This topic describes how to migrate traffic from a self-managed Istio ingress gateway to a Service Mesh (ASM) ingress gateway.
Traffic flow of the migration solution
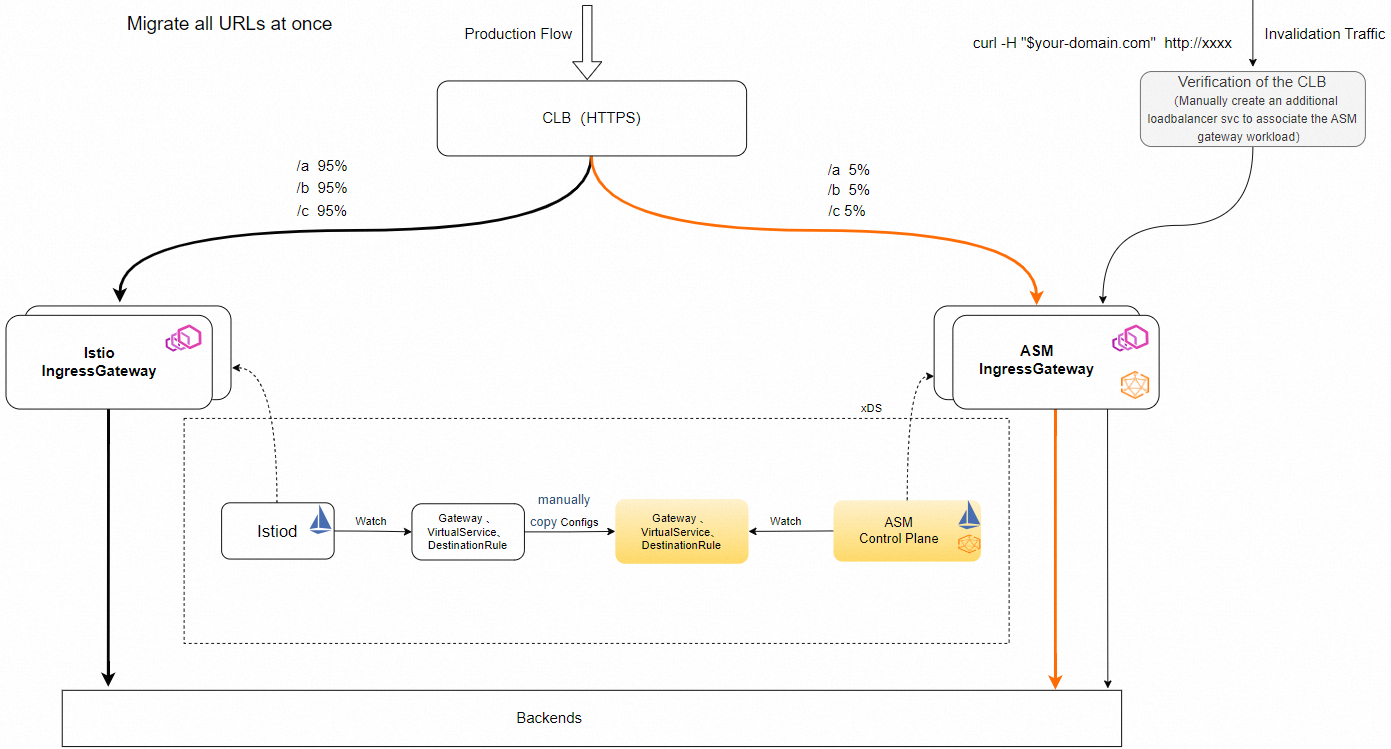
Step 1: Create an ingress gateway for the ASM instance
For more information, see Create an ingress gateway.
When you create an ASM ingress gateway, take note of the following points:
The name of the ASM ingress gateway must be different from the existing Istio ingress gateway. You can add the -asm suffix to the name of the ASM ingress gateway to distinguish the ASM ingress gateway from the existing Istio ingress gateway. For example, you can name the ASM ingress gateway ingressgateway-asm.
In Step 3 of the Create an ingress gateway topic, set the Cluster parameter to the Kubernetes cluster where the source Istio ingress gateway resides.
Change the Domain Name System (DNS) record of the domain name to the IP address of the ASM ingress gateway. If you cannot change the DNS record of the domain name, you can gradually migrate the traffic by adjusting the weights of source and destination ingress gateways. In this case, the ASM ingress gateway must reuse the Classic Load Balancer (CLB) instance that is associated with the source Istio ingress gateway. As shown in the preceding figure, the ASM ingress gateway reuses the CLB instance that is associated with the source Istio ingress gateway.
NoteFor more information about the reuse of the CLB instances that are created by using the LoadBalancer service type, see FAQ in this topic.
Step 2: Migrate configurations
Change the value of selector.istio to the name of your ASM ingress gateway in the YAML file to migrate ingress gateway configurations. Sample YAML file:
spec: selector: istio: ingressgateway-asmMigrate other configurations such as VirtualService and DestinationRule configurations.
Step 3: Migrate traffic
Modify the service annotations to adjust the weights of source and destination ingress gateways. You can first set the weight of the ASM ingress gateway to a small value, such as 10, and check whether the traffic flow meets expectations. Then, gradually increase the weight until all the traffic is routed to the ASM ingress gateway.
Methods of adjusting the weight:
To adjust the weight of the source Istio ingress gateway, edit the
service.beta.kubernetes.io/alibaba-cloud-loadbalancer-weightannotation for the corresponding service.To adjust the weight of the ASM ingress gateway, edit the
service.beta.kubernetes.io/alibaba-cloud-loadbalancer-weightservice annotation for the ASM ingress gateway.
FAQ: If a CLB instance is automatically created when a Service is created for a self-managed Istio ingress gateway, how do I reuse the CLB instance for an ASM ingress gateway?
Go to the CLB console and find the desired CLB instance. Delete the following two labels of the CLB instance:
kubernetes.do.not.deleteandack.aliyun.com.Add the following annotations to the corresponding Service of the self-managed Istio ingress gateway:
service.beta.kubernetes.io/alibaba-cloud-loadbalancer-force-override-listeners: "false"
service.beta.kubernetes.io/alibaba-cloud-loadbalancer-id: ${ID of the CLB instance}
service.beta.kubernetes.io/alibaba-cloud-loadbalancer-vgroup-port: ${ID of the vServer group}:${Port number}
service.beta.kubernetes.io/alibaba-cloud-loadbalancer-weight: "100"