Alibaba Cloud Container Service for Kubernetes (ACK) clusters use security groups to restrict network traffic between control plane nodes and worker nodes. Security groups also control traffic between nodes, Virtual Private Cloud (VPC) resources, and external IP addresses. When you create a cluster or a node pool, a security group is automatically assigned. You can also associate an existing security group. If you do so, the system does not configure additional access rules for it. You must then manage and converge the security group rules.
You can add security group rules to allow or deny access from the public or private network to the Elastic Compute Service (ECS) instances in the security group. For more information, see Security group overview and Add a security group rule.
Recommended inbound and outbound rules for cluster security groups
Basic security groups
Inbound
Cluster access rule | Protocol | Port | Authorization object |
Recommended scope | ICMP | -1/-1 (all ports) | 0.0.0.0/0 |
All Protocols | -1/-1 (all ports) |
| |
Minimum scope | All Protocols | 53/53 (DNS) |
|
ICMP | -1/-1 (all ports) | ||
TCP |
| ||
TCP | 9082 | The port used by the Poseidon component. This configuration is not required if the component is not used. | |
All protocols | All ports on which applications or components expect to be accessed | All source addresses or source security groups from which applications or components expect to be accessed |
Outbound
Cluster access rule | Protocol | Port | Authorization object |
Recommended scope | All protocols | -1/-1 (all ports) | 0.0.0.0/0 |
Minimum scope | All protocols | -1/-1 (all ports) | 100.64.0.0/10 (CIDR block for Alibaba Cloud services) |
All protocols | 53/53 (DNS) |
| |
TCP |
| ||
All protocols | All ports that applications or components expect to access | All destination addresses or destination security groups that applications or components expect to access |
Advanced security groups
Inbound
Cluster access rule | Protocol | Port | Authorization object |
Recommended scope | ICMP | -1/-1 (all ports) | 0.0.0.0/0 |
All protocols | -1/-1 (all ports) |
| |
Minimum scope | All protocols | 53/53 (DNS) |
|
ICMP | -1/-1 (all ports) | ||
TCP |
| ||
TCP | 9082 | The port used by the Poseidon component. This configuration is not required if the component is not used. | |
All Protocols | All ports on which applications or components expect to be accessed | All source addresses or source security groups from which applications or components expect to be accessed |
Outbound
Cluster access rule | Protocol | Port | Authorization object |
Recommended scope | All protocols | -1/-1 (all ports) | 0.0.0.0/0 |
Minimum scope | All protocols | -1/-1 (all ports) | 100.64.0.0/10 (CIDR block for Alibaba Cloud services) |
All protocols | 53/53 (DNS) |
| |
TCP |
| ||
All protocols | All ports that applications or components expect to access | All destination addresses or destination security groups that applications or components expect to access |
Disable deletion protection for a security group
To prevent the accidental deletion of security groups that are associated with a cluster, ACK enables deletion protection for all associated security groups. If you receive the following error message when you release a security group in the ECS console, it is because ACK enabled deletion protection for the security group.
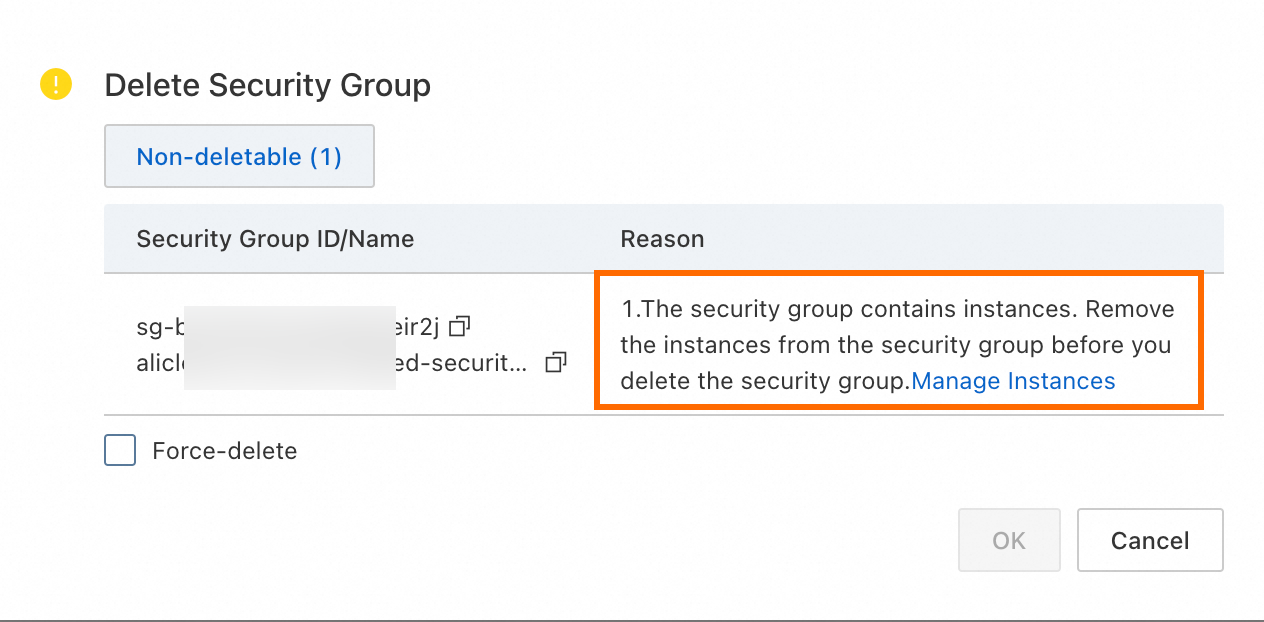
You cannot manually disable deletion protection for a security group in the console or by calling an API operation. ACK automatically disables deletion protection for a security group only after you delete all clusters that use that security group. To delete the security group, you must first identify and delete all associated clusters. The following steps describe how to find the security group associated with a cluster.
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, click the name of the destination cluster. Click the Basic Information tab to view the cluster's security group.
After you delete all clusters that use the security group, release the security group in the ECS console. If the release fails, submit a ticket to the Container Service team.
For more information about how to delete a security group, see Delete a security group.
References
For more information about best practices for network security, such as default allow or deny rules and namespace isolation, see Network security.
For more information about network planning for Kubernetes clusters, including planning for ECS IP addresses, Kubernetes pod IP addresses, and Service CIDR blocks, see Network planning for ACK managed clusters.