User Access Control
Access control decisions can be made by chaincode (and by the Hyperledger Fabric runtime) based upon an identity’s attributes. This is called Attribute-Based Access Control, or ABAC for short.When enrolling a user identity, the certificate (ECert) may contain one or more attribute name and value. The chaincode then extracts an attribute’s value to make an access control decision.
For example, suppose that you are developing application app1 and want a particular chaincode operation to be accessible only by app1 administrators. Your chaincode could verify that the caller’s certificate (which was issued by a CA trusted for the channel) contains an attribute named app1Admin with a value of true.
More information about Hyperledger Fabric ABAC, please refer: Attribute-Based Access Control.
Attribute Setting
When you create an organization user in the console, you can click “Superior” and set the user attributes.
Log on to the Alibaba Cloud BaaS console.
On the Overview page, locate My Organizations, locate the target organization, and click the name of the organization.
Click Users.
Click Add User, then click “Superior” and set the user attributes.
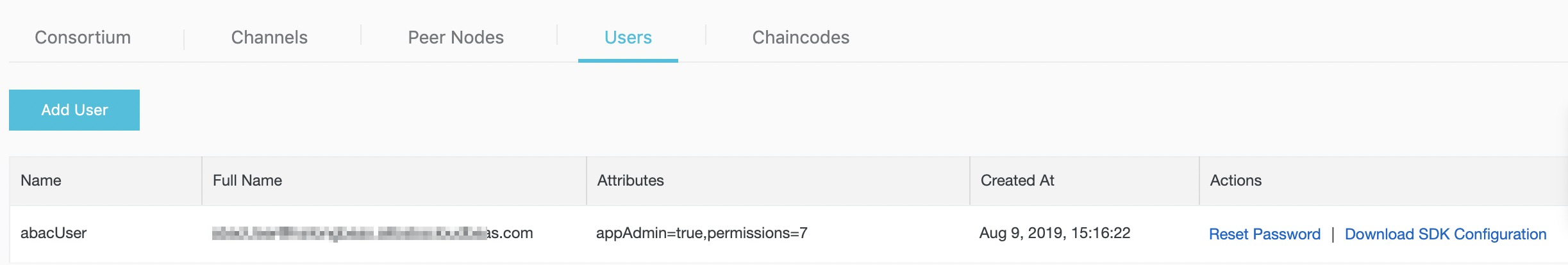
After creating the user, you can check the user attributes.
Attribute Setting Specification
Use delimiter “,” to split into different attributes
Use delimiter “=” to split into attribute name and value
Attribute name and value must consist of English letters or numbers
Attribute name and value are all string types
For example:
The attributes for “app1Admin=true,permissions=7” in user enrollment certificate will be:
{"attrs":{"app1Admin":"true","permissions":"7","hf.Affiliation":"","hf.EnrollmentID":"abacUser1","hf.Type":"client"}}Tips: The attributes hf.EnrollmentID, hf.Type and hf.Affiliation are automatically registered for every identity.
Extract user attributes in chaincode
More information, please refer: chaincode/shim/ext/cid
id, err := cid.New(stub)
fmt.Println("client ID object:")
fmt.Println(id)
if err != nil {
return shim.Error(err.Error())
}
val, ok, err = cid.GetAttributeValue(stub, "permissions")
if err != nil {
return shim.Error(err.Error())
}
if !ok {
return shim.Error("The client identity does not possess the attribute:permissions")
}
err := cid.AssertAttributeValue(stub, "permissions", "7")
if err != nil {
return shim.Error("The client identity does not have the permissions")
}
fmt.Println("permissions:")
fmt.Println(val)