Service Mesh (ASM) allows you to synchronize certificates to multiple clusters in an ASM instance by using the certificate management feature. The certificate management feature helps you manage certificates by providing such capabilities as certificate information display and expiration alerting. This topic describes how to use the certificate management feature of ASM.
Prerequisites
A cluster is added to an ASM instance whose version is 1.17 or later. For more information, see Add a cluster to an ASM instance.
Step 1: Create a server certificate and a private key
Run the following command to create a root certificate and a private key:
openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -subj '/O=myexample Inc./CN=aliyun.com' -keyout aliyun.root.key -out aliyun.root.crtRun the following commands to generate a server certificate and a private key whose validity periods are 365 days for the server of aliyun.com.
openssl req -out aliyun.com.csr -newkey rsa:2048 -nodes -keyout aliyun.com.key -subj "/CN=aliyun.com/O=myexample organization" openssl x509 -req -days 365 -CA aliyun.root.crt -CAkey aliyun.root.key -set_serial 0 -in aliyun.com.csr -out aliyun.com.crtRun the following commands to generate a server certificate and a private key whose validity periods are one day for the server of aliyun.com.
The purpose is to test the certificate expiration alerting feature.
openssl req -out expiring.aliyun.com.csr -newkey rsa:2048 -nodes -keyout expiring.aliyun.com.key -subj "/CN=aliyun.com/O=myexample organization" openssl x509 -req -days 1 -CA aliyun.root.crt -CAkey aliyun.root.key -set_serial 0 -in expiring.aliyun.com.csr -out expiring.aliyun.com.crt
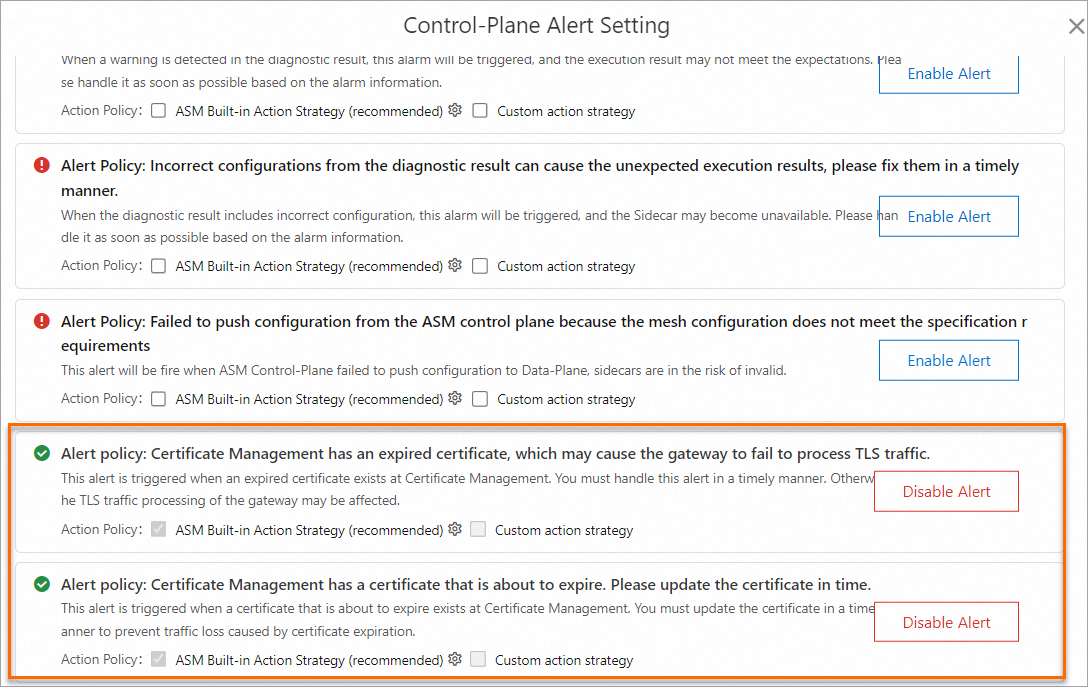
(Optional) Step 2: Enable control-plane log collection and certificate alerting
You can enable control-plane log collection, certificate expiration alerting, and certificate about-to-expiration alerting based on your business requirements. If the validity period of your certificate is less than 30 days, ASM considers that your certificate is about to expire.
If your ASM instance is earlier than 1.17.2.35, see Enable control-plane log collection and log-based alerting in an ASM instance of a version earlier than 1.17.2.35.
If your ASM instance is 1.17.2.35 or later, see Enable control-plane log collection and log-based alerting in an ASM instance of version 1.17.2.35 or later.
Step 3: Create a certificate on the Certificate Management page
Create a normal certificate.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Certificate Management page, click Create. In the Certificate Information panel, configure the required parameters and click OK.
Parameter
Description
Name
The certificate name.
Namespace
The default value is istio-system.
Public Key Certificate
For this example, enter the content of the
aliyun.com.crtfile generated in substep 2 of Step 1.Private Key
For this example, enter the content of the
aliyun.com.keyfile generated in substep 2 of Step 1.Enable mTLS
If you need to create a certificate for mTLS communication, turn on this switch and copy the content of the CA certificate to the CA Certificate field.
Create a certificate that is about to expire by referring to Step 1.
For the Public Key Certificate and Private Key parameters, enter the content of the
expiring.aliyun.com.crtandexpiring.aliyun.com.keyfiles that are generated in substep 3 of Step 1, respectively. After the certificate is created, you can view the two certificates on the Certificate Management page. To view the details of a certificate, click Details in the Operation column. To modify the certificate content, click Edit.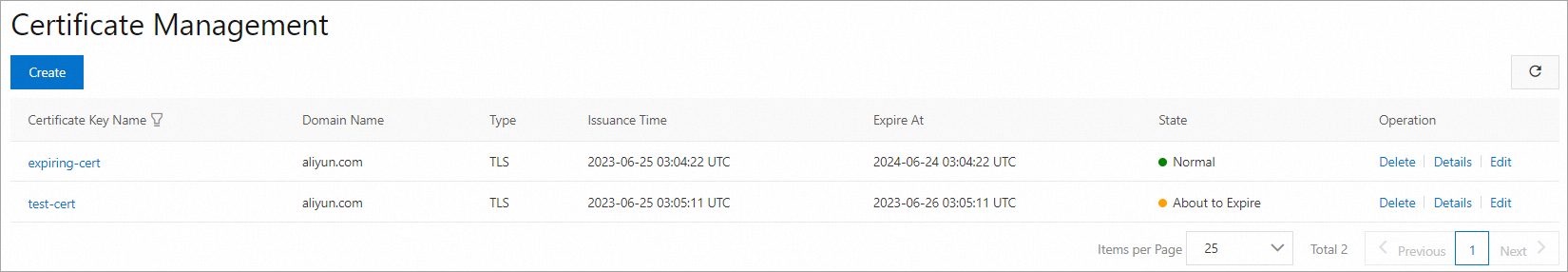
(Optional) View the alert logs of a certificate.
For an ASM instance whose version is earlier than 1.17.2.35
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
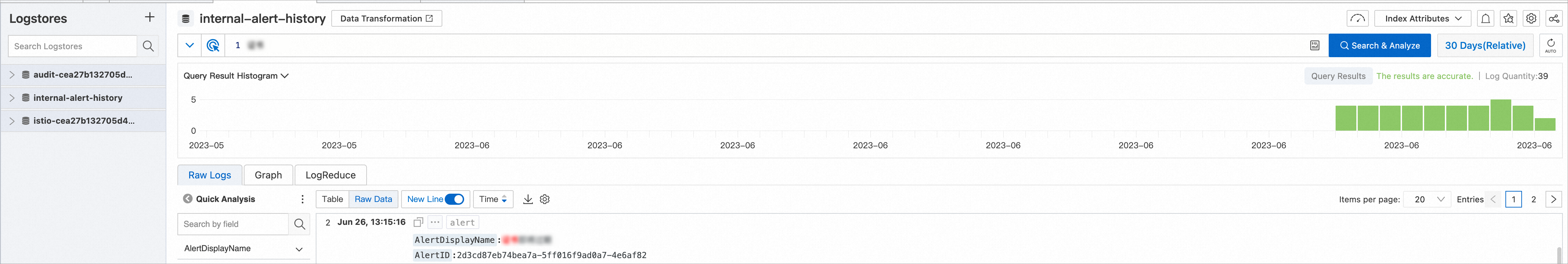
Click View log on the right of Control-plane log collection. In the left-side Logstore section, click internal-alert-history. On the internal-alert-history page, search for certificate and view the alert logs.
For an ASM instance whose version is 1.17.2.35 or later
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Log Center page, click the Control-Plane Logs tab, enter Certificate in the field, and then click Query&Analyze to view the certificate alert logs.
NoteThe system checks the certificate expiration alerts every 6 hours. If no alert logs are found, check the alert logs after 6 hours.
Use the certificates displayed on the Certificate Management page.
After you create a certificate on the Certificate Management page, you can use the certificate in the following scenarios:
If you want to configure a Transport Layer Security (TLS) certificate when you create or modify an Istio gateway by using a YAML template, enter the certificate name displayed on the Certificate Management page in the
credentialNamefield. For more information, see Manage Istio gateways.When you create an Istio gateway on the graphical user interface (GUI) provided by ASM, you can directly select the certificate displayed on the Certificate Management page. For more information, see Manage Istio gateways.
If you set the protocol to TLS when you create a domain on the Gateway overview > Domain/Certificate page, you can select the certificate displayed on the Certificate Management page for the credential parameter. For more information, see Bind a certificate to a domain name.
Step 4: Migrate a certificate
For ASM instances of version 1.17 or later, you can manage the certificates on the Certificate Management page. To go to this page, choose ASM Gateways > Certificate Management. If you have created a certificate on the Gateway overview > Domain/Certificate page, migrate the certificate to the Certificate Management page.
On the Certificate Management page, create a certificate with the same name as that of the certificate you have created on the Domain/Certificate page, and copy the content of the certificate on the Domain/Certificate page to the certificate that you are creating on the Certificate Management page. This way, the certificate on the Domain/Certificate page is migrated to the Certificate Management page.