You can use the Application Real-Time Monitoring Service (ARMS) console to connect your application to Application Security. This way, if you restart the local instances of the application, your application is protected. You do not need to modify the code of the application.
Prerequisites
- The application is a Java application monitored by Application Monitoring. This is because only Java applications can be connected to Application Security. For more information, see Overview.
- The ARMS agent meets the following requirements:
- In automatic upgrade scenarios, a containerized application or an Enterprise Distributed Application Service (EDAS) application must use the ARMS agent V2.7.1.2 or later. Note Automatic upgrade scenarios refer to the scenarios where you can automatically upgrade the ARMS agent by restarting applications or pods. For more information, see Update the ARMS agent for Java applications.a
- For a manual upgrade scenario, the ARMS agent must be V2.7.1.3 or later.
To view the version of the ARMS agent, perform the following operations: Log on to the ARMS console. In the left-side navigation pane, choose . Find the application and view the version of the ARMS agent. For information about how to upgrade an ARMS agent, see Update the ARMS agent for Java applications.
- In automatic upgrade scenarios, a containerized application or an Enterprise Distributed Application Service (EDAS) application must use the ARMS agent V2.7.1.2 or later.
Authorization
Before you connect the application to Application Security, you must authorize ARMS to access Alibaba Cloud Security. Then, ARMS gains limited access to relevant resources that Application Security depends on.
- Log on to the ARMS console.
- In the left-side navigation pane, choose .
- In the Application Security section, click Authorize Now.
- In the message that appears, click OK. After the authorization, ARMS automatically creates the AliyunServiceRoleForARMSSecurity service-linked role for Application Security. After the authorization is successful, you can view the application list and connect the application to Application Security. For information about the AliyunServiceRoleForARMSSecurity service-linked role, see Service-linked role for Application Security.Note If you are prompted that you do not have the permissions to create the service-linked role, contact the owner of the Alibaba Cloud account to add the specified policy for the current RAM user. For more information, see FAQ.
Connect the application to Application Security in Application Monitoring
- If your application is deployed in a Container Service for Kubernetes (ACK) cluster:
Add the tag
armsSecAutoEnable: "on". For more information, see Install an ARMS agent for Java applications deployed in ACK. - If your application is deployed in another environment:
Add the startup parameter
-Darms.appsec.enable=true. For more information, see Manually install an ARMS agent for a Java application.
Connect the application to Application Security in the ARMS console
If you have not activated Application Security when you connect the application to Application Monitoring, you can perform the following operations to connect the application to Application Security:
- Log on to the ARMS console.
- In the left-side navigation pane, choose . In the top navigation bar, select a region. The Applications page lists all Java applications that can be connected.Note Before you connect the application, make sure that the version of the ARMS agent is 2.7.1.3 or later.
- Connect the application.
- Connect an application: Click Add in the Actions column. In the message that appears, click OK.
- Connect multiple applications:
- On the Applications page, click Add Application.
- In the Add Application dialog box, select the applications that you want to connect from the No security applications are added. list, click the > icon to move the selected applications to the Security applications are added. list, and then click OK.
- Restart the local instances of the application to make the operation take effect.
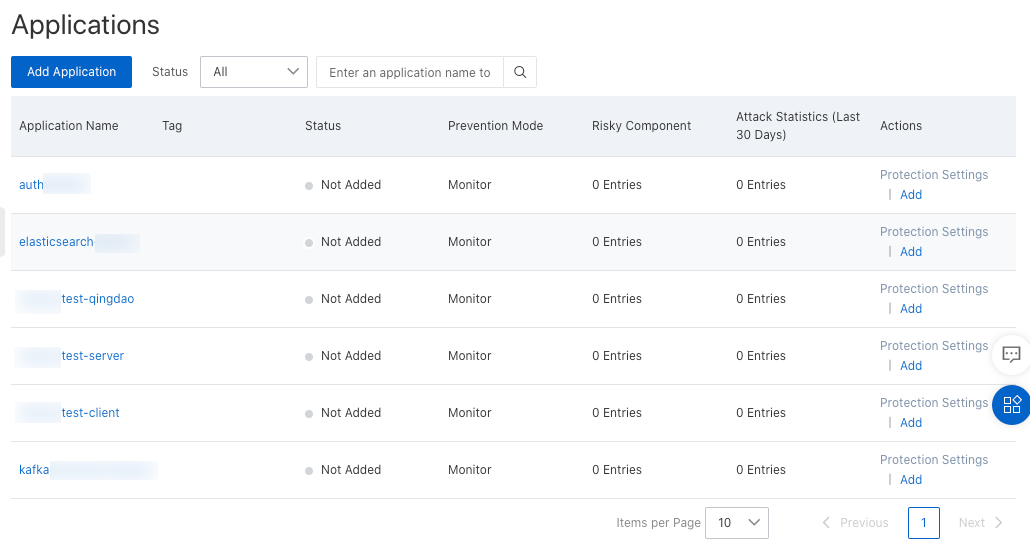
On the Applications page, check the connection status of the application in the Status column. After all instances are restarted, the application security feature takes effect on all instances for the application. If only some instances are restarted, the application security feature takes effect only on the restarted instances.
The Instances Added field in the Status column displays the number of connected instances and the number of all instances. You can click the numbers to view connection status of the instances.
Set the prevention mode
After you connect the application to Application Security, you can set the prevention mode of the application. The following prevention modes are available: Monitor, Monitor and Block, and Disable. The default prevention mode is Monitor. If the application is running as expected for a period of time, you can change the prevention mode to Monitor and Block. This ensures that the application can be protected against attacks.
- In the left-side navigation pane, choose . Find the application and then click Protection Settings in the Actions column.
- In the Protection Settings dialog box, set the following parameters and click OK.
Parameter Description Protection Mode - Monitor: monitors attacks. If alert rules are configured and an attack is detected, an alert is triggered. The application is not affected.
- Monitor and Block: monitors and blocks attacks. If an attack is blocked, the application throws an error.
- Disable: disables the application security feature for the current application. No attacks are detected or blocked.
Detection Timeout Period The maximum period to detect attacks. Valid values: 5 to 200000. Unit: milliseconds. Default value: 300. If the detection timeout period is reached, the original business logic continues to be executed even if the detection logic is not executed. We recommend that you use the default value. Attack Type The types of attacks to detect. We recommend that you retain the default settings. To retain the default settings, select Select All. For more information, see Attacks and solutions. Note If you modify the protection settings of the application, the new settings take effect with a latency of no more than 30 seconds.
Disconnect the application from Application Security
Disconnect the application from Application Security in Application Monitoring
Use one of the following methods to disconnect your application from Application Security in Application Monitoring:
- If your application is deployed in an ACK cluster:
Delete the tag
armsSecAutoEnable: "on". - If your application is deployed in another environment:
Delete the startup parameter
-Darms.appsec.enable=true.
Disconnect the application from Application Security in the ARMS console
To disconnect an application from Application Security, choose in the left-side navigation pane. On the page that appears, find the application and click Cancel in the Actions column. In the message that appears, click OK. You must restart the local instances of the application to make the operation take effect.
We recommend that you do not disconnect an application from Application Security only for the sake of application performance. After an application is connected to Application Security, the default prevention mode is Monitor. In Monitor mode, Application Security only reports attack alerts and does not block attacks. Therefore, the application is not affected. If you want to disable all security detection capabilities, you can change the prevention mode to Disable. In Disable mode, Application Security does not report attack alerts even if a security attack occurs.