IPv6 provides a larger address space and higher security compared with IPv4. This topic describes how to create a Service Mesh (ASM) ingress gateway that uses an IPv6 address. This topic also describes how to add an IPv6 address to an existing ingress gateway.
Prerequisites
The cluster is added to the ASM instance. For more information, see Add a cluster to an ASM instance.
Method 1: Create an ingress gateway that uses an IPv6 address
To create an ingress gateway that uses an IPv6 address, you must add the service.beta.kubernetes.io/alibaba-cloud-loadbalancer-ip-version: "ipv6" annotation to the YAML code.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Ingress Gateway page, click Create from YAML.
On the Create page, set the Namespace parameter to istio-system, enter the following content in the YAML code editor, and then click Create.
Replace the value of the
clusterIdsfield with the ID of your cluster on the data plane.Field
Description
service.beta.kubernetes.io/alicloud-loadbalancer-address-type
The type of the Classic Load Balancer (CLB) instance. Valid values:
internet: an Internet-facing CLB instance
intranet: an internal-facing CLB instance
service.beta.kubernetes.io/alibaba-cloud-loadbalancer-spec
The specifications of the CLB instance. Valid values: slb.s1.small, slb.s2.small, slb.s2.medium, slb.s3.small, slb.s3.medium, and slb.s3.large.
service.beta.kubernetes.io/alibaba-cloud-loadbalancer-ip-version
The version of the IP address used by the CLB instance. In this example, the parameter is set to
ipv6, which indicates that the CLB instance uses an IPv6 address.After the ingress gateway is created, you can see that Service address of the ingress gateway, which is displayed on the Ingress Gateway page, is an IPv6 address.
Method 2: Add an IPv6 address to an existing ingress gateway
If you have created an ingress gateway that uses an IPv4 address, you can create a CLB instance to add an IPv6 address to the ingress gateway. After that, the ingress gateway uses both the IPv4 and IPv6 addresses.
Log on to the ACK console. In the left-side navigation pane, click Clusters.
On the Clusters page, click the name of the cluster that you want to manage and choose in the left-side navigation pane.
In the upper part of the Services page, set the Namespace parameter to istio-system and click Create from YAML in the upper-right corner.
On the Create page, select Custom from the Sample Template drop-down list, copy the following content to the Template code editor, and then click Create.
ImportantThe value of the nodePort parameter cannot be the same as an existing port number.
Field
Description
service.beta.kubernetes.io/alicloud-loadbalancer-address-type
The type of the CLB instance. Valid values:
internet: an Internet-facing CLB instance
intranet: an internal-facing CLB instance
service.beta.kubernetes.io/alibaba-cloud-loadbalancer-spec
The specifications of the CLB instance. Valid values: slb.s1.small, slb.s2.small, slb.s2.medium, slb.s3.small, slb.s3.medium, and slb.s3.large.
service.beta.kubernetes.io/alibaba-cloud-loadbalancer-ip-version
The version of the IP address used by the CLB instance. In this example, the parameter is set to
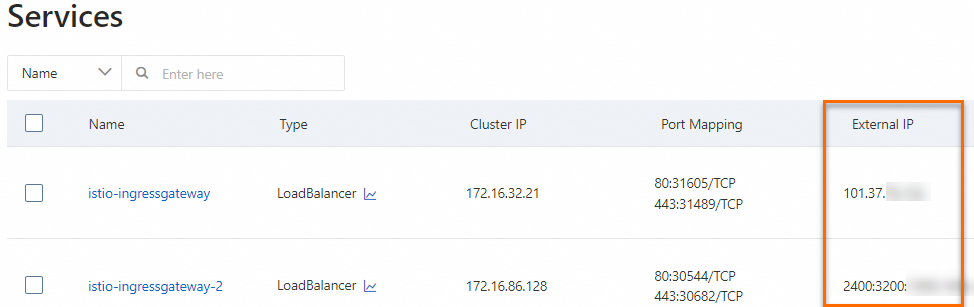
ipv6, which indicates that the CLB instance uses an IPv6 address.After the CLB instance is created, the IPv4 and IPv6 addresses of istio-ingressgateway and istio-ingressgateway-2 are displayed in the External IP column on the Services page. The displayed IPv4 and IPv6 addresses are used by the ingress gateway.
FAQ
How do I obtain the original IPv6 address of a client?
Configure a CLB instance that uses an IPv6 address. Enable Proxy Protocol in the Advanced Settings section for listeners of the CLB instance on ports 80 and 443. For more information, see Enable Layer 4 listeners to preserve client IP addresses.
Create an Envoy filter template.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose . On the page that appears, click Create EnvoyFilter Template.
On the Create page, enter a template name, click Add an EnvoyFilter template for specific adapted istio version, select an Istio version, enter the following content in the YAML code editor, and then click Create.
apiVersion: networking.istio.io/v1alpha3 kind: EnvoyFilter metadata: name: proxy-protocol namespace: istio-system spec: configPatches: - applyTo: LISTENER patch: operation: MERGE value: listener_filters: - name: envoy.listener.proxy_protocol - name: envoy.listener.tls_inspector workloadSelector: labels: istio: ingressgateway
Apply the Envoy filter template to the ingress gateway so that the ingress gateway supports Proxy Protocol.
On the EnvoyFilter Template page, find the Envoy filter template that you created in the previous step and click Edit template in the Actions column.
On the Edit EnvoyFilter Template page, click the Bind template to workloads tab and click Bind EnvoyFilter to Workloads.
In the Bind EnvoyFilter to Workloads dialog box, set the Namespace parameter to istio-system and the Workload Type parameter to Deployment, click Bind next to the ingress gateway in the Not bound section, and then click OK.
Access a URL that uses an IPv6 address and check the logs of the ingress gateway.
In the sample logs, the value of the
downstream_remote_addressfield indicates the original IPv6 address of the client.{"upstream_cluster":null,"bytes_received":0,"downstream_local_address":"[2400:XXXX:1300::12d1]:80","upstream_service_time":null,"FILTER_CHAIN_NAME":null,"path":"/","x_forwarded_for":"2402:XXXX:1800:af00:0:9671:f00f:314b","upstream_host":null,"bytes_sent":0,"requested_server_name":null,"route_name":null,"response_flags":"NR","start_time":"2022-12-28T06:41:57.796Z","upstream_transport_failure_reason":null,"protocol":"HTTP/1.1","authority":"[2400:XXXX:1300::12d1]","LOCAL_REPLY_BODY":"","duration":0,"method":"GET","downstream_remote_address":"[2402:XXXX:1800:af00:0:9671:f00f:314b]:58272","request_id":"fee2b69a-b755-986b-91e4-5d228c81****","user_agent":"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36","trace_id":null,"authority_for":"[2400:XXXX:1300::12d1]","upstream_local_address":null,"istio_policy_status":null,"response_code":404}