPv6 network connectivity between the VPCs.
By default, the security group rules do not allow IPv6 communication. Before you perform this step, make sure that the security group rules of ECS1 and ECS3 allow IPv6 communication. For more information, see View security group rules and Add a security group rule.
For example, configure an allow rule in the inbound direction and set the protocol to ICMP (IPv6) and the authorization object to ::/0. Then, you can use this rule to test IPv6 network connectivity.
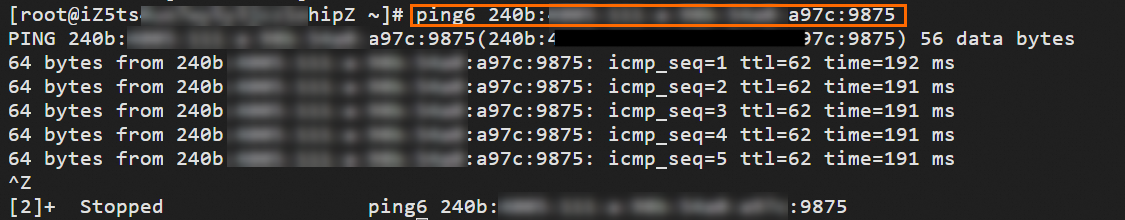
Log on to ECS1 in VPC1. For more information, see Methods for connecting to an ECS instance.
Run the following command to access ECS3 in VPC2 using the IPv6 address of ECS1.
ping6 <IPv6 address of ECS3>If ECS1 receives the following echo reply packet, the VPCs can communicate with each other over IPv6.
Terraform
You can use Terraform to set up the environment in this topic. For details on installing and configuring Terraform, see Install Terraform.
The steps below show how to run Terraform v1.9.8 on a Linux host. Make sure you have completed the Authentication.
Specific resources in this example may incur costs. Release or unsubscribe from the resources when they are no longer needed.
Step 1: Create resources
Create a directory for the scenario and navigate to it.
mkdir tf-CenIpv6 && cd tf-CenIpv6Create a
main.tffile to define resources.touch main.tfOpen the
main.tffile, paste the following code into the file, and save the changes. This file includes all the necessary resources and configurations.variable "pname" { description = "The prefix name for resources" type = string default = "tf-CenIpv6" } variable "default_region_id" { description = "The default region id" type = string default = "cn-hangzhou" } variable "hangzhou_region_id" { description = "The hangzhou region id" type = string default = "cn-hangzhou" } variable "shanghai_region_id" { description = "The shanghai region id" type = string default = "cn-shanghai" } variable "hangzhou_az_list" { description = "List of availability zones to use" type = list(string) default = ["cn-hangzhou-j", "cn-hangzhou-k"] } variable "shanghai_az_list" { description = "List of availability zones to use" type = list(string) default = ["cn-shanghai-m", "cn-shanghai-n"] } # --- provider --- provider "alicloud" { # default hangzhou region = var.default_region_id } provider "alicloud" { alias = "hangzhou" region = var.hangzhou_region_id } provider "alicloud" { alias = "shanghai" region = var.shanghai_region_id } # --- 2 vpc and 4 vsw --- resource "alicloud_vpc" "vpc1" { provider = alicloud.hangzhou vpc_name = "${var.pname}-vpc1" cidr_block = "10.0.0.0/16" enable_ipv6 = true } resource "alicloud_vpc" "vpc2" { provider = alicloud.shanghai vpc_name = "${var.pname}-vpc2" cidr_block = "172.16.0.0/16" enable_ipv6 = true } resource "alicloud_vswitch" "vsw1-1" { provider = alicloud.hangzhou vpc_id = alicloud_vpc.vpc1.id cidr_block = "10.0.0.0/24" zone_id = var.hangzhou_az_list[0] vswitch_name = "${var.pname}-vsw1-1" enable_ipv6 = true ipv6_cidr_block_mask = 1 # existed } resource "alicloud_vswitch" "vsw1-2" { provider = alicloud.hangzhou vpc_id = alicloud_vpc.vpc1.id cidr_block = "10.0.1.0/24" zone_id = var.hangzhou_az_list[1] vswitch_name = "${var.pname}-vsw1-2" enable_ipv6 = true ipv6_cidr_block_mask = 2 } resource "alicloud_vswitch" "vsw2-1" { provider = alicloud.shanghai vpc_id = alicloud_vpc.vpc2.id cidr_block = "172.16.0.0/24" zone_id = var.shanghai_az_list[0] vswitch_name = "${var.pname}-vsw2-1" enable_ipv6 = true ipv6_cidr_block_mask = 3 } resource "alicloud_vswitch" "vsw2-2" { provider = alicloud.shanghai vpc_id = alicloud_vpc.vpc2.id cidr_block = "172.16.1.0/24" zone_id = var.shanghai_az_list[1] vswitch_name = "${var.pname}-vsw2-2" enable_ipv6 = true ipv6_cidr_block_mask = 4 } # --- ecs1 --- resource "alicloud_instance" "ecs1" { provider = alicloud.hangzhou instance_name = "${var.pname}-ecs1" instance_type = "ecs.e-c1m1.large" security_groups = [alicloud_security_group.sg1.id] vswitch_id = alicloud_vswitch.vsw1-1.id image_id = "aliyun_3_x64_20G_qboot_alibase_20230727.vhd" system_disk_category = "cloud_essd" private_ip = "10.0.0.1" ipv6_address_count = 1 instance_charge_type = "PostPaid" user_data = base64encode(<<-EOT #!/bin/bash echo ecs_ok > /root/ok.txt sudo acs-plugin-manager --exec --plugin=ecs-utils-ipv6 EOT ) } # --- ecs2 --- resource "alicloud_instance" "ecs2" { provider = alicloud.shanghai instance_name = "${var.pname}-ecs2" instance_type = "ecs.e-c1m1.large" security_groups = [alicloud_security_group.sg2.id] vswitch_id = alicloud_vswitch.vsw2-1.id image_id = "aliyun_3_x64_20G_qboot_alibase_20230727.vhd" system_disk_category = "cloud_essd" private_ip = "172.16.0.1" ipv6_address_count = 1 instance_charge_type = "PostPaid" user_data = base64encode(<<-EOT #!/bin/bash echo ecs_ok > /root/ok.txt sudo acs-plugin-manager --exec --plugin=ecs-utils-ipv6 EOT ) } # sg resource "alicloud_security_group" "sg1" { provider = alicloud.hangzhou name = "${var.pname}-sg1" vpc_id = alicloud_vpc.vpc1.id } resource "alicloud_security_group_rule" "allow_inbound_ssh1" { provider = alicloud.hangzhou type = "ingress" ip_protocol = "tcp" nic_type = "intranet" policy = "accept" port_range = "22/22" priority = 1 security_group_id = alicloud_security_group.sg1.id cidr_ip = "0.0.0.0/0" } resource "alicloud_security_group_rule" "allow_inbound_icmp1" { provider = alicloud.hangzhou type = "ingress" ip_protocol = "icmp" nic_type = "intranet" policy = "accept" port_range = "-1/-1" priority = 1 security_group_id = alicloud_security_group.sg1.id cidr_ip = "0.0.0.0/0" } resource "alicloud_security_group_rule" "allow_inbound_ipv6_icmp1" { provider = alicloud.hangzhou type = "ingress" ip_protocol = "all" nic_type = "intranet" policy = "accept" port_range = "-1/-1" priority = 1 security_group_id = alicloud_security_group.sg1.id ipv6_cidr_ip = "::/0" } resource "alicloud_security_group" "sg2" { provider = alicloud.shanghai name = "${var.pname}-sg2" vpc_id = alicloud_vpc.vpc2.id } resource "alicloud_security_group_rule" "allow_inbound_ssh2" { provider = alicloud.shanghai type = "ingress" ip_protocol = "tcp" nic_type = "intranet" policy = "accept" port_range = "22/22" priority = 1 security_group_id = alicloud_security_group.sg2.id cidr_ip = "0.0.0.0/0" } resource "alicloud_security_group_rule" "allow_inbound_icmp2" { provider = alicloud.shanghai type = "ingress" ip_protocol = "icmp" nic_type = "intranet" policy = "accept" port_range = "-1/-1" priority = 1 security_group_id = alicloud_security_group.sg2.id cidr_ip = "0.0.0.0/0" } resource "alicloud_security_group_rule" "allow_inbound_ipv6_icmp2" { provider = alicloud.shanghai type = "ingress" ip_protocol = "all" nic_type = "intranet" policy = "accept" port_range = "-1/-1" priority = 1 security_group_id = alicloud_security_group.sg2.id ipv6_cidr_ip = "::/0" } # --- cen and tr --- resource "alicloud_cen_instance" "cen1" { cen_instance_name = "${var.pname}-cen1" } resource "alicloud_cen_transit_router" "tr1" { provider = alicloud.hangzhou transit_router_name = "${var.pname}-tr1" cen_id = alicloud_cen_instance.cen1.id } resource "alicloud_cen_transit_router" "tr2" { provider = alicloud.shanghai transit_router_name = "${var.pname}-tr2" cen_id = alicloud_cen_instance.cen1.id } # get tr sys table id data "alicloud_cen_transit_router_route_tables" "tr1" { # get tr sys table transit_router_id = alicloud_cen_transit_router.tr1.transit_router_id transit_router_route_table_type = "System" } data "alicloud_cen_transit_router_route_tables" "tr2" { transit_router_id = alicloud_cen_transit_router.tr2.transit_router_id transit_router_route_table_type = "System" } # tr-peer resource "alicloud_cen_transit_router_peer_attachment" "peer" { provider = alicloud.hangzhou cen_id = alicloud_cen_instance.cen1.id transit_router_id = alicloud_cen_transit_router.tr1.transit_router_id peer_transit_router_region_id = var.shanghai_region_id peer_transit_router_id = alicloud_cen_transit_router.tr2.transit_router_id bandwidth_type = "DataTransfer" bandwidth = 1 auto_publish_route_enabled = true # default is false } resource "alicloud_cen_transit_router_route_table_association" "ass_peer1" { transit_router_route_table_id = data.alicloud_cen_transit_router_route_tables.tr1.tables[0].id transit_router_attachment_id = alicloud_cen_transit_router_peer_attachment.peer.transit_router_attachment_id } resource "alicloud_cen_transit_router_route_table_propagation" "propa_peer1" { transit_router_route_table_id = data.alicloud_cen_transit_router_route_tables.tr1.tables[0].id transit_router_attachment_id = alicloud_cen_transit_router_peer_attachment.peer.transit_router_attachment_id } resource "alicloud_cen_transit_router_route_table_association" "ass_peer2" { transit_router_route_table_id = data.alicloud_cen_transit_router_route_tables.tr2.tables[0].id transit_router_attachment_id = alicloud_cen_transit_router_peer_attachment.peer.transit_router_attachment_id } resource "alicloud_cen_transit_router_route_table_propagation" "propa_peer2" { transit_router_route_table_id = data.alicloud_cen_transit_router_route_tables.tr2.tables[0].id transit_router_attachment_id = alicloud_cen_transit_router_peer_attachment.peer.transit_router_attachment_id } # cidr_list variable "cidr_list" { description = "The list of Private CIDR block" type = list(string) default = ["10.0.0.0/8", "172.16.0.0/12", "192.168.0.0/16"] } # attach1 resource "alicloud_cen_transit_router_vpc_attachment" "attach1" { provider = alicloud.hangzhou cen_id = alicloud_cen_instance.cen1.id transit_router_id = alicloud_cen_transit_router.tr1.transit_router_id vpc_id = alicloud_vpc.vpc1.id zone_mappings { zone_id = var.hangzhou_az_list[0] vswitch_id = alicloud_vswitch.vsw1-1.id } zone_mappings { zone_id = var.hangzhou_az_list[1] vswitch_id = alicloud_vswitch.vsw1-2.id } transit_router_vpc_attachment_name = "attach1" transit_router_vpc_attachment_options = { ipv6Support : "enable" } auto_publish_route_enabled = true # default is false } resource "alicloud_cen_transit_router_route_table_association" "ass1" { transit_router_route_table_id = data.alicloud_cen_transit_router_route_tables.tr1.tables[0].id transit_router_attachment_id = alicloud_cen_transit_router_vpc_attachment.attach1.transit_router_attachment_id } resource "alicloud_cen_transit_router_route_table_propagation" "propa1" { transit_router_route_table_id = data.alicloud_cen_transit_router_route_tables.tr1.tables[0].id transit_router_attachment_id = alicloud_cen_transit_router_vpc_attachment.attach1.transit_router_attachment_id } resource "alicloud_route_entry" "vpc1_to_tr1" { provider = alicloud.hangzhou count = 3 route_table_id = alicloud_vpc.vpc1.route_table_id destination_cidrblock = var.cidr_list[count.index] nexthop_type = "Attachment" nexthop_id = alicloud_cen_transit_router_vpc_attachment.attach1.transit_router_attachment_id } # attach2 resource "alicloud_cen_transit_router_vpc_attachment" "attach2" { provider = alicloud.shanghai cen_id = alicloud_cen_instance.cen1.id transit_router_id = alicloud_cen_transit_router.tr2.transit_router_id vpc_id = alicloud_vpc.vpc2.id zone_mappings { zone_id = var.shanghai_az_list[0] vswitch_id = alicloud_vswitch.vsw2-1.id } zone_mappings { zone_id = var.shanghai_az_list[1] vswitch_id = alicloud_vswitch.vsw2-2.id } transit_router_vpc_attachment_name = "attach2" transit_router_vpc_attachment_options = { ipv6Support : "enable" } auto_publish_route_enabled = true # default is false } resource "alicloud_cen_transit_router_route_table_association" "ass2" { transit_router_route_table_id = data.alicloud_cen_transit_router_route_tables.tr2.tables[0].id transit_router_attachment_id = alicloud_cen_transit_router_vpc_attachment.attach2.transit_router_attachment_id } resource "alicloud_cen_transit_router_route_table_propagation" "propa2" { transit_router_route_table_id = data.alicloud_cen_transit_router_route_tables.tr2.tables[0].id transit_router_attachment_id = alicloud_cen_transit_router_vpc_attachment.attach2.transit_router_attachment_id } resource "alicloud_route_entry" "vpc2_to_tr2" { provider = alicloud.shanghai count = 3 route_table_id = alicloud_vpc.vpc2.route_table_id destination_cidrblock = var.cidr_list[count.index] nexthop_type = "Attachment" nexthop_id = alicloud_cen_transit_router_vpc_attachment.attach2.transit_router_attachment_id } output "ecs1_login_address" { value = "https://ecs-workbench.aliyun.com/?from=EcsConsole&instanceType=ecs®ionId=${var.hangzhou_region_id}&instanceId=${alicloud_instance.ecs1.id}" } output "ecs2_login_address" { value = "https://ecs-workbench.aliyun.com/?from=EcsConsole&instanceType=ecs®ionId=${var.shanghai_region_id}&instanceId=${alicloud_instance.ecs2.id}" }Initialize the folder to complete Terraform setup.
terraform initCreate resources. Terraform will preview the resources to be created. After verification, enter
yesto initiate the creation process.terraform apply
Step 2: Test network connectivity
After completing the above steps, IPv6 network communication between VPC1 and VPC2 is now established. The following section describes how to test the IPv6 network connectivity between VPC instances:
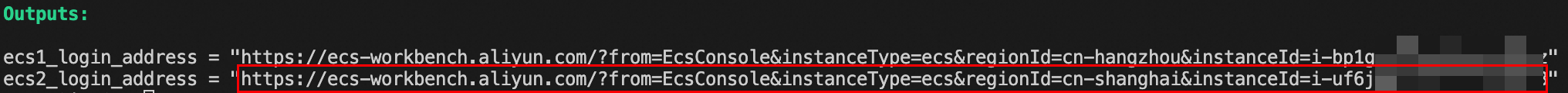
Log on to ECS2 (the instance name is
tf-CenIpv6-ecs2).The logon address for ECS2 is available in the Terraform Outputs. Copy this address into a browser to access it. Upon logging on, choose Temporary SSH Key-based as the method of authentication.
Run the following command in ECS2 to view the IPv6 address:
ifconfig
Log on to ECS1 (the instance name is
tf-CenIpv6-ecs1).The logon address for ECS1 is available in the Terraform Outputs. Copy this address into a browser to access it. Upon logging on, choose Temporary SSH Key-based as the method of authentication.
Run the following command to access ECS3 in VPC2 using the IPv6 address of ECS1.
ping6 <ECS2的IPv6地址>
If ECS1 receives the echo reply packets shown in the figure above, it indicates IPv6 communication is successful.
Stepp 3: Release resources
When verification is complete and you no longer need the resources, run the command below to release them and stop billing.
terraform destroy --auto-approve