This topic describes how to configure an IP address whitelist for an ApsaraDB RDS for MySQL instance. After an RDS instance is created, you must configure IP address whitelists for the RDS instance. A device can access the RDS instance only after you add the IP address of the device to an IP address whitelist of the RDS instance.
Prerequisites
An RDS instance is created. For more information, see Create an ApsaraDB RDS for MySQL instance.
Procedure
A system whitelist is configured for your RDS instance by default. The system whitelist is invisible and is used by system accounts to perform O&M operations on the databases of the RDS instance. For more information about system accounts, see System accounts.
Go to the Instances page. In the top navigation bar, select the region in which the RDS instance resides. Then, find the RDS instance and click the ID of the instance.
In the left-side navigation pane, click Whitelist and SecGroup.
View the network isolation mode of the RDS instance.
If your RDS instance runs MySQL 5.5, 5.6, or 5.7 and uses local disks, you can change the network isolation mode of the RDS instance to the enhanced whitelist mode. For RDS instances that run other database engine versions or use other storage types, the network isolation mode is set to standard whitelist mode.
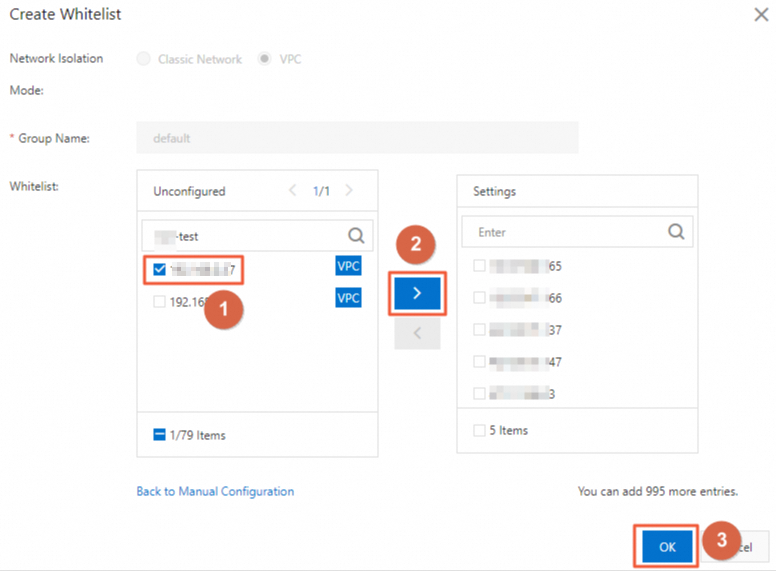
Click Modify to the right of default. You can use one of the following methods to configure an IP address whitelist for the RDS instance.
You can also click Create Whitelist and specify a whitelist name.
Method 1: Add the IP address of the server on which your application is deployed to the IP Addresses field. For more information about how to obtain the IP address of a server, see Appendix: Methods to obtain IP addresses. You can also click Load Local Public IP Address (If there is a network proxy on your PC, please turn it off first) to add the public IP address of your local computer.
If you add multiple IP addresses and CIDR blocks to an IP address whitelist, you must separate these IP addresses or CIDR blocks with commas (,). Do not add spaces preceding or following the commas.
You can add a maximum of 1,000 IP addresses and CIDR blocks in total for each RDS instance. If you want to add a large number of IP addresses, we recommend that you merge the IP addresses into CIDR blocks, such as 10.10.10.0/24.
If the RDS instance runs in enhanced whitelist mode, you must take note of the following considerations when you configure IP address whitelists for the RDS instance:
Add the public IP addresses or private IP addresses of Elastic Compute Service (ECS) instances that use classic networks to IP address whitelists of the classic network type.
Add the private IP addresses of VPC-type ECS instances to IP address whitelists of the VPC network type.
Method 2: Click Add Internal IP Address of ECS Instance to load the IP addresses of all ECS instances that are created within your Alibaba Cloud account in the region. Then, select the IP addresses and add them to an IP address whitelist.
The server on which your application is deployed can access the RDS instance only after you add the IP address of the server to an IP address whitelist of the RDS instance.
Click OK.
What to do next
Use a client or the CLI to connect to an ApsaraDB RDS for MySQL instance
References
For more information about how to modify an IP address whitelist of an RDS instance by calling an API operation, see ModifySecurityIps.
For more information about how to query the IP address whitelists of an RDS instance by calling an API operation, see DescribeDBInstanceIPArrayList.
For more information about how to configure an IP address whitelist for an RDS instance that runs a different database engine, see the following topics:
FAQ
A device can access my RDS instance but the IP address of the device is not added to an IP address whitelist of the RDS instance. Why?
You can use one of the following methods to troubleshoot the issue:
Check all IP address whitelists of your RDS instance. If one of the IP address whitelists contains the 0.0.0.0/0 entry, your RDS instance is at risk because this entry allows the access from all IP addresses. We recommend that you delete the 0.0.0.0/0 entry and add only trusted IP addresses to the IP address whitelist.
Check all security groups. If one of the security groups contains the IP address of the device, the device can access your RDS instance.
What do I do if I want to connect an on-premises host to my RDS instance without a public endpoint?
You can connect an on-premises host to your RDS instance over an internal network. For more information, see Connect a data center to a VPC.
How do I view the operator who added the IP address of a device to an IP address whitelist of my RDS instance?
In the left-side navigation pane of the instance details page, click Operation Audit. On the page that appears, find the event named ModifySecurityIps, and view the operator who added the IP address and the operation details.
If no fixed IP address is allocated to the server of a user, how do I add the IP address of the server to an IP address whitelist of my RDS instance?
If no fixed IP address is allocated to the server of a user and you cannot add
0.0.0.0/0to the IP address whitelist of your RDS instance, we recommend that you use identity authentication instead of IP address whitelists to implement access control. For example, you can use one of the following methods:Use dynamic Domain Name System (DNS) resolution: You can use dynamic DNS resolution to obtain the domain name that the dynamic IP address is mapped and add the domain name or the IP address that is resolved from the domain name to the IP address whitelist of the RDS instance.
Configure a reverse proxy or load balancer: All user requests are forwarded to the RDS instance by using the reverse proxy or load balancer. Only the fixed IP address of the proxy server is added to the IP address whitelist of the RDS instance.
Update the IP address whitelist at regular intervals: If IP addresses change within a specific range, such as IP addresses assigned by ISPs for home broadband, you can regularly obtain the IP addresses and add the IP addresses to the IP address whitelist of the RDS instance.
Appendix: Check whether your application can connect to the RDS instance over an internal network
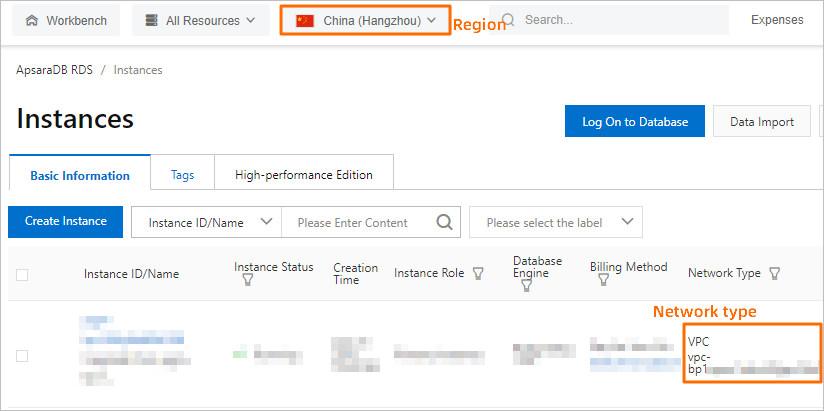
View the region and network type of the ECS instance on which your application is deployed. For more information, see Get ready to use ApsaraDB RDS.
View the region and network type of the RDS instance.
Log on to the ApsaraDB RDS console and go to the Instances page. In the top navigation bar, select the region in which the RDS instance resides. Then, find the RDS instance and click the ID of the instance. On the page that appears, you can view the region, network type, and VPC ID of the RDS instance.
Check whether the ECS instance and the RDS instance meet the following conditions for communication over an internal network:
The ECS instance and the RDS instance reside in the same region.
The ECS instance and the RDS instance reside in the same type of network. If the ECS instance and the RDS instance both reside in VPCs, these instances reside in the same VPC.
If one of the preceding conditions is not met, the ECS instance cannot communicate with the RDS instance over an internal network.
Appendix: Methods to obtain IP addresses
Table 1. Obtain IP addresses
Connection scenario | IP address to be obtained | Method to obtain the IP address |
You want to connect to the RDS instance from an ECS instance. The ECS instance and the RDS instance meet the conditions for communication over an internal network. | Private IP address of the ECS instance | Log on to the ECS console and go to the Instances page. In the top navigation bar, select the region in which the ECS instance resides. Then, view the public IP address and private IP address of the ECS instance. |
You want to connect to the RDS instance from an ECS instance. The ECS instance and the RDS instance do not meet the conditions for communication over an internal network. | Public IP address of the ECS instance | |
You want to connect to the RDS instance from an on-premises device. | Public IP address of the on-premises device | On the on-premises device, run the The IP address that you obtain by using this method may vary when the RDS instance after upgrades or configuration changes. If you cannot access an RDS instance after you add the IP address of your on-premises device to the whitelist of the RDS instance, refer to Why am I unable to connect to my ApsaraDB RDS for MySQL instance or ApsaraDB RDS for MariaDB instance from a local server over the Internet? |
Appendix: System whitelists
If you use Data Management (DMS), Data Transmission Service (DTS), and Database Autonomy Service (DAS) to access an RDS for MySQL instance, the system automatically adds the following whitelists to the RDS instance to allow access from DMS, DTS, and DAS.
Whitelist name | Configuration |
Whitelist name | Configuration |
dms | The whitelist enables DMS to log on to the RDS instance. |
dts | The whitelist enables DTS to read data from or write data to the RDS instance. |
hdm_security_ips | The whitelist enables DAS to obtain the data of the RDS instance, optimize and maintain databases, and perform security-related operations on the instance. If an RDS instance is created after December 2020, the IP address whitelist that is labeled hdm_security_ips is invisible to users. This prevents the IP address whitelist from being unintentionally modified or deleted. If the IP address whitelist is modified or deleted, related services cannot access the RDS instance. |