Elastic Compute Service (ECS) instances or elastic container instances in a scaling group can be released at any time. In this case, we recommend that you store instance data on cloud databases to ensure persistent storage. This topic describes how to associate instances in a scaling group with cloud databases by adding the private IP addresses of the instances to the IP address whitelists of the cloud databases. This way, the instances can access the cloud databases.
Association methods
Method | Supported instance | Supported cloud database |
(Recommended) Method 1: Add instances and cloud databases to the same security group | ECS instances and elastic container instances |
|
ECS instances and elastic container instances |
| |
Method 3: Use the lifecycle hook feature together with an OOS template to implement the association | ECS instances |
|
(Recommended) Method 1: Add instances and cloud databases to the same security group
After you configure a security group for a cloud database, the private IP addresses of the ECS instances or elastic container instances in the security group are automatically added to the IP address whitelist of the cloud database. This ensures direct access from the ECS instances or elastic container instances to the cloud database.
Configure a security group for instances in a scaling group
The security group of instances in a scaling group is determined by the scaling configuration from which the instances are created. When you create or modify a scaling configuration, you can configure a security group. For more information, see Create a scaling configuration of the ECS type and Create a scaling configuration of the Elastic Container Instance type.
NoteIf you specify a launch template as the instance configuration source, change the security group configured in the launch template from which instances are created.
For an existing ECS instance, you can go to the Security Groups tab on the instance details page to change the security group. For an existing elastic container instance, you cannot manually change the security group. You must recreate an elastic container instance and configure the desired security group for the instance.
Configure a security group for a cloud database
You must configure the security group of instances for the cloud database that you want to use.
Cloud database | References |
ApsaraDB RDS | Configure a security group for an ApsaraDB RDS for MySQL instance |
PolarDB | |
Redis | Batch add public and private IP addresses of ECS instances by using security groups |
MongoDB |
Method 2: Associate a scaling group with cloud databases
After you associate a scaling group with a cloud database, the private IP addresses of the ECS instances or elastic container instances in the scaling group are automatically added to the IP address whitelist of the cloud database. This ensures direct access from the ECS instances or elastic container instances to the cloud database.
Associate an existing scaling group with cloud databases
Log on to the Auto Scaling console.
NoteThe first time you log on to Auto Scaling, follow the on-screen instructions to activate Auto Scaling and grant the required permissions. For more information, see Service-linked role.
In the top navigation bar, select the region where Auto Scaling is activated.
In the left-side navigation pane, click Scaling Groups.
On the Scaling Groups page, find the scaling group that you want to associate with cloud databases and click Edit in the Actions column. The Edit Scaling Group dialog box appears.
In the Edit Scaling Group dialog box, find the Associate with ApsaraDB RDS, Redis, or MongoDB parameter and click Add Database. Then, follow the on-screen instructions to add databases.
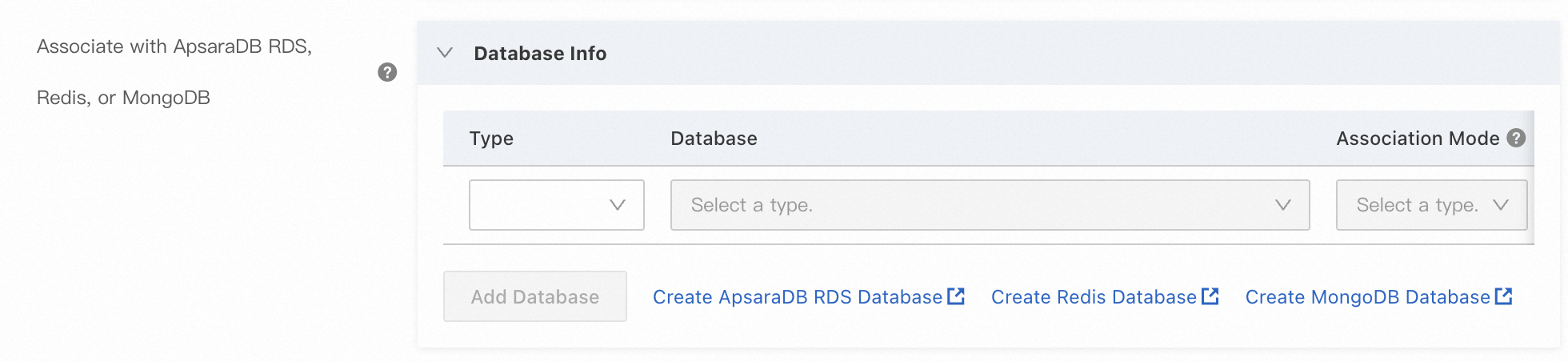
Click OK.
Associate databases with a scaling group when you create the scaling group
When you create a scaling group, configure the Associate with ApsaraDB RDS, Redis, or MongoDB parameter based on your business requirements.
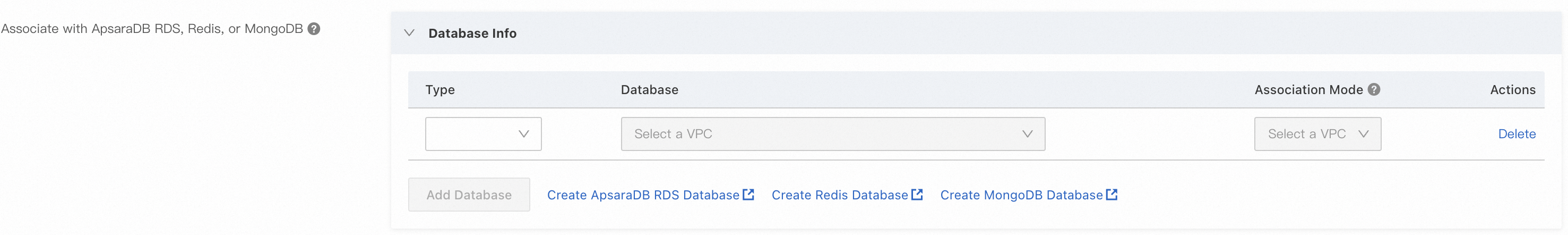
For information about how to create a scaling group, see Create a scaling group of the ECS type or Create a scaling group of the Elastic Container Instance type.
Method 3: Use the lifecycle hook feature together with an OOS template to implement the association
You can trigger a lifecycle hook to put the ECS instances that you want to scale out in a scaling group into the Pending Add state. Then, Auto Scaling automatically executes the predefined CloudOps Orchestration Service (OOS) template to add the private IP addresses of the ECS instances to the IP address whitelist of the desired cloud database. This ensures direct access from the ECS instances to the cloud database. For more information, see the following topics: