If your accelerated domain name uses a private Alibaba Cloud Object Storage Service (OSS) bucket to authenticate access and prevent unauthorized traffic, enable the origin fetch feature for private OSS buckets. This lets you use CDN to accelerate resources in the private OSS bucket.
How it works and benefits
How it works: After you enable this feature, CDN automatically adds an
Authorizationfield to the header of each origin request sent to your private OSS bucket. The value of this field is a valid signature generated from the identity information you authorized, such as a Security Token Service (STS) temporary token or an AccessKey. OSS uses this signature to authenticate the request.Secure access: Grant CDN read-only permissions. This ensures the legitimacy of origin requests and avoids the security risks associated with making a private bucket public.
Cost optimization: When end-user requests are served by the CDN cache, traffic fees are significantly lower than those for outbound Internet traffic generated by direct access to OSS. Additionally, traffic from CDN to OSS is billed as origin traffic, which has a lower unit price than outbound Internet traffic from OSS. This effectively reduces your overall costs. For more information, see Billing of CDN-accelerated OSS resources.
Procedure
The configuration process involves two steps: first, perform a one-time authorization for your account, and then enable the feature for the specified accelerated domain name.
Grant CDN access to OSS. Before using this feature for the first time on any domain name in your account, grant CDN permission to access OSS. This is a one-time, account-level authorization. If you are not prompted to authorize, skip this step.
(Recommended) Authorization in the console
Log on to the CDN console.
In the navigation pane on the left, click Domain Names.
On the Domain Names page, find the domain name that you want to manage and click Manage.
In the navigation pane on the left for the domain name, click Origin Fetch.
In the Alibaba Cloud OSS Private Bucket Access section, click Authorize. On the authorization confirmation page, click Authorize.

Manual authorization via RAM
Log on to the RAM console.
In the navigation pane on the left, click Permission Management > Permission Policies.
On the Policies page, click Create Policy .
On the Script Editor tab, enter the following policy.
Click OK. On the Create Policy page, enter the following information and click OK.
Policy Name : AliyunCDNAccessingPrivateOSSRolePolicy
Note: This authorization policy is for the role used by CDN or DCDN to perform an origin fetch from a private OSS bucket. This policy grants read-only permissions to OSS.
{ "Version": "1", "Statement": [ { "Action": [ "oss:List*", "oss:Get*" ], "Resource": "*", "Effect": "Allow" } ] }In the left navigation pane, click Identity Management > Roles .
On the Roles page, click Create Role.
Set Principal Type to Alibaba Cloud Account, select Current Alibaba Cloud Account for Principal Name, and click OK.
In the Create Role step, enter the following information.
Role Name : AliyunCDNAccessingPrivateOSSRole
After the role is created, click AliyunCDNAccessingPrivateOSSRole in the role list on the Roles page to access the role details page.
On the Trust Policy tab, click Edit Trust Policy , enter the following information, and click OK .
You can switch to the Permission Management tab. Then, in the Grants tab, click Grant Permission.
Resource Scope: Account
Principal: Select the AliyunCDNAccessingPrivateOSSRole that you created.
For Authorization Policy, select Custom Policy. Then, select the AliyunCDNAccessingPrivateOSSRolePolicy you created and click Grant Permissions.
{ "Statement": [ { "Action": "sts:AssumeRole", "Effect": "Allow", "Principal": { "Service": [ "cdn.aliyuncs.com" ] } } ], "Version": "1" }Confirm New Authorization After you confirm the new authorization, return to the Origin Fetch page in the CDN console. You can see that the Alibaba Cloud OSS Private Bucket Access feature is now authorized.
Enable Alibaba Cloud OSS Private Bucket Access and configure the origin fetch type.
Find the Alibaba Cloud OSS Private Bucket Access section. Turn on its switch.
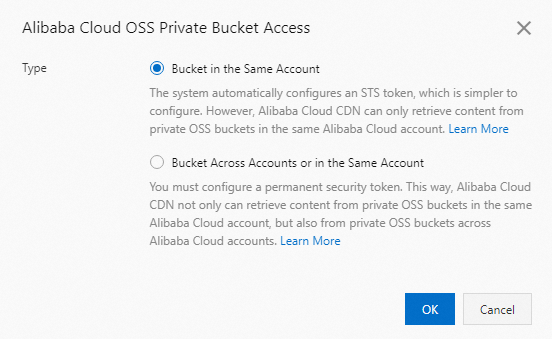
In the Alibaba Cloud OSS Private Bucket Access dialog box, select an origin fetch type. Click OK.
Origin fetch type
Recommended use case and description
Origin Fetch From Same Account
(Recommended) This is suitable for cases where CDN and the OSS bucket are under the same Alibaba Cloud account. The system automatically uses a temporary STS token for authentication. This simplifies configuration, eliminates the need to manage keys, and provides higher security.
STS temporary security tokens can also be used for cross-account origin fetch. For more information, see CDN: Using STS to Configure Cross-Account Origin Fetch for Private OSS Buckets.
Cross-Account or Same-Account Origin Fetch
This is suitable for cases where CDN and the OSS bucket belong to different Alibaba Cloud accounts. It also supports same-account scenarios. This method requires you to manually provide the AccessKey ID and AccessKey secret of the Alibaba Cloud account to which the destination private OSS bucket belongs. For more information, see Create an AccessKey pair.
NoteAccess scope: After you enable this feature, the accelerated domain name can access all resources in its origin private bucket. You cannot restrict access to specific resources within the bucket in CDN.
Signature conflicts: To prevent OSS authentication failures, ensure that origin requests do not contain signatures in both the request header and URL parameters.
Feature conflicts: This feature conflicts with the default index page configuration of the static website hosting feature in OSS. To use both features simultaneously, see the related document.
Security recommendations
After you enable origin fetch from a private bucket, your origin data is secure. However, the resources cached on POPs are publicly accessible by default. To prevent unauthorized use of CDN traffic, use the following security features provided by CDN:
Configure a Referer blacklist or whitelist: Restrict access to your CDN resources to requests from specific websites.
Configure URL signing: Set a dynamic signature and an expiration time for your resource URLs to effectively prevent malicious downloads.
Disable origin fetch from private OSS buckets
If you no longer want an accelerated domain name to access resources in a private bucket, revoke the authorization in the RAM console. This action revokes the permissions that allow CDN to perform origin fetch from the private OSS bucket.
Disable the feature in the CDN console.
Log on to the CDN console.
In the navigation pane on the left, click Domain Names.
On the Domain Names page, find the target domain name and click Manage.
In the navigation pane on the left for the domain name, click Origin Fetch.
In the Alibaba Cloud OSS Private Bucket Access section, turn off the Alibaba Cloud OSS Private Bucket Access switch.
Completely delete the authorization in the RAM console.
Log on to the RAM console.
In the navigation pane on the left, click
In the Role Name list, click AliyunCDNAccessingPrivateOSSRole.
Remove all permissions from the AliyunCDNAccessingPrivateOSSRole role.
Click Revoke Authorization to revoke the permission.
In the confirmation dialog box for removing permissions, click Revoke Permission.
Return to the page and delete the AliyunCDNAccessingPrivateOSSRole role.
Click Delete Role for the AliyunCDNAccessingPrivateOSSRole role.
In the Delete Role confirmation dialog box, click Delete Role .
On the page, delete the AliyunCDNAccessingPrivateOSSRolePolicy policy.
Click the Delete Policy button for the AliyunCDNAccessingPrivateOSSRolePolicy.
In the Delete Access Policy confirmation dialog box, you can enter the policy name and click Delete Access Policy.
FAQ
How do I resolve the This request is forbidden by kms. error when CDN accesses OSS resources?
If you use Key Management Service (KMS) to encrypt data in your OSS bucket, grant the CDN origin fetch role additional permissions to use the KMS key. Otherwise, CDN cannot decrypt or access these files, and a This request is forbidden by kms. error is returned.
Log on to the RAM console.
In the navigation pane on the left, choose
In the Role Name list, find the AliyunCDNAccessingPrivateOSSRole role.
Click Grant Permission, and the Principal is automatically populated.
Under Access Policy , select System Policy . Search for and click AliyunKMSCryptoUserAccess to add it to the Selected Access Policies box.
Click Grant Permissions. The status changes to Completed.
Click Close.

Use the Refresh Resources feature. After the refresh task is complete, try to access the resource again.
References
Best practices for using CDN to accelerate access to OSS resources