You can create cloud service interaction rules to enable Anti-DDoS Proxy to work together with Alibaba Cloud resources that are assigned public IP addresses. The cloud service interaction feature prevents additional service access latency after a website is added to an Anti-DDoS Proxy instance.
Prerequisites
Your services use an Alibaba Cloud resource that is assigned a public IP address, such as an elastic IP address (EIP) or a Web Application Firewall (WAF), Elastic Compute Service (ECS), or Server Load Balancer (SLB) instance.
An Anti-DDoS Proxy (Chinese Mainland) instance of the Profession mitigation plan or an Anti-DDoS Proxy (Outside Chinese Mainland) instance of the Insurance or Unlimited mitigation plan is purchased.
ImportantThe clean bandwidth and queries per second (QPS) of the instance must meet the mitigation requirements of your services.
For more information, see Purchase an Anti-DDoS Proxy instance.
Your website is added to the instance for protection.
For more information, see Add one or more websites.
The instance forwards service traffic as expected.
For more information, see Verify the forwarding configurations on your on-premises computer.
Background information
After you add your service to the Anti-DDoS Proxy instance, service traffic is automatically scrubbed by the instance. Then, only service traffic is forwarded to the origin server. Service traffic is forwarded by the instance even if no attacks occur, which increases service access latency.
If you want to prevent additional latency, you can create a cloud service interaction rule for Sec-Traffic Manager. This rule allows service traffic to be switched to the instance for scrubbing and then to the origin server only if an attack occurs. If no attacks occur, service traffic is directly forwarded to the origin server.
Create a cloud service interaction rule
Log on to the Anti-DDoS Proxy console.
In the top navigation bar, select the region of your instance.
Anti-DDoS Proxy (Chinese Mainland): If your instance is an Anti-DDoS Proxy (Chinese Mainland) instance, select Chinese Mainland.
Anti-DDoS Proxy (Outside Chinese Mainland): If your instance is an Anti-DDoS Proxy (Outside Chinese Mainland) instance, select Outside Chinese Mainland.
In the left-side navigation pane, choose .
On the General Interaction tab, click Add Rule.
In the Add Rule panel, configure a cloud service interaction rule and click Next.
Figure 1 Sample configuration of a cloud service interaction rule in the Anti-DDoS Proxy (Chinese Mainland) console
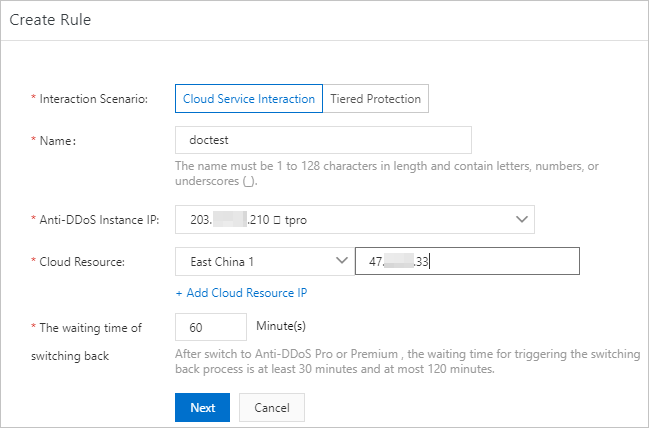
Parameter
Description
Interaction Scenario
Select Cloud Service Interaction.
Rule Name
Enter a name for the rule.
The name can be up to 128 characters in length and can contain letters, digits, and underscores (_).
Anti-DDoS Pro
Select an Anti-DDoS Proxy instance.
Resource for Interaction
Enter the IP address of the cloud resource. You can enter an EIP or the IP address of an ECS, SLB, or WAF instance.
You can click Add IP Address of Cloud Resource to add more IP addresses. You can add up to 20 IP addresses.
NoteAfter you add multiple IP addresses, these IP addresses are associated with the specified Anti-DDoS Proxy instance. If one of the IP addresses is attacked, service traffic is forwarded to other IP addresses. Service traffic is forwarded to the Anti-DDoS Proxy instance only if all IP addresses are attacked. For more information about how to forward traffic to Anti-DDoS Proxy when one of the IP addresses is attacked, see Share one Anti-DDoS Proxy instance among multiple cloud resources.
Waiting Time of Switchback
Specify the waiting time before the service traffic is switched from your Anti-DDoS Proxy instance back to the IP address of a cloud resource. When the attack stops and the waiting time that you specify elapses, the service traffic is automatically switched back to the IP address of the cloud resource.
You can specify a value that ranges from 30 to 120. Unit: minutes. We recommend that you set the value to 60.
NoteIf blackhole filtering is triggered for your Anti-DDoS Proxy instance or before the specified waiting time that starts from the start time of the blackhole filtering event of the instance elapses, the service traffic of a cloud resource cannot be switched to the instance.
If blackhole filtering is triggered for a cloud resource, the service traffic of the cloud resource is automatically switched to your Anti-DDoS Proxy instance for protection. If blackhole filtering is not deactivated for the cloud resource, the service traffic cannot be switched from your Anti-DDoS Proxy instance back to the cloud resource. If blackhole filtering is deactivated for the cloud resource, the service traffic can be immediately switched back to the cloud resource regardless of the specified waiting time.
Change the DNS records of the domain name as prompted and click Complete.
For the cloud service interaction rule to take effect, you must change the DNS records of your domain name on the website of your DNS service provider to map the domain name to the CNAME provided by Sec-Traffic Manager. If your DNS service is provided by Alibaba Cloud DNS, you need to only change the DNS records in the Alibaba Cloud DNS console.
ImportantAfter you change the DNS record of your domain name, the network acceleration rule takes effect. Before you change the DNS records, we recommend that you modify the hosts file on your on-premises computer to verify the cloud service interaction rule. This helps prevent incompatibility issues caused by inconsistent back-to-origin policies. CDN allows you to change the origin host for back-to-origin requests. However, you cannot use Anti-DDoS Proxy to change the origin host for back-to-origin requests. If you use CDN together with Anti-DDoS Proxy to retrieve data from an Object Storage Service (OSS) object, the service traffic that is forwarded by Anti-DDoS Proxy cannot be identified by OSS. As a result, your services are interrupted. For more information about origin hosts, see Configure the default origin host.
For more information about how to verify traffic forwarding rules, see Verify the forwarding configurations on your on-premises computer.
For more information about how to change the DNS records of a domain name, see Change the CNAME record to redirect traffic to Sec-Traffic Manager.
If no DDoS attacks occur on your cloud resource after you enable the cloud service interaction rule, traffic is not scrubbed by your Anti-DDoS Proxy instance and is directly forwarded from the client to the cloud resource. If DDoS attacks occur on your cloud resource after you enable the cloud service interaction rule, traffic is automatically switched to your Anti-DDoS Proxy instance for scrubbing, and only service traffic is forwarded to the cloud resource. After traffic is automatically switched to your Anti-DDoS Proxy instance, the instance switches the service traffic back to the cloud resource when the attacks stop and the waiting time that you specify elapses.
In addition to automatic switchback, you can manually switch the traffic to your Anti-DDoS Proxy instance for scrubbing and then to the cloud resource based on the protection requirements of your services. For more information, see What to do next.
What to do next
After a cloud service interaction rule is created, you can perform the following operations on the rule.
Operation | Description |
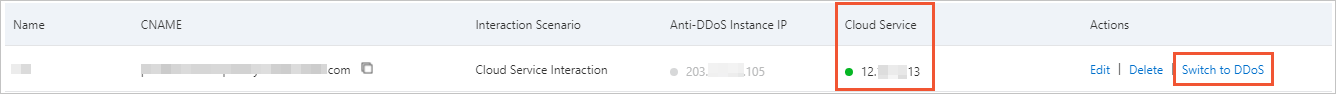
Switch to Anti-DDoS | If traffic scrubbing is not automatically triggered by your Anti-DDoS Proxy instance, the Traffic can be switched to your instance only if blackhole filtering is not triggered for the IP address of the instance. Important After you manually switch traffic to your Anti-DDoS Proxy instance, the traffic cannot be automatically switched back to the associated cloud resources. To switch the traffic back to the associated cloud resources, you must click Switchback to manually switch the service traffic. |
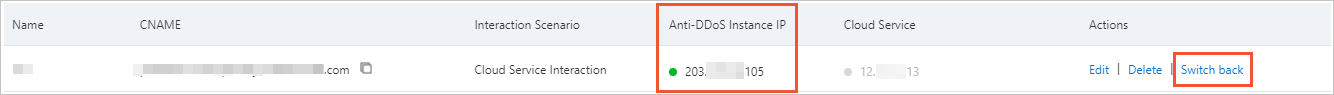
Switchback | If traffic is scrubbed by your Anti-DDoS Proxy instance, the Important
If blackhole filtering is triggered for the IP addresses of all associated cloud resources, the switchback fails. If blackhole filtering is deactivated for specific cloud resources, traffic is switched back to the cloud resources first. After blackhole filtering is deactivated for the remaining cloud resources, traffic is switched back to the cloud resources. |
Edit | You can modify the cloud service interaction rule. However, you cannot change the values of Interaction Scenario and Rule Name for the rule. |
Delete | You can delete the cloud service interaction rule. Warning Before you delete an interaction rule, make sure that the domain name of your website is not pointed to the CNAME of Sec-Traffic Manager. Otherwise, access to your website may fail after you delete the rule. |
 icon is displayed in the Resource for Interaction column. You can manually switch traffic before blackhole filtering is triggered. This reduces adverse impacts on your services.
icon is displayed in the Resource for Interaction column. You can manually switch traffic before blackhole filtering is triggered. This reduces adverse impacts on your services.