When dynamic access control is required, you can integrate an Open Policy Agent (OPA) engine in an ingress gateway to customize authorization policies based on user identities or request content and control communication between services in real time. This effectively prevents unauthorized access, reduces the risks of data breach, and enhances the security of applications in a Service Mesh (ASM) instance. This topic describes how to use an OPA engine to authenticate and authorize requests that are received by an ingress gateway. In this example, requests flow through the ingress gateway to access the HTTPBin application.
Prerequisites
A Kubernetes managed cluster is added to an ASM instance whose version is 1.15.3.25 or later. For more information, see Add a cluster to an ASM instance and Update an ASM instance.
The HTTPBin application is deployed and can be accessed. For more information, see Deploy the HTTPBin application.
Automatic sidecar proxy injection is enabled for the default namespace. For more information, see Configure sidecar proxy injection policies.
Step 1: Deploy an OPA engine
Create a file named asm-opa.yaml and copy the following content to the file.
The YAML code deploys an OPA Service, an OPA Deployment, and a Secret.
Kind
Description
Deployment
Replace the region ID in the image
registry-vpc.cn-hangzhou.aliyuncs.com/acs/opa:0.46.1-istio-3-staticwith the ID of the region where your cluster is deployed.By default, logging is enabled for the OPA engine (
--set=decision_logs.console=true). This facilitates debugging.
Secret
The Secret defines the following OPA policies:
If the path of a request is
health, the request is allowed.If the method of a request is
HEAD, the request is allowed.If the user name of a request is
alice, the request is allowed.NoteThe user name is carried in the
Authorizationheader of the request, in the form ofAuthorization: Basic ${user name: Base64-encoded password string}.
Use kubectl to connect to the Container Service for Kubernetes (ACK) cluster based on the information in the kubeconfig file and run the following command to deploy OPA:
kubectl apply -f asm-opa.yaml
Step 2: Use the external authorization feature of the ingress gateway to integrate the OPA engine with the ingress gateway
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Ingress Gateway page, click Gateway security next to the ingress gateway with which you want to integrate the OPA engine.
In the left-side navigation pane, choose .
Configure a custom authorization service.
In the Custom Authorization Service Configuration step, configure the OPA engine as the custom authorization service for the ingress gateway and click Next.
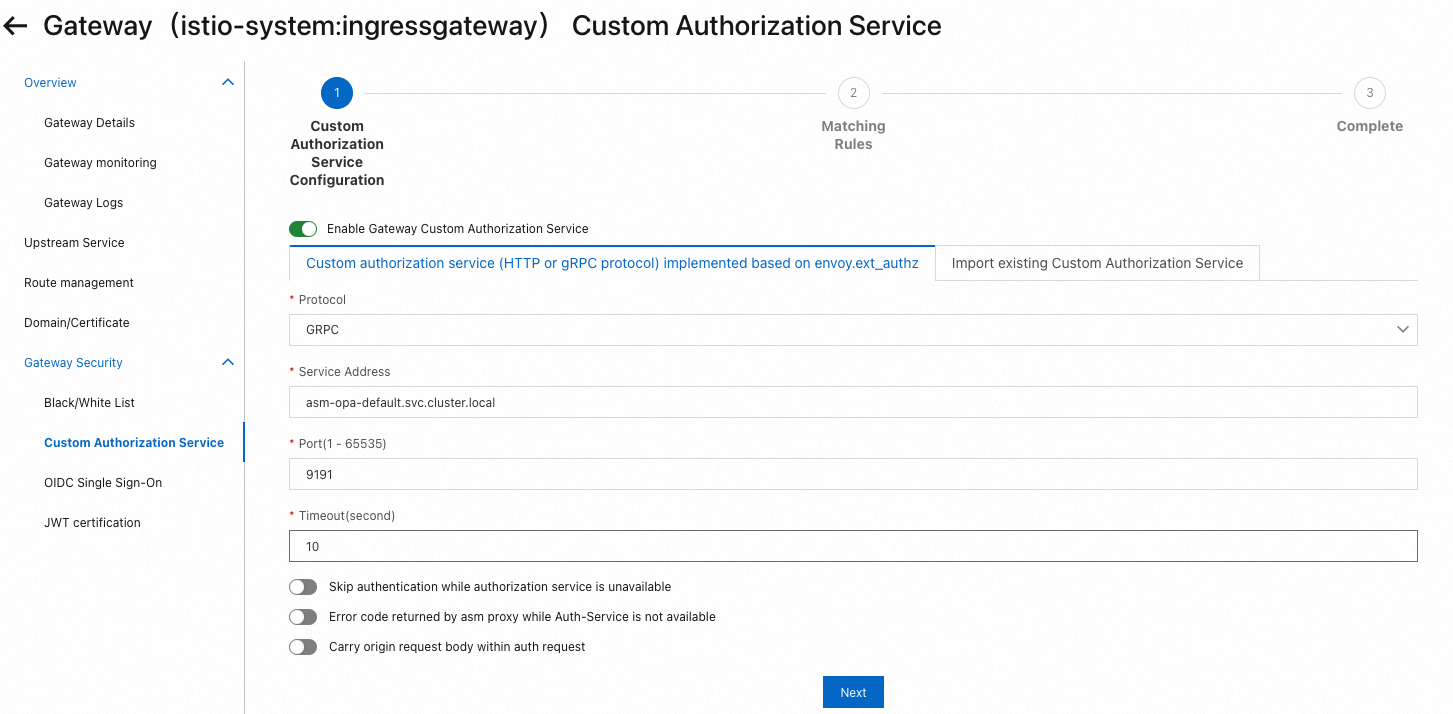
In the Matching Rules step, configure a request matching rule, specify which requests must be authenticated and authorized by the OPA engine, and then click Submit.
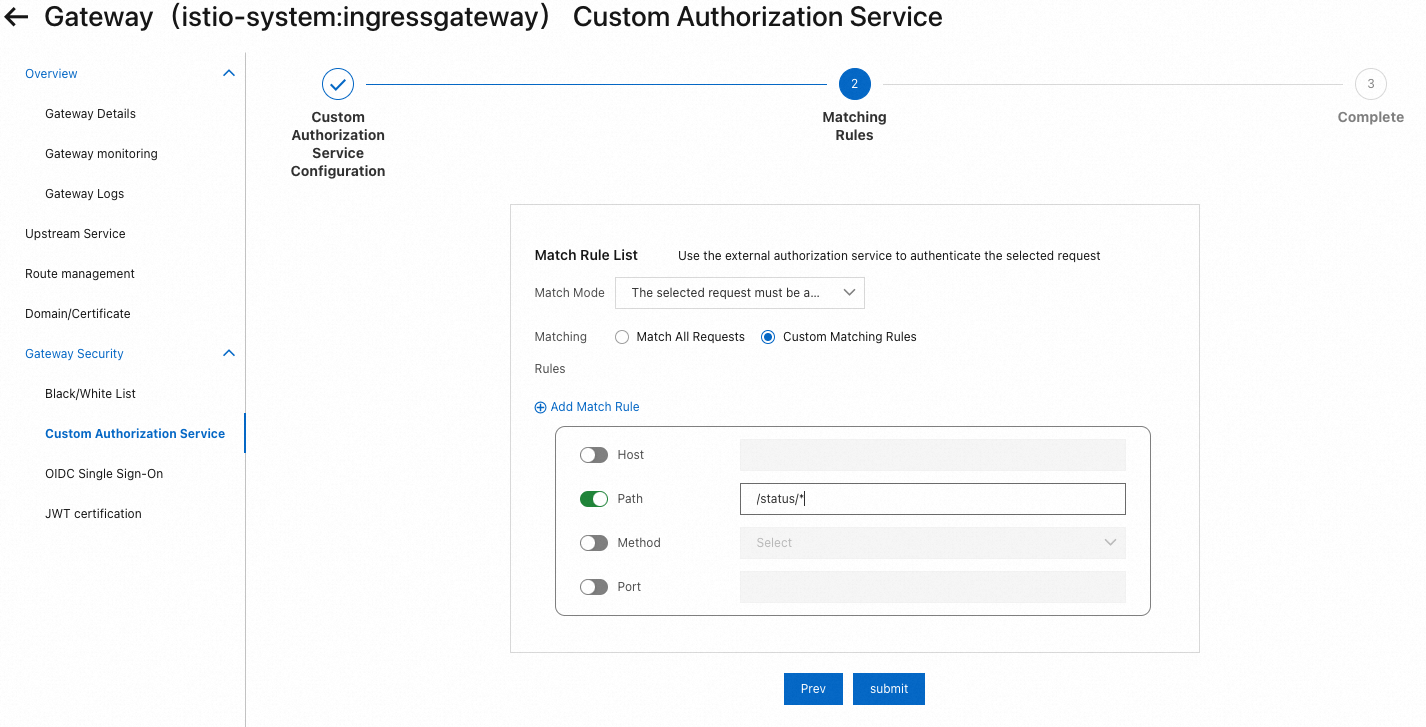
The following figure shows the page after the custom authorization service is created.
Step 3: Test the access to the HTTPBin application
Run the following command to access the
/path:curl ${IP address of the ASM gateway}/ -I -X GETExpected output:
HTTP/1.1 200 OK server: istio-envoy date: Tue, 25 Jul 2023 08:30:58 GMT content-type: text/html; charset=utf-8 content-length: 9593 access-control-allow-origin: * access-control-allow-credentials: true x-envoy-upstream-service-time: 2The output indicates that authentication is not required for the access requests to the path.
Run the following command to access the
/status/201path without valid parameters:curl ${IP address of the ASM gateway}/status/201 -I -X GETExpected output:
HTTP/1.1 403 Forbidden date: Tue, 25 Jul 2023 08:31:18 GMT server: istio-envoy content-length: 0 x-envoy-upstream-service-time: 1The output indicates that the access request without valid parameters is rejected.
Run the following command to access the
/status/201path with valid parameters:curl ${IP address of the ASM gateway}/status/201 -I -X GET --user alice:testpasswordExpected output:
HTTP/1.1 201 Created server: istio-envoy date: Tue, 25 Jul 2023 08:31:38 GMT content-type: text/html; charset=utf-8 access-control-allow-origin: * access-control-allow-credentials: true content-length: 0 x-envoy-upstream-service-time: 3The output indicates that the access request with valid parameters is allowed.
Step 4: Update the OPA policy
Call the HTTP API of the OPA engine to update the OPA policy.
Run the following commands to allow only the user named bob to access the HTTPBin application over HTTP and reject the user named alice from accessing the HTTPBin application over HTTP.
kubectl exec deployment/httpbin -c istio-proxy -- curl asm-opa:8181/v1/policies/policy/policy.rego -XPUT --data-binary 'package asm.authz import future.keywords import input.attributes.request.http as http_request import input.parsed_path default allow := false allow if { parsed_path[0] == "health" } allow if { http_request.method == "HEAD" } allow if { user_name == "bob" } user_name := parsed if { [_, encoded] := split(http_request.headers.authorization, " ") [parsed, _] := split(base64url.decode(encoded), ":") }'Run the following command to access the HTTPBin application by using the user named bob:
curl ${IP address of the ASM gateway}/status/201 -I -X GET --user bob:testpasswordExpected output:
HTTP/1.1 201 Created server: istio-envoy date: Tue, 25 Jul 2023 08:32:16 GMT content-type: text/html; charset=utf-8 access-control-allow-origin: * access-control-allow-credentials: true content-length: 0 x-envoy-upstream-service-time: 3The output indicates that the access of the user named bob is successful.
Run the following command to access the HTTPBin application by using the user named alice:
curl ${IP address of the ASM gateway}/status/201 -I -X GET --user alice:testpasswordExpected output:
HTTP/1.1 403 Forbidden date: Tue, 25 Jul 2023 08:32:49 GMT server: istio-envoy content-length: 0 x-envoy-upstream-service-time: 1The output indicates that the access of the user named alice is forbidden.