Common Vulnerabilities and Exposures (CVEs) in a node's operating system (OS) can cause data breaches, service interruptions, and other issues. These vulnerabilities threaten the stability, security, and compliance of your cluster. You can enable the OS CVE patching feature to scan for security vulnerabilities on nodes, receive patching recommendations, and quickly apply fixes from the console.
Prerequisites
This feature is an advanced feature provided by Security Center. To use this feature, you must subscribe to the Pro, Enterprise, or Ultimate edition of Security Center and have a sufficient quota. ACK does not charge extra fees for this feature. For more information, see Purchase Security Center and Features.
Usage notes
Security Center ensures the compatibility of CVE patches. However, you must verify the compatibility of your cluster applications with these patches. If you encounter issues during the patching process, you can pause or cancel the patching Job at any time.
If a node restart is required to patch a CVE vulnerability, ACK drains the node before restarting it.
Cluster usage: Make sure that the cluster usage is not too high. Sufficient pod allocation space is required for the drain operation.
To ensure high availability, we recommend that you scale out the node pool to add more nodes before you enable this feature. For more information, see Manually scale a node pool.
PDB restrictions: If you configured a pluggable database (PDB), ensure that the cluster has enough resources for the drain operation. The number of pod replicas must meet the minimum availability requirement specified in the PDB. The number of pod replicas must be greater than the value of
spec.minAvailable. If this PDB restriction is not required, you can delete the PDB rule.Pod termination: Ensure that the containers in a pod can properly handle the TERM (SIGTERM) signal. This prevents the pod from failing to terminate within the grace period, which would cause the drain operation to fail.
Maximum drain timeout: The maximum timeout period for a drain operation is 1 hour. If the drain operation does not succeed within the timeout period, ACK stops subsequent operations.
When you patch CVE vulnerabilities that require a node restart, if the target nodes include GPU nodes, we recommend that you manually upgrade the kernel instead. This helps avoid GPU driver compatibility issues. For more information, see Manually upgrade the kernel of a GPU node in an existing cluster.
CVE patching Jobs are executed in batches. If a Job is paused or canceled, batches that have already started will continue to run until they are complete. Pending batches will be paused or canceled.
CVE patching Jobs run within the configured cluster maintenance window. If a Job's running time exceeds the maintenance window, the unfinished part of the Job is automatically canceled. Batches that have already started will continue to run until they are complete. Pending batches will be canceled.
Only one CVE patching Job can run on a node pool at a time.
If the operating system is ContainerOS, we recommend that you fix CVE vulnerabilities by upgrading the operating system. Only ContainerOS 3.2 and 3.3 support the CVE vulnerability fix feature.
For more information about ContainerOS versions, see Release notes for ContainerOS images.
If you change the maintenance window, scheduled CVE patching plans are canceled. A new schedule will be created later.
Procedure
Automatically patch OS CVE vulnerabilities (recommended)
Managed node pools provide automated Operations and Maintenance (O&M) capabilities that allow you to automatically patch OS CVE vulnerabilities. After you enable this feature, ACK schedules and runs patching plans based on global Job rules. Automatic patching runs within the configured maintenance window. Because ACK uses a progressive push method for patching, there may be a delay before a patch is applied to a node pool after a vulnerability is detected. The delay can vary based on factors such as the region.
Starting from August 5, 2025, parameters related to the automatic CVE vulnerability patching policy will be adjusted. For more information, see Change 3: Adjustments to parameters related to the automatic security vulnerability patching policy.
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the cluster to manage and click its name. In the left navigation pane, choose .
In the Actions column of the target node pool, click
 . Then, select Enable Managed Node for a standard node pool or Configure Managed Node for a managed node pool. Set the Configure Managed Node Pool mode to Custom Node Management and select the severity levels of CVE vulnerabilities that you want to automatically patch.
. Then, select Enable Managed Node for a standard node pool or Configure Managed Node for a managed node pool. Set the Configure Managed Node Pool mode to Custom Node Management and select the severity levels of CVE vulnerabilities that you want to automatically patch.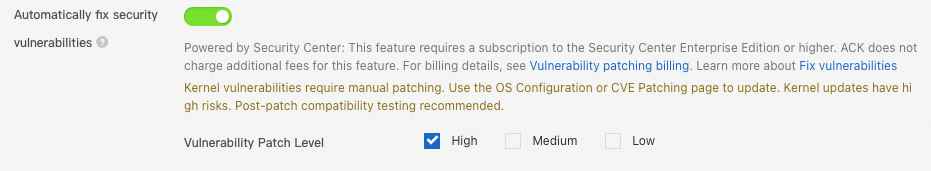
After a security vulnerability is found in the Linux kernel software, you usually need to upgrade the kernel package and restart the node. Due to the high stability risks involved in such operations, ACK skips patching kernel security vulnerabilities by default. We recommend that you handle these vulnerabilities manually by changing the operating system or by following the steps in Manually patch OS CVE vulnerabilities.
If you still need to automatically patch kernel vulnerabilities, submit a ticket to request this change.
Manually patch OS CVE vulnerabilities
You can also manually patch CVE vulnerabilities.
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the cluster to manage and click its name. In the left navigation pane, choose .
On the Node Pools page, find the node pool that you want to manage. In the Actions column, click
 and select CVE Patching (OS).
and select CVE Patching (OS).In the Vulnerabilities area, select the vulnerabilities that you want to patch. In the Instances area, select the instances that you want to patch. Configure the Batch Repair Policy and click Start Repair. Then, follow the on-screen instructions to complete the operation.
The batch patching policy includes the following parameters:
Maximum Number of Nodes to Repair per Batch: Nodes are patched for CVE vulnerabilities in batches. The number of nodes in each batch increases sequentially, such as 1, 2, 4, and 8, until the specified maximum number of concurrent nodes is reached. After the maximum number is reached, each subsequent batch patches the maximum number of nodes. For example, if you set the maximum number of concurrent nodes to 4, one node is patched in the first batch, two nodes are patched in the second batch, and four nodes are patched in the third and subsequent batches.
Dry Run Mode: If you enable this mode, ACK simulates the patching process and generates a report. The CVE vulnerabilities are not actually patched.
What to do next
After a patching Job starts, you can control its progress by clicking Pause, Resume, or Cancel.