OpenID Connect (OIDC) built on the OAuth 2.0 protocol is a protocol for identity authentication and authorization. It is commonly used to implement single sign-on (SSO). After you configure OIDC-based SSO on an ingress gateway, you can use identity information provided by Alibaba Cloud IDentity as a Service (IDaaS) or other identity providers (IdPs) that comply with the OIDC protocol to log on to multiple related systems with a single ID. In addition, you do not need to modify your applications. This improves application security and simplifies the development and management of your application.
Prerequisites
Automatic sidecar proxy injection is enabled for the specified namespaces. For more information, see Configure sidecar proxy injection policies.
An ingress gateway is created in a Service Mesh (ASM) instance and the IP address of the ingress gateway is obtained. For more information, see Create an ingress gateway and Substep 1 of Step 3 in Use Istio resources to route traffic to different versions of a service.
An IdP is configured. For more information, see Step 1 and Step 2 in Integrate Alibaba Cloud IDaaS with ASM to implement single sign-on.
After an IdP is configured, you can obtain the following information that will be used in Step 5.
redirect uri: http://${IP address of the ingress gateway}/oauth2/callback issuer: https://eiam-api-cn-hangzhou.aliyuncs.com/v2/idaas_tbn25osdlmz6gtqfq3j2pz****/app_ml5tzapsl7zmfo53wb3nwk****/oidc client id: ******** client secret: *********
Procedure
In this example, an Alibaba Cloud IDaaS instance is used as the IdP to implement SSO to applications in ASM. If you use a self-managed OIDC IdP, see Integrate Keycloak with ASM to implement single sign-on.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Ingress Gateway page, click the ingress gateway that you want to use.
In the left-side navigation pane, choose .
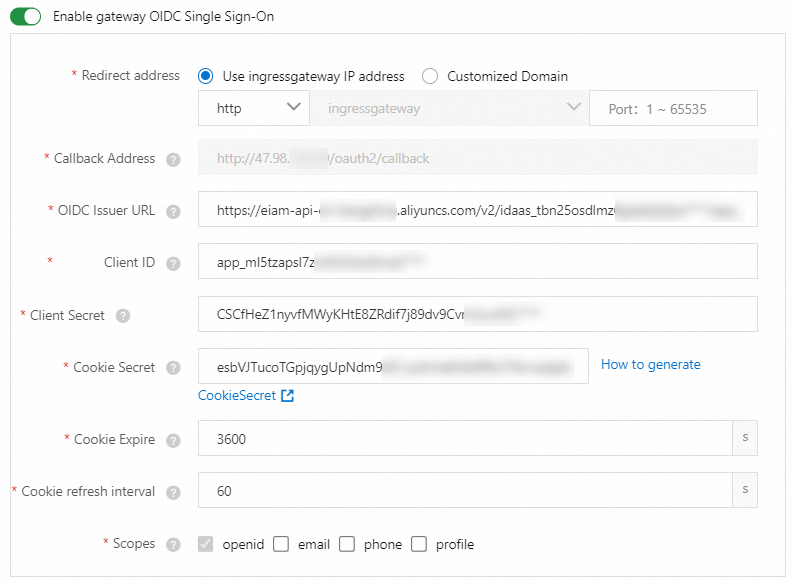
In the OIDC Config step of the configuration wizard, turn on Enable gateway OIDC Single Sign-On, configure the parameters, and then click Next.
Parameter
Description
Redirect address
In this example, Use ingressgateway IP address and http are selected.
Callback Address
The URL to which users are redirected.
OIDC Issuer URL
The URL used to identify and authenticate the OIDC issuer.
Client ID
The client ID provided by the issuer.
Client Secret
The client secret provided by the issuer.
Cookie Secret
The seed string for the secure cookies, which can be Base64-encoded.
Cookie Expire
The validity period of the cookie. The cookie expires after the period has elapsed. If you set this parameter to 0, the cookie does not expire.
Cookie refresh interval
The interval at which the cookie is refreshed. If you set this parameter to 0, the cookie is not refreshed.
Scopes
The types of user information that can be obtained. The specified scopes must be supported by the issuer.
In the Matching Rule step of the configuration wizard, configure the parameters and click Submit.
Parameter
Description
Match Mode
In this example, Auth If Matched is selected. Valid values:
Auth If Matched: Users must log on to access resources in the specified path.
Bypass Auth If Matched: Users do not need to log on to access resources in the specified path.
Add Match Rule
Turn on the Path switch and set this parameter to /productpage. This configuration indicates that requests to access resources in the /productpage path require OIDC authentication.
Then, in the Complete step of the configuration wizard, a message that indicates OIDC-based SSO is successfully configured appears, and native Istio security resources are displayed. You can click YAML to view the resource configurations.
Use a browser to access http://${ASM gateway address}/productpage to check whether the OIDC-based SSO configuration takes effect.
Replace ${IP address of the ingress gateway} with the IP address of the desired ingress gateway. If the following page appears, it indicates that the access is successful and the OIDC-based SSO configuration takes effect.
FAQ
After OIDC-based SSO is configured on an ingress gateway, does my application need to obtain an access token or request user information from an IdP?
After OIDC-based SSO is configured on an ingress gateway, your application can ignore logic related to IdP authorization and authentication. Your application receives a request that contains a header with the key of Authorization. This header is added when the request is processed by the ingress gateway. This header is a JSON Web Token (JWT) generated by the IdP. The JWT payload contains the user information required by your application and the JWT is authenticated by the ingress gateway. Therefore, your application does not need to repeatedly authenticate the JWT. Your application can directly parse this header from the request without the need to request user information from the IdP.
After OIDC-based SSO is configured, a cookie is added when I log on to the browser. Is this cookie important for my application?
Your application can ignore this cookie. This cookie is used by the gateway to record the state of the current session and is meaningless for your application. Your application can just obtain the JWT in a request.
How do I obtain the extended information provided by my IdP?
No configuration is required in ASM. You need to refer to the corresponding IdP implementation. In this example, Alibaba Cloud IDaaS is used.
How do I log off from an application?
You can log off an application by performing the following steps:
Log off from the IdP. You must log off from the IdP by using the methods provided by your IdP. Generally, the IdP provides a URI for logoff. You can log off from the IdP by visiting the URI.
Clear the cookies set by the ingress gateway on the client. You can call the
/oauth2/sign_outpath directly, and the ingress gateway automatically clears the corresponding cookies.
ASM V1.18.147 and later allows you to configure an IdP logoff endpoint on an ingress gateway. You can enter the endpoint on the OIDC configuration page. Then, in the configuration of the match rule, you can specify that requests to access resources in the /oauth2/sign_out path do not require OIDC authentication. After the configuration is complete, when you visit the /oauth2/sign_out path by using a browser, the corresponding cookies will be cleared and you will be redirected to the logoff endpoint that you set. For more information about how to log out Alibaba Cloud IDaaS, see SLO.
References
For more information about configuration items of OIDC applications, such as API operations, secret rotation, OIDC grant types supported by IDaaS, configurations in IDaaS, and configurations in applications, see General Config, Configure SSO, OIDC SSO Configuration, and Rules for OIDC id_token Extended Fields.
When a user who logs on to an application by implementing SSO from IDaaS wants to log out, the user can initiate a global logout on the application to terminate the application sessions as well as the primary IDaaS logon session. For more information, see SLO.