You must configure data sources before you create a data migration or synchronization task. This topic describes how to create a MySQL data source by using the data transmission service.
Security risks
You can choose to automatically or manually add public CIDR blocks for the data transmission service, but security risks exist. Your use of the data transmission service indicates that you have understood and acknowledged the possible security risks. You must take basic security protection measures, such as setting a complex password for your account, limiting the open port numbers of CIDR blocks, enabling authentication for communication among internal APIs, and regularly checking for and limiting CIDR blocks that are not required.
The data transmission service will add or delete the CIDR blocks automatically added to a whitelist or security group based on business needs and security risks. Do not use the CIDR blocks in a whitelist or security group for business needs other than the data transmission service. If you use such CIDR blocks for other business needs, the issues thus incurred are beyond the guarantee scope of the SLA of the data transmission service. For information about how to automatically or manually add the IP address of the data transmission server to a whitelist or security group, see Add a whitelist.
Procedure
Log on to the
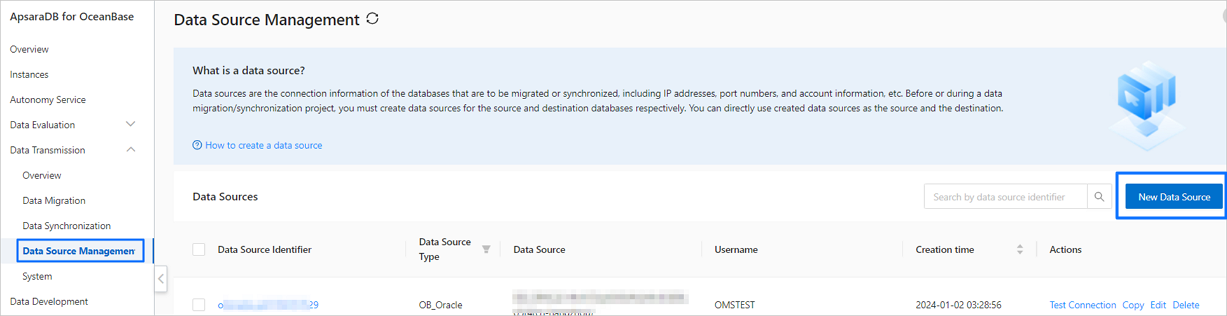
ApsaraDB for OceanBase console.In the left-side navigation pane, choose Data Transmission > Data Source Management.
In the Data Sources section, click New Data Source in the upper-right corner.
In the New Data Source dialog box, select MySQL for Data Source Type.
Configure the parameters. Select an instance type from the Instance Type drop-down list. The corresponding configuration section automatically appears.
Instance type
Parameter
Description
RDS Instance
RDS Instance ID
The ID of the target ApsaraDB RDS instance. Select the ID from the drop-down list.
PolarDB Instance
PolarDB Instance ID
The ID of the target PolarDB instance. Select the ID from the drop-down list.
Self-Managed Database in VPC
VPC
Select the desired virtual private cloud (VPC) from the VPC drop-down list. You can also perform a fuzzy search.
Host IP Address
The IP address of the host where the database is located.
Port
The port number of the host where the database is located.
Self-Managed Database with Public IP Address
Host IP Address
The IP address of the host where the database is located.
Port
The port number of the host where the database is located.
Common parameters
Data Source Identifier
We recommend that you set it to a combination of digits and letters. It must not contain any spaces and cannot exceed 32 characters in length.
Cross Alibaba Cloud Account
The data transmission service allows you to configure a task to migrate or synchronize data between instances under different Alibaba Cloud accounts.
You can choose whether to select this option based on business needs. If you select this option, enter the Alibaba Cloud account of the target instance. If you do not have permissions on this Alibaba Cloud account, request for authorization first. For more information, see Apply for cross-account authorization.
ImportantThis parameter is unavailable if you select Self-Managed Database with Public IP Address as the instance type.
Username
The name of the MySQL database user for data migration or synchronization.
We recommend that you create a separate database user for the migration or synchronization task.
Password
The password of the database user.
Remarks
The additional information about the data source.
Enable SSL
In the New Data Source dialog box, you can click Expand next to Advanced Options and set this parameter as needed.
ImportantBefore you select this parameter, enable SSL encryption for the database instance.
Click Test Connection to verify the network connection between the data transmission service and the data source, as well as the validity of the username and password.
After the test is passed, click OK.