MaxCompute is a multi-tenant big data processing platform that supports project-based security configurations to meet tenants' requirements for data security. Project owners can customize their external account support and authentication models to protect their project data.
Typically, MaxCompute and DataWorks are used together for data protection configuration. In this scenario, the data security solution is as follows:
Method 1:
The data protection mechanism is also known as project protection. You can enable this feature in the MaxCompute console to disable exporting data from the server end.
set ProjectProtection=true
--Sets ProjectProtection to allow data import and prohibit data export.
--The default value of ProjectProtection is false.Method 2:
You can use DataWorks to analyze data, and download the analysis result displayed on the IDE. In this case, choose Project Management > Project Configuration and enable Select Result Can Be Downloaded.
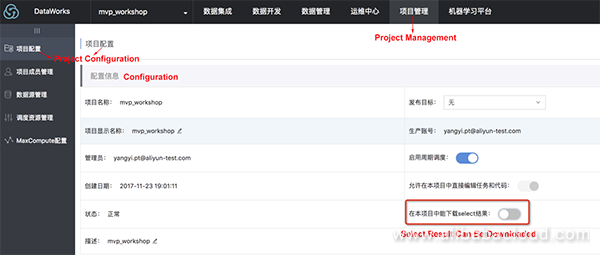
Then, you cannot click Download to download the data on the query result page of DataWorks.
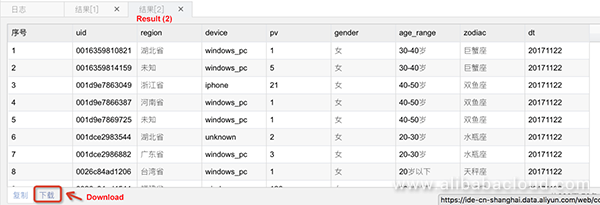
Assume that a user applies for permissions to export a table containing your project data after you set ProjectProtection to true, and you have confirmed that the table does not contain any sensitive data. To meet the user's service requirement, you can use either of the following data export methods that MaxCompute offers:
Method 1:
Configure an exception policy as a project owner to specify exceptions for protected project data. The configuration is as follows (performed on the MaxCompute console):
SET ProjectProtection=true WITH EXCEPTION <policyFile>Exception policy-based data protection differs from policy-based authorization, even though they use the same syntax. An exception policy describes an exception for project protection. That is, the ProjectProtection settings do not take effect for access that matches the exception policy.
{
"Version": "1",
"Statement":
[{
"Effect":"Allow",
"Principal":"ALIYUN$Alice@aliyun.com",
"Action":["odps:Select"],
"Resource":"acs:odps:*:projects/alipay/tables/table_test",
"Condition":{
"StringEquals": {
"odps:TaskType":["DT", "SQL"]
}
}
}]
}ProjectProtection controls the direction of data flows but not data access. Data access is a prerequisite for controlling the data flow direction.
In addition, you can run the following statement to verify the exception policy settings:
show grants [for <username>] [on type <objectType>]Method 2:
Set a trusted project. If project protection is enabled for your project and your project imports data from another project, you can then specify that project as a trusted project. Importing data to the trusted project is not considered as a violation of the ProjectProtection rule. Run the following commands in the MaxCompute console:
list trustedprojects;
--Displays all trusted projects.
add trustedproject <projectname>;
--Adds a trusted project.
remove trustedproject <projectname>;
--Removes a trusted project.MaxCompute supports project-based IP whitelist control.
setproject odps.security.ip.whitelist=101.132.236.134,100.116.0.0/16,101.132.236.134-101.132.236.144;IP addresses in an IP whitelist can be in the following formats:
For more information, see IP whitelist control.
The policy mechanism of MaxCompute allows you to control a user or role to access specific resources (such as tables and UDFs) using a certain IP address.
Policy example:
{
"Version": "1",
"Statement":
[{
"Effect":"Allow",
"Principal":"ALIYUN$alice@aliyun.com",
"Action":["odps:CreateTable","odps:CreateInstance","odps:List"],
"Resource":"acs:odps:*:projects/prj1",
"Condition":{
"DateLessThan": {
"acs:CurrentTime":"2013-11-11T23:59:59Z"
},
"IpAddress": {
"acs:SourceIp":"10.32.180.0/23"
}
}
},
{
"Effect":"Deny",
"Principal":"ALIYUN$alice@aliyun.com",
"Action":"odps:Drop",
"Resource":"acs:odps:*:projects/prj1/tables/*"
}]
}The preceding policy authorizes the alice@aliyun.com user to use the IP address 10.32.180.0/23 to access the prj1 project only before 23:59:59 of November 11, 2013 (Beijing time). The user can only perform the CreateInstance, CreateTable, and List actions. The user cannot delete any tables in the project.
Data Security Guard is a DataWorks data security module that provides functions including data masking and security audit.
Sensitive data displayed on the DataWorks UI is masked using asterisks (*).
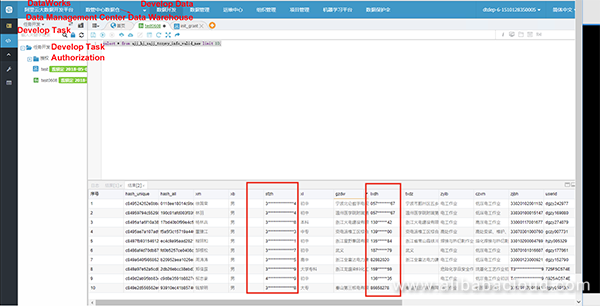
Note: The data masking function of Data Security Guard does not take effect for data downloaded using Tunnel commands through the console.
The label-based security mechanism (LabelSecurity) of a project is disabled by default and can be enabled by the project owner if needed.
Scenario
The project table user_profile contains the following sensitive data in 5 of its 100 columns: id_card, credit_card, mobile, user_addr, and birthday. The current DAC mechanism allows all users to perform the Select action on this table. To prevent all users except the administrator from accessing the sensitive data in these five columns, the project owner performs the following configurations:
set LabelSecurity=true;
--Enables LabelSecurity.
set label 2 to table user_profile(mobile, user_addr, birthday);
--Sets the sensitivity levels of the mobile, user_addr, and birthday columns of the user_profile table to 2.
set label 3 to table user_profile(id_card, credit_card);
--Sets the sensitivity levels of the id_card and credit_card columns of the user_profile table to 3.Based on service requirements, Alice, who is involved in this project, needs to access data in the mobile column of the user_profile table in a week. As the project owner, you can perform the following configurations:
GRANT LABEL 2 ON TABLE user_profile TO USER alice WITH EXP 7;For more information about column-based access control, visit https://www.alibabacloud.com/help/doc-detail/34604.htm
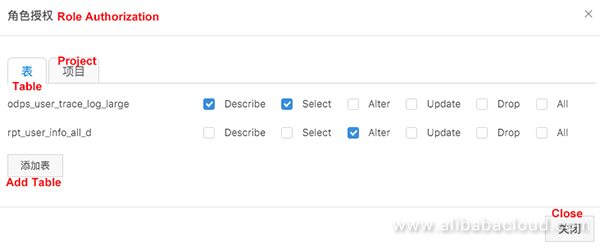
If predefined DataWorks roles such as data developers, O&M engineers, and administrators cannot meet your customization requirements, you can use ACL to create roles such as data analysts and ETL developers to adapt to your service logic. You can use role policies to perform refined role management; for example, grant these roles access permissions to tables with names starting with ods_, grant permissions with conditions, or grant Deny permissions.
Method 1:
The policy code is as follows:
get policy --Reads the policy of the project.
put policy <policyFile> --Configures (overwrites) a project policy.
get policy on role <roleName> --Reads the policy for a project role.
put policy <policyFile> on role <roleName> --Configures (overwrites) a policy for the project role.Method 2:
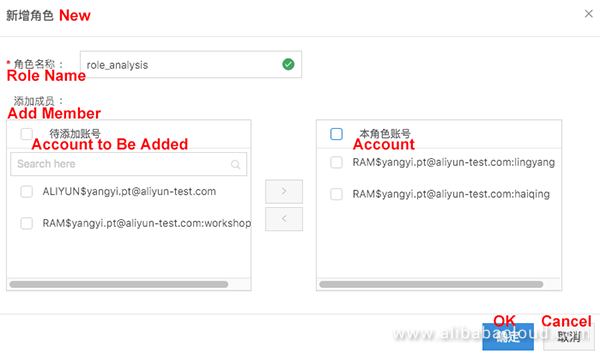
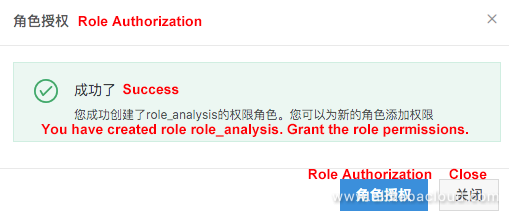
Log on to DataWorks and choose Project Management > MaxCompute Configuration > User-defined Role.
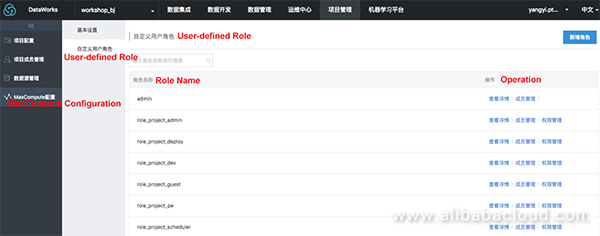
Perform the following operations:
MaxCompute JDBC 2.4 offers enhanced data security. JDBC packages are available at https://github.com/aliyun/aliyun-odps-jdbc/releases
SET ProjectProtection=true
For more information, see chapter 1 "Prevent data from being downloaded locally."
setproject READ_TABLE_MAX_ROW=1000
Note: If you have enabled project protection and query data using JDBC of a version earlier than JDBC 2.4, an error will occur because no permissions are granted).
To learn more about Alibaba Cloud MaxCompute, visit www.alibabacloud.com/product/maxcompute

137 posts | 21 followers
FollowAlibaba Clouder - March 30, 2021
Alibaba Cloud New Products - August 20, 2020
Alibaba Cloud MaxCompute - August 27, 2020
Alibaba Cloud MaxCompute - January 22, 2021
Alibaba Clouder - July 10, 2020
Alibaba Clouder - June 26, 2018

137 posts | 21 followers
Follow Big Data Consulting for Data Technology Solution
Big Data Consulting for Data Technology Solution
Alibaba Cloud provides big data consulting services to help enterprises leverage advanced data technology.
Learn More MaxCompute
MaxCompute
Conduct large-scale data warehousing with MaxCompute
Learn More Big Data Consulting Services for Retail Solution
Big Data Consulting Services for Retail Solution
Alibaba Cloud experts provide retailers with a lightweight and customized big data consulting service to help you assess your big data maturity and plan your big data journey.
Learn More Hologres
Hologres
A real-time data warehouse for serving and analytics which is compatible with PostgreSQL.
Learn MoreMore Posts by Alibaba Cloud MaxCompute