You can authorize a Resource Access Management (RAM) user or a RAM role to use Service Mesh (ASM) as needed by granting required permissions to the RAM user or RAM role. Only authorized RAM users and RAM roles can perform operations such as creating ASM instances and updating ASM configurations in the ASM console. This eliminates security risks caused by the leakage of AccessKey pairs of Alibaba Cloud accounts. This topic describes how to grant permissions to a RAM user and a RAM role.
Prerequisites
A RAM user and a RAM role are created. For more information, see Create a RAM user and Create a RAM role for a trusted Alibaba Cloud account.
You have a basic knowledge of the policy elements, structure, and syntax. For more information, see Policy structure and syntax.
Background information
The permissions required by RAM users and RAM roles vary with different scenarios.
If a RAM user or a RAM role needs to manage ASM instances but not Container Service for Kubernetes (ACK) clusters, you need to grant only permissions on ASM instances to the RAM user or RAM role. For more information, see Attach system policies to RAM users and RAM roles and Attach custom policies to RAM users and RAM roles.
If a RAM user or a RAM role needs to manage both ASM instances and ACK clusters, you must grant permissions on ASM instances and ACK clusters to the RAM user or RAM role. For example, the RAM user or RAM role needs to add ACK clusters to ASM instances and remove ACK clusters from ASM instances. For more information, see Attach system policies to RAM users and RAM roles, Attach custom policies to RAM users and RAM roles, and Use RAM to authorize access to clusters and cloud resources.
Attach system policies to RAM users and RAM roles
By default, ASM creates two system policies: AliyunASMReadOnlyAccess and AliyunASMFullAccess. You can attach the policies to RAM users and RAM roles. The following part describes the two system policies:
AliyunASMReadOnlyAccess
The policy contains only read-only permissions on ASM instances. After you attach the policy to a RAM user, the RAM user can only view the information about ASM instances but cannot modify the configurations of ASM instances.
AliyunASMFullAccess
The policy contains all permissions on ASM instances. After you attach the policy to a RAM user, the RAM user has the same permissions on ASM instances as an Alibaba Cloud account and can perform all operations on ASM instances.
The following part describes how to attach a system policy to a RAM user or RAM role. In the following example, the AliyunASMReadOnlyAccess policy is attached to a RAM user. For more information, see Grant permissions to a RAM user and Grant permissions to a RAM role.
Log on to the RAM console as a RAM administrator.
In the left-side navigation pane, choose .
On the Users page, find the required RAM user, and click Add Permissions in the Actions column.
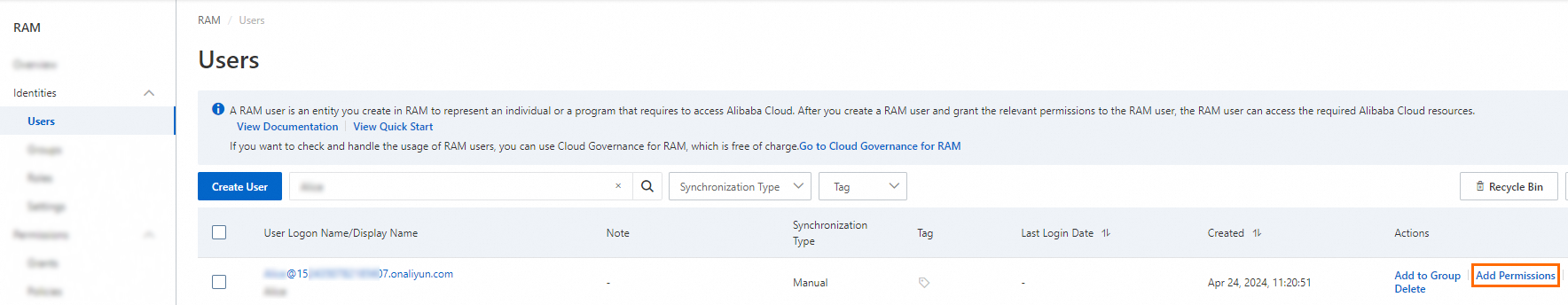
You can also select multiple RAM users and click Add Permissions in the lower part of the page to grant permissions to the RAM users at a time.
In the Grant Permission panel, grant permissions to the RAM user.
Configure the Resource Scope parameter.
Account: The authorization takes effect on the current Alibaba Cloud account.
ResourceGroup: The authorization takes effect on a specific resource group.
ImportantIf you select Resource Group for the Resource Scope parameter, make sure that the required cloud service supports resource groups. For more information, see Services that work with Resource Group. For more information about how to grant permissions on a resource group, see Use a resource group to grant a RAM user the permissions to manage a specific ECS instance.
Configure the Principal parameter.
The principal is the RAM user to which you want to grant permissions. The current RAM user is automatically selected.
Select System Policy from the All Types drop-down list, enter AliyunASMReadOnlyAccess in the search box, and then select AliyunASMReadOnlyAccess.
NoteYou can attach a maximum of five policies to a RAM user at a time. If you want to attach more than five policies to a RAM user, repeat the operation.
Click Grant permissions.
Click Close.
Attach custom policies to RAM users and RAM roles
If you want to enforce fine-grained control on permissions, you can create custom policies and attach custom policies to RAM users and RAM roles.
Create a policy that is used to grant permissions on ASM instances
Log on to the RAM console as a RAM user who has administrative rights.
In the left-side navigation pane, choose .
On the Policies page, click Create Policy.
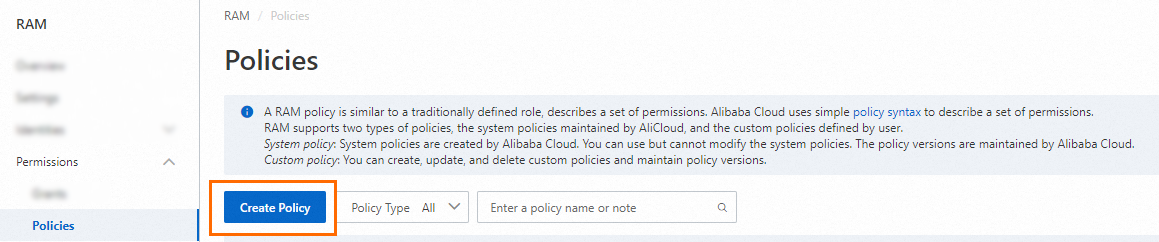
On the Create Policy page, click the JSON tab.

Enter the custom policy and click OK.
You can modify the
Actionfield in theStatementblock to enable fine-grained authentication for API operations. In this example, a policy with limited permissions is created. The policy grants all RAM permissions on ASM except role-based access control (RBAC) authorization permissions. A RAM user to which the policy is attached cannot grant RBAC permissions to other users but has all other permissions. For more information about the syntax and structure of RAM policies, see Policy structure and syntax.{ "Statement": [ { "Effect": "Allow", "Action": [ "servicemesh:Add*", "servicemesh:CRBatchDeletion", "servicemesh:Create*", "servicemesh:Delete*", "servicemesh:Describe*", "servicemesh:Enable*", "servicemesh:Disable*", "servicemesh:Get*", "servicemesh:InvokeApiServer", "servicemesh:List*", "servicemesh:Modify*", "servicemesh:Re*", "servicemesh:Run*", "servicemesh:Set*", "servicemesh:Sync*", "servicemesh:Update*", "servicemesh:Upgrade*" ], "Resource": "*" }, { "Effect": "Allow", "Action": [ "log:ListLogStores", "log:ListDashboard", "log:GetDashboard", "log:ListSavedSearch", "log:ListProject" ], "Resource": "*" }, { "Effect": "Allow", "Action": "log:GetLogStoreLogs", "Resource": "acs:log:*:*:project/*/logstore/audit-*" }, { "Effect": "Allow", "Action": "log:GetLogStoreLogs", "Resource": "acs:log:*:*:project/*/logstore/istio-*" }, { "Action": "ram:CreateServiceLinkedRole", "Resource": "*", "Effect": "Allow", "Condition": { "StringEquals": { "ram:ServiceName": "servicemesh.aliyuncs.com" } } } ], "Version": "1" }In the Basic Information section, enter a policy name in the Name field. In this example, the policy name is ASMPolicy1. Then, click OK.
Attach the custom policy to a RAM user or RAM role
In this example, the custom policy is attached to a RAM user. For more information about how to attach a custom policy to a RAM role, see Grant permissions to a RAM role.
Log on to the RAM console as a RAM user who has administrative rights.
In the left-side navigation pane, choose .
On the Users page, find the required RAM user, and click Add Permissions in the Actions column.

You can also select multiple RAM users and click Add Permissions in the lower part of the page to grant permissions to the RAM users at a time.
In the Add Permissions panel, grant permissions to the RAM user.
Configure the Resource Scope parameter.
Account: The authorization takes effect on the current Alibaba Cloud account.
ResourceGroup: The authorization takes effect on a specific resource group.
ImportantIf you select Resource Group for the Resource Scope parameter, make sure that the required cloud service supports resource groups. For more information, see Services that work with Resource Group. For more information about how to grant permissions on a resource group, see Use a resource group to grant a RAM user the permissions to manage a specific ECS instance.
Configure the Principal parameter.
The principal is the RAM user to which you want to grant permissions. The current RAM user is automatically selected.
Configure the Policy parameter.
Select Custom Policy from the All Types dropdown. Enter ASMPolicy1 in the text box and select it from the search result.
Click Grant permissions.
Click Close.
Sample scenarios of custom policies
Scenario 1: Grant the permissions on a single ASM instance
You can use the following script to create a policy that grants the permissions on a single ASM instance. After you attach the policy to a RAM user or RAM role, the RAM user or RAM role can manage only the ASM instance with the specified ID.
When you create the policy, replace <ServicemeshId> in the script with the ID of the ASM instance on which you want to grant permissions.
{
"Statement": [
{
"Effect": "Allow",
"Action": "servicemesh:*",
"Resource": "acs:servicemesh:*:*:servicemesh/<ServicemeshId>"
},
{
"Effect": "Allow",
"Action": "servicemesh:DescribeServiceMeshes",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "log:GetLogStoreLogs",
"Resource": "acs:log:*:*:project/*/logstore/audit-<ServicemeshId>"
},
{
"Effect": "Allow",
"Action": "log:GetLogStoreLogs",
"Resource": "acs:log:*:*:project/*/logstore/istio-<ServicemeshId>"
}
],
"Version": "1"
}Scenario 2: Grant the read and write permissions on Istio resources in the ASM console
By default, the system policy AliyunASMReadOnlyAccess provided by ASM grants RAM users or RAM roles the read-only permissions on ASM instances. RAM users or RAM roles to which this policy is attached cannot manage Istio resources in ASM.
You can use the following script to create a policy that grants the read and write permissions on Istio resources. After you attach the policy to a RAM user or RAM role, the RAM user or RAM role can use the ASM console to manage Istio resources on ASM instances. However, the RAM user or RAM role cannot change other settings of the ASM instances, such as feature settings.
{
"Statement": [
{
"Effect": "Allow",
"Action": [
"servicemesh:List*",
"servicemesh:Describe*",
"servicemesh:Get*",
"servicemesh:InvokeApiServer"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"log:ListLogStores",
"log:ListDashboard",
"log:GetDashboard",
"log:ListSavedSearch"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "log:GetLogStoreLogs",
"Resource": "acs:log:*:*:project/*/logstore/audit-*"
}
],
"Version": "1"
}Scenario 3: Grant RBAC authorization permissions
You can use the following script to create a policy that grants RBAC authorization permissions. After you attach the policy to a RAM user or RAM role, the RAM user or RAM role can use the ASM console to manage the RBAC permissions of other RAM roles or RAM users. However, the RAM user or RAM role cannot manage ASM instances.
{
"Statement": [
{
"Effect": "Allow",
"Action": [
"servicemesh:DescribeUserPermissions",
"servicemesh:GrantUserPermissions",
"servicemesh:DescribeServiceMeshes",
"servicemesh:DescribeUsersWithPermissions"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "ims:ListUserBasicInfos",
"Resource": "*"
}
],
"Version": "1"
}