Security Center provides a security operations dashboard for your cloud assets. The dashboard helps you understand the security status, assessment results, and real-time monitoring alerts for your assets.
Data overview
The Overview page displays security data for your cloud assets from data centers in China and globally across multiple dimensions. These dimensions include security score, security risks, security operation trends, and an overview of asset information. The page also provides quick access to upgrade, renew, and expand your services for unified security management.
You can view the following information on the Overview page in the Security Center console:
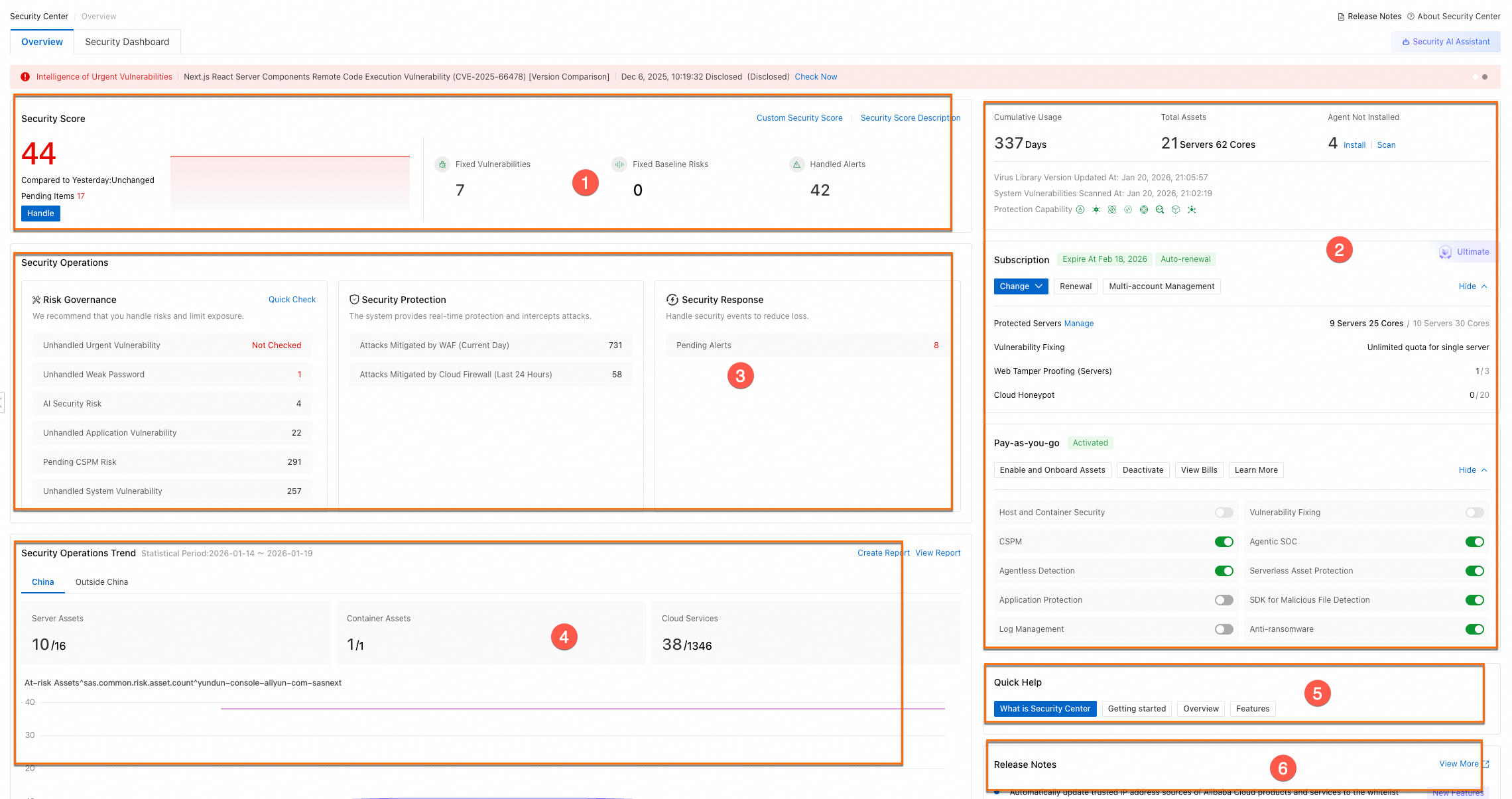
Module Name | Description | Supported operations | |
Security Score (① in the figure) | This module displays the security score of your assets and security management statistics. This includes statistics on fixed vulnerabilities, resolved baseline risks, and handled alerts. |
| |
Overview of instance information (② in the figure) | This module displays the edition, configuration details, expiration time, and protected asset statistics for your Security Center subscription. It also shows the status of your pay-as-you-go services. Note The user interface (UI) may vary depending on your Security Center edition. |
| |
Security Operations (③ in the figure) | Risk Governance | This module provides statistics on the security risks of your cloud assets. These risks include vulnerabilities that require immediate attention, application and system vulnerabilities, weak passwords, baseline risks for cloud products and hosts, and API security risks. It also highlights data security risks, improperly connected security products, key feature configurations, and reminders for expiring products. Note The supported detection features vary by Security Center edition. |
Note Handle alerts promptly by referring to the relevant Security Center documentation. |
Security Protection | This module displays attack behaviors that are intercepted in real time. Examples include the number of scrubbed DDoS attacks, attacks blocked by Web Application Firewall, attacks blocked by Cloud Firewall, host defenses provided by Security Center, and security risks intercepted by ID Verification. | Click the statistics in each area, select a specific risk item, and click Handle Now. | |
Security Response | This module displays risks that are related to security alerts. We recommend that you handle these alerts promptly to minimize potential impact. These alerts include unhandled urgent, reminder, and suspicious alert events. | Click the statistics in the Pending Alerts area, select a specific risk item, and click Handle Now. For more information, see Evaluate and handle security alerts. | |
Security Operations Trend (④ in the figure) | This module displays trends in your security operations. These trends include changes in the number of host assets, container assets, total cloud products, and associated risky assets. | In the upper-right corner of the Security operation trends section, click Create Report or View Report to view details on the Security Report page. For more information, see Security report. | |
Quick Help (⑤ in the figure) | This module provides quick links to key information and resources related to Security Center. | Related information includes: | |
Release Notes (⑥ in the figure) | This module displays recent feature optimizations, new feature releases, and information about newly available features. | Click View More to view more product update information on the Product Updates page. | |
Security score
The Security Center security score is a health index from 0 to 100 that reflects the security posture of your cloud assets. A comprehensive evaluation mechanism, deployed in data centers in China and other regions worldwide, dynamically calculates the score by deducting points for security issues such as alert events and configuration defects. A higher score indicates fewer security risks and a higher degree of remediation.
Improve your security score
The risk levels for cloud assets are categorized as Important (below 69), Medium (70–84), At Risk (85–94), and Secure (95–100). To improve the security of your cloud assets, handle risk alerts promptly to increase your security score.
In the Security Score module, click the security score value.
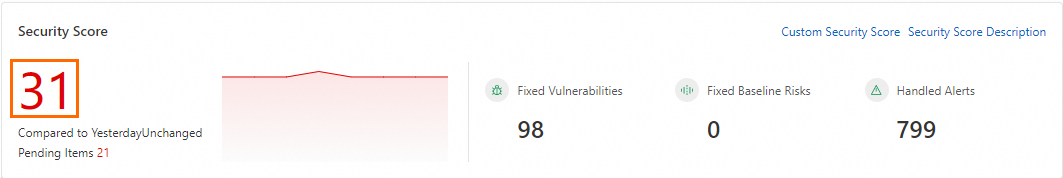
In the Security Score Details panel, view the specific deduction items. Click Handle Now to the right of a deduction item. You are redirected to the risk handling page for that item. View the risk list and fix the risks based on the provided details or hardening suggestions.
NoteThe supported detection features vary by Security Center edition.
The Security Score Details panel consolidates all pending items from Risk Governance, Security Response, and Security Protection. You can also refer to the category guidance in the Data Overview security operations module and the priority for handling events in the security score to handle related risk alerts promptly.
Customize security score
Security Center sets a default deduction value for each configuration item. You can customize the security score values based on your business priorities.
In the upper-right corner of the Security Score module, click Custom Security Score.
In the Custom Security Score panel, set the deduction value for each configuration item, and then click OK.
The deduction modules for the security score include Core Feature Configurations, Unhandled Alerts, Unfixed Vulnerabilities, and more. The deduction threshold for each module ranges from 0 to 100, and the sum of all module thresholds cannot exceed 100.
Deduction modules contain different deduction items. The deduction value for an item ranges from 0 to the module's deduction threshold. The sum of deduction values for all items within a module cannot exceed the module's threshold.
NoteIf you have previously modified and saved your security score settings, the Custom Security Score panel displays the Restore to Default Settings option. Click it to restore the deduction values to the system defaults.
FAQ
What is the priority for handling events in the security score?
The following table lists the priority for handling events in the security score. A smaller number indicates a higher priority, with 1 being the highest.
Priority | Event |
1 | Configured or enabled key features, including the following:
|
2 | Handled AccessKey pair leak events. |
3 | Handled cloud platform configuration risks. |
4 | Fixed baseline check issues. |
5 | Handled security alerts. |
6 | Fixed vulnerabilities. |
What is the relationship between changing the vulnerability attention level and improving the security score?
If you primarily focus on fixing important and medium-risk vulnerabilities and want to ignore low-risk ones, follow these steps. The security score will no longer include low-risk vulnerabilities in its calculation.
On the Risk Governance > Vulnerabilities page, click Vulnerability Settings in the upper-right corner. In the Vulnerability Settings panel, set the Vulnerability Scan Level. For more information, see Scan for vulnerabilities.
What is the relationship between changing the baseline attention level and improving the security score?
If you primarily focus on fixing high-risk and medium-risk baselines and want to ignore low-risk ones, follow these steps. The security score will no longer include low-risk baseline risks in its calculation.
On the page, click Policy Management in the upper-right corner. On the tab, select the Baseline Check Level. For more information, see Baseline check.
 icon and click Scale Out to purchase more anti-ransomware storage or log storage.
icon and click Scale Out to purchase more anti-ransomware storage or log storage. icon to quickly enable or disable the related service. For more information about the services, see:
icon to quickly enable or disable the related service. For more information about the services, see: