After you enable the mitigation analysis feature, you can query and analyze mitigation logs that record the events of an Anti-DDoS Origin instance. The events include traffic scrubbing, blackhole filtering, and traffic rerouting.
Prerequisites
The mitigation analysis feature is enabled. For more information, see Enable mitigation analysis.
Query and analyze mitigation logs
Log on to the Traffic Security console.
In the left-side navigation pane, choose .
In the top navigation bar, select the resource group to which the instance belongs and the region in which the instance resides.
For an Anti-DDoS Origin 1.0 instance or EIP with Anti-DDoS (Enhanced) enabled, select the region in which the instance or EIP resides.
For an Anti-DDoS Origin 2.0 instance, select All Regions.
On the Mitigation Logs page, select an Anti-DDoS Origin instance.
Enter a query statement in the search box.
A query statement consists of a search statement and an analytic statement in the Search statement|Analytic statement format. For more information, see Search syntax and SQL syntax and functions.
In the upper-right corner of the page, specify a time range for the query.
NoteThe query results contain reports that are generated 1 minute earlier or later than the specified time range.
Click Search & Analyze to view the query results.
Manage query and analysis results
You can view the query and analysis results in a log distribution histogram, on the Raw Logs tab, or by using a chart. You can also configure alert rules and saved searches.
By default, only 100 rows of data are returned after you execute a query statement. You can use a LIMIT clause to change the number of returned rows. For more information, see LIMIT clause.
Query result histogram
The query result histogram displays the distribution of query and analysis results in different time ranges.
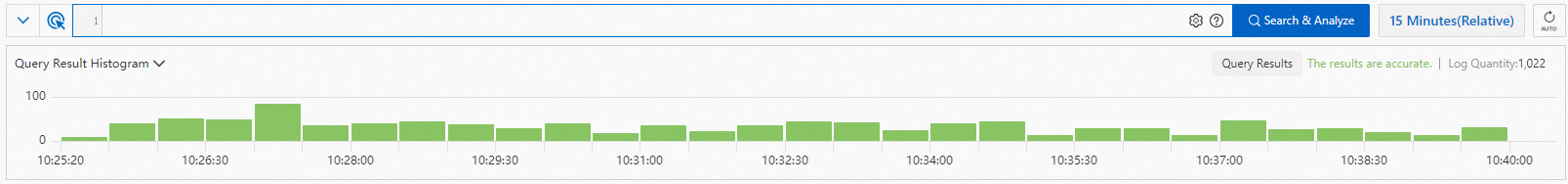
If you move the pointer over a green rectangle, you can view the time range that is represented by the rectangle and the number of logs that are obtained within the time range.
If you double-click the green rectangle, you can view a more fine-grained log distribution. You can also view the query and analysis results on the Raw Logs tab.
Raw Logs tab
On the Raw Logs tab, you can view the logs that match your search conditions. You can click Table or Raw Data to view the logs and perform the following operations:
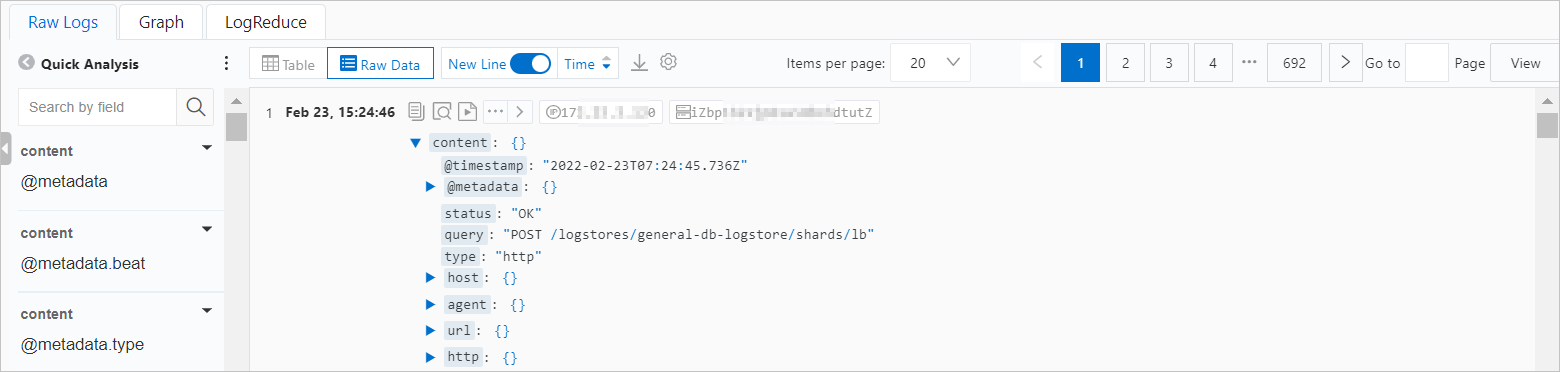
Quick analysis: You can use this feature to analyze the distribution of a specific field within a specific period of time. For more information, see Quick analysis.
You can click the
 icon to specify whether to show the names or aliases of fields. You can specify aliases when you create indexes. For example, if you set the alias of the host_name field to host, host is displayed in the Quick Analysis list after you select Show Field Aliases. Note
icon to specify whether to show the names or aliases of fields. You can specify aliases when you create indexes. For example, if you set the alias of the host_name field to host, host is displayed in the Quick Analysis list after you select Show Field Aliases. NoteIf you do not specify an alias for a field, the field name is displayed after you select Show Field Aliases.
Contextual query: On the Raw Data tab, you can find a log and click the
 icon to view the context of the log in the raw log file. For more information, see Contextual query. Important
icon to view the context of the log in the raw log file. For more information, see Contextual query. ImportantThe contextual query feature is supported only for log data that is collected by Logtail.
LiveTail: On the Raw Data tab, you can find a log and click the
 icon to monitor logs in real time and extract important information from the logs. For more information, see LiveTail. Important
icon to monitor logs in real time and extract important information from the logs. For more information, see LiveTail. ImportantThe LiveTail feature is supported only for log data that is collected by Logtail.
Tag configurations: On the Raw Data tab, you can click the
 icon and select Tag Configurations to hide fields that are less important.
icon and select Tag Configurations to hide fields that are less important. 
Column settings: On the Table tab, you can click the
 icon and select Column Settings to specify the columns that you want to display in the table. The column names are field names, and the column content is used as field values.
icon and select Column Settings to specify the columns that you want to display in the table. The column names are field names, and the column content is used as field values. 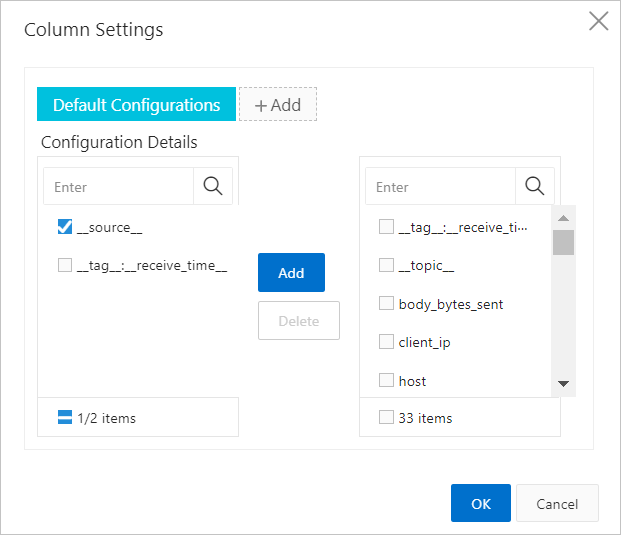
JSON configurations: On the Table or Raw Data tab, you can click the
 icon and select JSON Configurations to specify the level for JSON expansion.
icon and select JSON Configurations to specify the level for JSON expansion. Event settings: On the Table or Raw Data tab, you can click the
 icon and select Event Settings to configure events for raw logs. For more information, see Configure events.
icon and select Event Settings to configure events for raw logs. For more information, see Configure events. Log download: On the Table or Raw Data tab, you can click the
 icon to download logs. You can specify the method that is used to download logs and the range of logs to download. For more information, see Download logs.
icon to download logs. You can specify the method that is used to download logs and the range of logs to download. For more information, see Download logs.
Graph tab
After you execute a query statement, you can view the query and analysis results on the Graph tab.
View query and analysis results: Simple Log Service renders the results of query statements into charts. Simple Log Service provides multiple chart types, such as tables, line charts, and bar charts. Simple Log Service provides the following versions of charts: Pro and Standard. For more information, see Overview of charts (Pro) and Chart overview.
Simple Log Service allows you to create dashboards to perform real-time data analysis. You can click Add to New Dashboard to save query and analysis results as charts to a dashboard. For more information, see Overview of visualization.
Configure interaction occurrences: Interaction occurrences are important for data analysis. You can use interaction occurrences to switch between the levels of data dimensions and the analysis granularities to obtain more detailed information. For more information, see Drill-down events.
LogReduce tab
On the LogReduce tab, you can click Enable LogReduce to cluster similar logs. For more information, see LogReduce.
Alerting
On the Search & Analysis page, you can click the
 icon to configure an alert rule based on the query and analysis results. For more information, see Configure an alert monitoring rule in Log Service.
icon to configure an alert rule based on the query and analysis results. For more information, see Configure an alert monitoring rule in Log Service. Saved searches
On the Search & Analysis page, you can click the
 icon to save a query statement as a saved search. For more information, see Saved search.
icon to save a query statement as a saved search. For more information, see Saved search.