If you need to implement an end-to-end canary release for multiple services, you can configure traffic labels to identify traffic characteristics and divide the ingress traffic of a gateway into regular traffic and canary traffic. The canary traffic characteristics are passed among the services that are used to process user requests. This way, an end-to-end canary release is implemented. This topic describes how to use traffic labels to implement an end-to-end canary release for microservices.
Prerequisites
A Service Mesh (ASM) instance of Enterprise Edition or Ultimate Edition is created. The version of the ASM instance is 1.17.2.22 or later. For more information, see Create an ASM instance or Update an ASM instance.
The cluster is added to the ASM instance. For more information, see Add a cluster to an ASM instance.
An ingress gateway is created. For more information, see Create an ingress gateway.
Feature description
Canary releases can be implemented in various ways. For example, you can use ASM to deploy an application in blue-green release mode and phased release mode. The sample mode is applicable to the release of a single service. This mode uses VirtualService of open source Istio to specify the traffic weight of each version of the service. This mode cannot meet requirements in canary release scenarios of multiple services.
ASM provides the end-to-end canary release feature based on the traffic labeling and label-based routing features. This allows you to implement the canary release of multiple services at the same time. During canary testing of business, the system divides ingress traffic into regular traffic and canary traffic and identifies the characteristics of traffic. If the traffic of a request is identified as canary traffic, the request is routed to the canary release service. This way, the system no longer simply distributes traffic to backend services of different versions at specific traffic ratios. Instead, the canary traffic characteristics are passed among all the services that are used to process user requests. For more information, see Label traffic.
Configuration description
You can click here to download the sample configuration files. The following figure shows the call chains of the services in the example:
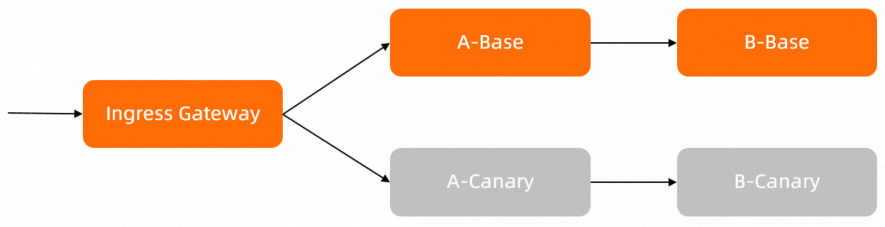
In this example, when Service A calls Service B, Service A contains the code implementation logic to pass the HTTP header my-trace-id. For more information, see the main.go configuration file in the src/mock-abc/go/main.go path.
If you use other applications, make sure that the applications contain the logic to pass the HTTP header. Subsequent functions rely on the HTTP header.
Step 1: Deploy sample services in the ACK cluster
Enable automatic sidecar proxy injection for the desired namespace (the default namespace in this example). For more information, see Enable automatic sidecar proxy injection.
Use kubectl to connect to the ACK cluster based on the information in the kubeconfig file and run the following commands to deploy sample services.
For more information about the YAML files, see Configuration description.
kubectl apply -n default -f application-base.yaml kubectl apply -n default -f application-canary.yaml
Step 2: Configure initial routing rules
Create a file named routing.yaml and copy the following content to the file:
Use kubectl to connect to the ASM instance based on the information in the kubeconfig file and run the following command to configure routing rules:
kubectl apply -n default -f routing.yamlCheck whether the services of different versions can be accessed.
Obtain the public IP address of the ingress gateway in the ASM console. For more information, see Step 2: Obtain the IP address of the ASM ingress gateway.
Run the following command to configure an environment variable.
xxxxis the IP address obtained in Substep a.export ASM_GATEWAY_IP=xxxxRun the following command to check whether the services of different versions can be accessed:
for i in {1..200}; do curl -H'my-asm-prefer-tag: version-base' -H'my-trace-id: x000'$i http://${ASM_GATEWAY_IP}/; echo; sleep 1; done;Expected output:
-> mocka(version: canary, ip: 172.17.0.129)-> mockb(version: base, ip: 172.17.0.70) -> mocka(version: base, ip: 172.17.0.132)-> mockb(version: base, ip: 172.17.0.70) -> mocka(version: base, ip: 172.17.0.132)-> mockb(version: canary, ip: 172.17.0.54) -> mocka(version: canary, ip: 172.17.0.129)-> mockb(version: canary, ip: 172.17.0.54) -> mocka(version: canary, ip: 172.17.0.129)-> mockb(version: base, ip: 172.17.0.70) -> mocka(version: base, ip: 172.17.0.132)-> mockb(version: base, ip: 172.17.0.70) -> mocka(version: canary, ip: 172.17.0.129)-> mockb(version: canary, ip: 172.17.0.54)The output shows that the routing policy of random load balancing is adopted for traffic flows from the ingress gateway to Service A and from Service A to Service B. The
my-asm-prefer-tagheader or other request headers specified by using thecurlcommand do not change the random routing policy.
Step 3: Configure traffic labels for the sample services
ASM allows you to configure traffic labels by using a TrafficLabel CustomResourceDefinition (CRD) and route traffic to different workloads based on the traffic labels. For more information, see Label traffic.
Create a file named trafficlabel.yaml and copy the following content to the file:
Configuration description:
The
trafficlabel-nstraffic label takes effect on all services in the default namespace, such as the mocka and mockb services deployed in this example. Theingressgatewaytraffic label takes effect only on the ingressgateway gateway.In this example, the
my-asm-prefer-tagrequest header is used to distinguish versions. Therefore, set the first parameter ingetExternalInboundRequestHeadertomy-asm-prefer-tag. Modify the configuration based on your business requirements.In this example,
my-trace-idis the HTTP header that needs to be passed. Therefore, set the second parameter ingetExternalInboundRequestHeadertomy-trace-id. Modify the configuration based on your business requirements.
Use kubectl to connect to the ASM instance based on the information in the kubeconfig file and run the following command to configure the traffic labels:
kubectl apply -f trafficlabel.yaml
Step 4: Configure label-based routing rules
You can configure label-based routing rules to control traffic flows.
1. Check the canary release on the service provider side
Check whether the traffic routing from Service A to Service B meets the expectation. To be specific, check whether the canary traffic that flows into Service A is forwarded to the canary release version of Service B, and whether the base traffic that flows into Service A is forwarded to the base version of Service B.
The following figure shows the traffic flows after the traffic label-based routing rule is configured for Service B: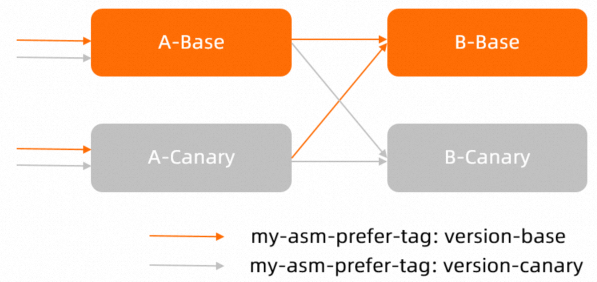
Create a file named vs-tf-mockb.yaml and copy the following content to the file:
apiVersion: networking.istio.io/v1beta1 kind: VirtualService metadata: name: vs-mockb spec: hosts: - mockb http: - route: - destination: host: mockb subset: $asm-labels-sampleRun the following command to make the routing rule take effect for Service A:
kubectl apply -n default -f vs-tf-mockb.yamlRun the following command to check whether the canary traffic that flows into Service A is forwarded to the canary release version of Service B:
for i in {1..200}; do curl -H'my-asm-prefer-tag: version-canary' -H'my-trace-id: x000'$i http://${ASM_GATEWAY_IP}/; echo; sleep 1; done;Expected output:
-> mocka(version: canary, ip: 172.17.0.129)-> mockb(version: canary, ip: 172.17.0.54) -> mocka(version: base, ip: 172.17.0.132)-> mockb(version: canary, ip: 172.17.0.54) -> mocka(version: base, ip: 172.17.0.132)-> mockb(version: canary, ip: 172.17.0.54) -> mocka(version: canary, ip: 172.17.0.129)-> mockb(version: canary, ip: 172.17.0.54) -> mocka(version: canary, ip: 172.17.0.129)-> mockb(version: canary, ip: 172.17.0.54) -> mocka(version: base, ip: 172.17.0.132)-> mockb(version: canary, ip: 172.17.0.54)Run the following command to check whether the base traffic that flows into Service A is forwarded to the base version of Service B:
for i in {1..200}; do curl -H'my-asm-prefer-tag: version-base' -H'my-trace-id: x000'$i http://${ASM_GATEWAY_IP}/; echo; sleep 1; done;Expected output:
-> mocka(version: canary, ip: 172.17.0.129)-> mockb(version: base, ip: 172.17.0.70) -> mocka(version: base, ip: 172.17.0.132)-> mockb(version: base, ip: 172.17.0.70) -> mocka(version: base, ip: 172.17.0.132)-> mockb(version: base, ip: 172.17.0.70) -> mocka(version: canary, ip: 172.17.0.129)-> mockb(version: base, ip: 172.17.0.70) -> mocka(version: base, ip: 172.17.0.132)-> mockb(version: base, ip: 172.17.0.70) -> mocka(version: canary, ip: 172.17.0.129)-> mockb(version: base, ip: 172.17.0.70) -> mocka(version: canary, ip: 172.17.0.129)-> mockb(version: base, ip: 172.17.0.70) -> mocka(version: base, ip: 172.17.0.132)-> mockb(version: base, ip: 172.17.0.70)The results show that the ingress canary traffic and ingress base traffic that flow into Service A are not routed to the expected versions of Service B. You need to configure a traffic label-based routing rule for Service A. For more information, proceed to the next step.
2. Check the end-to-end canary release feature
Configure a traffic label-based routing rule file named a-vs-tf.yaml for Service A and make the file take effect for the ingress gateway. The expected result is that the canary traffic of ingress requests is first forwarded to the canary release version of Service A and then to that of Service B, and the base traffic is first forwarded to the base version of Service A and then to that of Service B.
The following figure shows the traffic flows after the traffic label-based routing rule is configured for Service A: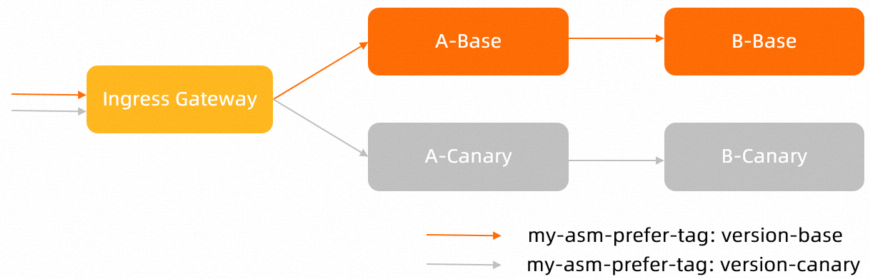
Create a file named vs-tf-mocka.yaml and copy the following content to the file:
apiVersion: networking.istio.io/v1beta1 kind: VirtualService metadata: name: vs-gateway-mocka spec: gateways: - simple-gateway hosts: - "*" http: - route: - destination: host: mocka subset: $asm-labels-sampleRun the following command to make the routing rule take effect for the ingress gateway:
kubectl apply -n default -f vs-tf-mocka.yamlRun the following command to check whether the canary traffic of ingress requests is first forwarded to the canary release version of Service A and then to that of Service B:
for i in {1..200}; do curl -H'my-asm-prefer-tag: version-canary' -H'my-trace-id: x000'$i http://${ASM_GATEWAY_IP}/; echo; sleep 1; done;Expected output:
-> mocka(version: canary, ip: 172.17.0.69)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: canary, ip: 172.17.0.69)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: canary, ip: 172.17.0.69)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: canary, ip: 172.17.0.69)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: canary, ip: 172.17.0.69)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: canary, ip: 172.17.0.69)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: canary, ip: 172.17.0.69)-> mockb(version: canary, ip: 172.17.0.130)Run the following command to check whether the base traffic of ingress requests is first forwarded to the base version of Service A and then to that of Service B:
for i in {1..200}; do curl -H'my-asm-prefer-tag: version-base' -H'my-trace-id: x000'$i http://${ASM_GATEWAY_IP}/; echo; sleep 1; done;Expected output:
-> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93)
3. Check whether the weight-based traffic distribution that corresponds to the traffic label-based routing meets the requirements
The following figure shows the traffic flows after the weight-based and traffic label-based routing rules are configured for Service A: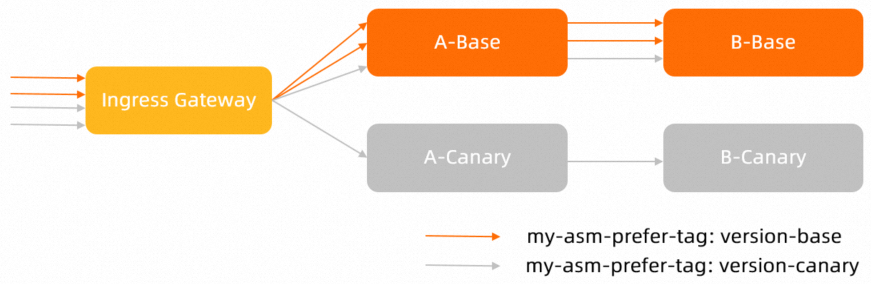
Create a file named vs-tf-mocka-90-10.yaml and copy the following content to the file:
apiVersion: networking.istio.io/v1beta1 kind: VirtualService metadata: name: vs-gateway-mocka spec: gateways: - simple-gateway hosts: - "*" http: - route: - destination: host: mocka subset: version-base weight: 90 - destination: host: mocka subset: $asm-labels-sample weight: 10Run the following command to make the routing rules take effect for the ingress gateway:
kubectl apply -n default -f vs-tf-mocka-90-10.yamlRun the following command to check whether the canary traffic of ingress requests is forwarded to the canary release and base versions of Service A:
for i in {1..200}; do curl -H'my-asm-prefer-tag: version-canary' -H'my-trace-id: x000'$i http://${ASM_GATEWAY_IP}/; echo; sleep 1; done;Expected output:
-> mocka(version: base, ip: 172.17.0.90)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: canary, ip: 172.17.0.130) -> mocka(version: canary, ip: 172.17.0.69)-> mockb(version: canary, ip: 172.17.0.130)The results show that about 90% of the canary traffic of ingress requests is forwarded to the base version of Service A and about 10% is forwarded to the canary release version of Service A. According to the above routing rules, about 90% of the request traffic is forwarded to the base version of Service A, and the remaining 10% is forwarded based on the value of the
my-asm-prefer-tagheader. The request command sets the value ofmy-asm-prefer-tagtoversion-canary. Therefore, 10% of the request traffic is forwarded to the canary release version of Service A.Run the following command to check whether all base traffic of ingress requests is forwarded to the base version of Service A:
for i in {1..200}; do curl -H'my-asm-prefer-tag: version-base' -H'my-trace-id: x000'$i http://${ASM_GATEWAY_IP}/; echo; sleep 1; done;Expected output:
-> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93) -> mocka(version: base, ip: 172.17.0.90)-> mockb(version: base, ip: 172.17.0.93)According to the above routing rules, about 90% of the request traffic is forwarded to the base version of Service A, and the remaining 10% is forwarded based on the value of the
my-asm-prefer-tagheader. The request command sets the value ofmy-asm-prefer-tagtoversion-base. Therefore, 10% of the request traffic is forwarded to the base version of Service A.