This topic describes security check items for a database, including cluster check items and tenant check items. You can enable security settings based on your business needs.
Background
OceanBase Database supports security check items on clusters and tenants, to guide you to configure necessary security settings to ensure overall database security.
Cluster check items: Check whether the whitelist range is too large, check whether link encryption is enabled, check whether the link encryption certificate has expired, check whether the remote backup feature is enabled, and check whether the SQL diagnostics feature is enabled.
Tenant check items: Check whether the whitelist range is too large, and check whether the transparent encryption feature is enabled.
Type | Check item | Description |
Cluster | Check whether the whitelist range is too large | If 0.0.0.0 or 0.0.0.0/0 is added to the whitelist of the cluster, all IP addresses are allowed to access the cluster. This is considered risky. |
Check whether link encryption is enabled | Check whether SSL link encryption is enabled for the cluster. If the feature is not enabled, it is not a risk. You can enable it as needed for security reinforcement. Once enabled, it cannot be disabled. | |
Verify whether the link encryption certificate has expired | When the validity period of the SSL certificate is less than 7 days, the certificate is to expire, and a risk alert is generated to prompt you to renew the certificate as soon as possible. | |
Check whether the remote backup feature is enabled | Check whether the remote backup feature is enabled for the cluster. If the feature is not enabled, it is not a risk. You can enable it as needed for security reinforcement. | |
Check whether the SQL diagnostics feature is enabled | Check whether the SQL diagnostics feature is enabled for the cluster. If the feature is not enabled, it is not a risk. You can enable it as needed for security reinforcement. | |
Tenant | Check whether the whitelist range is too large | If 0.0.0.0 or 0.0.0.0/0 is added to the whitelist of the tenant, all IP addresses are allowed to access the tenant. This is considered risky. |
Check whether the transparent encryption feature is enabled | Check whether the transparent encryption feature is enabled for the tenant. If the feature is not enabled, it is not a risk. You can enable it as needed for security reinforcement. Once enabled, it cannot be disabled. |
Procedure
In the left-side navigation pane, click Instances and select the destination cluster instance to go to the Cluster Instance Workspace page.
In the left-side navigation pane, click Security Settings.
Click the Security Assessment tab and view the statistics on Total Inspection Item(s), Cluster Security Risks, and Tenant Security Risks.
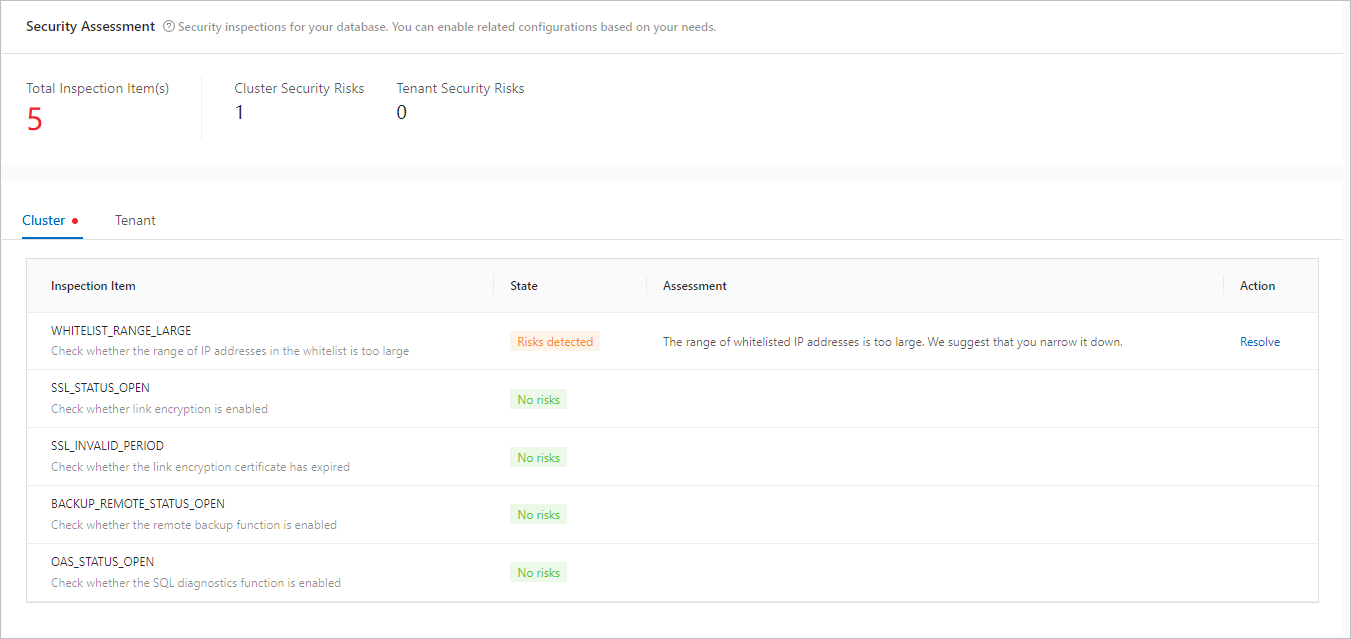
Click the Cluster tab and view the status of each cluster check item. For a project in the "Risks Detected" state, view the suggestions provided after the assessment and click To Resolve to go to the corresponding page to modify related settings.
Click the Tenant tab and view the status of each tenant check item. For a project in the "Risks Detected" state, view the suggestions provided after the assessment and click To Resolve to go to the corresponding page to modify related settings.