Service Mesh (ASM) comes with multiple built-in monitoring metrics and multiple dimensions to help you better understand the real-time running of your applications. With powerful extension mechanism, ASM allows you to specify processing logics based on request or response content and add the processing results to the dimensions of monitoring metrics. This topic describes how to use the Wasm plug-in to add custom dimensions to the existing monitoring metrics in ASM.
Background information
ASM provides multiple monitoring metrics including istio_requests_total and istio_request_duration_milliseconds. By default, these metrics are configured with some dimensions, such as source_workload, destination_workload, and response_code. You can configure the monitoring metrics generated by the mesh proxy based on these dimensions. For more information, see Configure observability settings. In this way, you can create various dashboards and alert rules.
Prerequisites
Add a cluster to an ASM instance of version 1.18 or later.
Automatic sidecar proxy injection is enabled. For more information, see Configure sidecar proxy injection policies.
The HTTPBin application is deployed and can be accessed. For more information, see Deploy the HTTPBin application.
Step 1: Write a Wasm plug-in and apply it to an HTTPBin application
This section describes how to develop a Wasm plug-in in Rust, decode the user-name in a request header using Base64, and then add the user-name to the istio_requests_total metric as a dimension.
The API for other languages is similar to that of Rust plug-ins. If you write Wasm plug-ins in other languages, please refer to the corresponding SDK documentation.
Get the plug-in source code.
Compile and deploy a Wasm plug-in. For more information, see Write a Wasm plug-in in Rust for an Envoy proxy in ASM.
The plug-in is designed to call the
SetPropertyfunction to specify the parsing result as a filter_state. The sample YAML file forWasmPluginis as follows.apiVersion: extensions.istio.io/v1alpha1 kind: WasmPlugin metadata: name: add-metrics-log namespace: default spec: imagePullPolicy: IfNotPresent selector: matchLabels: app: httpbin url: oci://registry-cn-hangzhou.ack.aliyuncs.com/ack-demo/asm-wasm-rust-add-metrics-tag:v1.22.6.7-g1926b20-aliyun phase: AUTHNThe image in this example is stored in a public repository. Therefore, you do not need to configure
wasm-secrets. If the ACR you are using is a private repository, you need to make adjustments according to the sample YAML file in Write a Wasm plug-in in Rust for an Envoy proxy in ASM.
Step 2: Modify the observability settings to add custom dimensions
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
In the Monitoring Metrics Configuration list, enable the Client-side Metrics and Server-side Metrics for REQUEST_COUNT, and add the custom dimension
user_namewith the valuefilter_state["wasm.user-name"]respectively.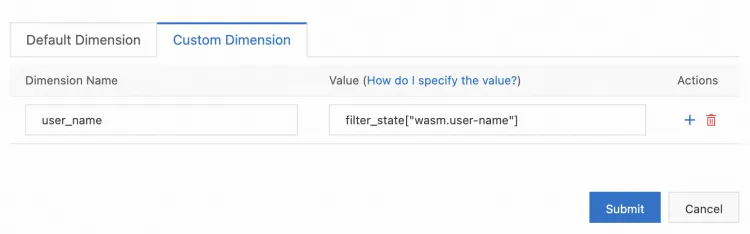
Click Submit to add the
filter_stateto the custom dimension.
Step 3: Access an HTTPBin service
Run the following command to access an HTTPBin service.
curl ${IP address of ASM gateway}:80/status/418 --header "user-name:YXNtLXRlc3QtdXNlcgo="YXNtLXRlc3QtdXNlcgo=the result of asm-test-user encoded in Base64.Expected output:
-=[ teapot ]=- _...._ .' _ _ `. | ."` ^ `". _, \_;`"---"`|// | ;/ \_ _/ `"""`Run the following command by using the kubeconfig file of the ASM cluster on the data plane to view the Prometheus metrics for the HTTPBin pod.
kubectl exec deploy/httpbin -it -c istio-proxy -- curl localhost:15000/stats/prometheus | grep istio_requests_totalExpected output:
# TYPE istio_requests_total counter istio_requests_total{reporter="destination",source_workload="istio-ingressgateway",...,user_name="asm-test-user"} 3In this case, you can specify statistics information for specific users in Prometheus based in this dimension.