Service Mesh (ASM) includes a sidecar injector that automatically injects sidecar proxies into new pods. You can configure injection policies to meet specific needs using labels to select which pods require a sidecar. This helps you use resources more efficiently and simplifies management. Based on the size and load of your cluster, you can also adjust the injector's resource configuration to ensure it has sufficient resources to run.
Prerequisites
An ACK cluster has been added to the ASM instance. For more information, see Add a cluster to an ASM instance.
Configure automatic injection policies
You can match pods for sidecar injection using the labels of the pod's namespace, the pod's labels, or the pod's annotations.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Sidecar Proxy injection page, in the Injection strategy configuration management section, configure the automatic injection policy.
A sidecar is automatically injected into a pod only if the pod matches both the Pod namespace label should meet condition and the Pod label/annotation should meet condition.
Matching condition
Description
Pod namespace label should meet condition
The matching condition for the labels of the namespace where the pod resides.
Include istio-injection: enabled: The pod meets the automatic injection condition if its namespace contains the istio-injection: enabled label.
Not include istio-injection: disabled: The pod meets the automatic injection condition if its namespace does not contain the istio-injection: disabled label.
Pod label/annotation should meet condition
The matching condition for the pod's own labels or annotations.
Not Include sidecar.istio.io/inject: "false" or Selected by NeverInjectSelector: The pod meets the automatic injection condition if it does not have the sidecar.istio.io/inject: "false" label or annotation.
Include sidecar.istio.io/inject: "true" or Selected by AlwaysInjectSelector: The pod meets the automatic injection condition if it has the sidecar.istio.io/inject: "true" label or annotation.
NoteFor ASM instances earlier than version 1.12, automatic injection is supported only by matching pod annotations.
For ASM instances of version 1.12 and later, automatic injection is supported by matching both pod labels and annotations.
Labels have a higher matching priority than annotations. For example, if a pod has both the sidecar.istio.io/inject: "true" label and the sidecar.istio.io/inject: "false" annotation, the pod is marked with the sidecar.istio.io/inject: "true" label, not the sidecar.istio.io/inject: "false" annotation.
NoteIf you configure a policy where the namespace does not include the istio-injection: disabled label and the pod does not include the sidecar.istio.io/inject: "false" label, ASM automatically adds the istio-injection: disabled label to the kube-system namespace. This ensures that system components are not affected.
(Optional) Below the Injection strategy configuration management section, click Show Advanced Settings to configure advanced options.
Configuration item
Description
The label selector which selector pods to be injected istio-proxy (AlwaysInjectSelector)
AlwaysInjectSelector is a configurable pod label selector. Pods selected by AlwaysInjectSelector are treated as if they have the sidecar.istio.io/inject:"true" label or annotation.
The label selector which selector pods which will never be injected (NeverInjectSelector)
NeverInjectSelector is a configurable pod label selector. Pods selected by NeverInjectSelector are treated as if they have the sidecar.istio.io/inject:"false" label or annotation.
NoteAlwaysInjectSelector and NeverInjectSelector are both pod label selectors and are configured in the same way. Each selector can have multiple lines, and each line is a label selection expression. A pod is selected if its labels match any of the expressions.
Each label selection expression has three parts:
Key: The key from the pod's label used for matching.
Operator: The operator used to match pod labels. You can select one of the following four operators:
In: The expression matches if the pod's label value is in the specified list of values.
NotIn: The expression matches if the pod's label value is not in the specified list of values.
Exists: The expression matches if the specified key exists in the pod's labels.
DoesNotExist: The expression matches if the specified key does not exist in the pod's labels.
Value: If you select In or NotIn for the operator, specify a list of values to match against.
At the bottom of the page, click Update Settings.
Configure the sidecar injector
The sidecar injector is an admission webhook service deployed in the data plane Kubernetes cluster. It is not a sidecar proxy but is responsible for automatically injecting sidecar proxies. The service and workloads of the sidecar injector are deployed in the istio-system namespace of the Kubernetes cluster, and their names start with istio-sidecar-injector. You can adjust the resource settings and the number of replicas for the sidecar injector component to ensure its availability when many pods are injected simultaneously. We recommend that you configure monitoring metrics and alert rules for the admission webhook service of the sidecar injector. For more information, see Container Service alert management and kube-apiserver: Monitoring metrics.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Sidecar Proxy injection page, in the Injection strategy configuration management section, configure the sidecar injector. Then, at the bottom of the page, click Update Settings.
Configuration item
Description
Resource Settings for Sidecar Injector
Configure the Resource Limits and Required Resources for the sidecar injector container.
Resource Limits: Configure the CPU and memory resource limits for the sidecar injector container. The unit for CPU is cores, and the unit for memory is MiB.
Required Resources: Configure the CPU and memory resources required by the sidecar injector container. The unit for CPU is cores, and the unit for memory is MiB.
pod replicas
Configure the number of replicas for the sidecar injector pod.
NoteIncreasing the number of replicas improves the availability of the sidecar injection service when many pods are injected at the same time. We recommend that you set the number of pod replicas to 2 or more.
Rewrite App Probe
Specifies whether to rewrite the health check for the pod during injection. To determine to enable health check rewriting, see Enable health check redirection for applications in a service mesh.
Sidecar-injector NodeSelector
Select the nodes where the sidecar injector pods are deployed by matching labels.
Click Add Match Label, and enter the Name and Value of a data plane cluster node label to match specific deployment nodes.
Example 1: Disable automatic injection for specific pods in a namespace and enable it for others
Configure the automatic injection policy.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Sidecar Proxy injection page, in the Injection strategy configuration management section, configure the related information.
The following configuration indicates that sidecar proxies are automatically injected into all pods within a namespace that has the istio-injection: enabled label, unless a pod has the sidecar.istio.io/inject: "false" label or annotation.
Configuration item
Description
Pod namespace label should meet condition
Select Include istio-injection: enabled
Pod label/annotation should meet condition
Select Not Include sidecar.istio.io/inject: "false" or Selected by NeverInjectSelector
Create a global namespace and enable automatic injection for it.
On the details page of the ASM instance, choose in the left-side navigation pane. On the page that appears, click Create.
In the Create Namespace panel, enter a Name for the namespace. In this example, use test1. To the right of Labels, click Add. Set Name to istio-injection and Value to enabled. Then, click OK.
At the top of the page, click Sync Sidecar Auto-Injection from Kubernetes Cluster to sync the global namespace with the data plane Kubernetes cluster.
Create an application.
Create the details application in the test1 namespace of the data plane ACK cluster. For more information, see Deploy an application in a cluster associated with an ASM instance.
Verify whether a sidecar proxy is injected into the pod of the application.
Log on to the ACK console. In the navigation pane on the left, choose Clusters.
On the Clusters page, click the name of the target cluster. In the navigation pane on the left, choose .
At the top of the Deployments page, set Namespace to test1 and click the name of the details application.
On the Pods tab, you can see that the pod contains a Proxy image. This indicates that the sidecar proxy was successfully injected.
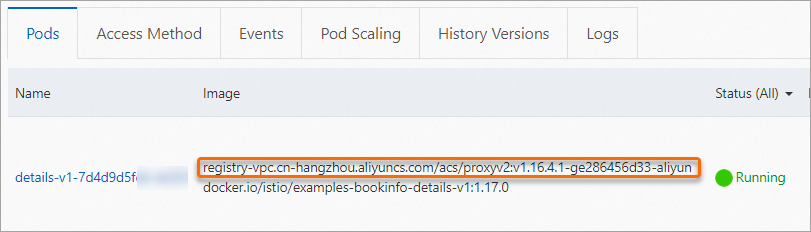
Add a label to the pod to disable automatic injection.
Log on to the ACK console. In the navigation pane on the left, choose Clusters.
On the Clusters page, click the name of the target cluster. In the navigation pane on the left, choose .
On the Stateless page, click More > Edit YAML in the Actions column of the details application in the test1 namespace.
In the Edit YAML dialog box, modify the YAML configuration and click Update.
If your ASM version is 1.12.4 or later, add a label to the labels parameter with the key
sidecar.istio.io/injectand the value"false", that is,sidecar.istio.io/inject: 'false'.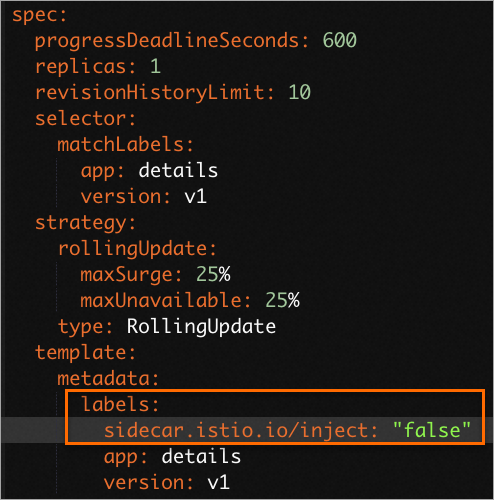
If the ASM version is earlier than 1.12.4, add an annotation under the annotations parameter with the key
sidecar.istio.io/injectand the value"false":sidecar.istio.io/inject: "false".
Verify that automatic injection is disabled for the pod of the details service, even though automatic injection is enabled for the test1 namespace.
Log on to the ACK console. In the navigation pane on the left, choose Clusters.
On the Clusters page, click the name of the target cluster. In the navigation pane on the left, choose .
At the top of the Deployments page, set Namespace to test1 and click the name of the details application.
On the Pods tab, you can see that the pod does not contain a Proxy image. This indicates that automatic injection is disabled for the pod of the details service, even though automatic injection is enabled for the test1 namespace.
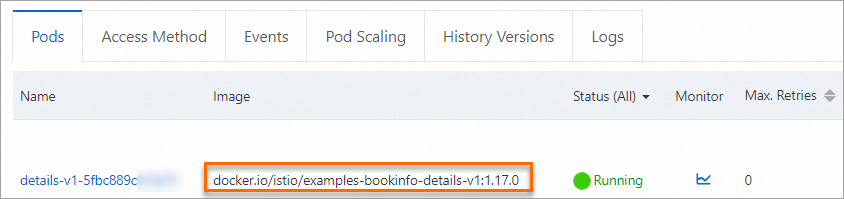
Example 2: Configure an automatic injection policy for an individual pod
If you do not want to configure automatic injection policies at the namespace level, you can configure them for individual pods. The following steps describe how to perform this operation.
Configure the automatic injection policy.
Log on to the ASM console. In the left-side navigation pane, choose .
On the Mesh Management page, click the name of the ASM instance. In the left-side navigation pane, choose .
On the Sidecar Proxy injection page, in the Injection strategy configuration management section, configure the related information. Then, at the bottom of the page, click Update Settings.
The following configuration indicates that sidecar proxies are automatically injected into all pods that have the sidecar.istio.io/inject: "true" label. However, sidecar proxies are not injected into any pods in a namespace that has the istio-injection:disabled label.
Configuration item
Description
Pod namespace label should meet condition
Select Not include istio-injection: disabled
Pod label/annotation should meet condition
Select Include sidecar.istio.io/inject: "true" or Selected by AlwaysInjectSelector
In the ACK cluster, create a namespace named test2 that does not have any labels. For more information, see Manage namespaces and quotas.
Create the reviews application in the test2 namespace of the ACK cluster. For more information, see Deploy an application in a cluster associated with an ASM instance.
Add a label to the pod to enable automatic injection.
Log on to the ACK console. In the navigation pane on the left, choose Clusters.
On the Clusters page, click the name of the target cluster. In the navigation pane on the left, choose .
At the top of the Stateless page, set Namespace to test2. In the Actions column for the reviews service, click More > View YAML.
In the Edit YAML dialog box, under the labels parameter, add the
sidecar.istio.io/inject: "true"label. Then, click Update.NoteTo use labels to configure automatic injection for pods, your Service Mesh (ASM) instance must be version 1.12.4 or later. For more information about how to upgrade an instance, see Upgrade an ASM instance.
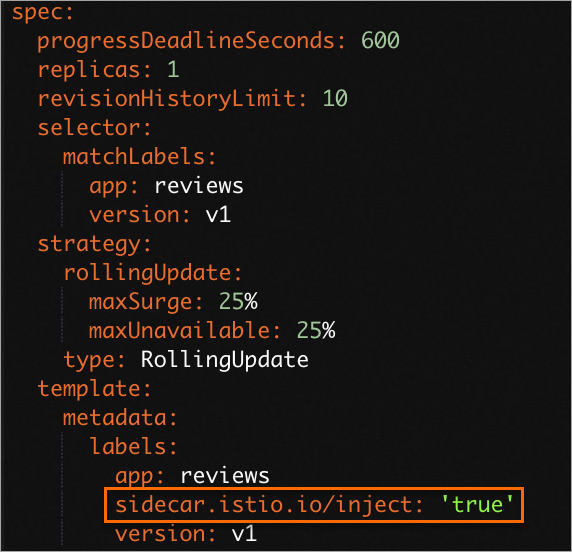
Verify that the automatic injection policy is successfully configured for the pod.
Log on to the ACK console. In the navigation pane on the left, choose Clusters.
On the Clusters page, click the name of the target cluster. In the navigation pane on the left, choose .
At the top of the Stateless page, set Namespace to test2, and click the name of the reviews application.
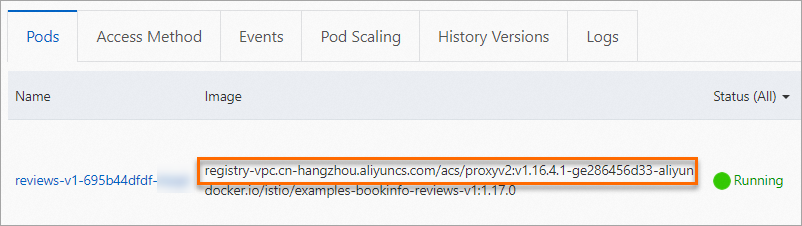
On the Pods tab, you can see that the pod contains a Proxy image. This indicates that the automatic injection policy is successfully configured for the pod.
References
Running pods must be restarted for the sidecar injection policy to take effect. For more information, see Restart a pod.
If applications with Istio enabled still use an old version of the sidecar proxy after you upgrade the control plane, you must upgrade the sidecar proxy. For more information, see Upgrade sidecar proxies.
You can configure the resource usage, traffic interception policy, DNS proxy, and lifecycle of sidecar proxies at different levels, such as global, namespace, workload, and pod. For more information, see Configure a sidecar proxy.