If your client uses Hypertext Transfer Protocol Secure (HTTPS) and is limited to support HTTP/2 and you cannot solve this issue by modifying configurations, we recommend that you disable HTTP/2 on your ingress gateway. This topic describes how to disable HTTP/2 on an ingress gateway on which HTTPS is enabled.
Prerequisites
Step 1: Confirm the default settings
Run the following command to access the ingress gateway and verify that HTTP/2 is negotiated through Application-Layer Protocol Negotiation (ALPN):
curl -k -H Host:b.aliyun.com --resolve b.aliyun.com:443:${IP address of the ingress gateway} https://b.aliyun.com/status/418 -vExpected output:
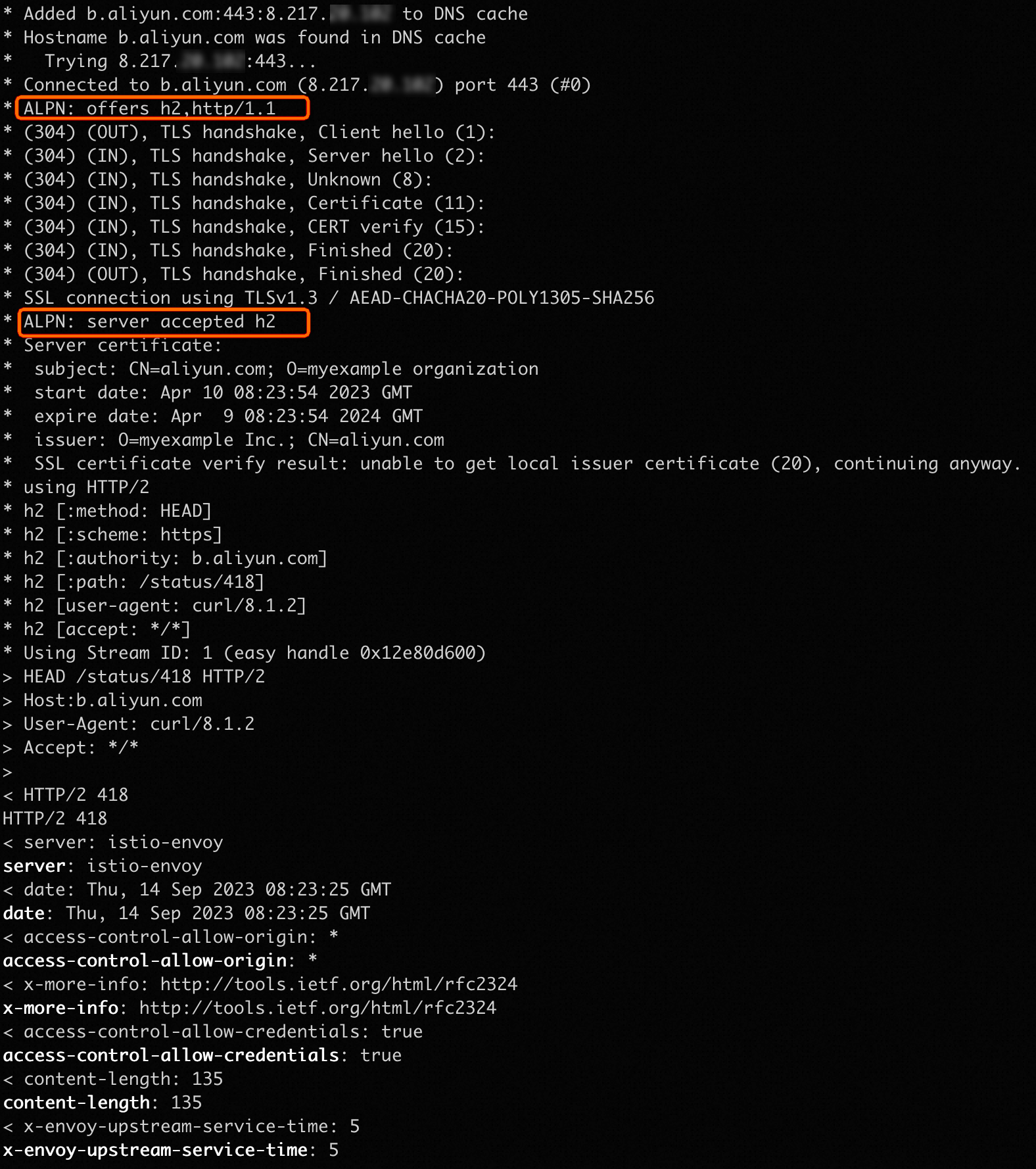
The output indicates that both HTTP/2 and HTTP/1.1 are negotiated through ALPN. By default, the ingress gateway preferentially uses HTTP/2.
Step 2: Disable HTTP/2 when HTTPS is used
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Ingress Gateway page, find the desired gateway and click YAML in the Actions column. In the Edit dialog box, set the
podAnnotationsparameter in thespecfield and click OK.podAnnotations: proxy.istio.io/config: | httpsHttp2Disabled: trueNoteThis configuration causes the ingress gateway to restart.
Step 3: Verify that HTTP/2 is disabled on the ingress gateway while HTTPS is enabled
Run the following command to access the ingress gateway:
curl -k -H Host:b.aliyun.com --resolve b.aliyun.com:443:${IP address of the ingress gateway} https://b.aliyun.com/status/418 -vExpected output:
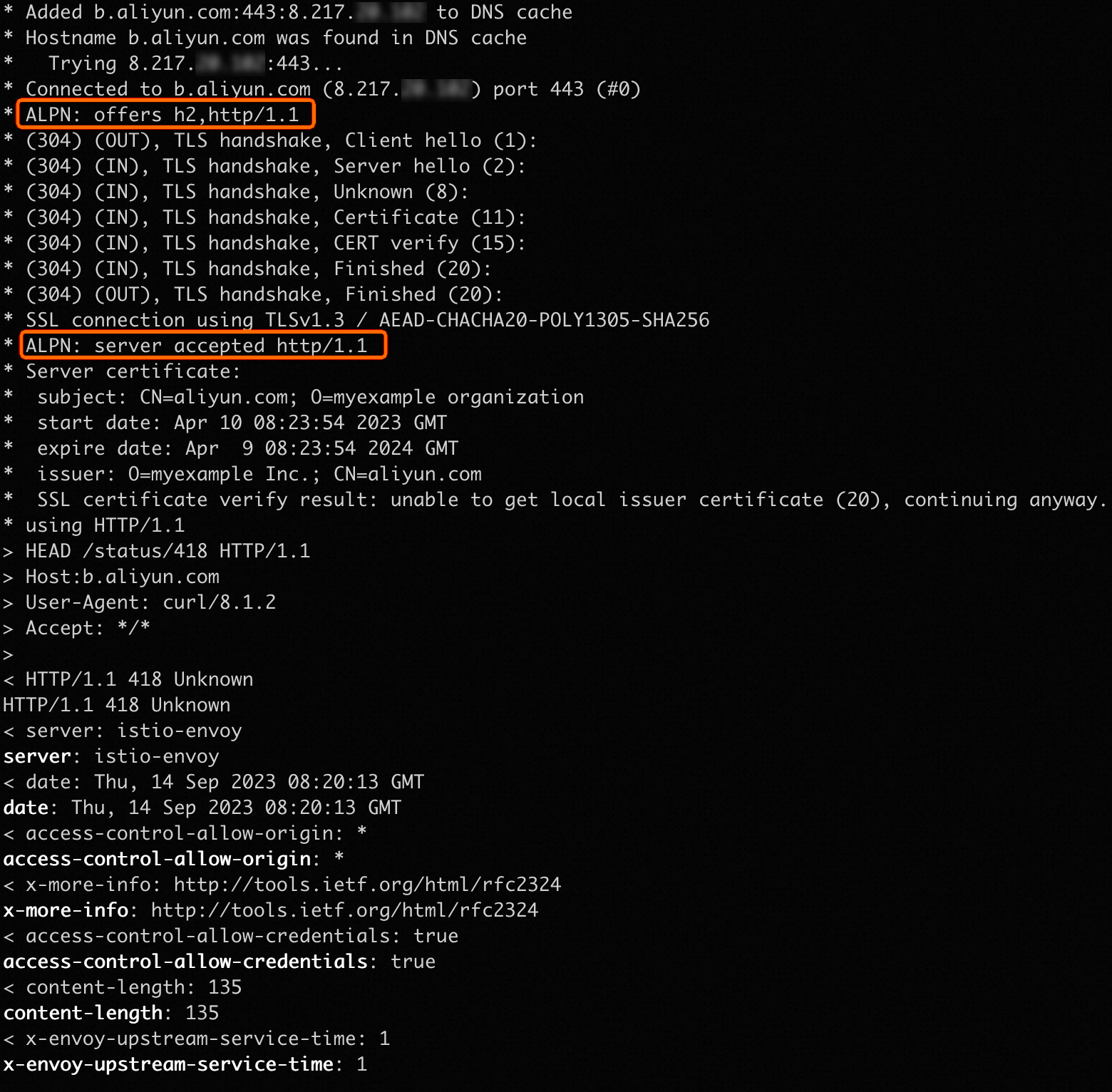
The output indicates that only HTTP/1.1 is negotiated through ALPN. This means that HTTP/2 is disabled.