To meet cluster compliance requirements and improve cluster security, you can enable the security policy management feature. The security policy management feature provides security policy rules for Kubernetes container scenarios. These rules cover dimensions such as infrastructure (Infra), Kubernetes compliance specifications (Compliance), extensions based on PodSecurityPolicy (PSP) capabilities, and general policies (K8s-general). You can enable or customize security policies for container applications in the console. This helps you ensure that pod deployments and updates are secure and controllable.
Introduction to policy administration
PodSecurityPolicy (PSP) was deprecated in Kubernetes 1.21. In response, Container Service for Kubernetes (ACK) upgraded its original PSP-based policy management feature. ACK extended its capabilities using the Gatekeeper admission controller, which is based on Open Policy Agent (OPA) policies. These extensions include statistics on policy administration status, and log reporting and retrieval. ACK also provides a rich, built-in library of policy administration rules for a wider range of Kubernetes application scenarios. You can configure rules using a simple interface in the console. This lowers the barrier to entry for using policy administration features.
Prerequisites
The cluster version is 1.16 or later. To upgrade a cluster, see Manually upgrade an ACK cluster.
If you use a Resource Access Management (RAM) user to manage policies, make sure that the RAM user has the following permissions:
cs:DescribePolicies: Lists the policy administration rule libraries.cs:DescribePolicyDetails: Retrieves the details of a policy rule template.cs:DescribePolicyGovernanceInCluster: Retrieves the policy administration details of a cluster.cs:DescribePolicyInstances: Retrieves the list of policy instances that are deployed in a cluster.cs:DescribePolicyInstancesStatus: Retrieves the deployment status of instances for different policy types in a cluster.cs:DeployPolicyInstance: Deploys a policy rule instance in a specified cluster.cs:DeletePolicyInstance: Deletes a policy rule instance in a specified cluster.cs:ModifyPolicyInstance: Modifies a policy rule instance in a specified cluster.
For more information about how to create a custom RAM policy, see Use RAM to grant access permissions to clusters and cloud resources.
Comparison of security policy components
ACK provides two types of security policy components: managed and unmanaged. Only one type can be enabled in a cluster at a time. The following table compares the two types.
Item | Managed | Unmanaged |
Deployment mode | Control plane-hosted: The component is deployed on the cluster's control plane and is fully managed by ACK. | Data plane-hosted: The component is deployed in the cluster as a workload. By default, it is installed in the kube-system namespace and consumes pod resources on worker nodes. |
Applicable clusters | ACK clusters in Auto Mode that run Kubernetes 1.30 or later | ACK managed clusters and ACK dedicated clusters that run Kubernetes 1.16 or later |
Startup parameter configuration | The startup parameters of the component are set to default values by the system and cannot be customized. | You can customize the startup parameters of the component. |
Core component installation |
On the Add-ons page, a |
|
Policy log collection | Logs are sent to a specified Simple Log Service (SLS) project. For more information, see Collect logs from control plane components in ACK managed clusters. | A log collection component is installed in the cluster to collect logs and send them to a specified SLS project. |
Policy rule library | All policies in Predefined security policies of ACK |
|
Notes
This feature applies only to Linux nodes.
Custom policy rules are not supported. All rules are from the built-in rule library of ACK.
Step 1: Install or upgrade the security policy management component
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the cluster you want and click its name. In the left navigation pane, choose .
On the Policy Governance page, install or upgrade the component as prompted.
When you enable the security policy management feature, you must install the following components. These components are free of charge but consume pod resources.
gatekeeper: a Kubernetes policy admission controller that is based on the OPA policy engine. It helps you manage and apply OPA policies in your cluster to implement features such as namespace tag management.
NoteOnly the gatekeeper component that is provided by ACK is supported. If you have installed the gatekeeper component from other sources, you must uninstall it and then reinstall the one that is provided by ACK. For more information about the release notes for the gatekeeper component, see gatekeeper.
Log collection component: collects and retrieves block or alert events that violate policy constraints.
policy-template-controller: a Kubernetes controller developed based on Alibaba Cloud policy templates. It helps you manage policy instances that are deployed from different policy templates and the overall administration status of the cluster.
Step 2: Use the security policy management feature
Entry point
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the cluster you want and click its name. In the left navigation pane, choose .
On the Policy Governance page, install or upgrade the component as prompted, if required. Then, perform the following operations as needed.
View the current execution status of security policies in the cluster
Click the Overview tab to view the policy administration status of the cluster.
Policy enablement overview: This section displays the total number and the number of enabled high-risk and medium-risk mitigation policies. It also provides a list of recommended policies to enable.
Statistics on block and alert events over the last 7 days.
The table of policy implementation records for the last 7 days displays the 100 most recent Block or alert logs from the last 7 days by default. If you want to view more audit logs, you can click the
 icon next to Actions within Last 7 Days, and then click the Simple Log Service link in the pop-up window to view all logs in the specified logstore in the Simple Log Service (SLS) console.
icon next to Actions within Last 7 Days, and then click the Simple Log Service link in the pop-up window to view all logs in the specified logstore in the Simple Log Service (SLS) console.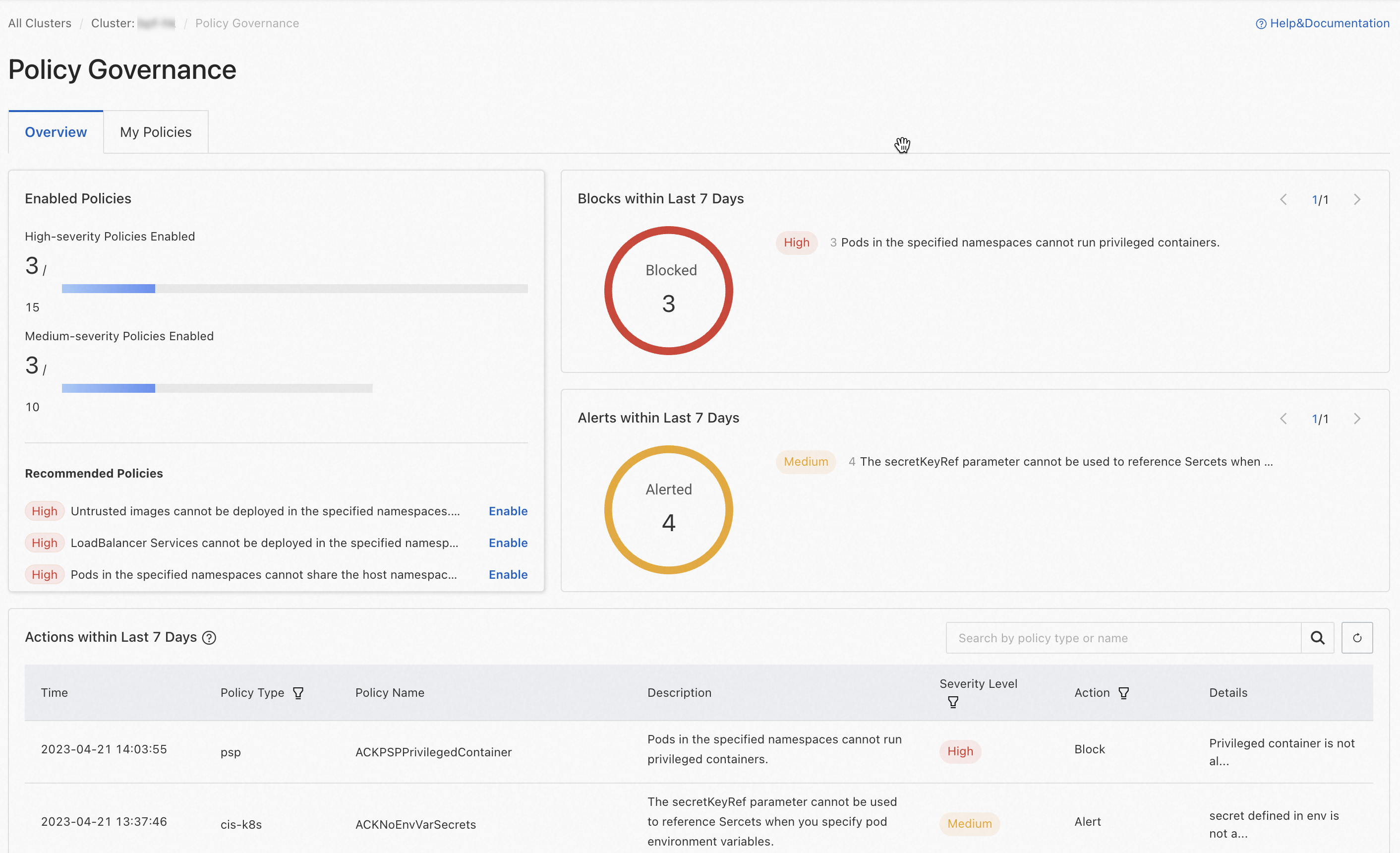
Create and manage security policy instances
Click the My Policies tab. Then, click Create Policy Instance and configure the parameters in the Create Policy Instance dialog box.
Configuration Item | Description |
Policy Type | Select a policy type. The following major types are available:
For more information, see Predefined security policies of ACK. |
Policy Name | Based on the selected policy type, select the name of the policy template to deploy from the drop-down list. |
Action |
|
Applicable Scope | Select the namespaces in the cluster where the policy instance is enforced. |
Parameters |
|
View the list of security policies and deployed security policy instances in the cluster
Click the My Policies tab to view the names of all deployable policies in the cluster.
You can filter the policies that are displayed in the upper-right corner of the list. The names of enabled policies are displayed first. The number of policy instances indicates how many instances of the policy are deployed in the cluster.
If the number of policy instances is empty, the policy is not yet deployed in the cluster. In the Actions column, click Enable to configure parameters and deploy the corresponding policy instance.
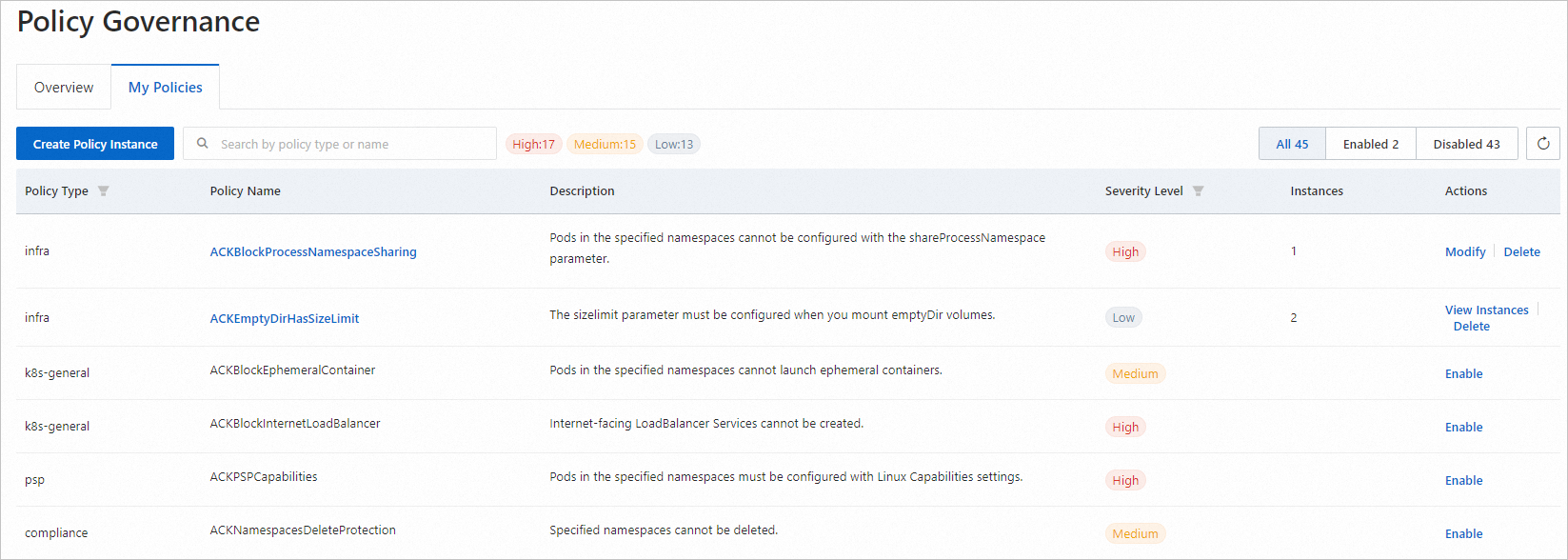
Click Modify in the Actions column to modify the configuration of a policy instance.
If more than one instance of a policy is deployed in the cluster, click View Instances in the Actions column. Then, click Modify to modify the relevant configuration.
Click Delete in the Actions column to delete all instances of the policy deployed in the cluster.
For more information about policy descriptions and sample templates, see Predefined security policies of ACK.
Related operations: Enable deletion protection for a namespace or service
After you enable the security policy management feature as described in Step 1: Install or upgrade the security policy management component, you can also enable deletion protection for namespaces or services that involve critical business or sensitive data. This helps prevent maintenance costs caused by accidental deletion. After you enable this feature, the corresponding resource can be deleted only after you manually disable its deletion protection.
The following procedure shows how to enable deletion protection for an existing namespace. The steps for other operations are similar. You can go to the corresponding page in the console and complete the configuration as prompted.
Enable deletion protection for an existing namespace
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the cluster you want and click its name. In the left-side navigation pane, click Namespaces and Quotas.
In the namespace list, find the namespace that you want to manage. In the Actions column, click Edit. In the dialog box that appears, enable deletion protection as prompted.
Enable deletion protection for an existing service
Log on to the ACK console. In the left navigation pane, click Clusters.
On the Clusters page, find the cluster you want and click its name. In the left navigation pane, choose .
In the service list, find the service that you want to manage. In the Actions column, click the
 icon and then click Enable Deletion Protection. In the dialog box that appears, enable deletion protection as prompted.
icon and then click Enable Deletion Protection. In the dialog box that appears, enable deletion protection as prompted.
References
You can configure the inspection feature to scan for security risks in the workload configurations of your cluster. For more information, see Configure inspection to check cluster workloads.