Service Mesh (ASM) allows you to isolate a version or certain features of an application into an independent runtime environment (known as swimlane). Then, you can configure swimlane rules to route requests that meet the rules to the destination version or features of the application. In a development environment, developers may isolate stable versions and canary versions by setting swimlanes, and route users to different swimlanes. In this case, you can direct a specific proportion of users to the version to test the functionality, while the remaining users are randomly routed to the canary release versions based on the weight-based routing rule. This topic describes how to configure swimlanes and Hash tagging plug-ins to implement canary release by user segment.
Prerequisites
A cluster has been created and added to the ASM instance of 1.18 or later. For more information, see Add a cluster to an ASM instance.
A Kubernetes managed cluster or ACS cluster has been created. For more information, see Create an ACK managed cluster or Create an ACS cluster.
An ingress gateway has been deployed. For more information, see Create an ingress gateway.
Sidecar injection policy has been configured.
Procedure
In this example, three applications are created, and the call chain is shown in the following figure.
mocka in version 1.
mockb in version 1.
mockc in version 1 and 2.

In this example, the applications identifies user identity based on the x-user-id request header, and the header is passed among applications. The traffic routing rules are as follows:
The user requests containing
x-user-id: jasonheader are routed to the new version of the application.A specified proportion of user requests containing
x-user-idheader are routed to the new version of the applications based on Hash value.
Step 1: Deploy an application
Create a sample.yaml file with the following content.
Run the following command to deploy an application by using the kubeconfig file of the cluster on the data plane.
kubectl apply -f sample.yaml
Step 2: Create gateway rules
Run the following command to create an Istio gateway named ingressgateway in the Istio-system namespace. For more information, see Manage Istio gateways.
apiVersion: networking.istio.io/v1beta1
kind: Gateway
metadata:
name: ingressgateway
namespace: istio-system
spec:
selector:
istio: ingressgateway
servers:
- port:
number: 80
name: http
protocol: HTTP
hosts:
- '*'Step 3: Create a lane group and a lane
Create a lane group.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the target ASM instance. In the left-side navigation pane, select .
On the Traffic Swimlane page, click Create Swimlane Group. Configure the relevant settings in the Create Swimlane Group panel, and click OK.
Parameter
Description
Name of Swim lane Group
In this example, enter canary.
Ingress Type
Select ingressgateway.
Lane Mode
Select Loose Mode.
Pass-through Mode of Trace Context
Select Pass-through Trace Id.
Trace ID Request Header
In this example, set it to x-user-id.
Request Routing Header
Enable the gateway to route traffic to different lanes based on the request content and pass through the header in lane context. This parameter is user-defined. In this example, enter x-asm-prefer-tag.
Swimlane Service
Select the target cluster in Kubernetes clusters filed and select default in namespace field. Select the mocka, mockb, and mockc services in the list below, and click the
 icon to add the target services to the Selected pane.
icon to add the target services to the Selected pane.
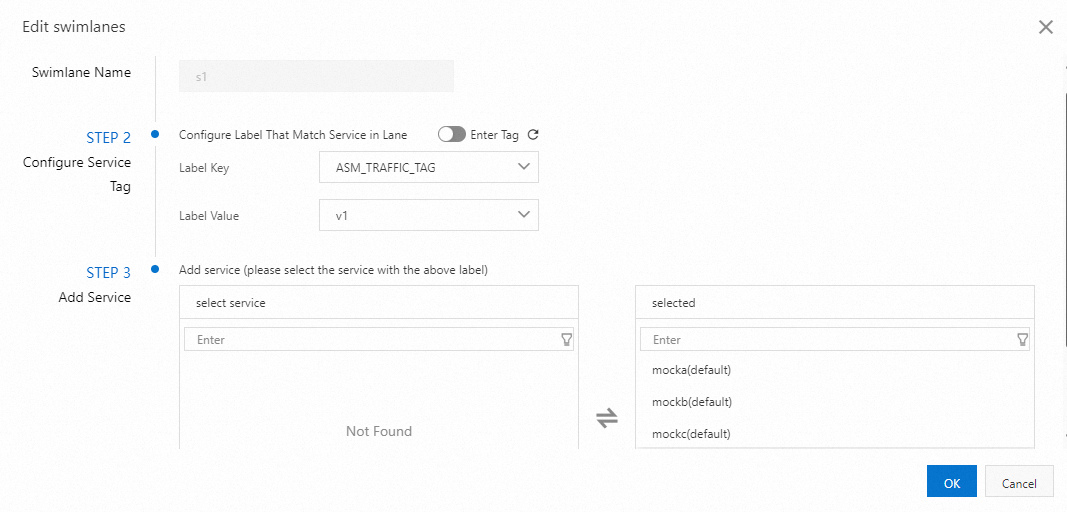
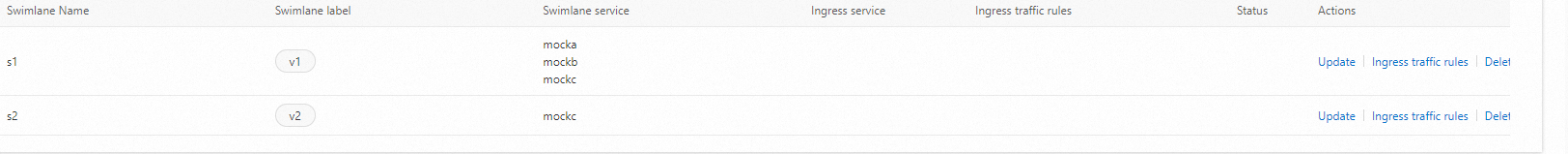
Create swimlanes s1 and s2, and bind them with versions 1 and 2 respectively.
On the Traffic Swimlane page, click Create Swimlanes in the Traffic Rule Definition pane.
In the Create Swimlanes dialog box, configure the relevant settings, and then click OK.
Parameter
Description
Swimlane Name
Enter s1 and s2 respectively.
Configure Service Tag
Label Key: Select ASM_TRAFFIC_TAG
Label Value: Select v1 and v2 for the two lanes respectively.
Add Service
Lane s1: Select mocka(default), mockb(default), mockc(default).
Lane s2: Select mockc(default).
The following figure shows an example of configuring swimlane s1:
The two swimlanes are as follows:
 Note
NoteBy default, the first lane you create in a lane group serves as the baseline lane. You are allowed to modify the services in this baseline lane. When a request is sent to services that do not exist in other lanes, the request is forwarded to the baseline lane through a fallback mechanism. For more information, see Modify the baseline lane in loose mode.
Create request routing rules for the swimlanes.
Create request routing rules for the swimlanes with the following content. The rules are as follows:
Requests containing
x-user-id: jasonheader are routed to swimlane s2. Thex-asm-prefer-tag: s2header that is provided for a request indicates that the request is routed to swimlane s2.Requests containing
x-asm-prefer-tag: s2header are routed to swimlane s2.Requests containing
x-asm-prefer-tag: s1header are routed to swimlane s1.
Step 4: Deploy a Hash tagging plug-in
Create a wasm.yaml file with the following content.
apiVersion: extensions.istio.io/v1alpha1 kind: WasmPlugin metadata: name: hash-tagging namespace: istio-system spec: imagePullPolicy: IfNotPresent selector: matchLabels: istio: ingressgateway url: registry-cn-hangzhou.ack.aliyuncs.com/acs/asm-wasm-hash-tagging:v1.22.6.2-g72656ba-aliyun phase: AUTHN pluginConfig: rules: - header: x-user-id modulo: 100 tagHeader: x-asm-prefer-tag policies: # 20% of user requests are routed to swimlane s2 - range: 20 tagValue: s2 # 80% of user requests are routed to swimlane s1 - range: 100 tagValue: s1Run the following command to deploy a Hash tagging plug-in by using the kubeconfig file of the ASM instance.
kubectl apply -f wasm.yaml
Step 5: Verify routing rules
Run the following command to configure a temporary environment variable for the ingress gateway address.
export GATEWAY_ADDRESS=`kubectl get svc -n istio-system | grep istio-ingressgateway | awk '{print $4}'`Run the following command to access the application as Jason.
curl ${GATEWAY_ADDRESS} -H 'x-user-id: jason'Expected output:
-> mocka(version: v1, ip: 10.0.0.15)-> mockb(version: v1, ip: 10.0.0.130)-> mockc(version: v2, ip: 10.0.0.133)%The result shows that the request is directly routed to version 2 of the mockc application.
Run the following command to route specific users to the new version.
for i in 'bob' 'stacy' 'jessie' 'vance' 'jack'; do curl ${GATEWAY_ADDRESS} -H "x-user-id: $i";echo " user $i requested"; doneExpected output:
-> mocka(version: v1, ip: 10.0.0.15)-> mockb(version: v1, ip: 10.0.0.130)-> mockc(version: v1, ip: 10.0.0.131) user bob requested -> mocka(version: v1, ip: 10.0.0.15)-> mockb(version: v1, ip: 10.0.0.130)-> mockc(version: v1, ip: 10.0.0.131) user stacy requested -> mocka(version: v1, ip: 10.0.0.15)-> mockb(version: v1, ip: 10.0.0.130)-> mockc(version: v2, ip: 10.0.0.133) user jessie requested -> mocka(version: v1, ip: 10.0.0.15)-> mockb(version: v1, ip: 10.0.0.130)-> mockc(version: v1, ip: 10.0.0.131) user vance requested -> mocka(version: v1, ip: 10.0.0.15)-> mockb(version: v1, ip: 10.0.0.130)-> mockc(version: v2, ip: 10.0.0.133) user jack requestedThe results show that the requests of users Jessie and Jack are directly routed to version 2 of the mockc application, while the requests from other users are routed to the version 1.