By Victor Mak, Lead Solutions Architect from Alibaba Cloud Intelligence International Macau
The coronavirus outbreak forced unprecedented changes in work culture worldwide, and most people worked from home. From a company perspective, building a remote workspace become a new trend. However, security, employee satisfaction, and cost-efficiency become the main challenges:
Alibaba Cloud Elastic Desktop Services (EDS) is a product that allows quick and convenient creation and deployment as well as centralized management and O&M for desktop environments. The company can create a secure, high-performance, and cost-efficient cloud desktop quickly without making large hardware investments upfront. EDS is widely applied in fields, such as finance, design, video, and education, which have high requirements for secure data management and control and high-performance computing.
Some EDS benefits:
Secure and Reliable - Data is stored on the cloud, which reduces the risks of data leaks. Data access protocols are encrypted securely, and storage reliability is 99.9999999% (nine 9's).
On-Demand Deployment - You can deploy cloud desktops on-demand and access your cloud desktops anytime, anywhere, and from any EDS client.
Access Security - EDS uses Active Directory (AD) for secure account management. This allows access to the authentication systems of enterprises.
Support for GPUs - EDS supports high-performance display protocols, such as image design and modeling protocols, to meet video editing requirements.
Combine with Alibaba Cloud VPN and Identity as a Service (IDaaS), a cloud-based identity and access management service (IAM) covering comprehensive functions that enable user portal, user directory, flexible authentication, single sign-on, centralized authorization, and audit reporting to provide a secure remote workspace and extreme performance to employees to enjoy their work at any time at anywhere.
The section below describes how to build up a secure remote workspace based on Alibaba Cloud best practices step by step:
The following figure illustrates the architecture to build a secure workspace:
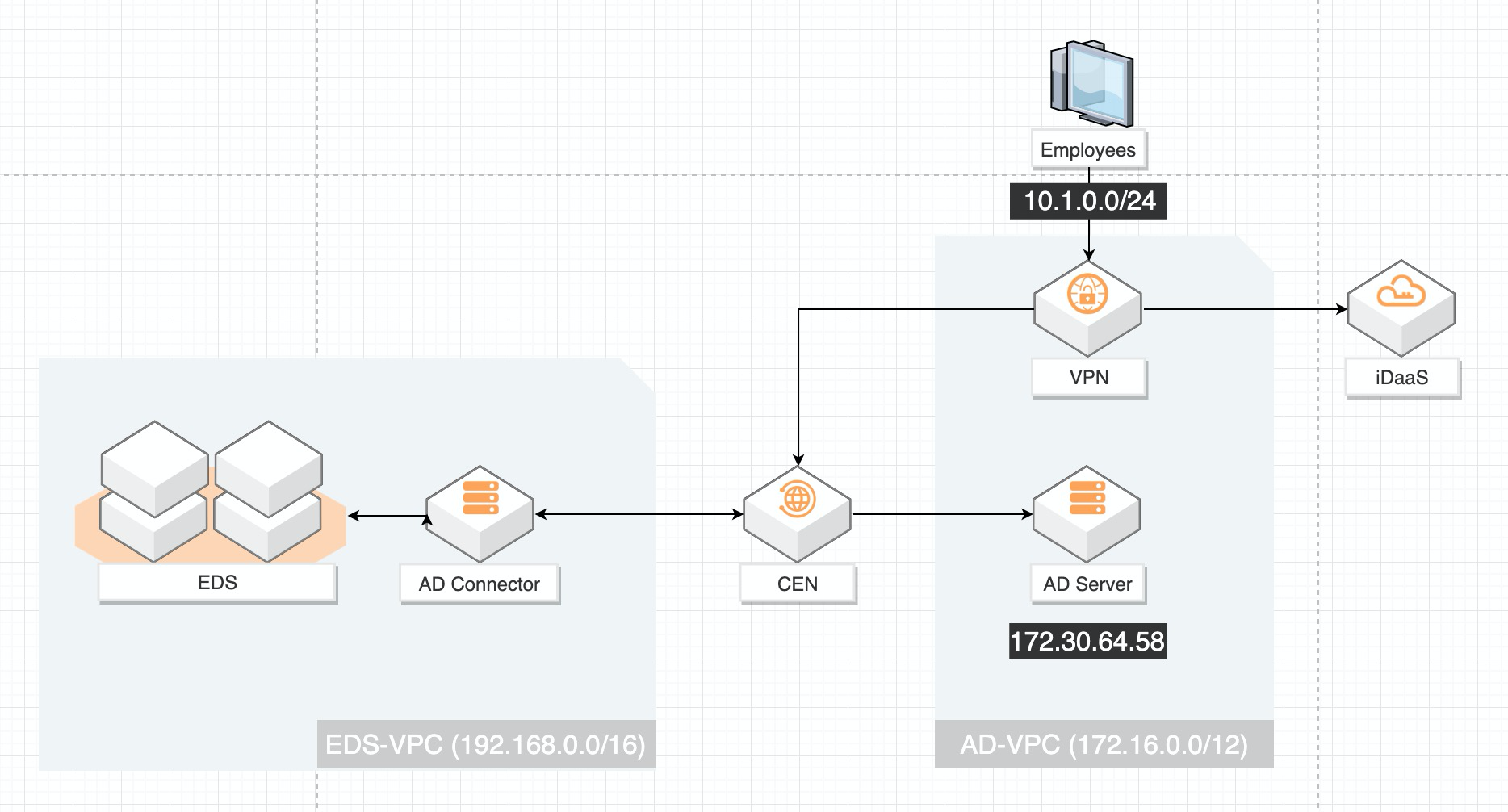
Before you begin, make sure of the following:
Since Elastic Desktop Service (EDS) needs to communicate with Active Directory Server via Cloud Enterprise Network (CEN), please follow the step below to create a CEN instance:
1. Log on to the CEN console
2. On the Instances page, click Create CEN Instance:
3. Click Create Transit Router, Select the Region where your Active Directory is located (e.g. Hong Kong Region), and fill in the Name for Transit Router:
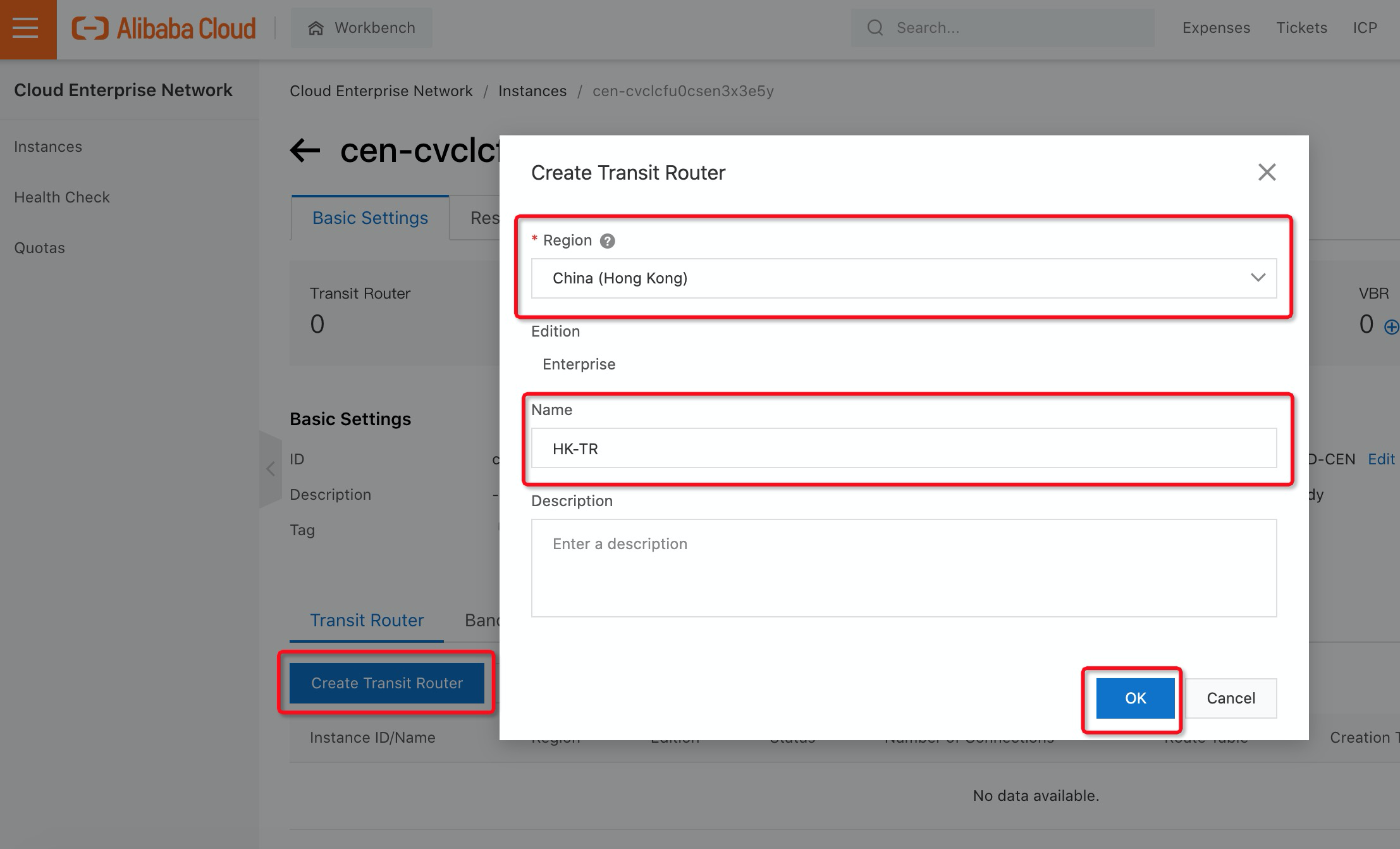
4. Once you have created the transit router, you need to add the VPC where your Active Directory is located into the transit router by clicking Create Connection:
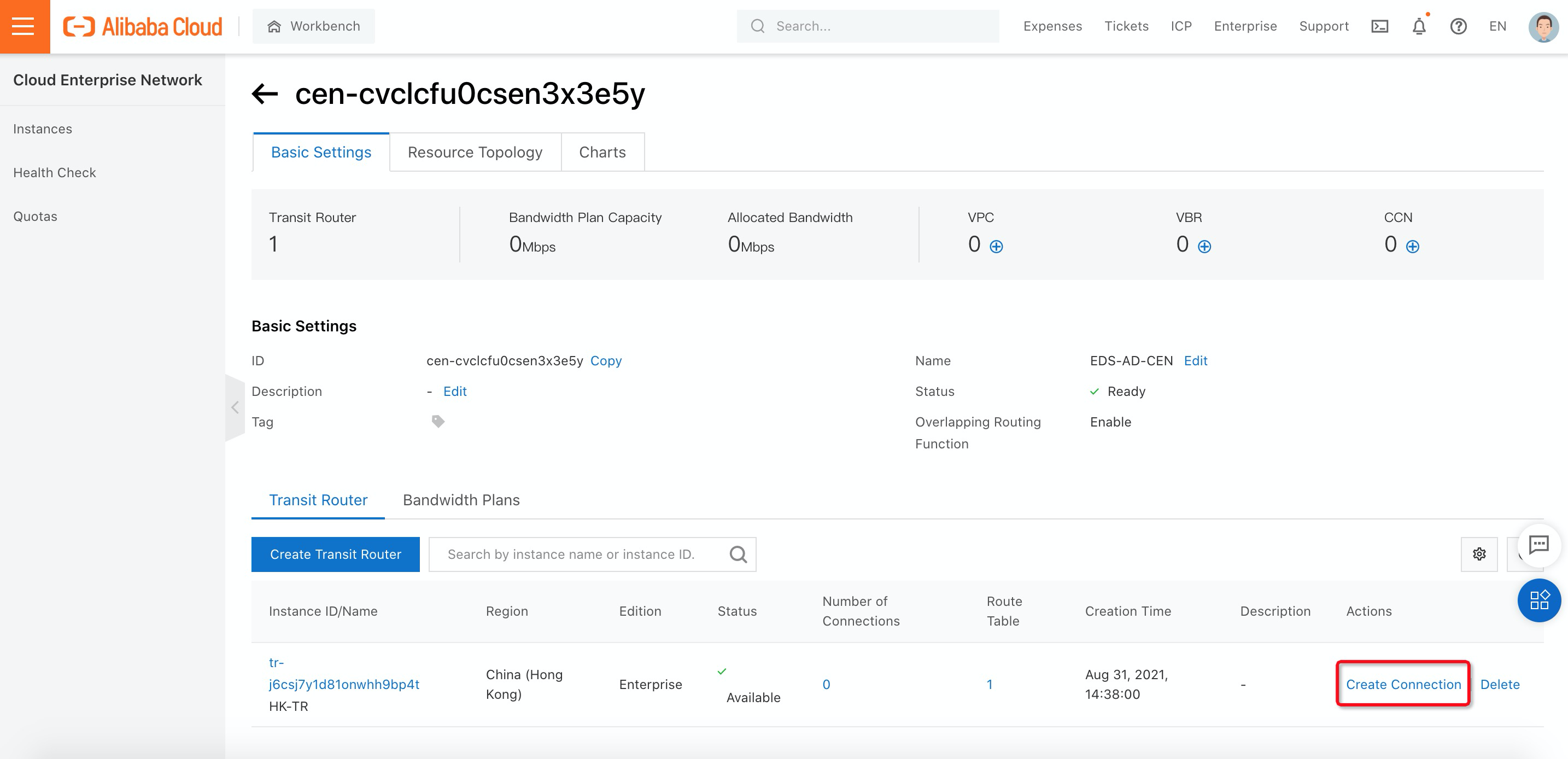
5. In the Network Type, select VPC and fill in corresponding information about where the VPC is located:
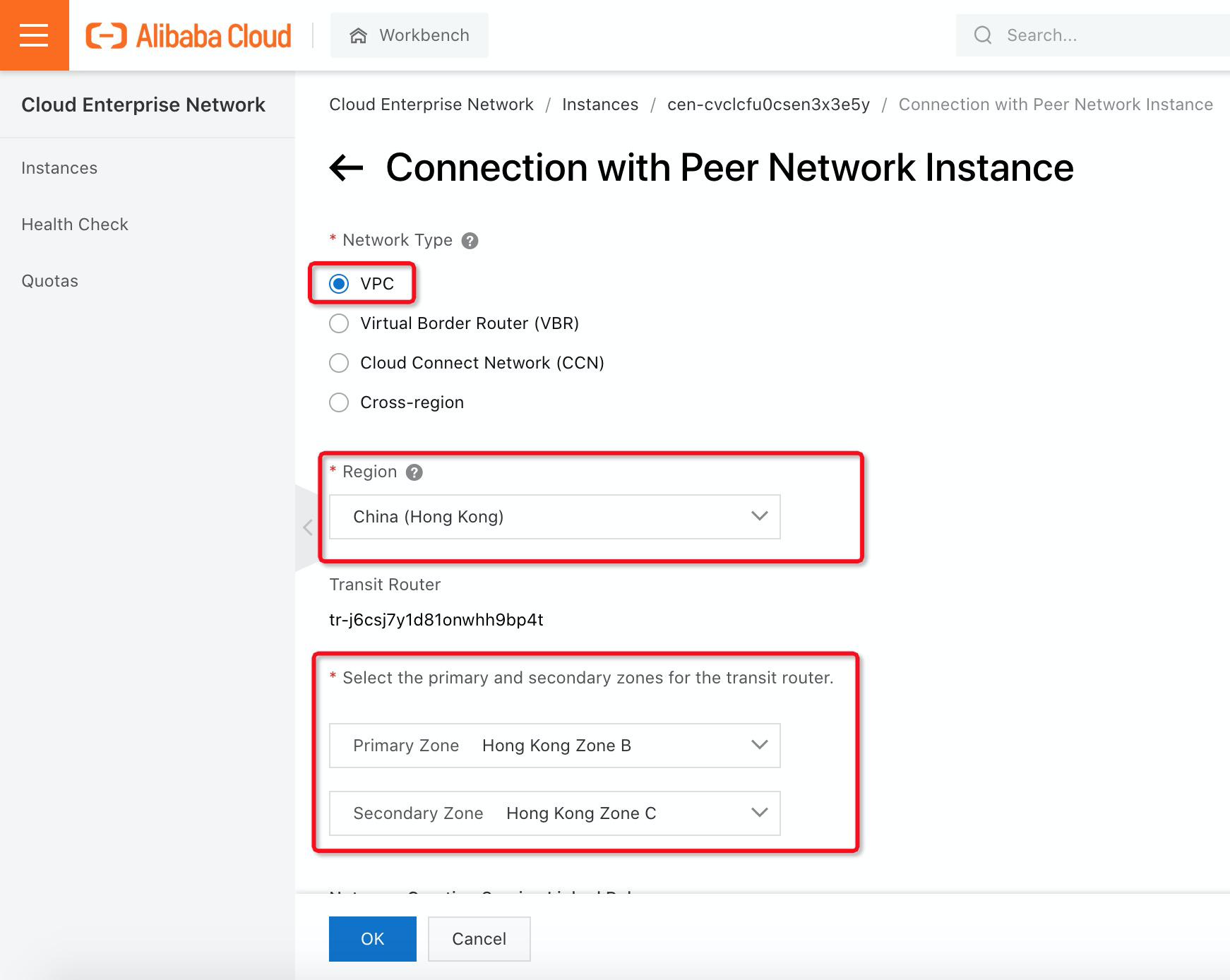
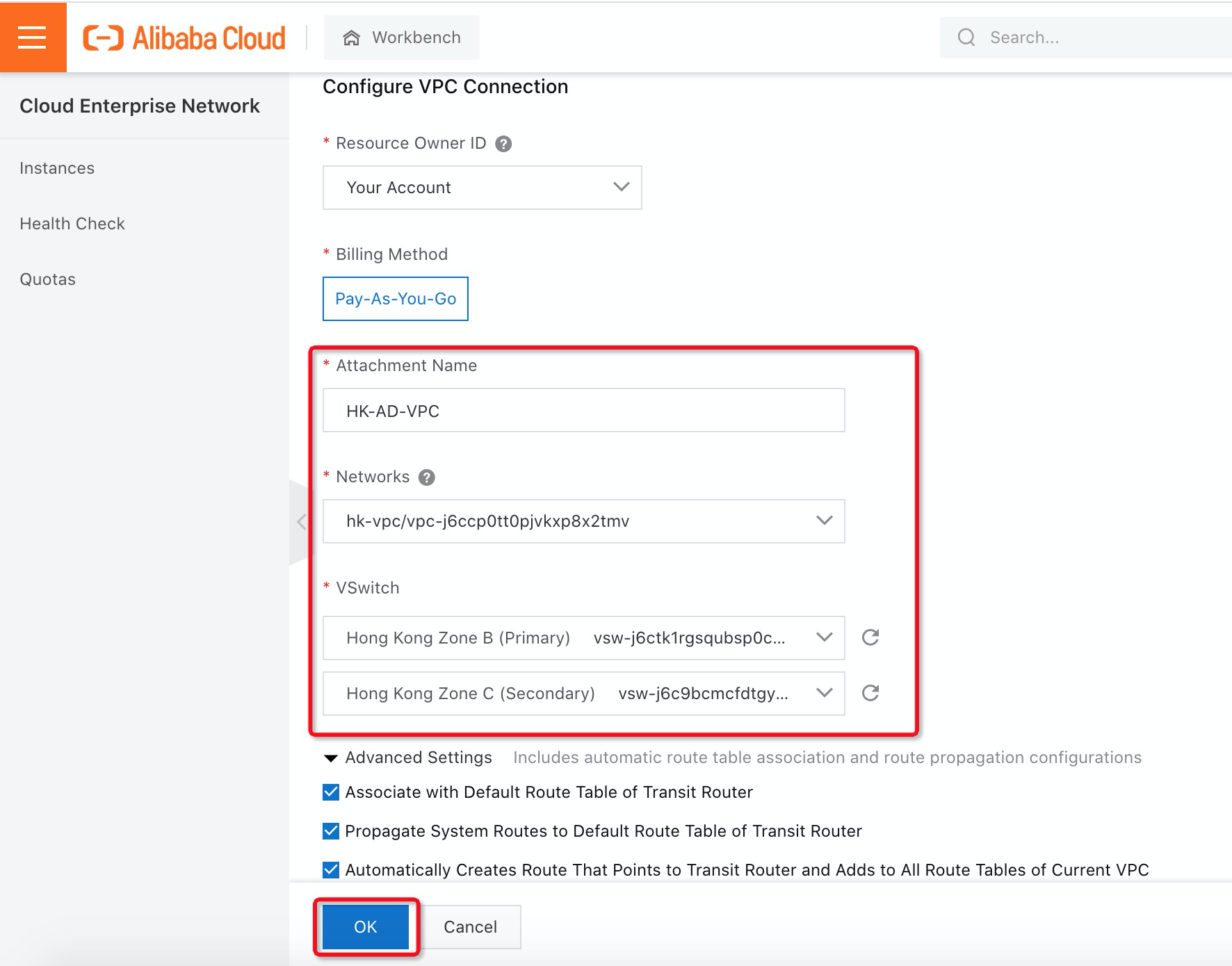
Before you can enable Active Directory (AD) integration in EDS, you need to create a workspace. A workspace is a collection of environment configurations of cloud desktops and includes settings, such as secure office networks, user account systems, and Internet access. Cloud desktops are deployed within workspaces. This topic describes the terms and features of workspaces. Please follow the steps below to create a workspace in EDS:
1. Log on to the EDS console
2. On the left-side navigation pane, click Overview. Then, on the Overview page, click Create Workspace:
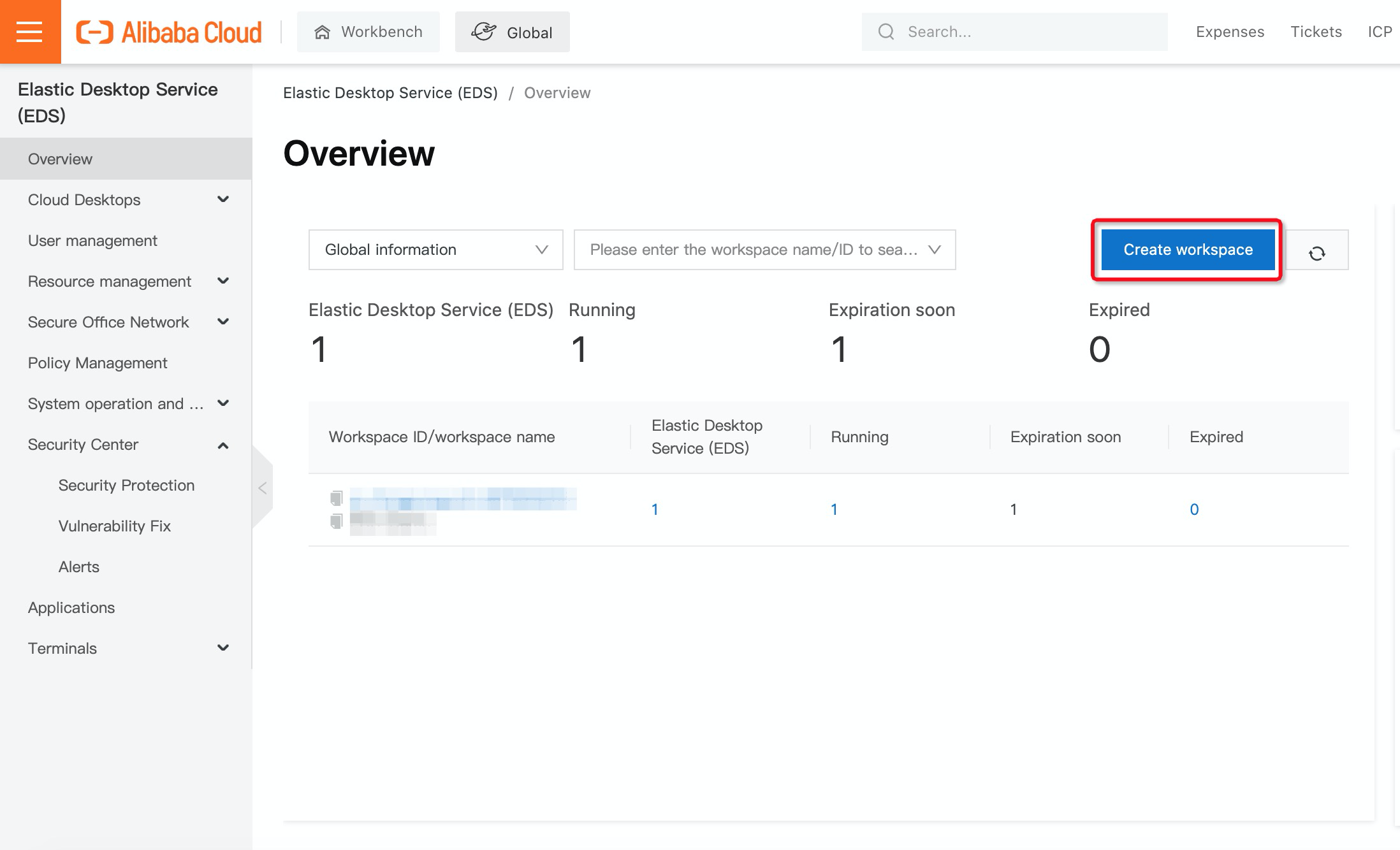
3. In the create workspace step, select a region, enter a workspace name, and specify the IPv4 CIDR block. To connect the workspace to the Active Directory Server, you need to select the Join cloud enterprise network you created above. Then, click Next: Configure Account System.
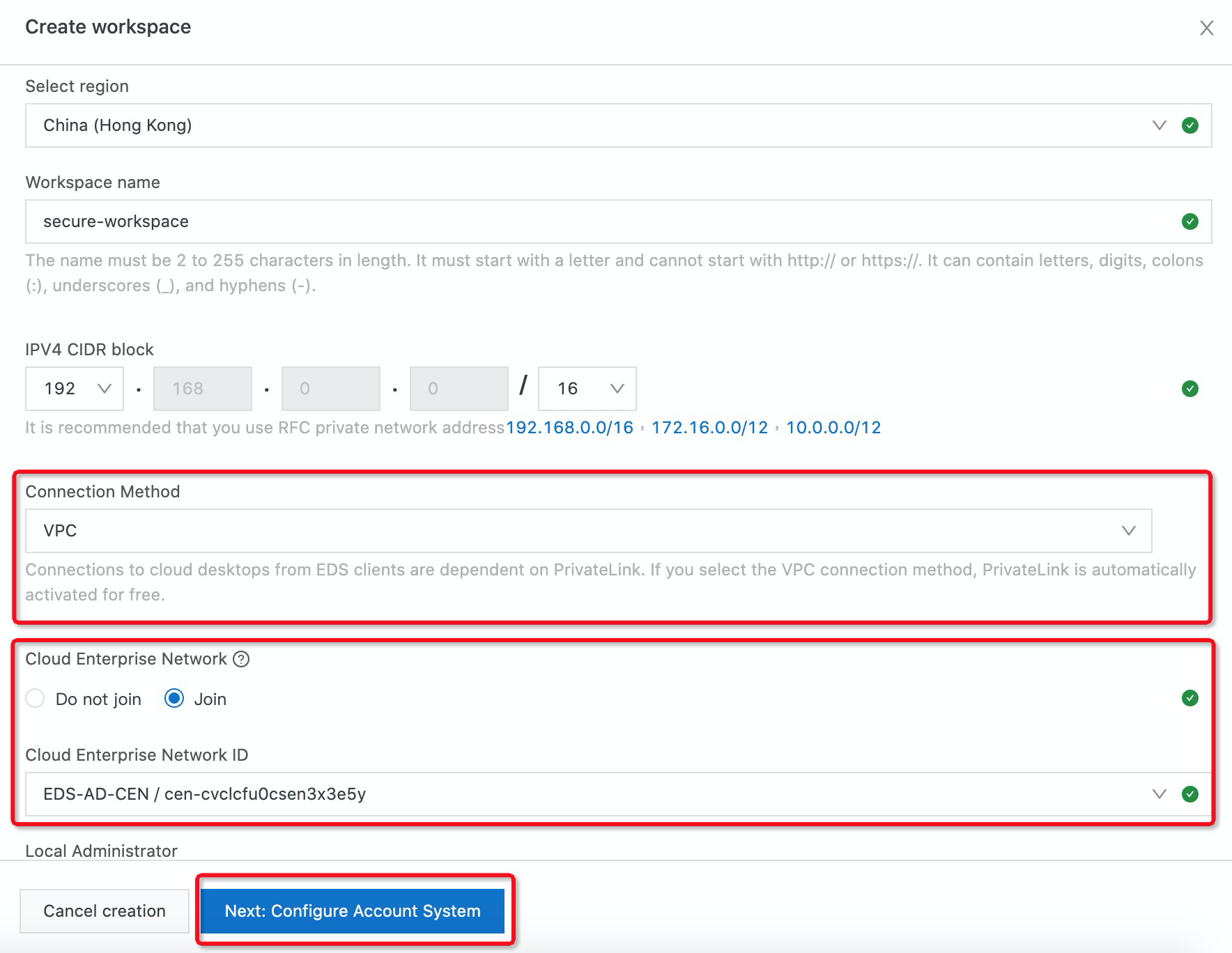
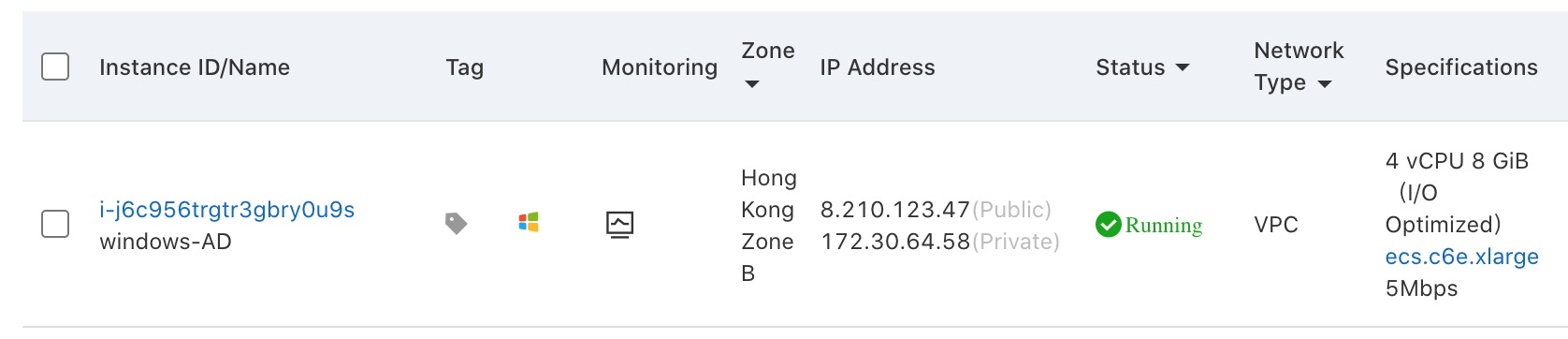
4. Select Enterprise AD account number, enter the Active Directory Server IP address in the DNS Address field, and add a Domain Name. (In this example, we used “alibabacloud.local”):
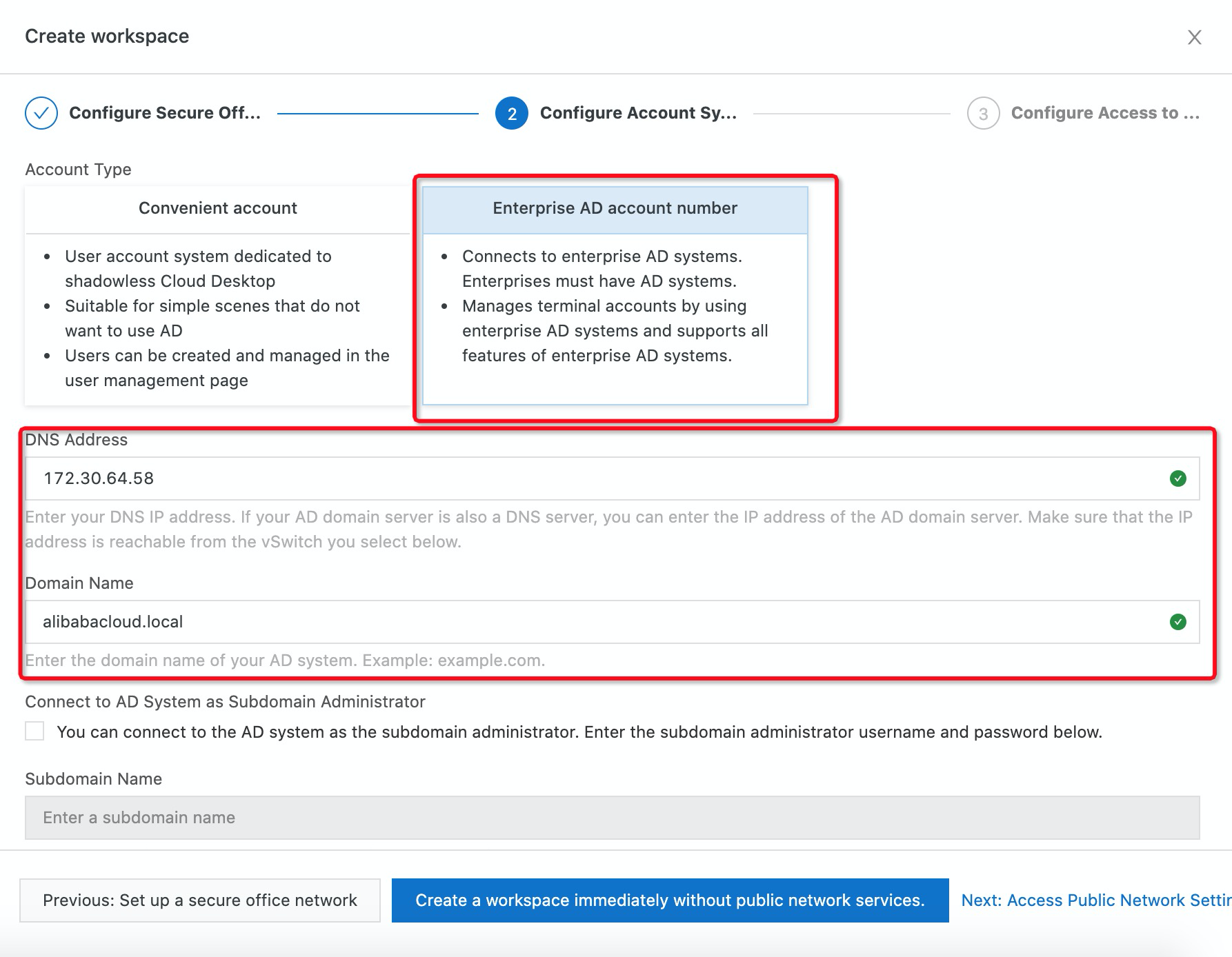
5. Enter the username and password of the domain administrator and click Next: Access Public Network Settings if you need to enable Internet access for those EDS resources. (Note: If you do not need to access the Internet, you can click Create a workspace immediately without public network services.)
6. Select Open public network access for desktop and specify the peak bandwidth value. Click Create workspace now:
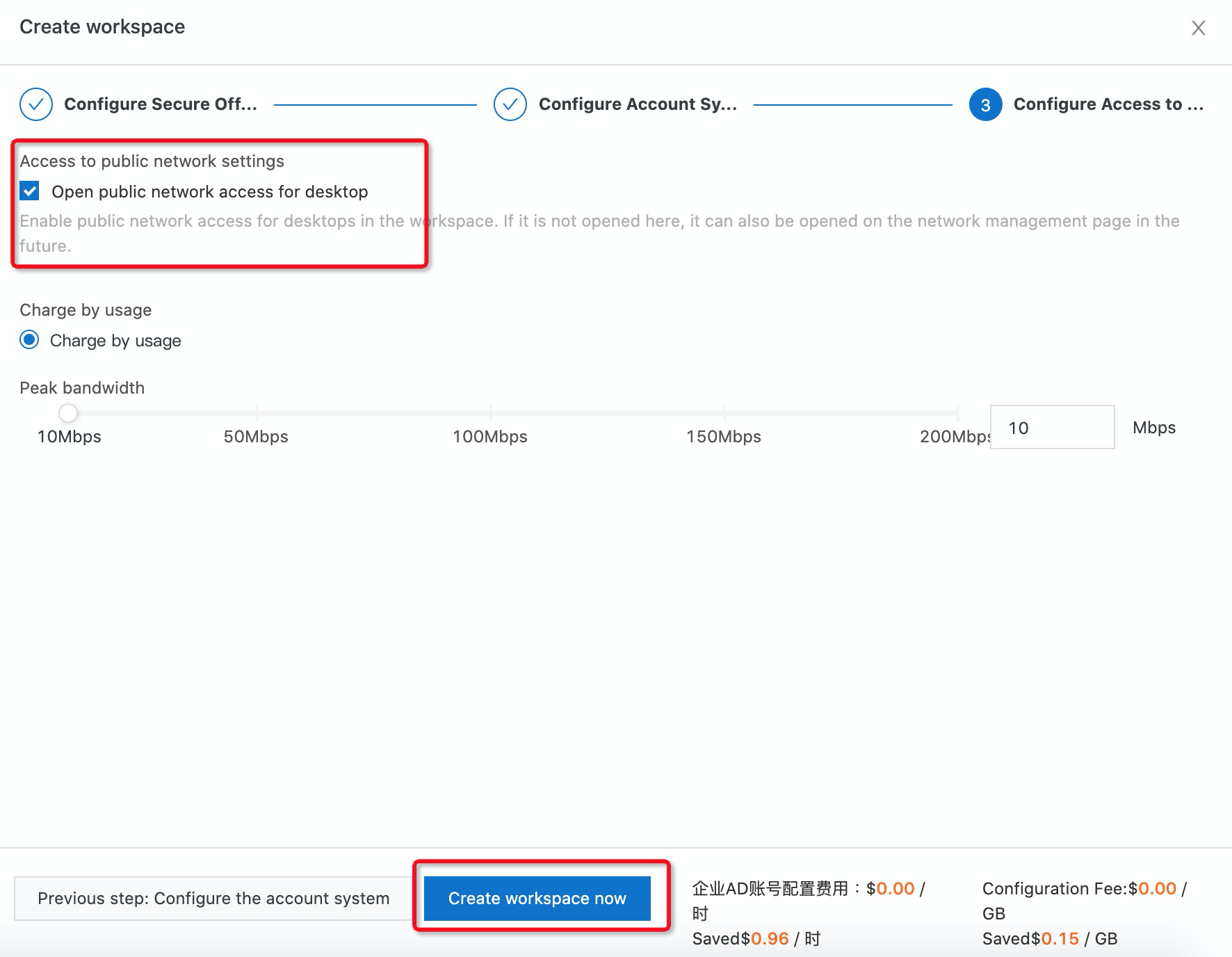
7. After you have created the workspace, you should verify the result on the Secure office network section on the left-hand side. You can see an Active Directory Connector is in Registering Status. The connection address is 192.168.255.251.
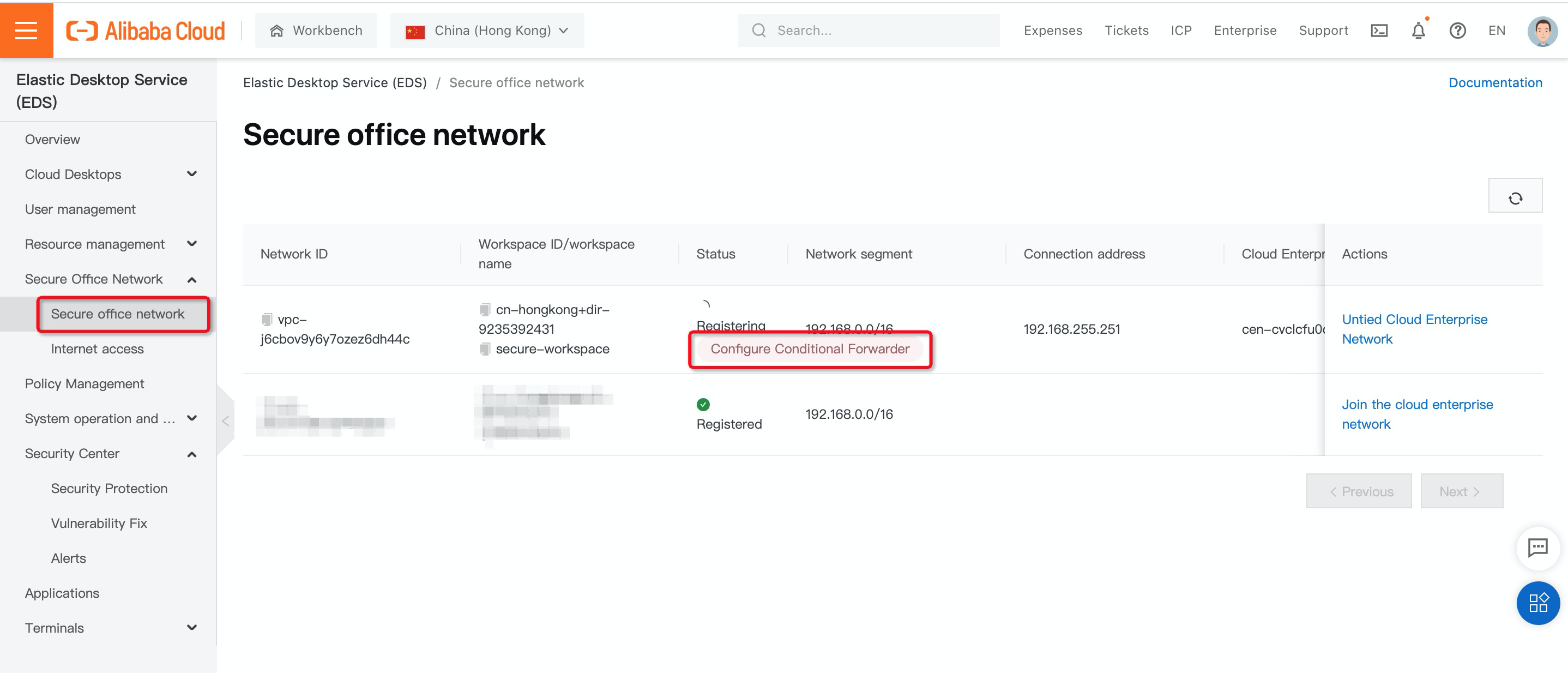
8. Before configuring AD integration between your Active Directory and EDS, make sure the EDS VPC can access the Active Directory services with the configured firewall policies below:
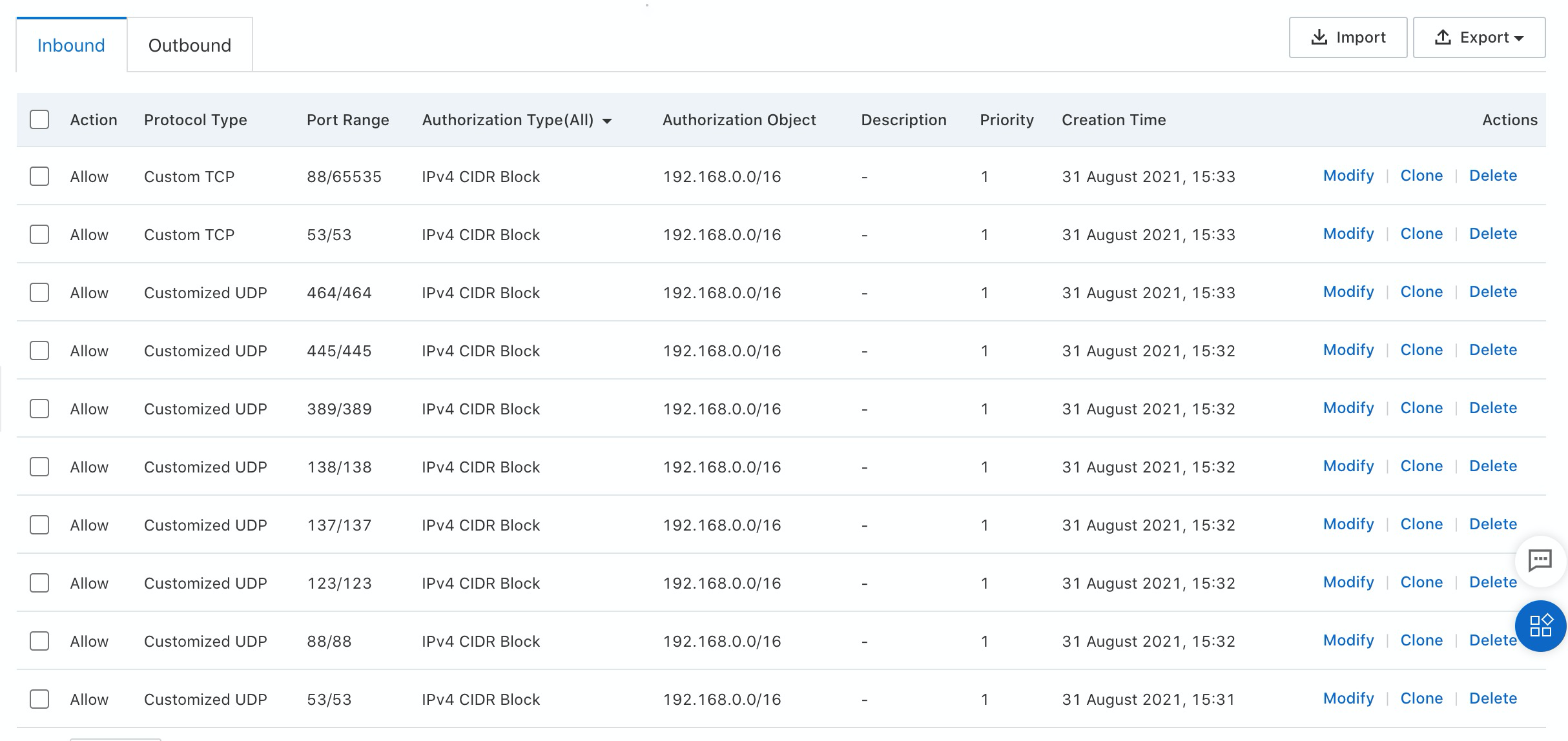
9. You must enable zone transfer for the DNS addresses of the domains of your enterprise AD system:
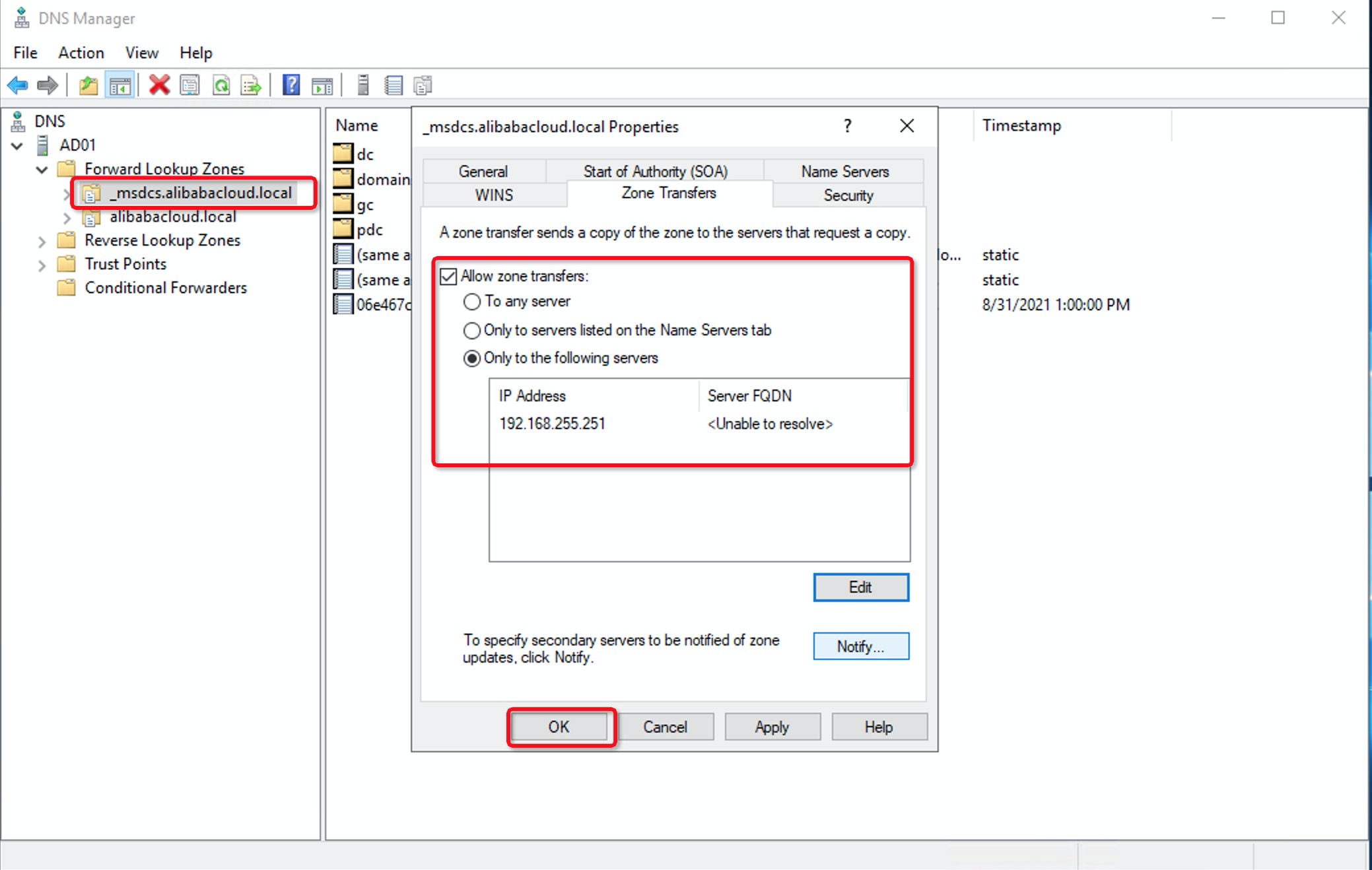
10. You must configure the conditional forwarder for the DNS addresses of the domains of your enterprise AD system. In the DNS Manager dialog box, right-click Conditional Forwarders and select New Conditional Forwarder. Enter ecd.acs in the DNS domain and IP address 192.168.255.251 of the master servers and click OK:
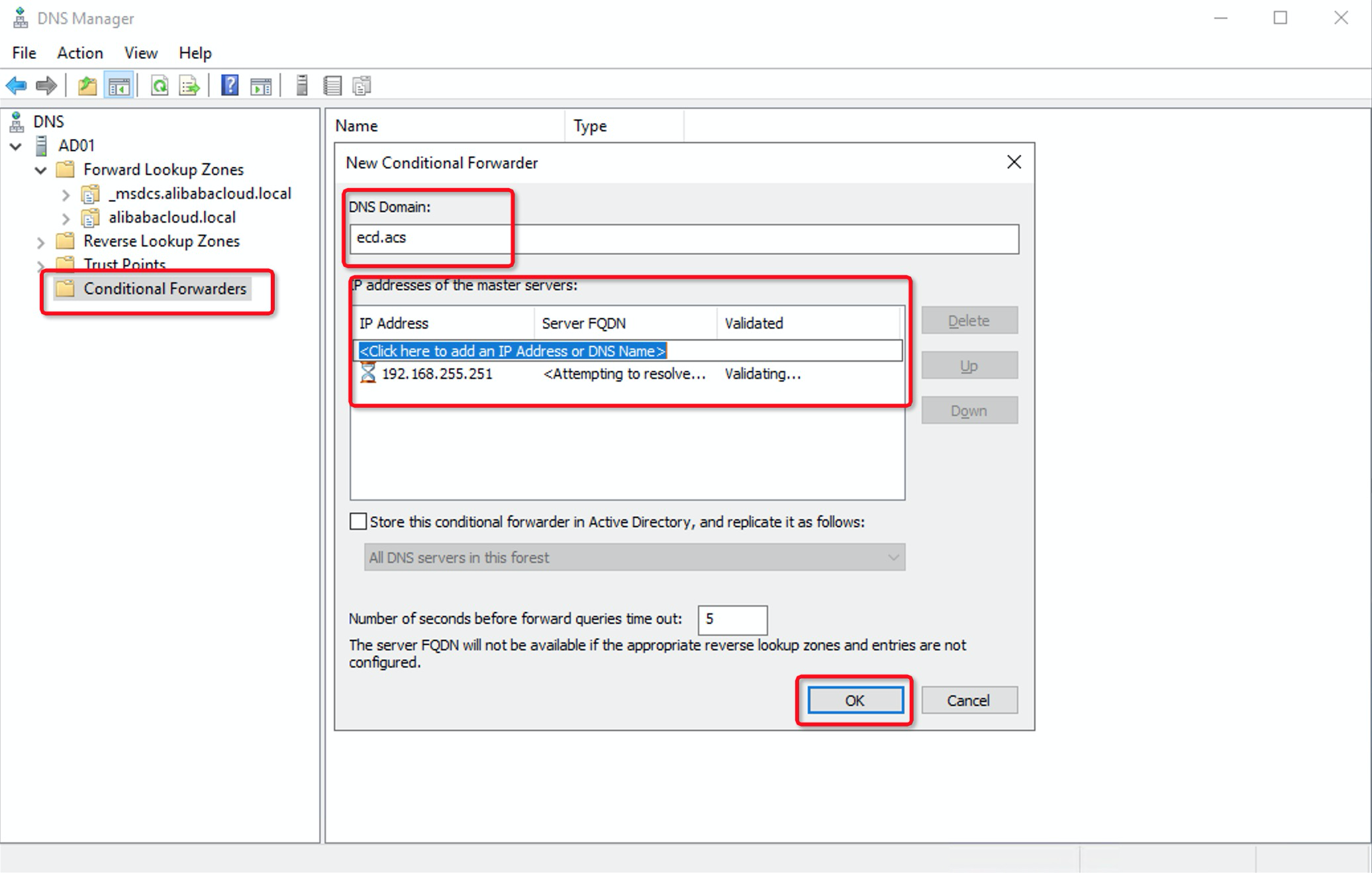
11. After the preceding configurations are complete, the Active Directory Connector is now in the Registered state:
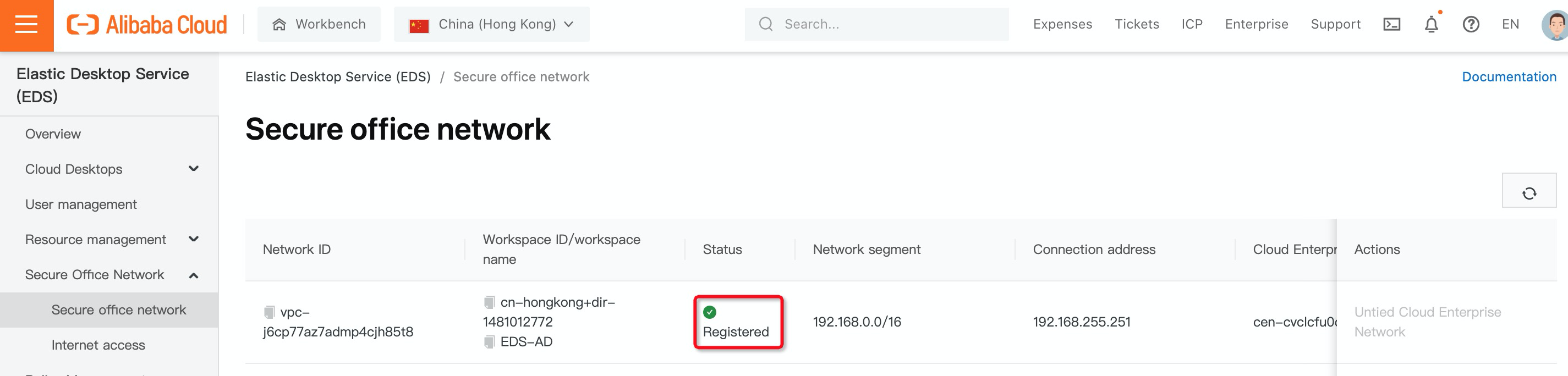
12. You can create a desktop by navigating to Desktops under Cloud Desktops and clicking Create Cloud Desktop:
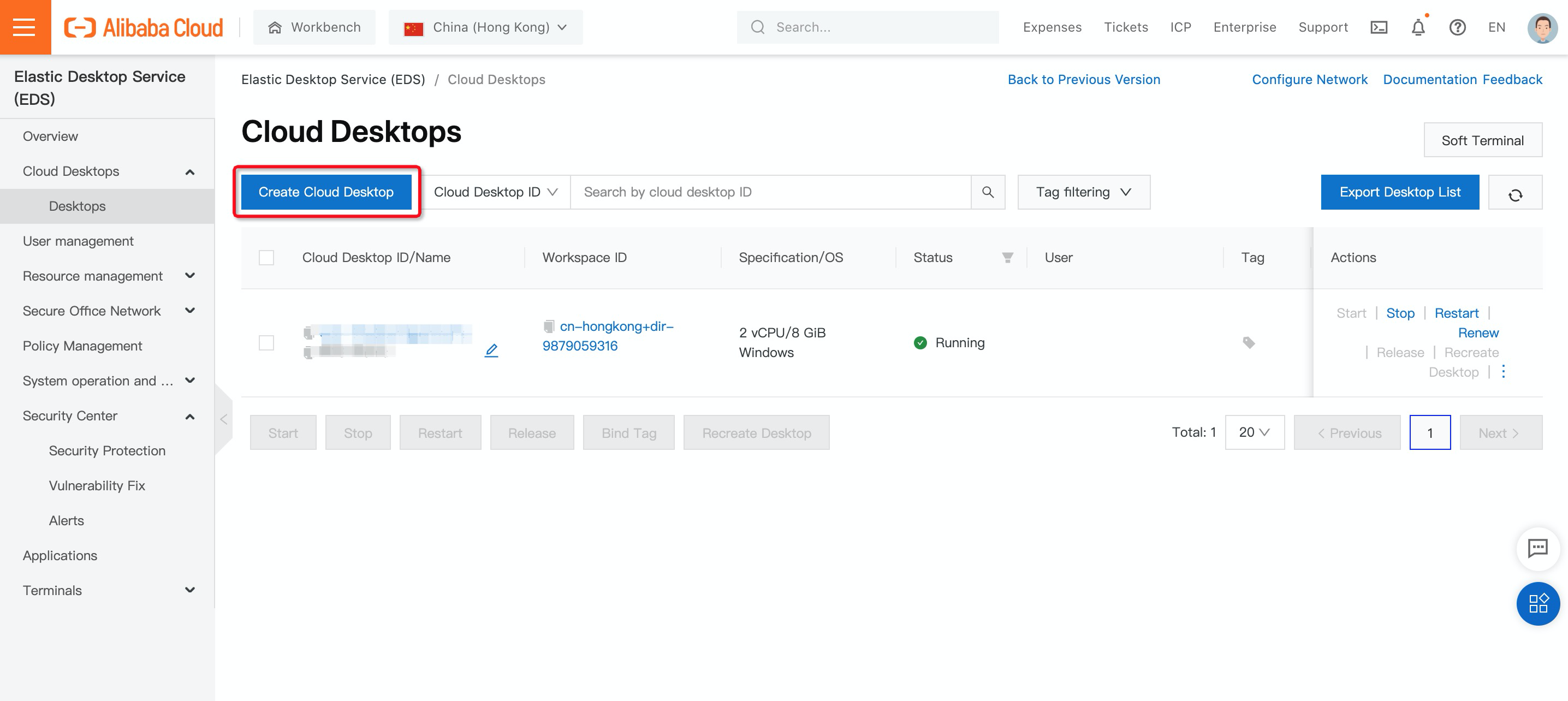
13. On the Elastic Desktop Service Create Desktop page, configure the parameters for the cloud desktop. (In this example, under billing method, select Subscription, enter desktop name, and select the workspace you created before and the number of cloud desktops you want to purchase):
14. Select Desktop Templates for cloud desktop and duration and click Confirm Order:
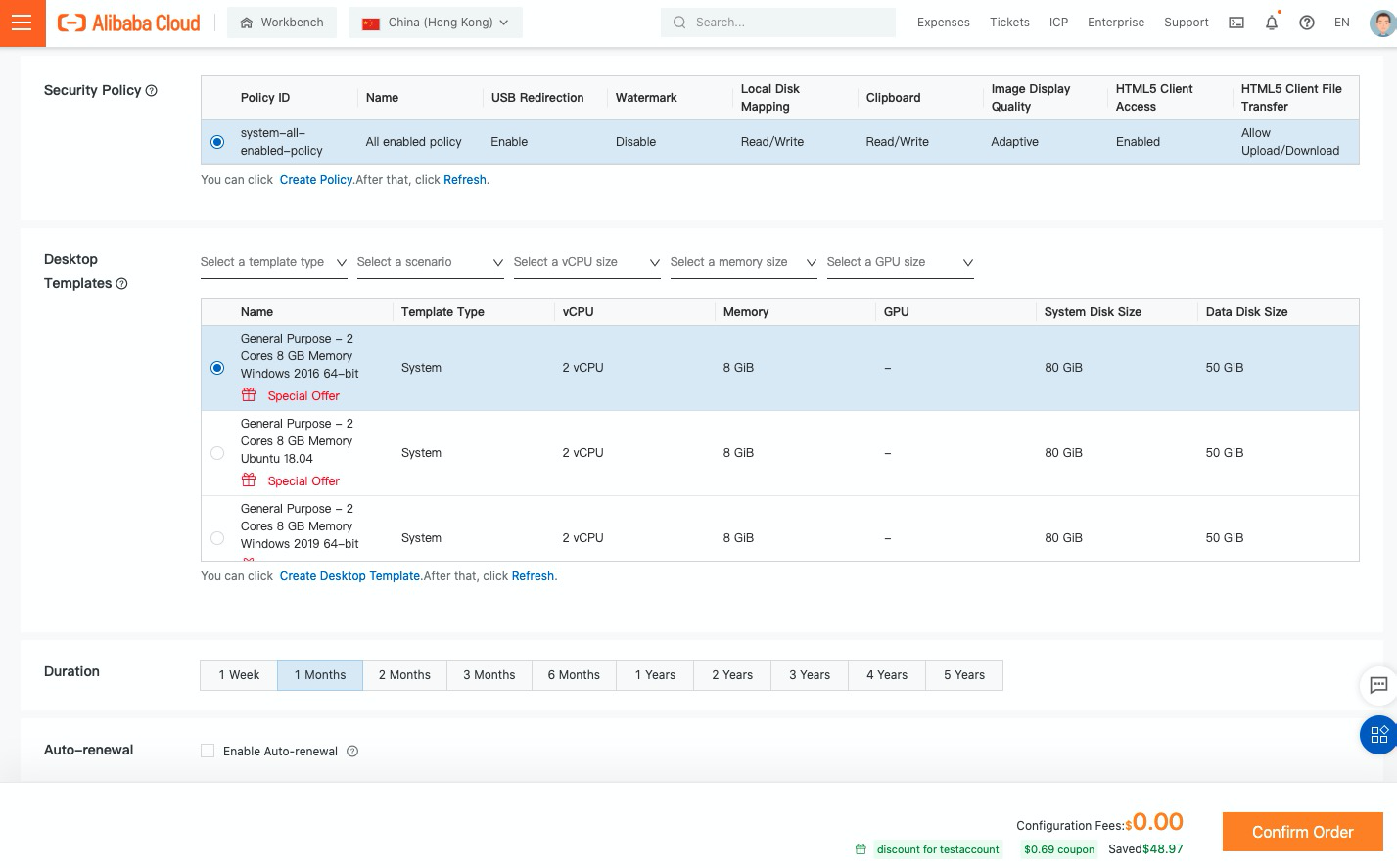
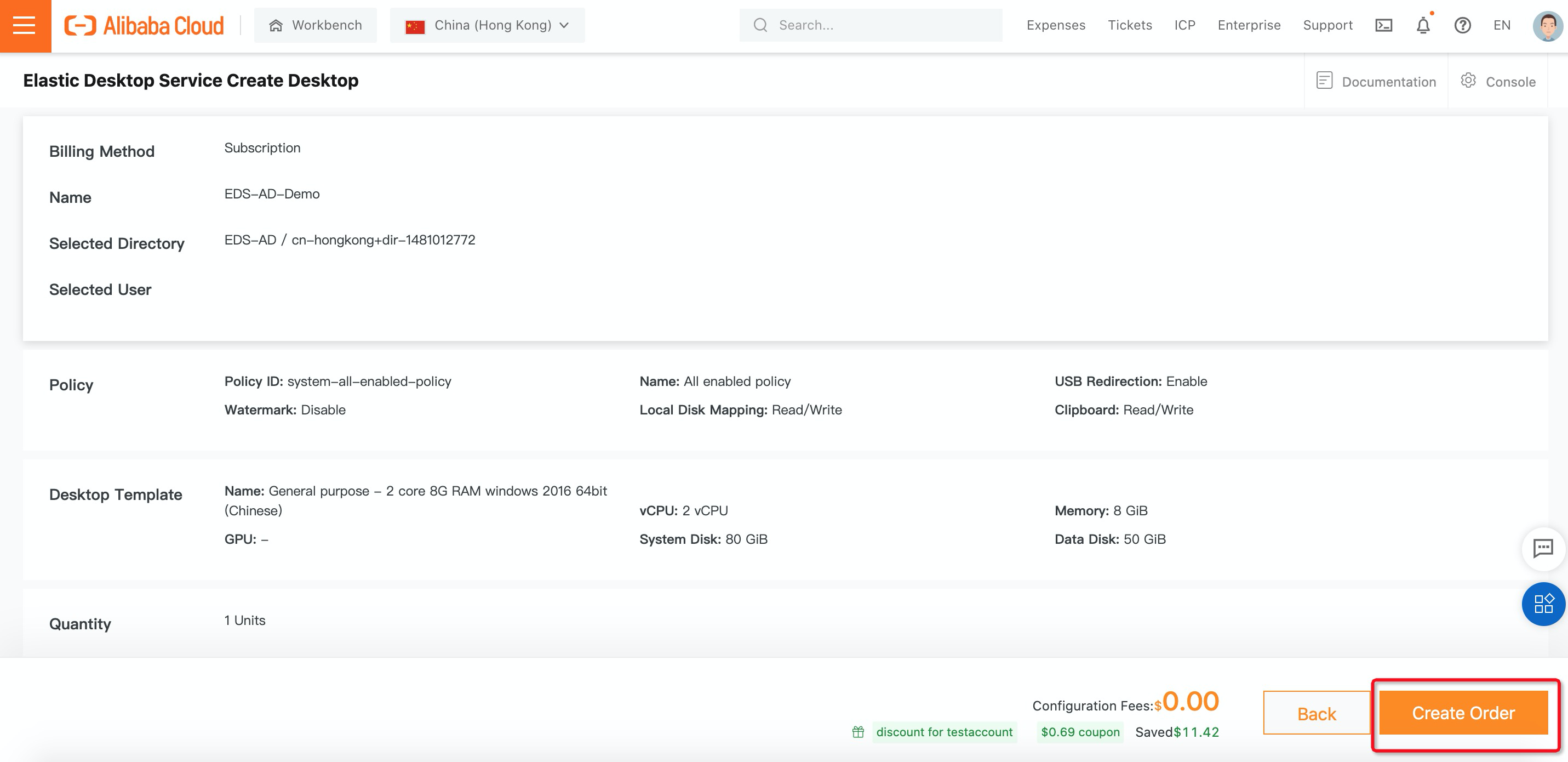
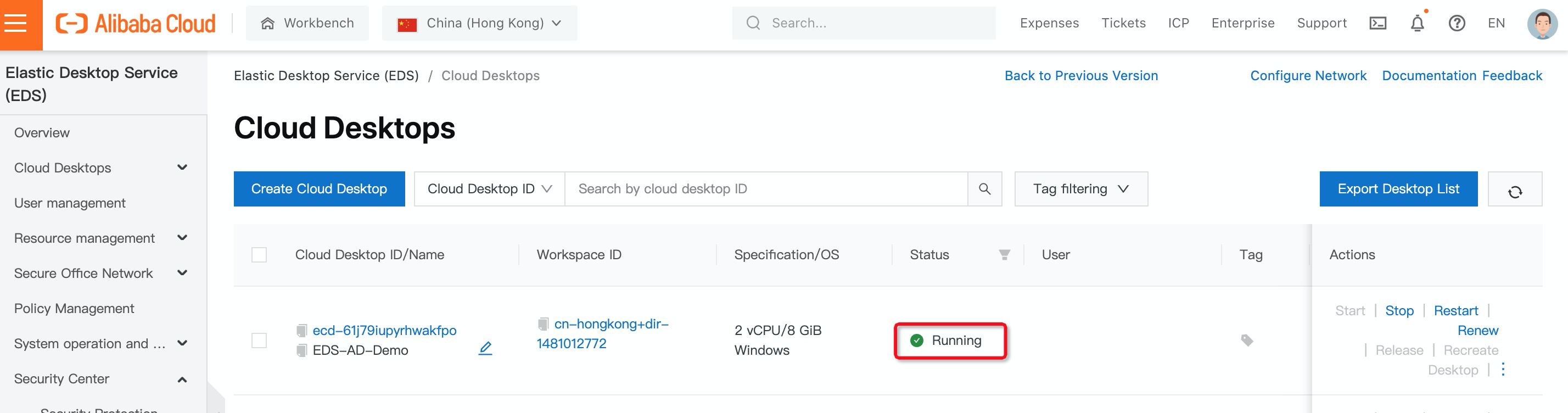
15. The desktop you created is up and running now:
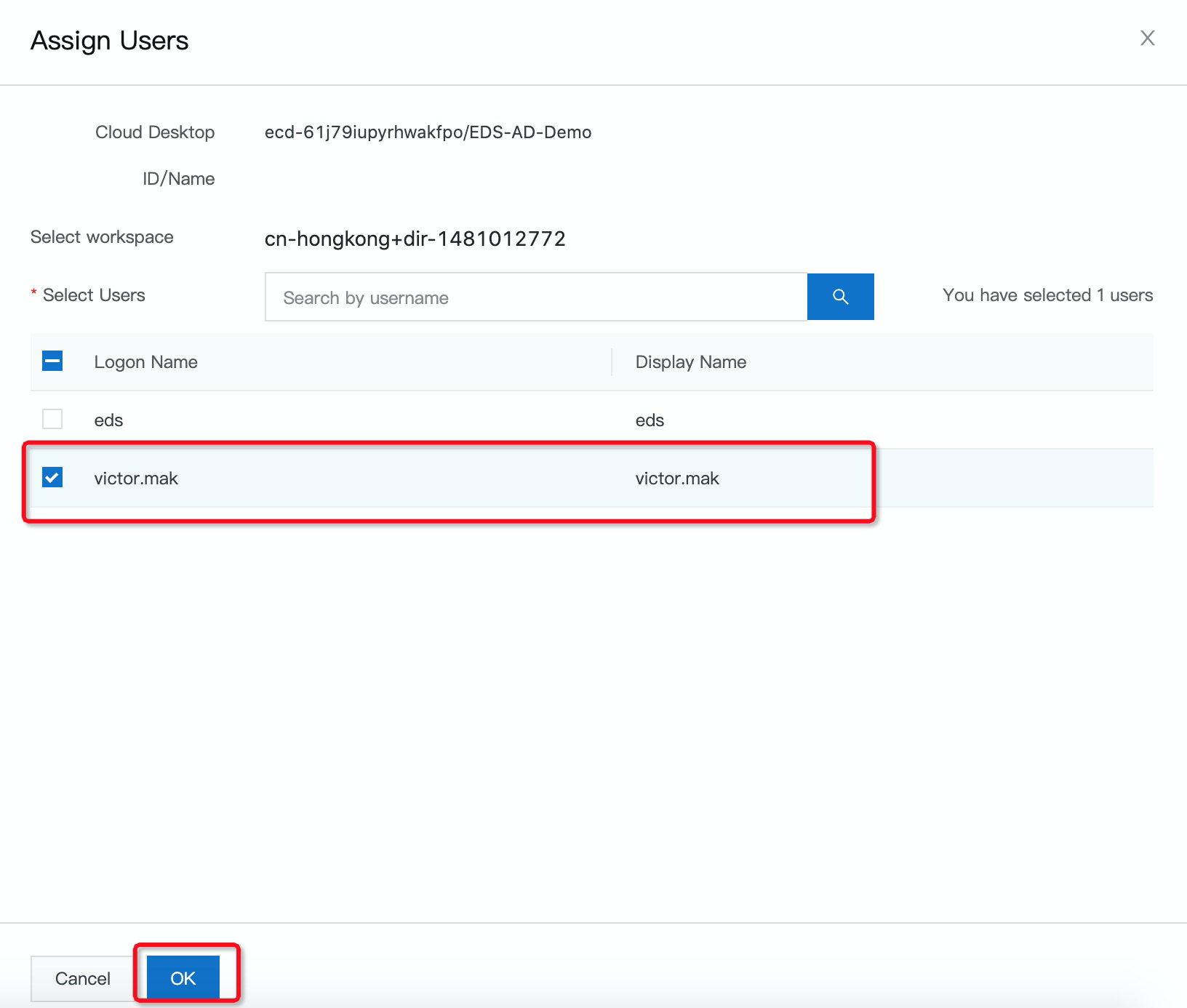
16. On the Cloud Desktops page, find the cloud desktop that you want to assign to regular users, click the More icon in the Actions column, and then click Assign Users:
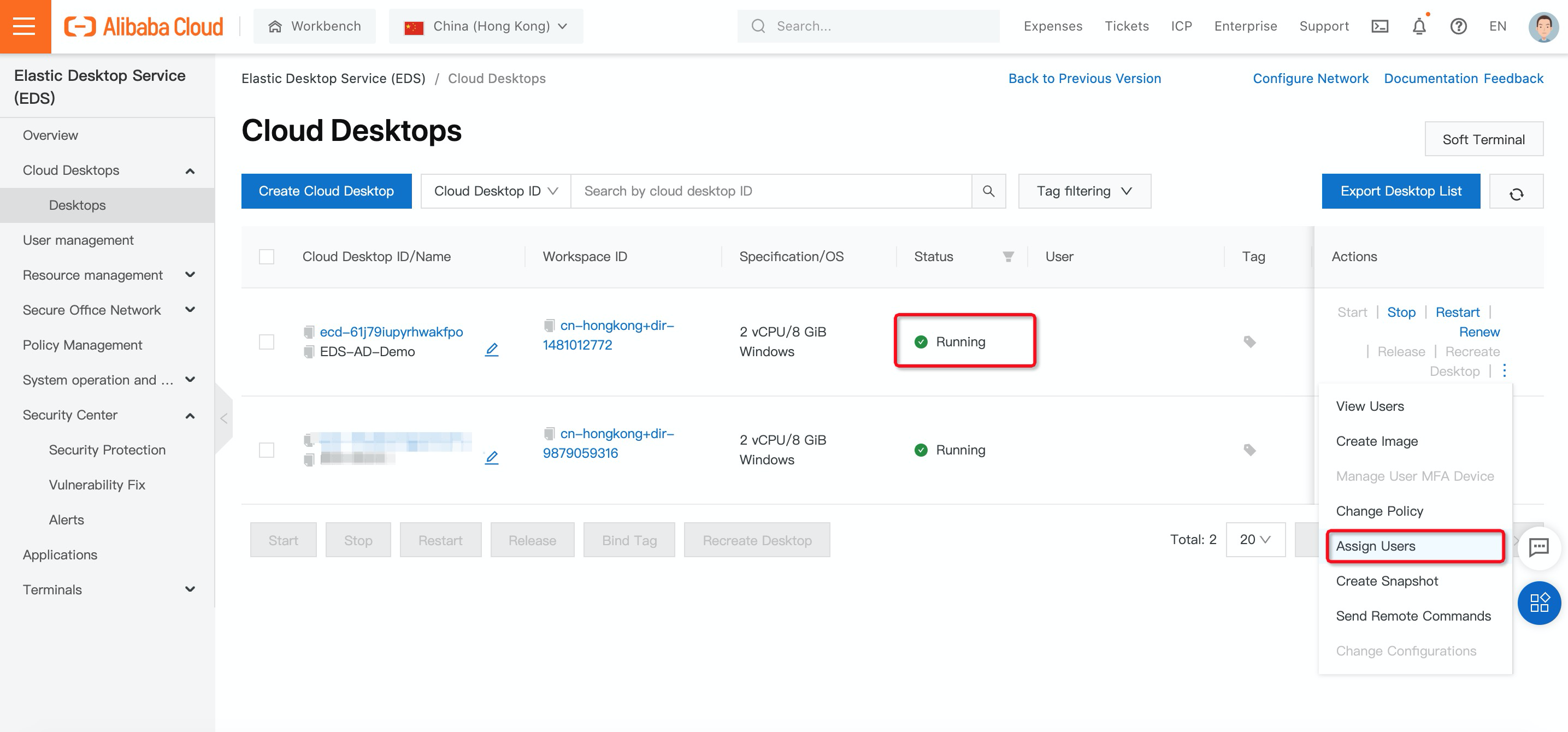
17. In the Assign Users panel, select users in the Active Directory and click OK.
A policy is a set of security rules used to control security configurations when regular users use cloud desktops. A policy contains a basic policy (USB redirection and watermarks) and one or more network control rules (inbound and outbound traffic rules):
1. On the left-side navigation pane, click Policy Management and then Create Policy:
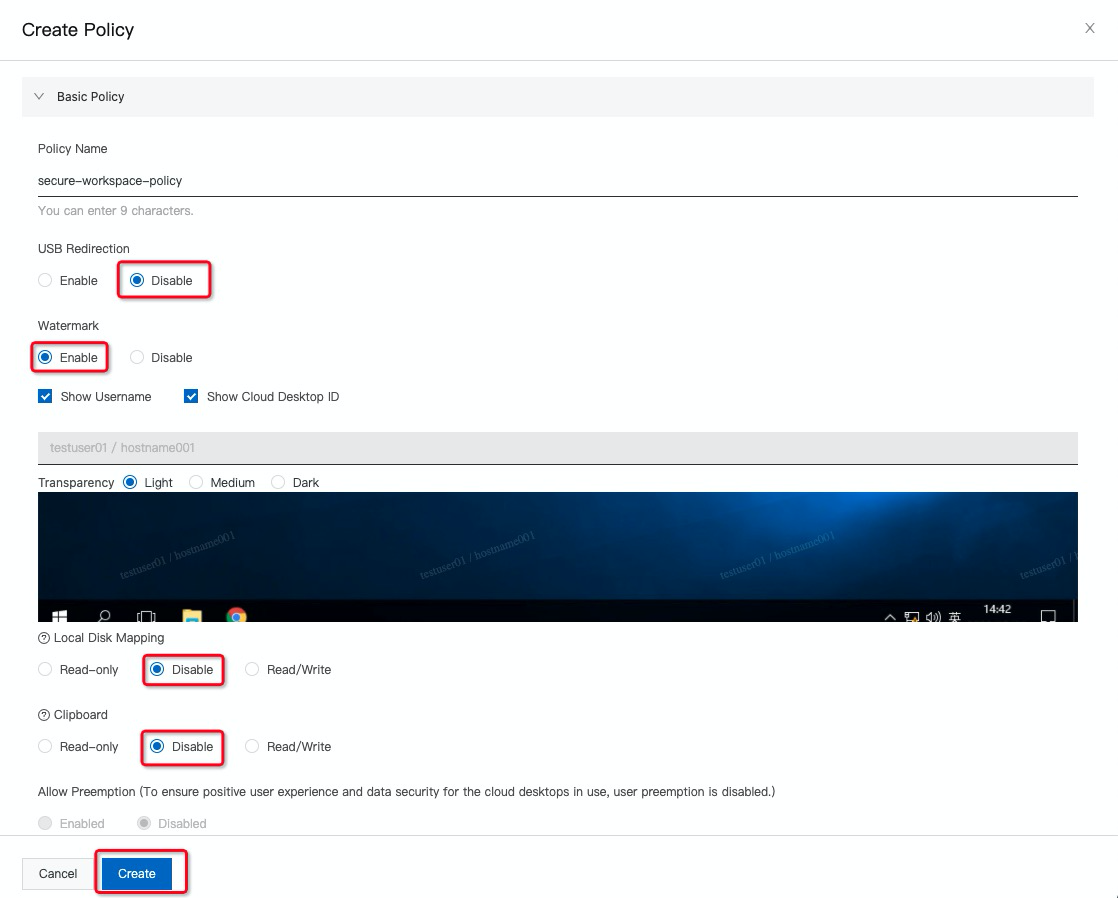
2. Here are the best practices settings to build a secure remote workspace. You can also modify the settings based on company policies and leads:
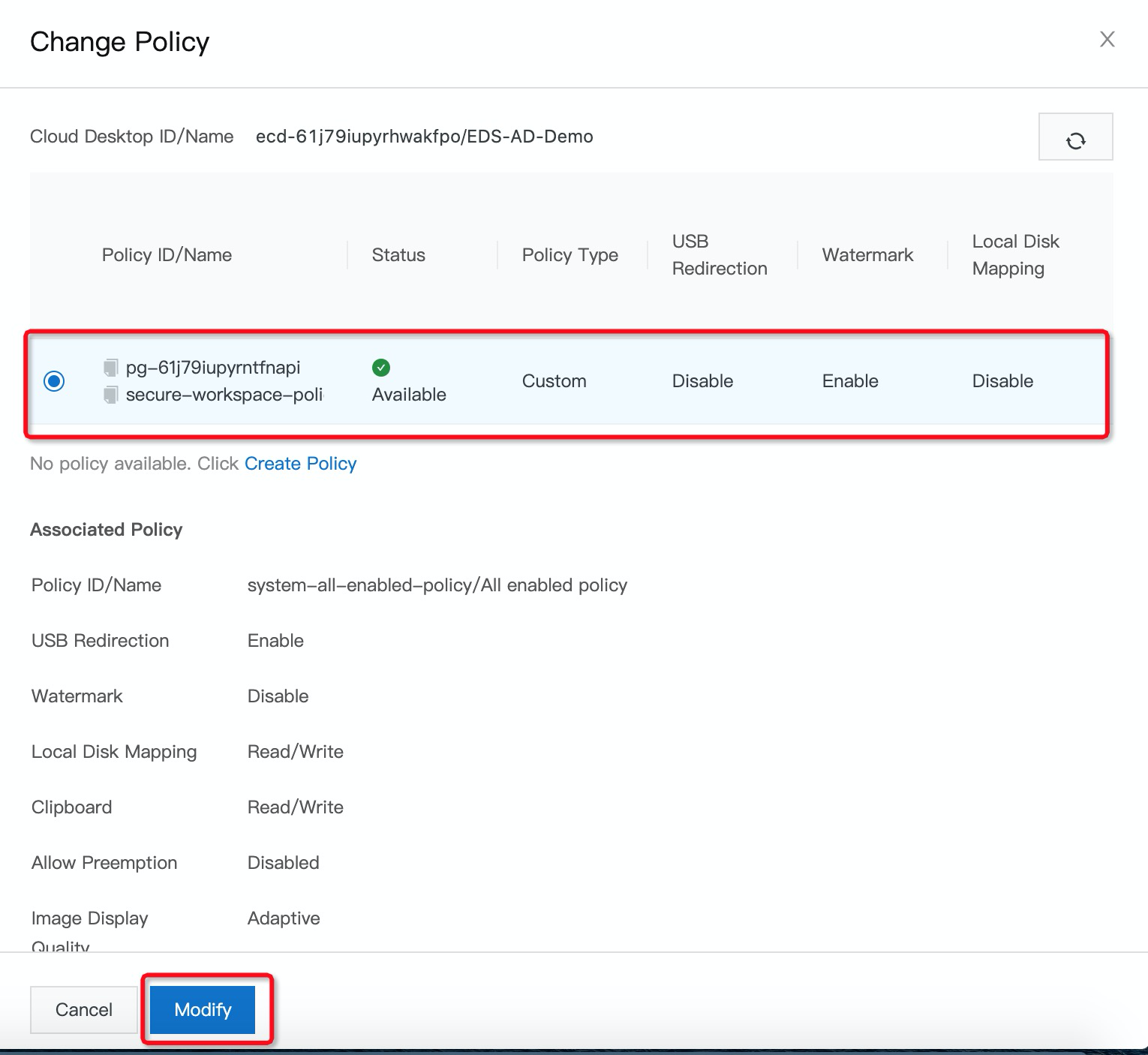
3. After you have successfully created secure policies, on the Cloud Desktops page, find the cloud desktop for which you want to change the policy, click the More icon in the Actions column, and then click Change Policy.
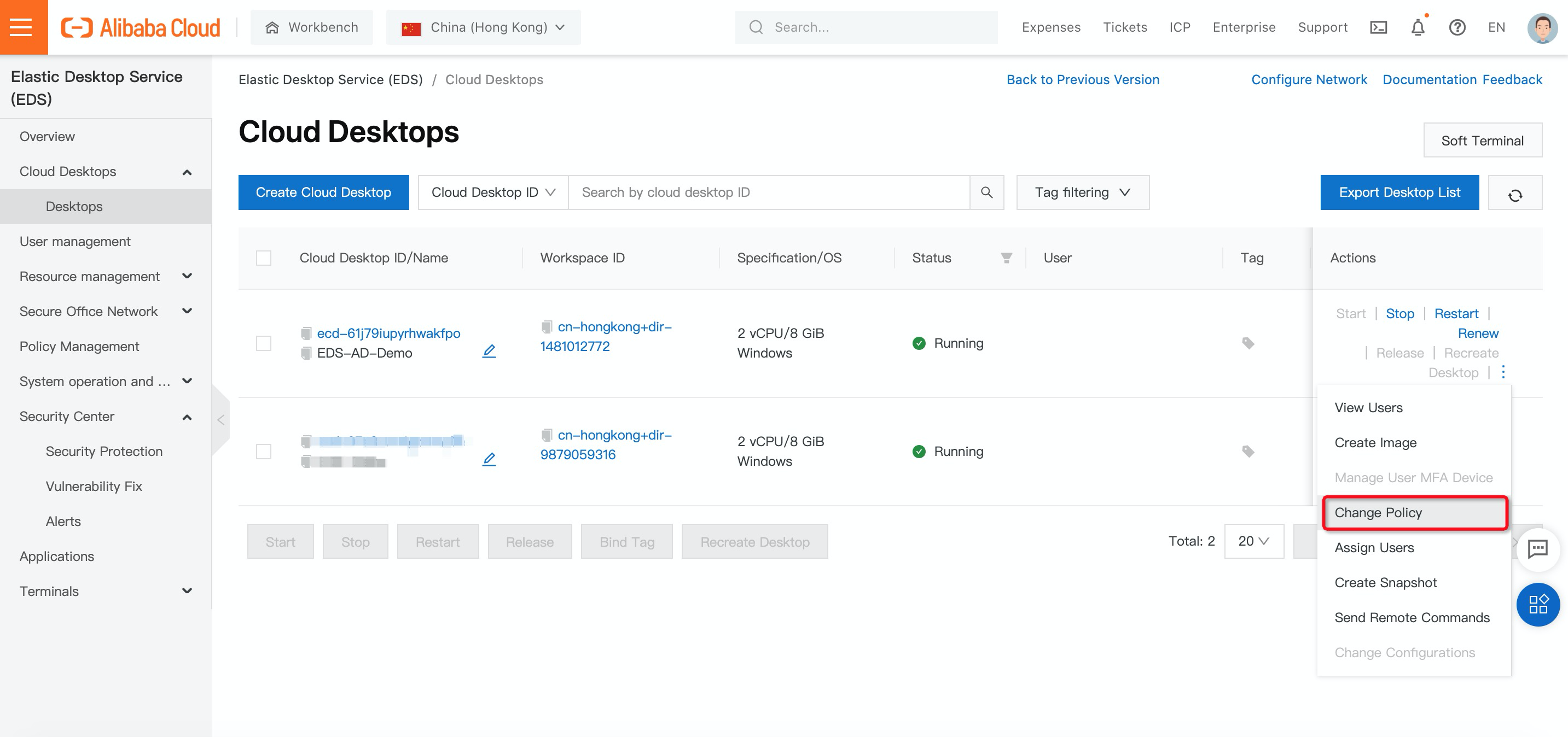
4. In the Change Policy panel, select a policy and click Modify:
The security protection feature provides antivirus and vulnerability detection and fixing for all cloud desktops within a specific region to ensure security. The security protection feature provides the following capabilities based on Security Center:
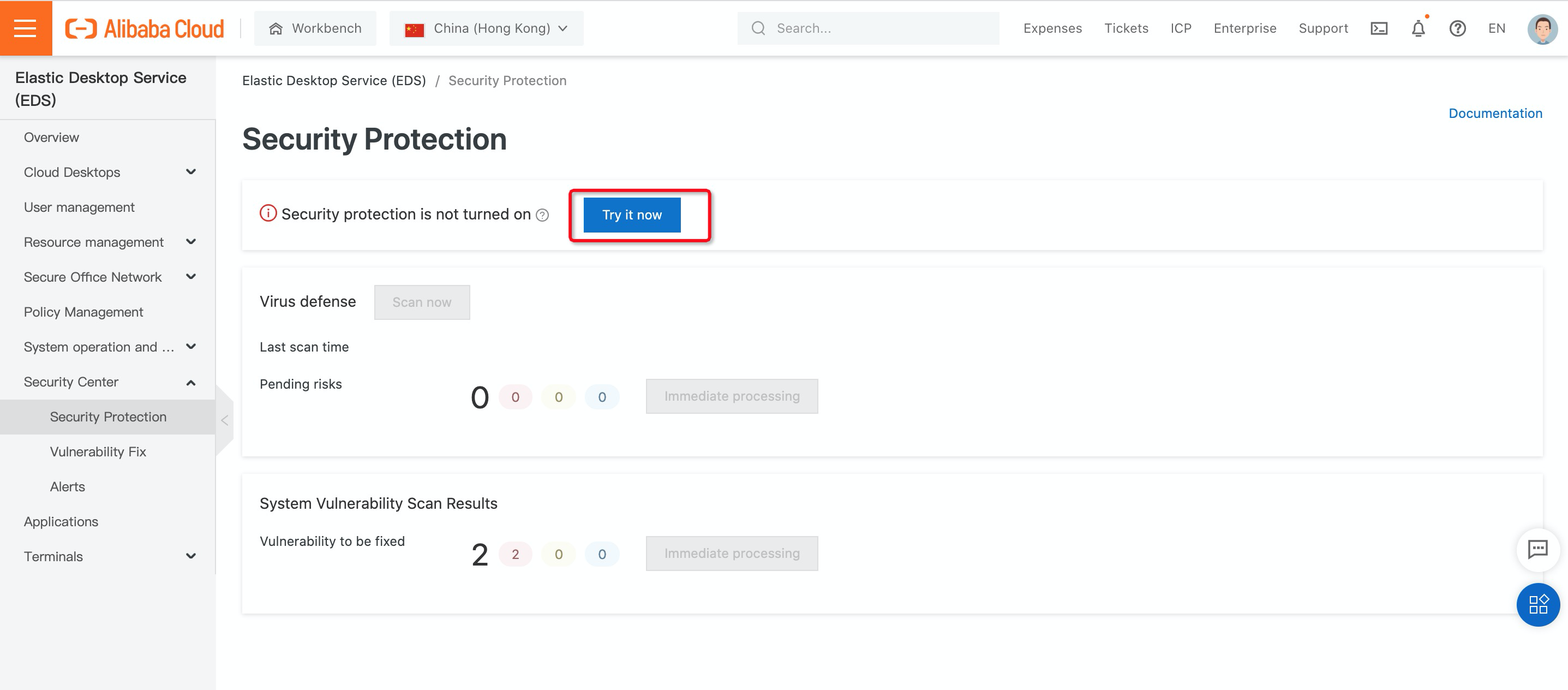
1. On the left-side navigation pane, choose Security Protection under Security Center and click Try it now:
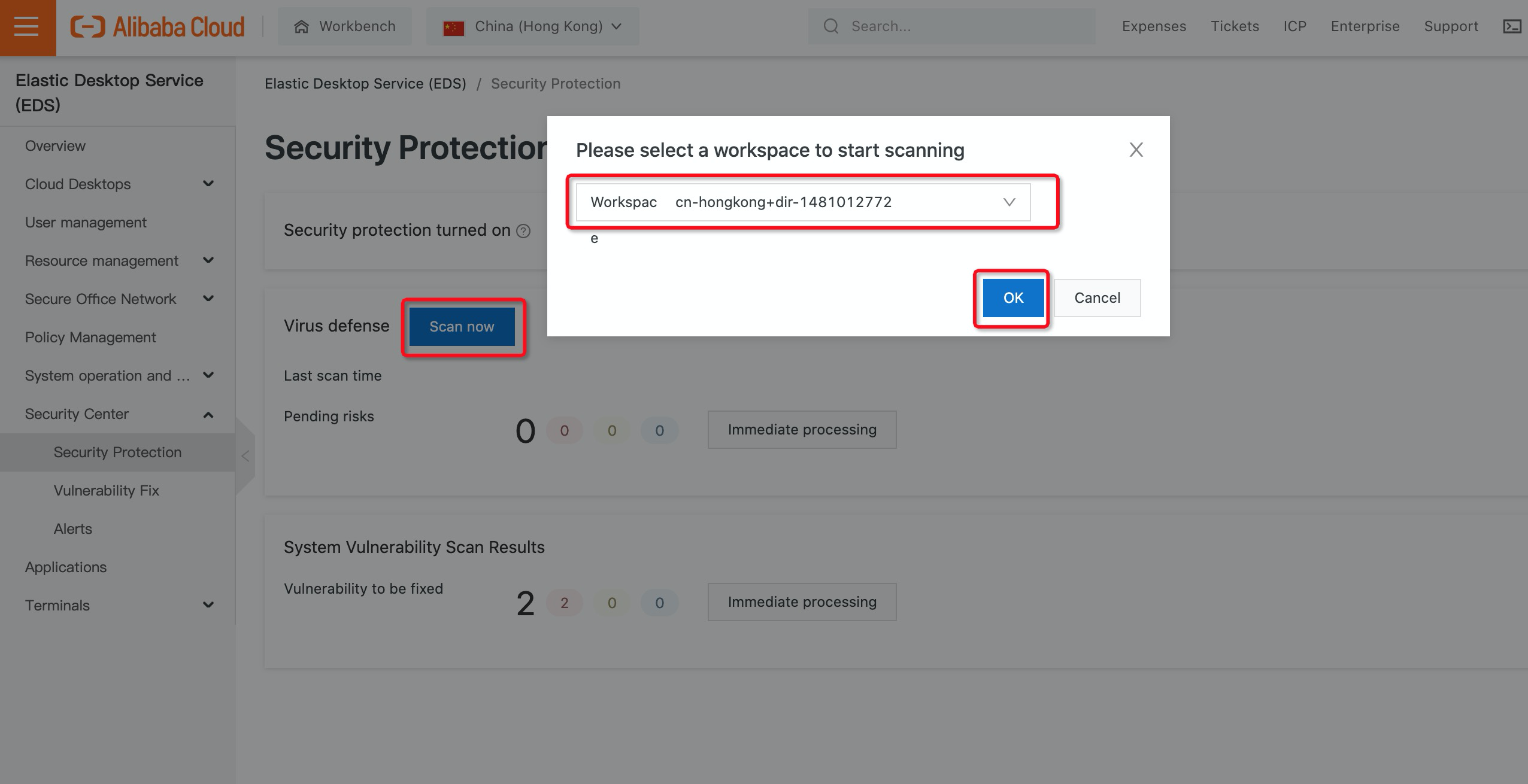
2. After security protection is enabled, the system scans your cloud desktops once every day. You can also trigger scanning manually based on your needs by clicking Scan Now and selecting the workspace for which you want to perform manual scanning.
3. After completing security scanning, the statistics of the scan results are displayed by severity, as shown in the following figure:
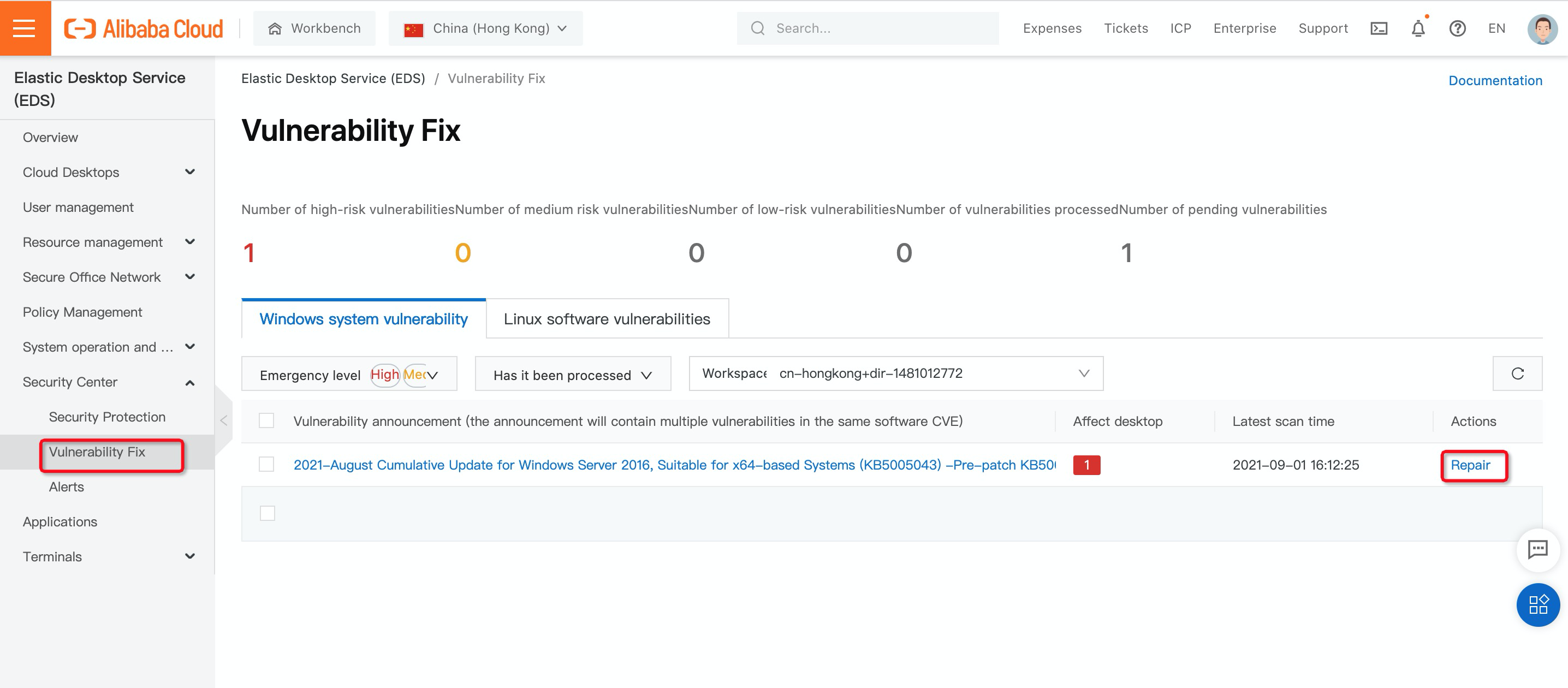
4. On the left-side navigation pane, choose Vulnerability Fix under Security Center. You can filter vulnerabilities by selecting the required options from the Emergency level. Find the vulnerability that you want to fix and click Repair in the Actions column:
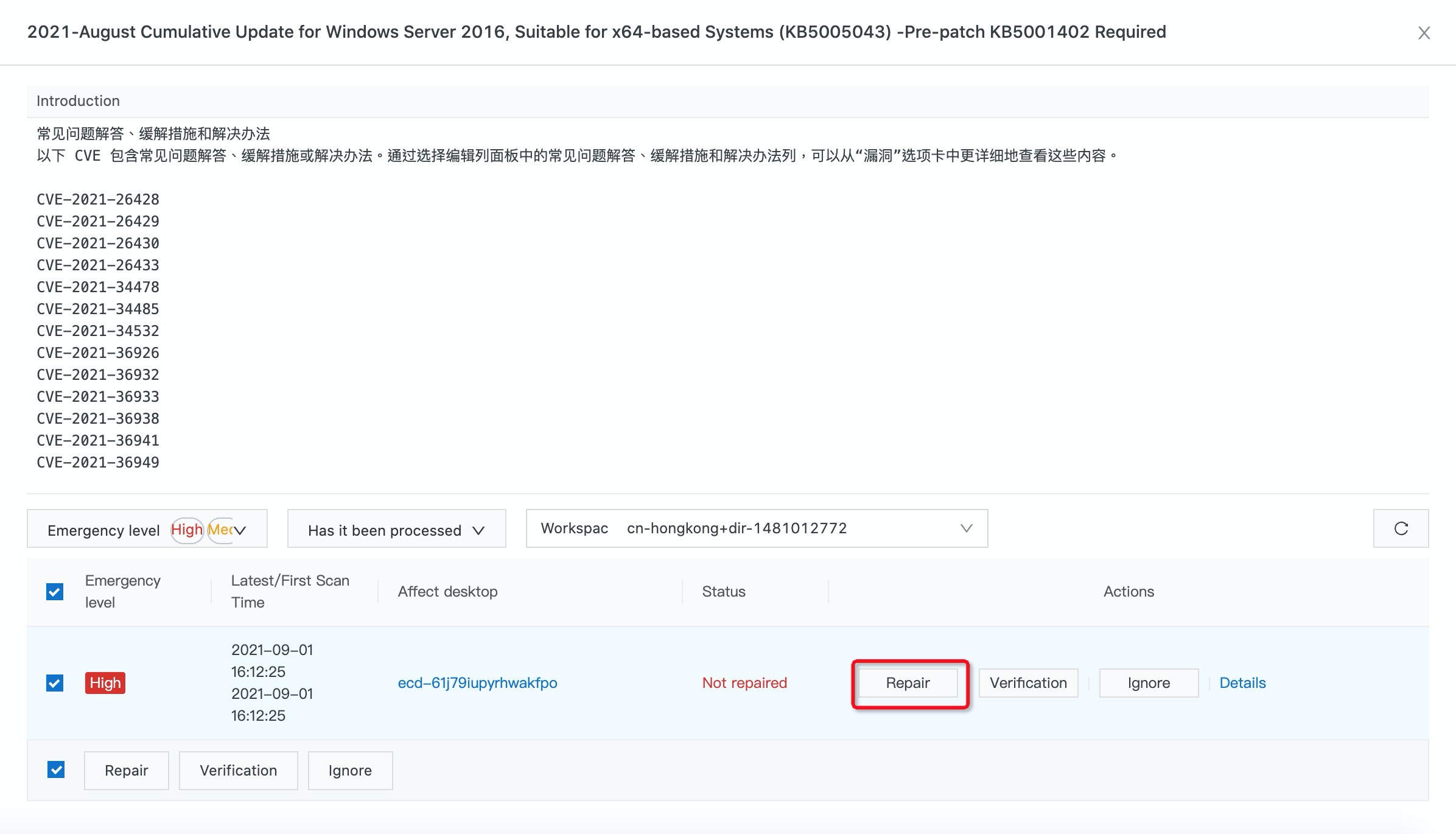
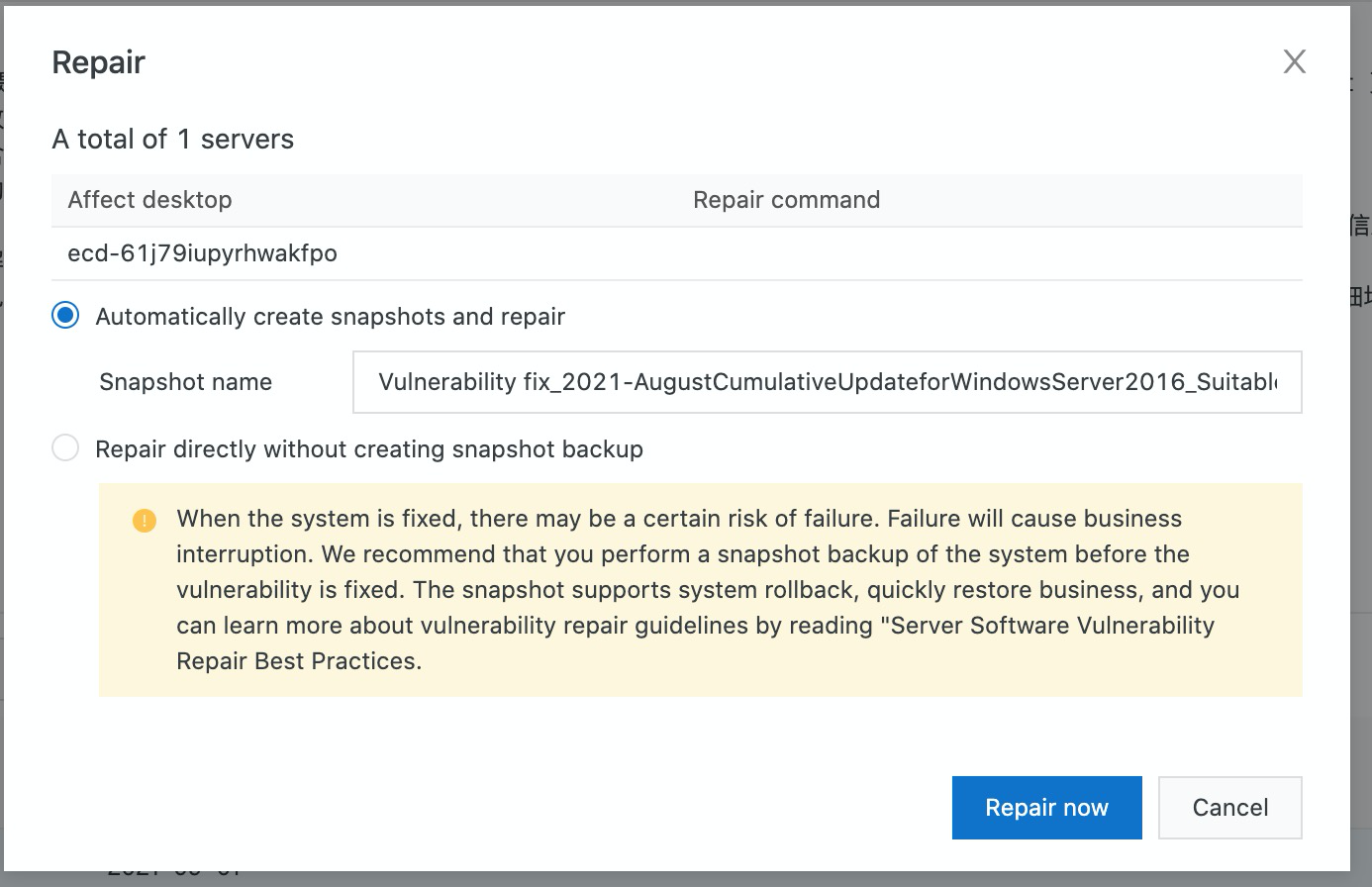
5. You can either select automatically create snapshots and repair or repair directly without creating snapshot. Then, click Repair Now.
To allow employees remote access to the cloud desktop via a secure connection, customers can use Alibaba Cloud VPN services and integrate with Alibaba Cloud Identity as a Service (iDaaS) to provide 2FA authentication via Active Directory.
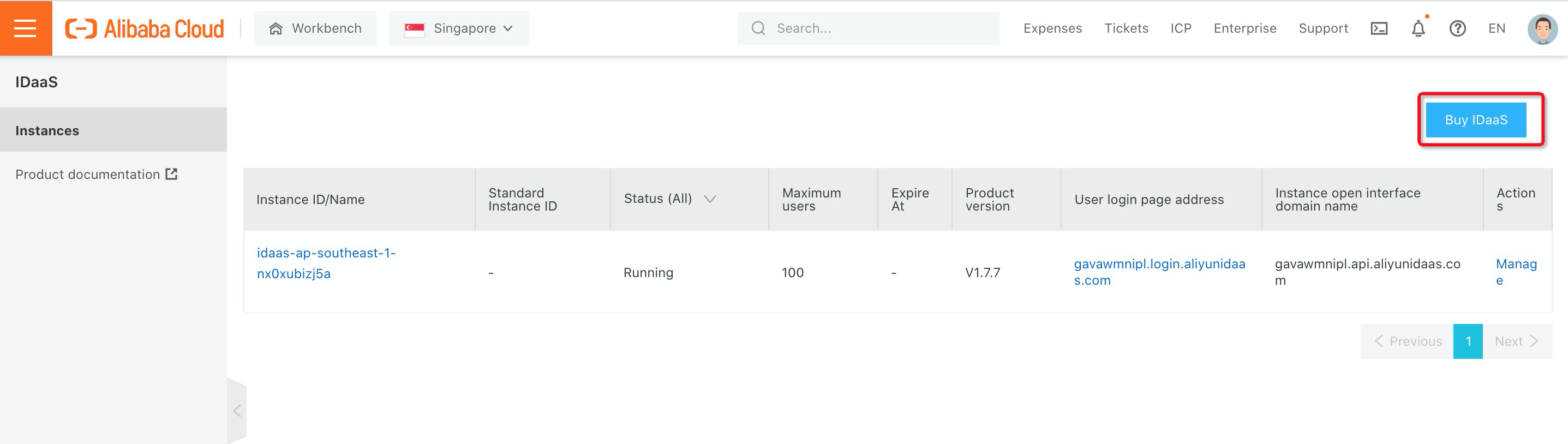
1. Log on to the Alibaba Cloud iDaaS console and click Buy iDaaS:
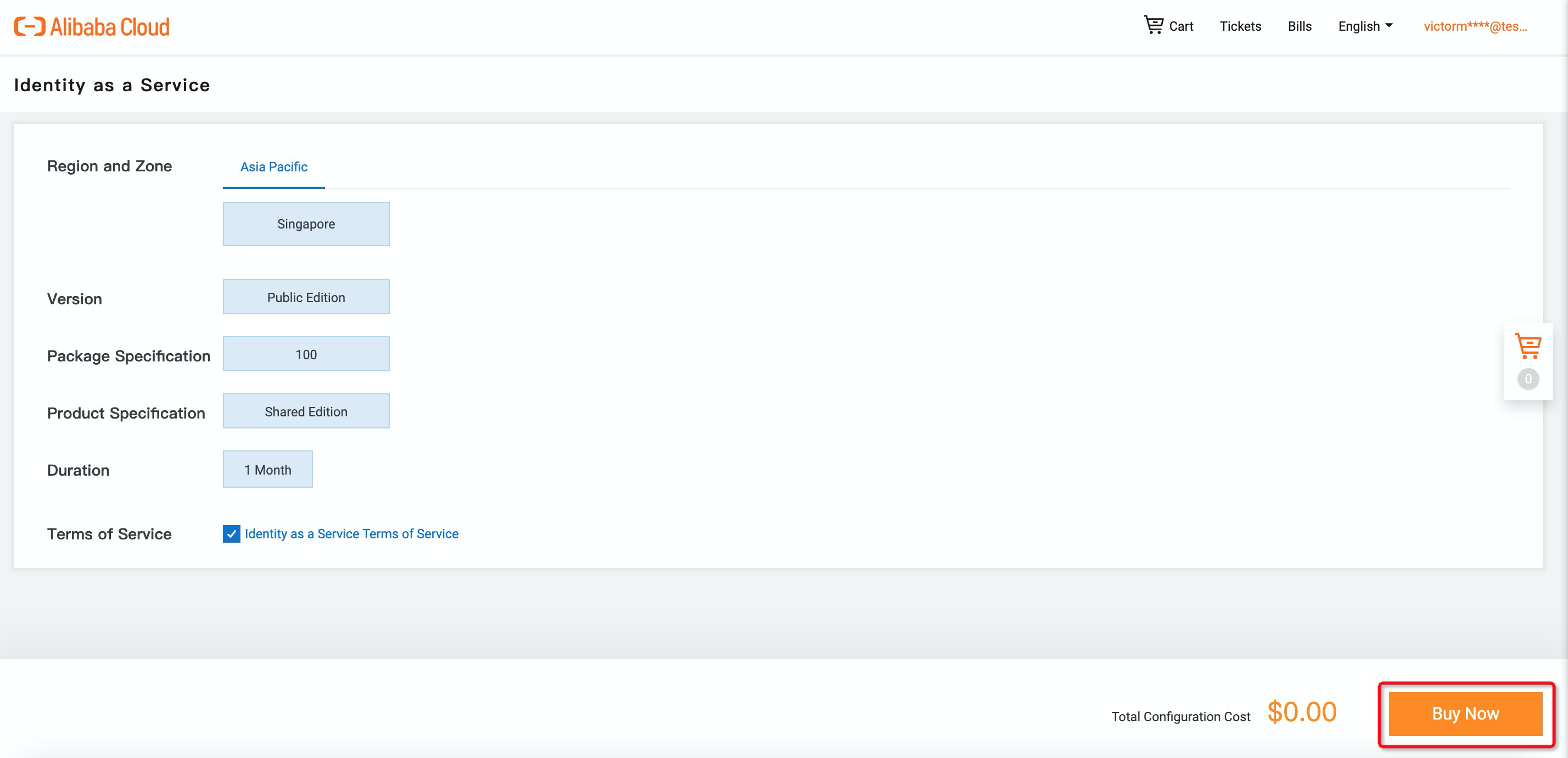
2. Click Buy Now and Purchase to enable iDaaS:
3. Once the iDaaS instance is ready, you can click Manage in the iDaaS console:
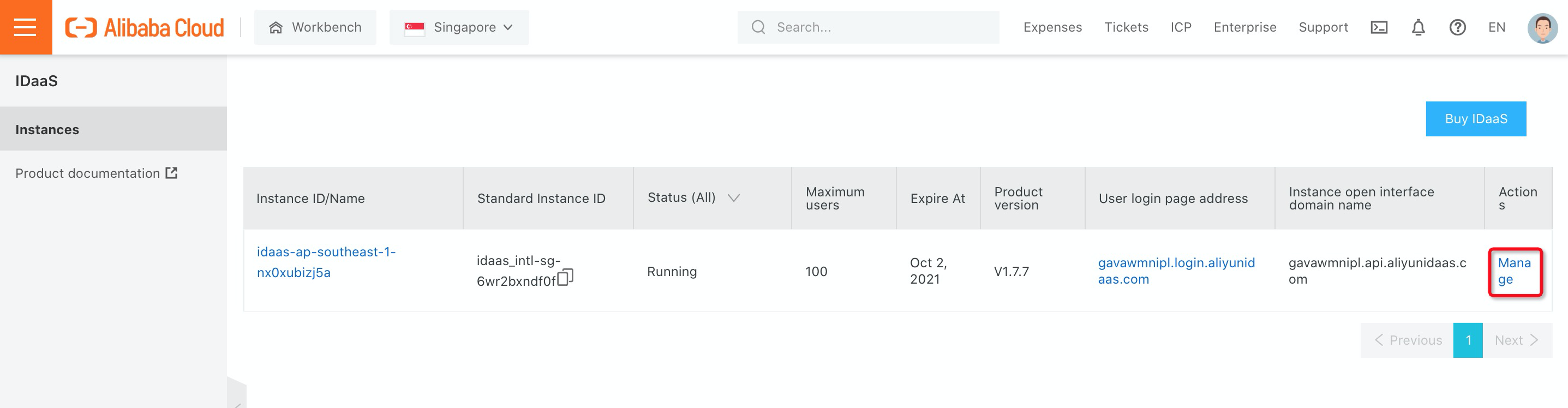
4. Navigate to Authentication Sources under Authentication, find LDAP and click Add Authentication Source:
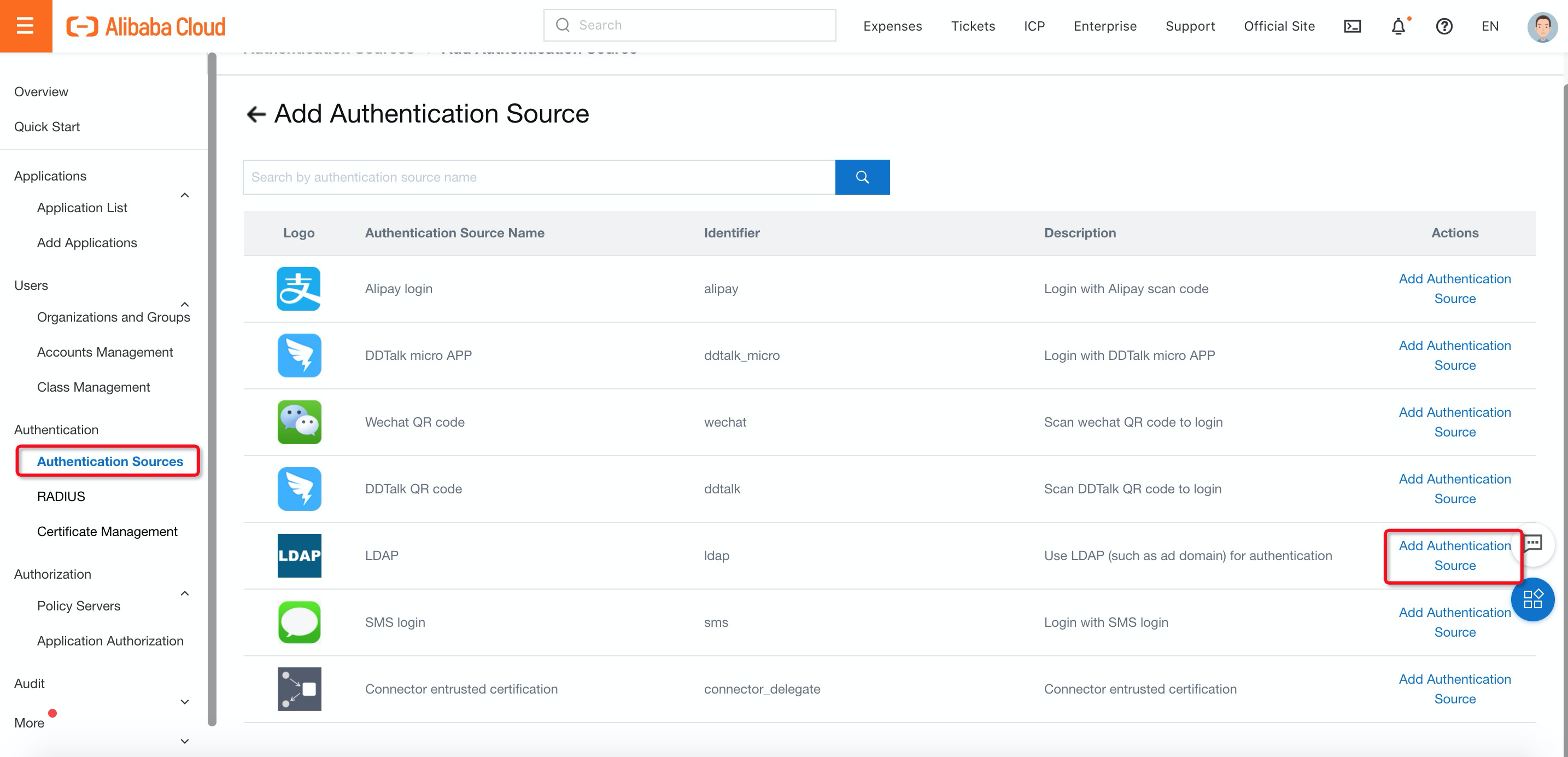
5. Fill in the LDAP information:
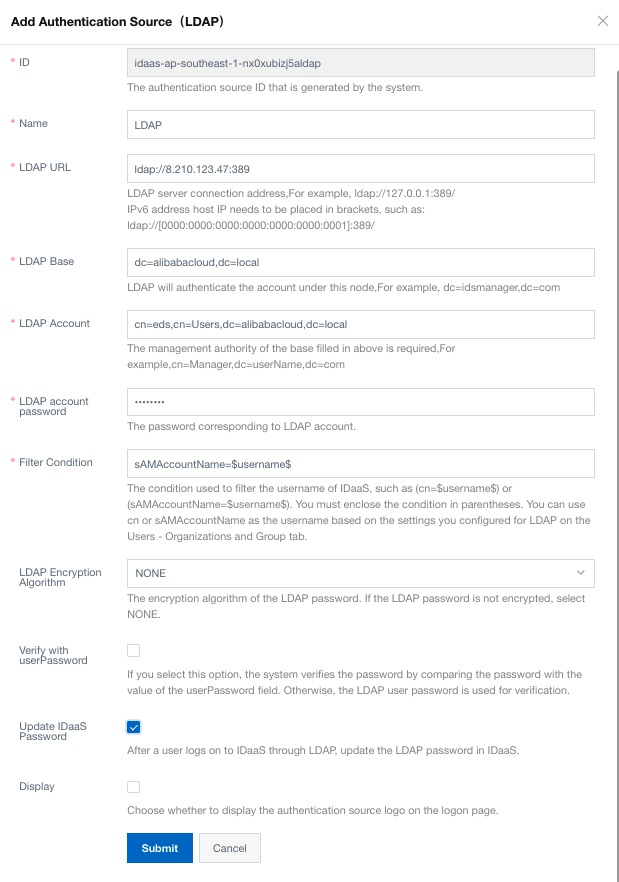
6. Make sure LDAP status is switched ON:
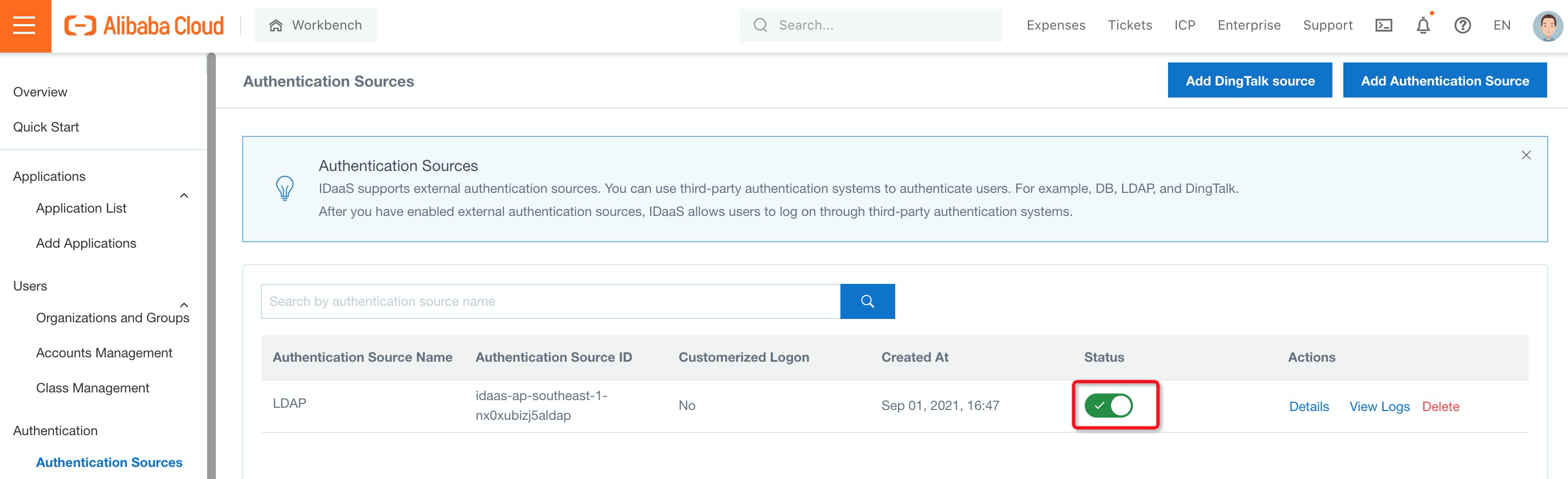
7. Navigate to Cloud Product AD Authentication under Security Settings, select AD Authentication Source and switch to Enable. Then, click Save:
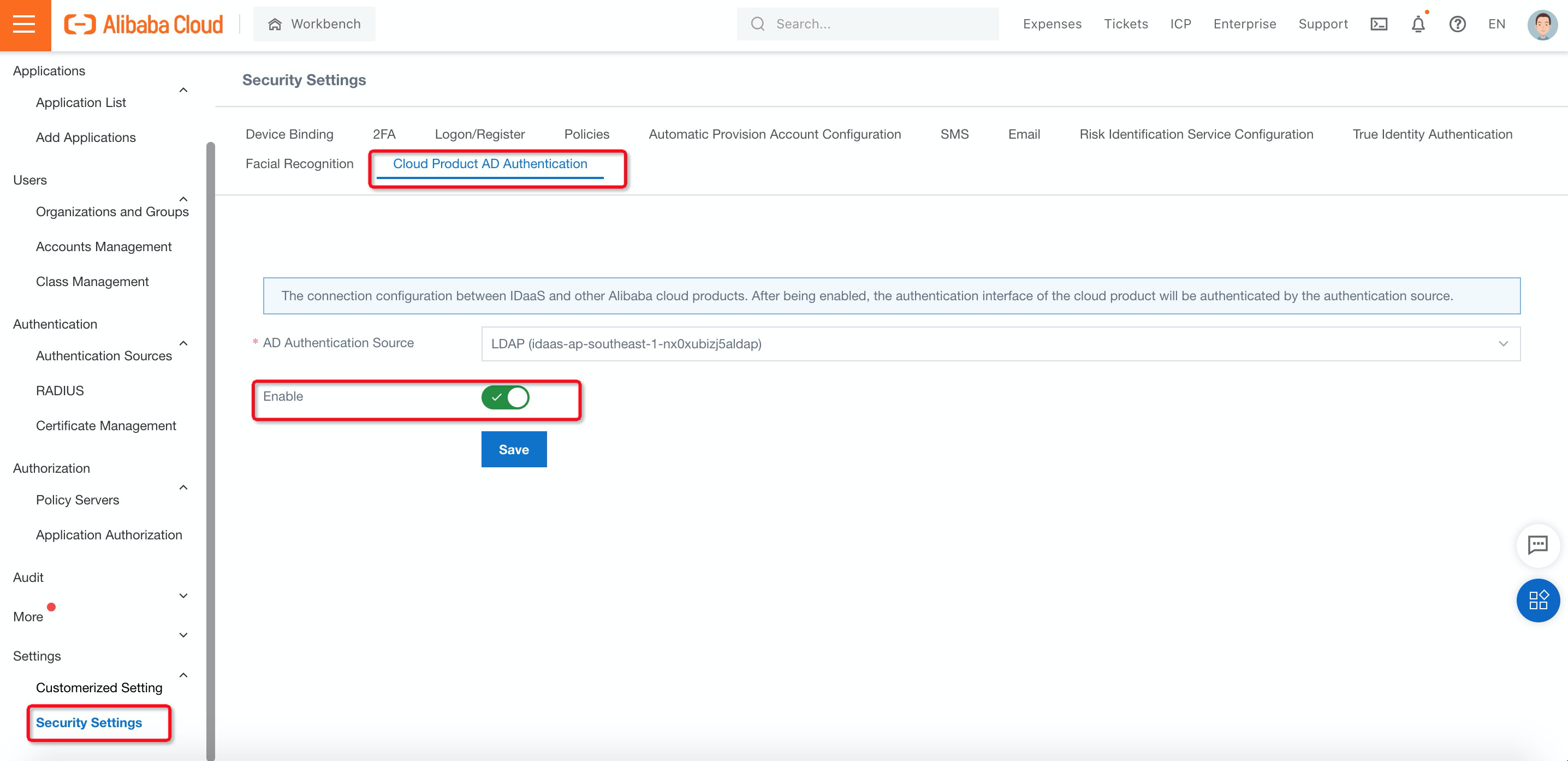
8. Navigate to Organizations and Groups under Users, click Configure LDAP and Create on the right side to configure the LDAP settings:
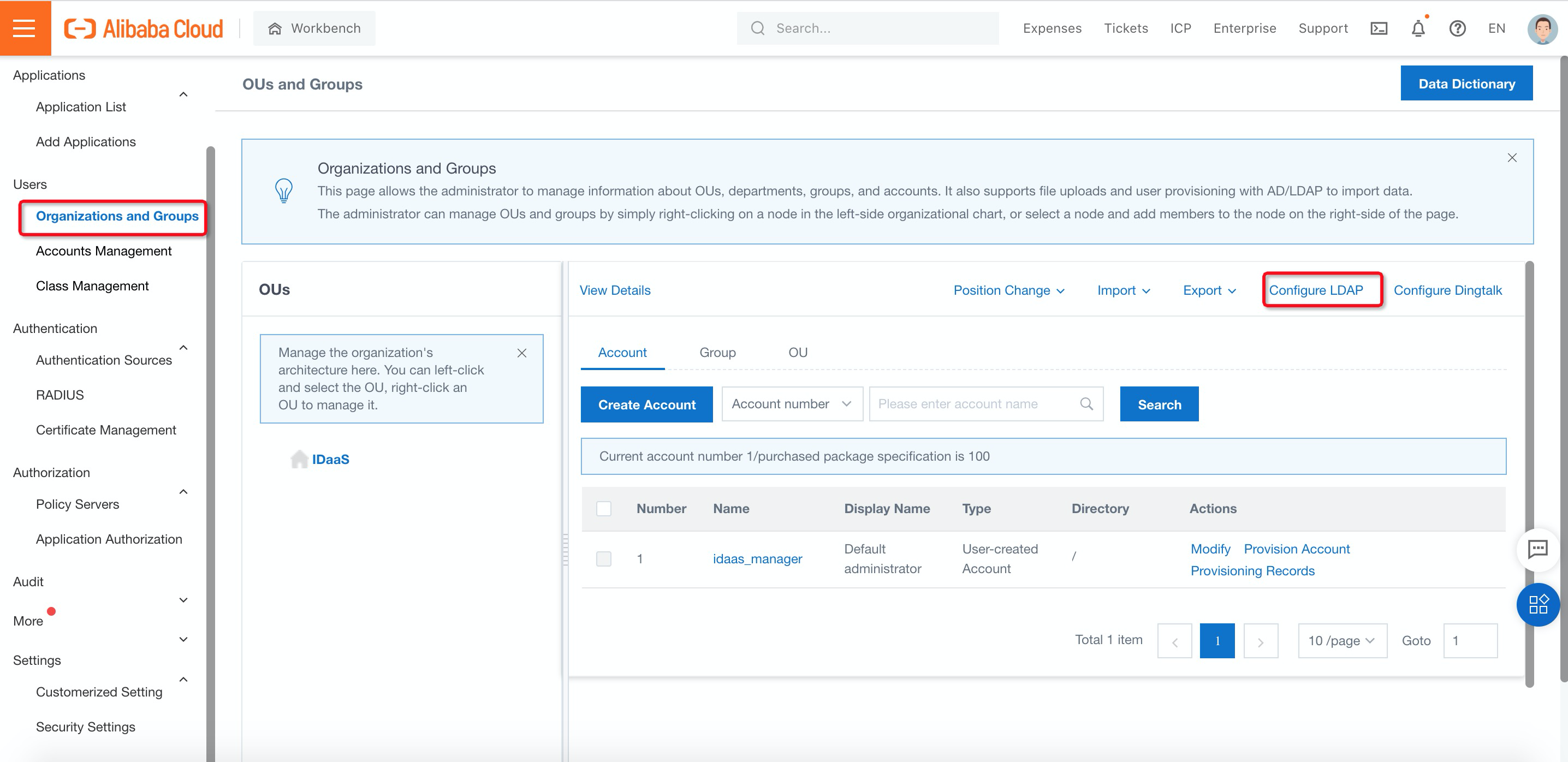
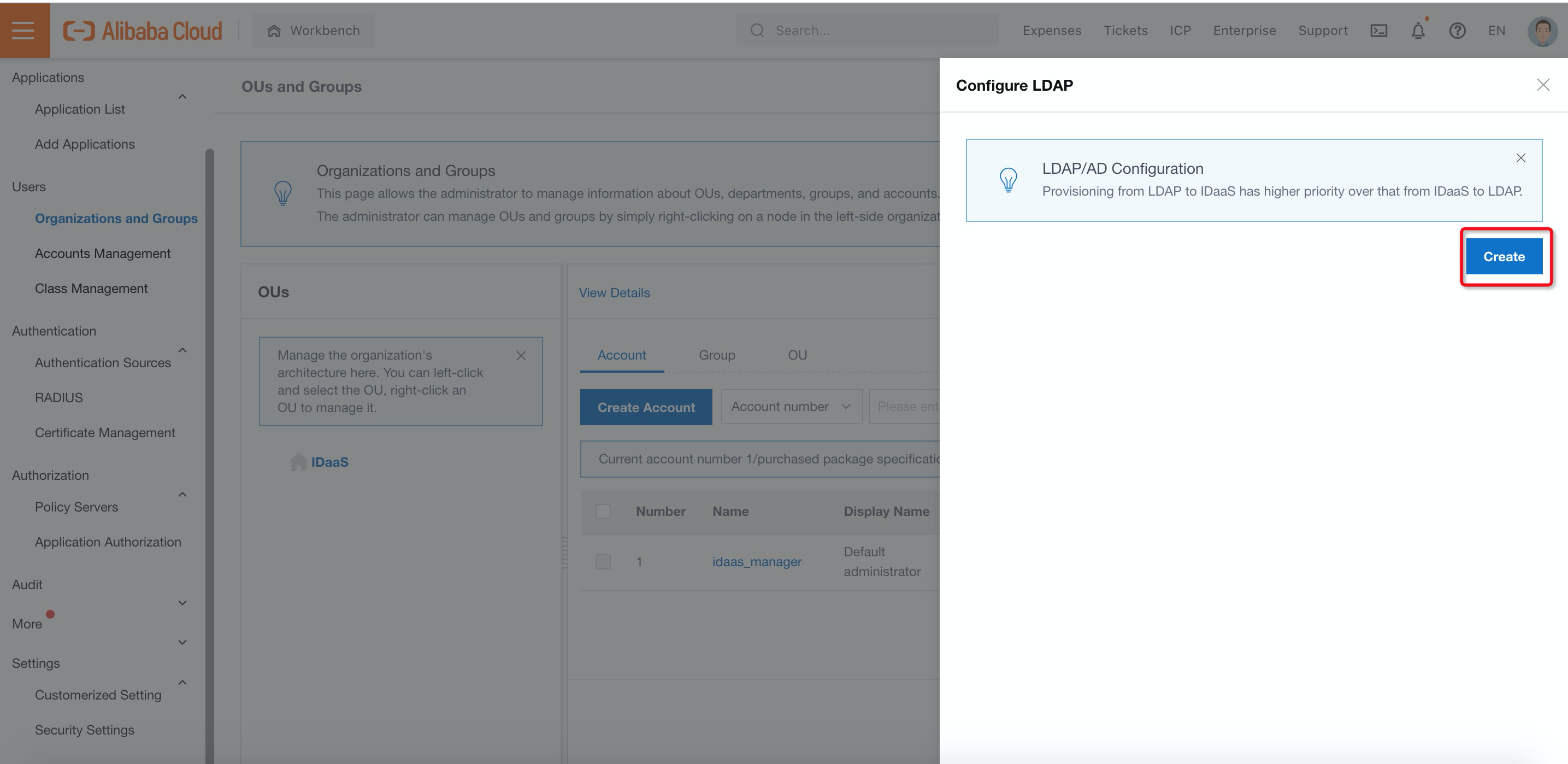
9. Fill in the LDAP server information on the Server Connection sheet:
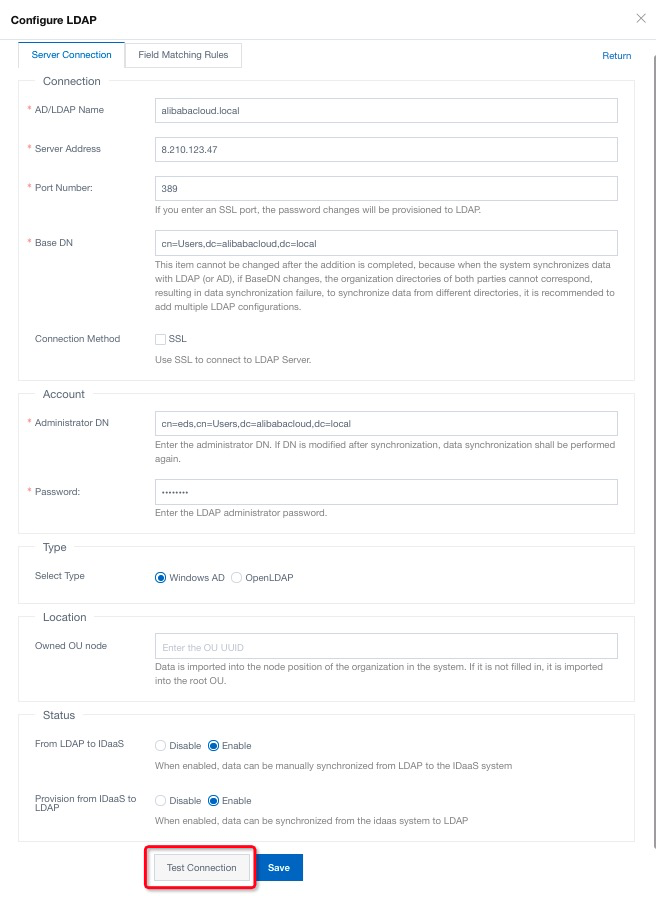
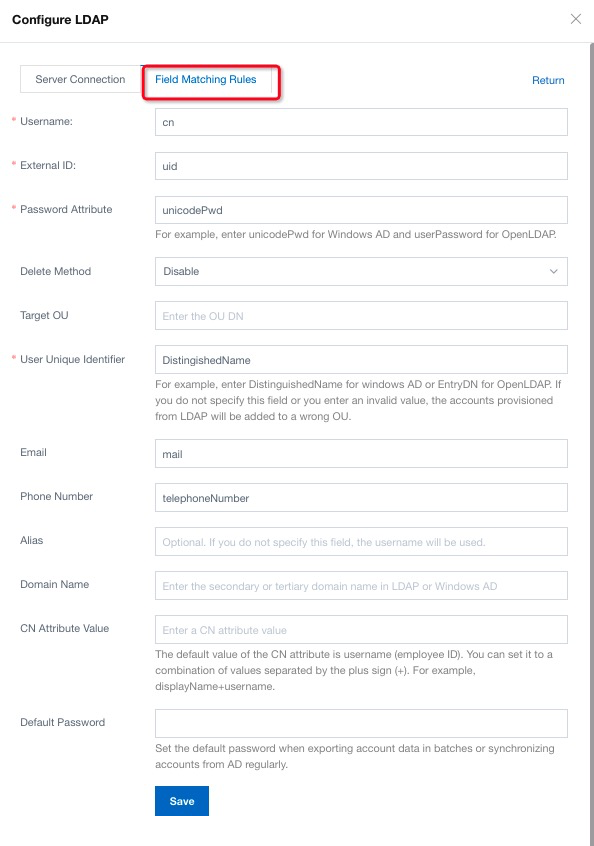
10. Switch to Field Matching Rules, follow the instruction, fill in the necessary information, and click Save. There is configure sample below:
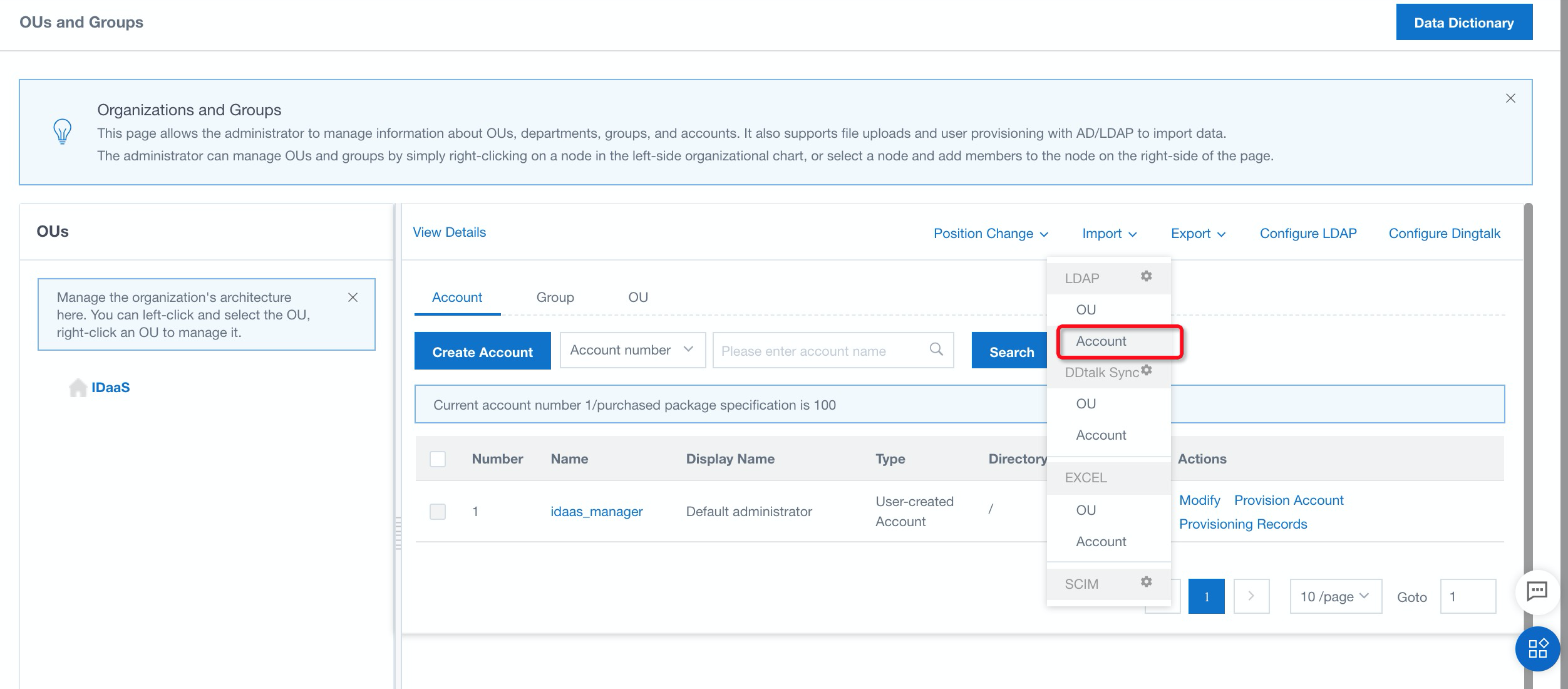
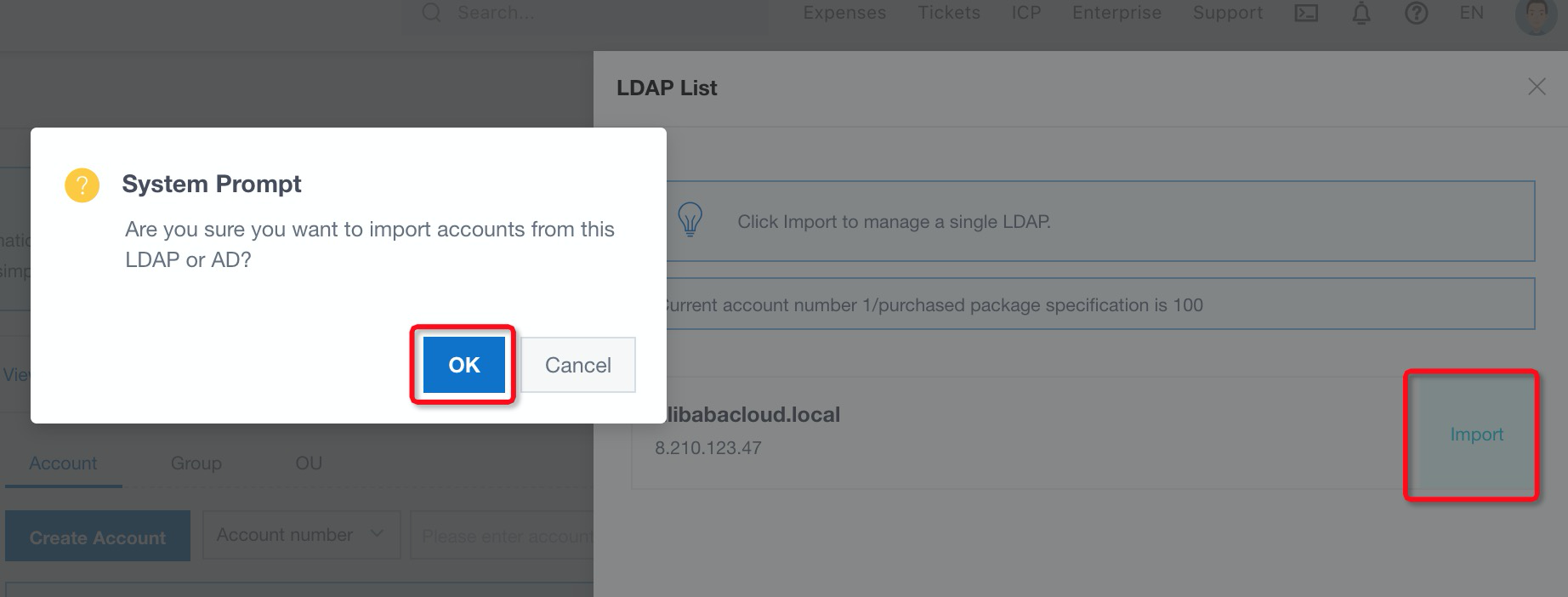
11. Navigate to Account under Import. Then, click import and OK to import account to iDaaS:
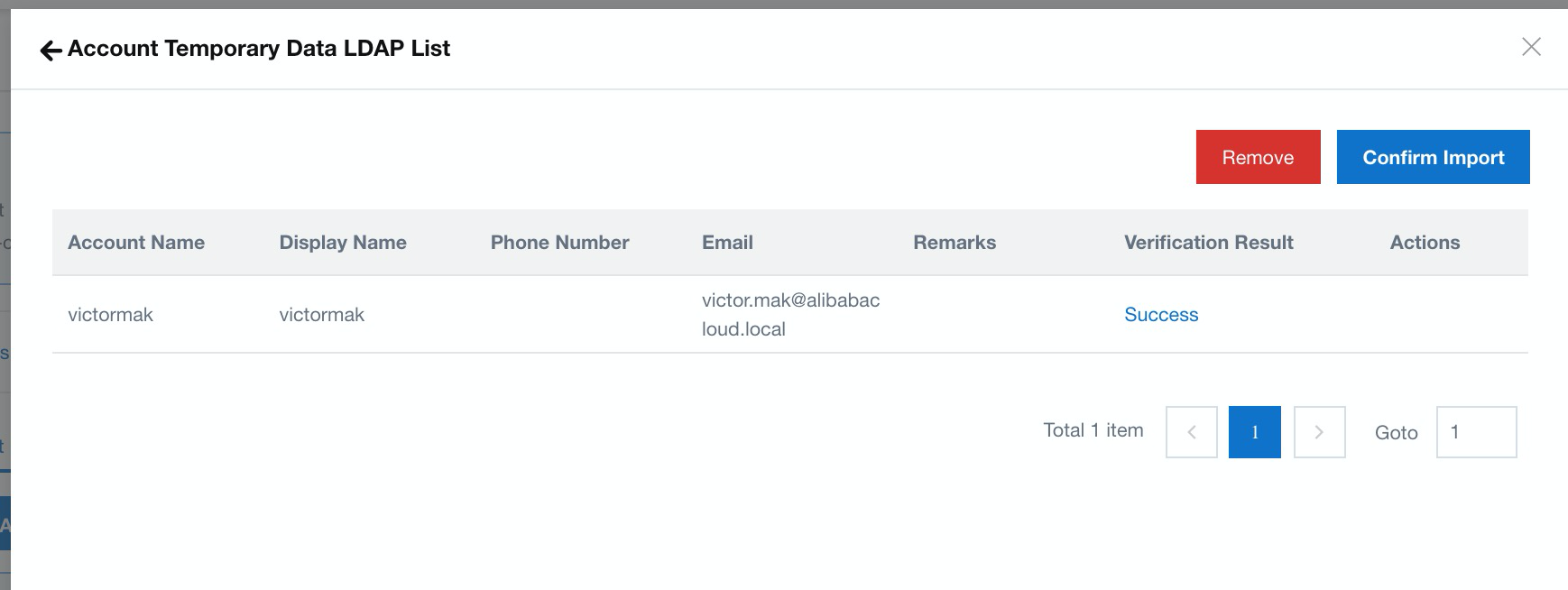
12. The lists of accounts are ready to import to iDaaS; select Confirm Import. Now, you have done all the iDaaS configuration. You are ready to integrate with the VPN gateway on 2FA authorization.
13. Log on to the Alibaba Cloud VPN Gateway console and click Create VPN Gateway:
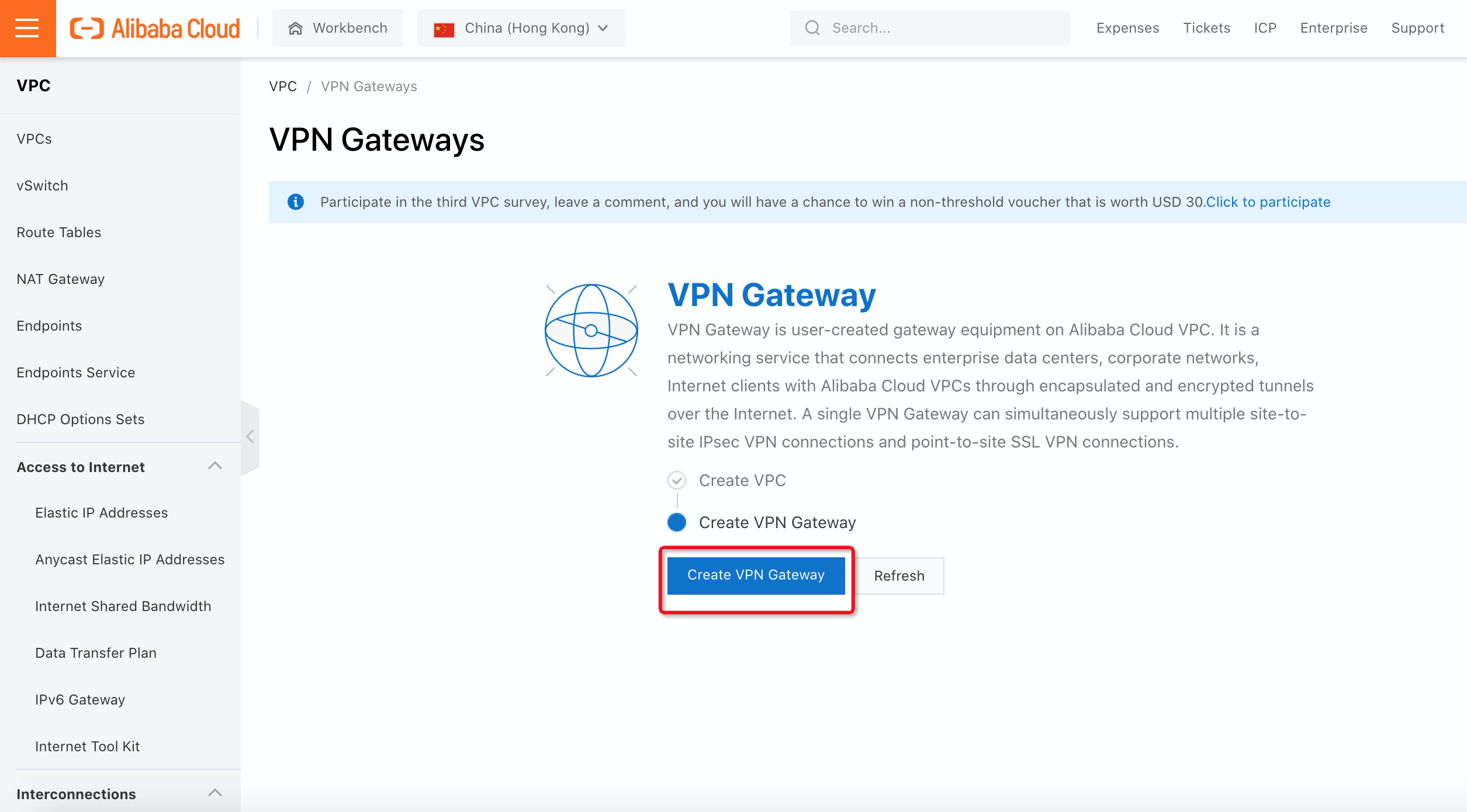
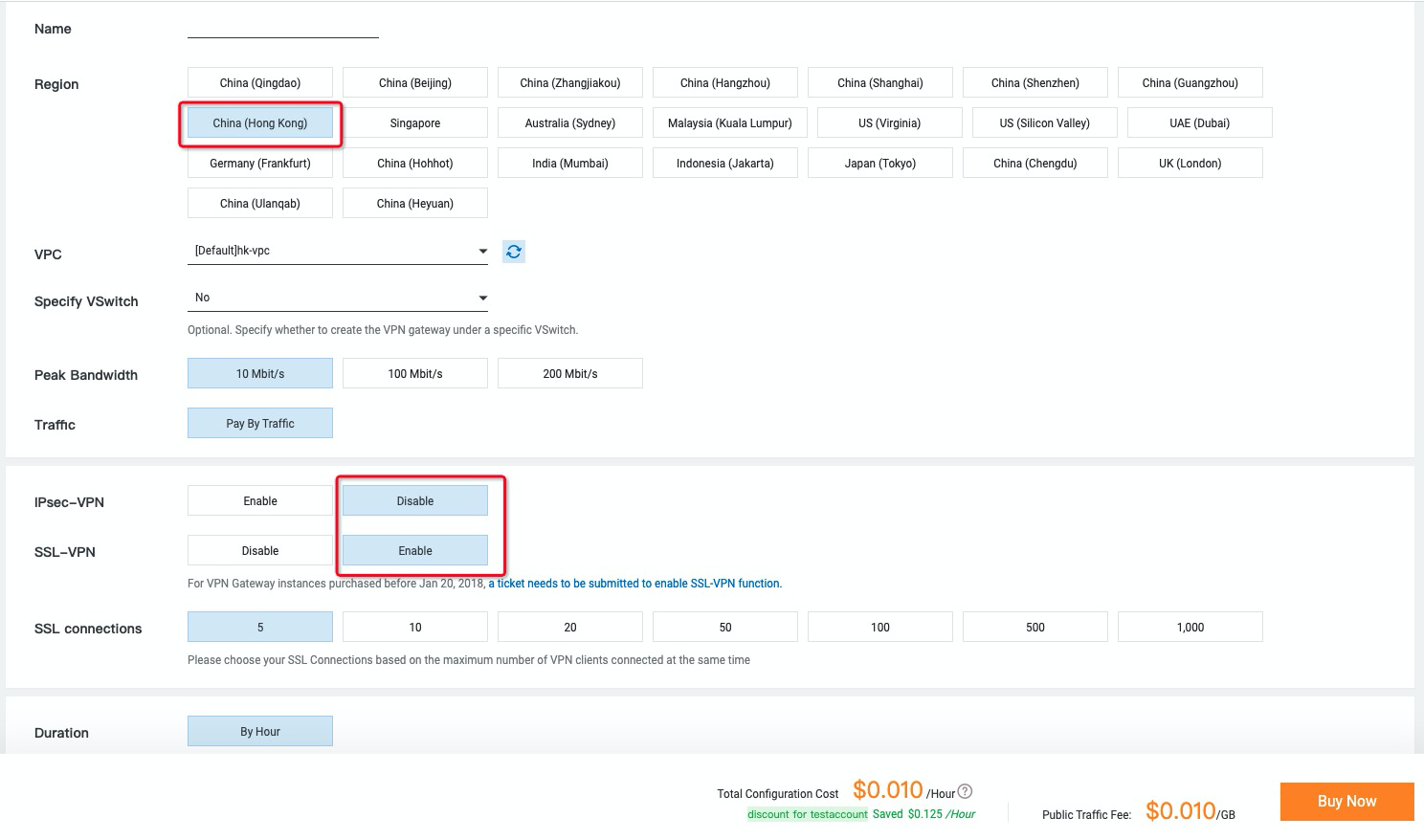
14. Select the Region, VPC, and vSwitch that you want the VPN Gateway to create. Make sure SSL-VPN Enable is selected and click Buy Now:
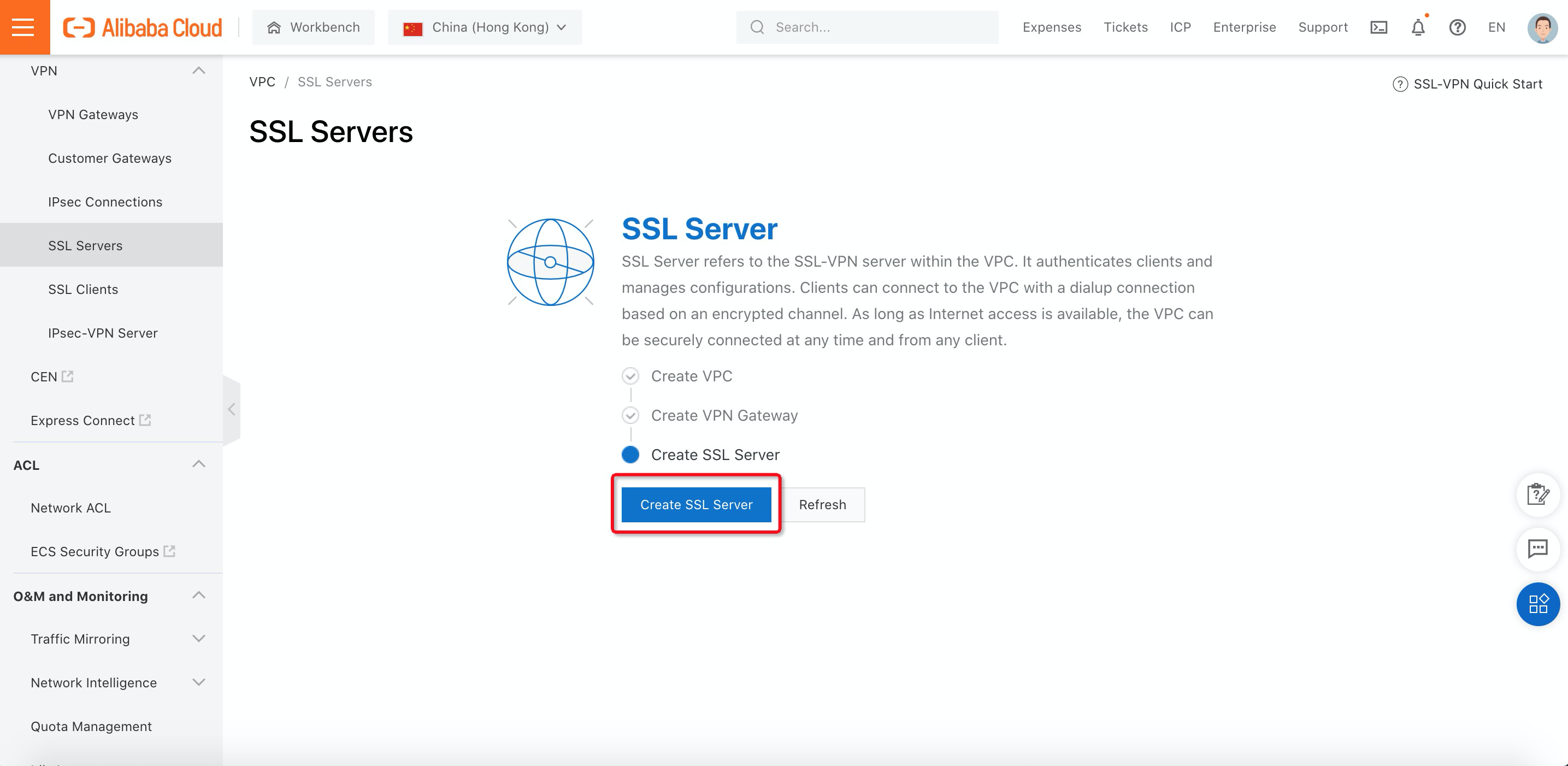
15. Navigate to SSL Servers and click Create SSL Server:
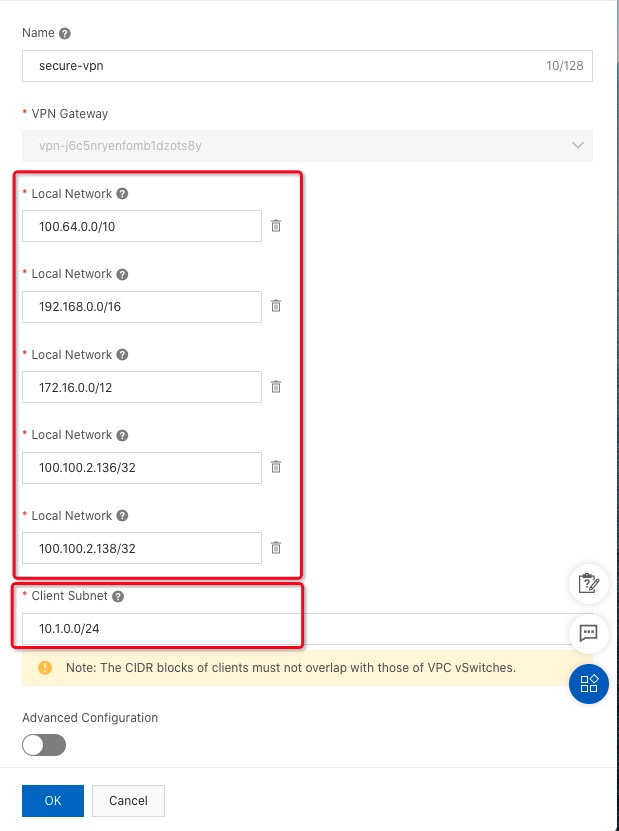
16. Fill in the value of the SSL Server name, VPN Gateway, Local Network, and Client Subnet. Then, enable Advanced Configuration. Here is the explanation for Local Network:
17. Select Advanced Configuration. Enable Two-factor Authentication and select IDaaS Instance:
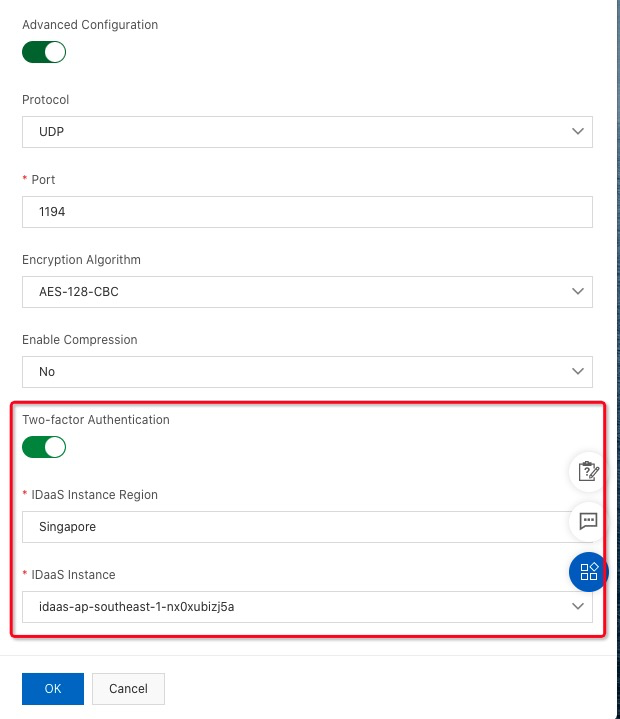
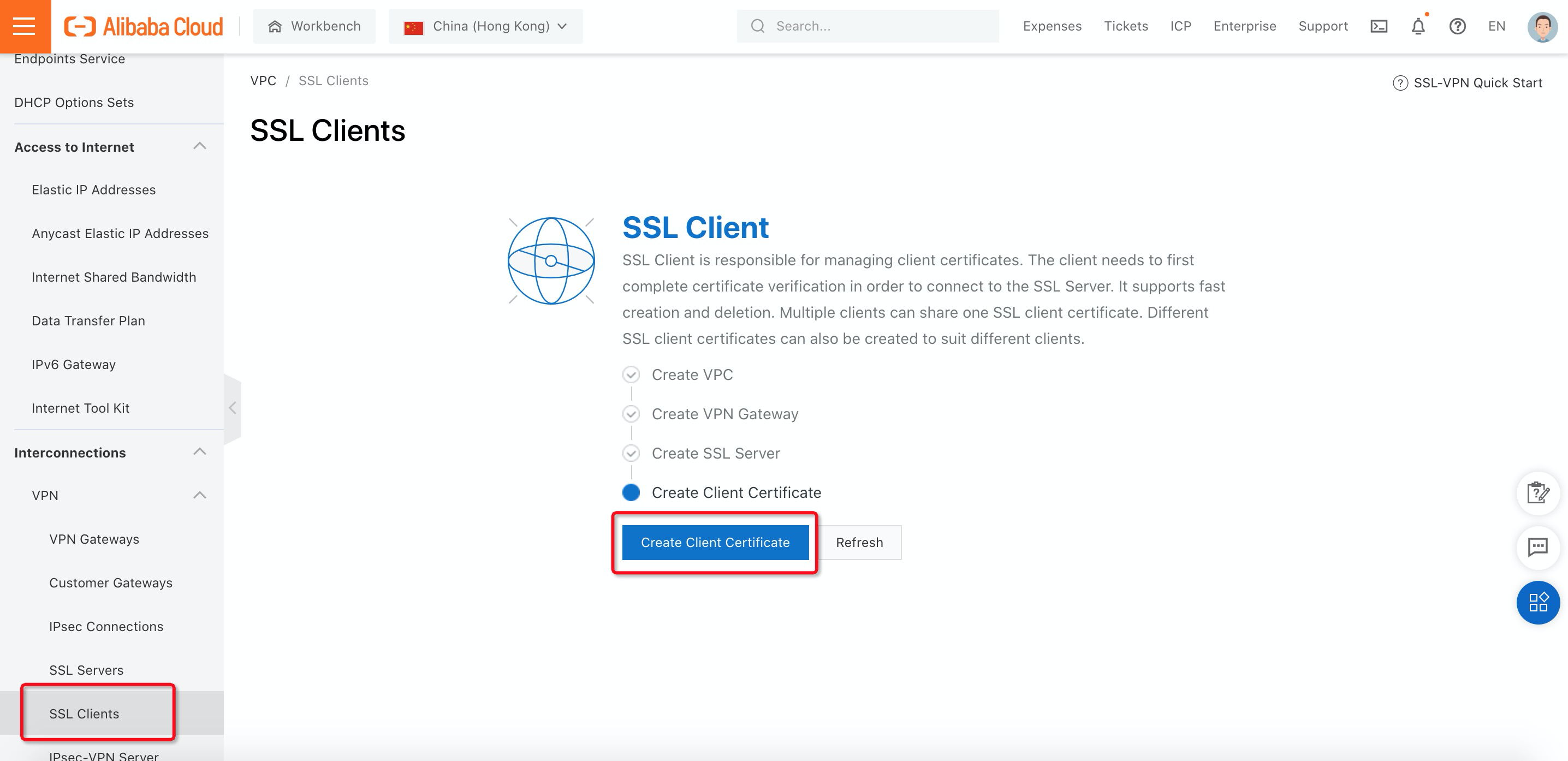
18. Navigate to SSL Clients under VPN and click Create Client Certificate:
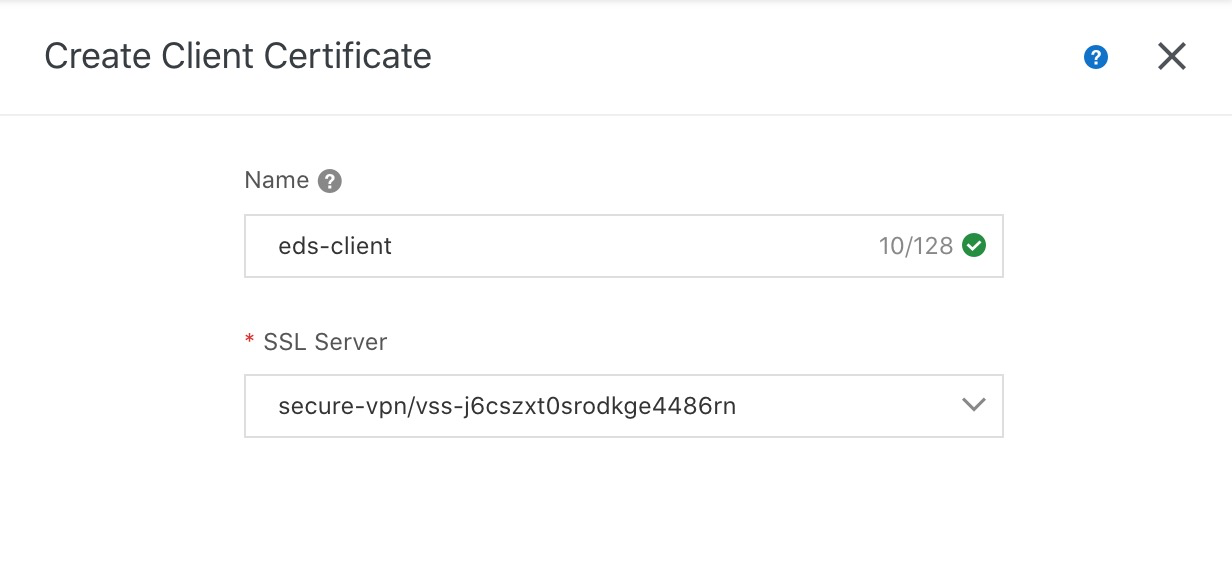
19. Fill in the Name and select SSL Server. Then, click OK.
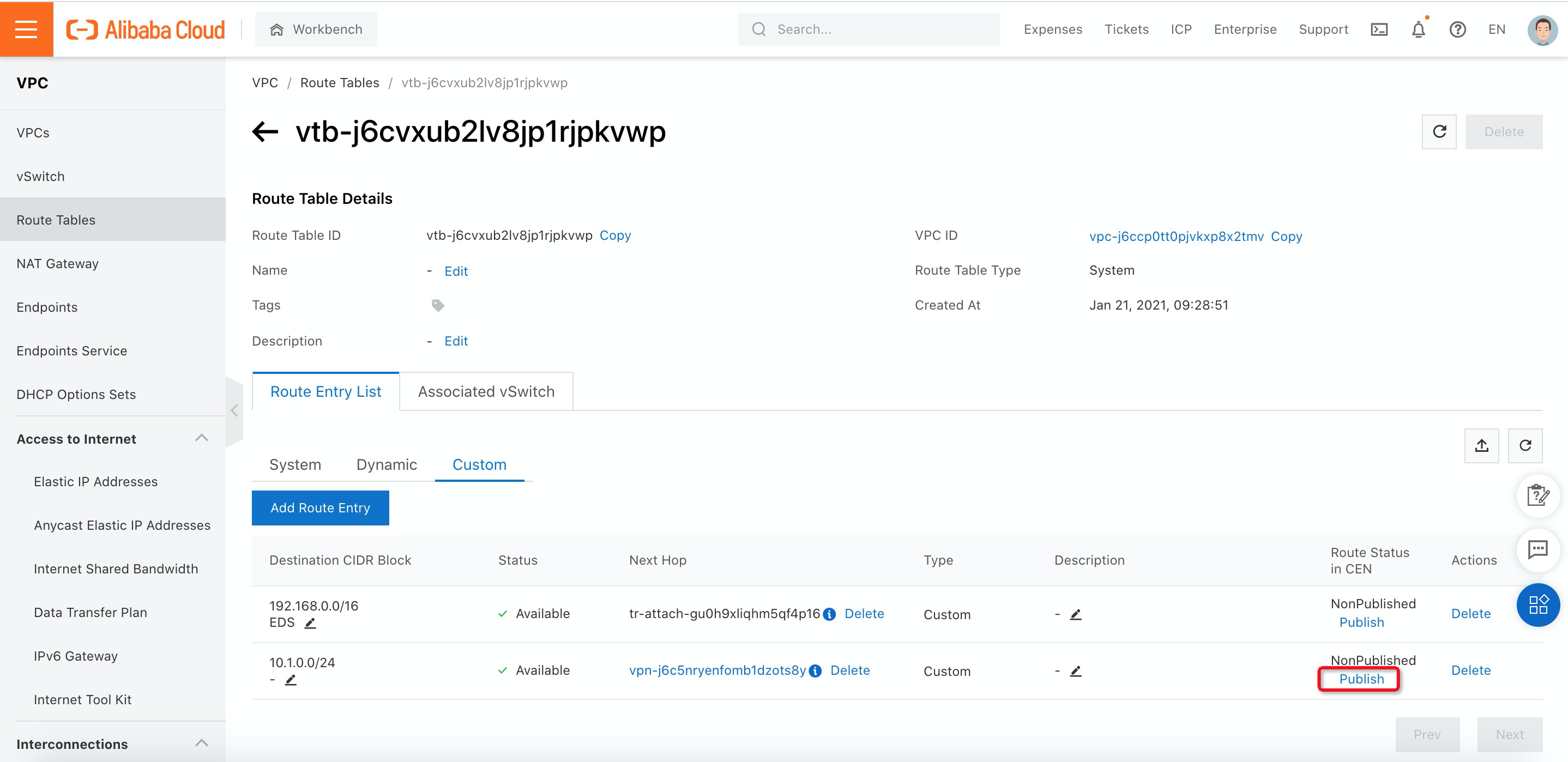
20. Since the subnet 10.1.0.0/24 will be used for the SSLVPN client, you need to publish this route to Cloud Enterprise Network (CEN) by navigating to Route Tables under VPC. Then, click Publish.
21. You have completed all the configurations! You are ready to verify the result.
1. Download the Client Certificate from SSL Clients you created:
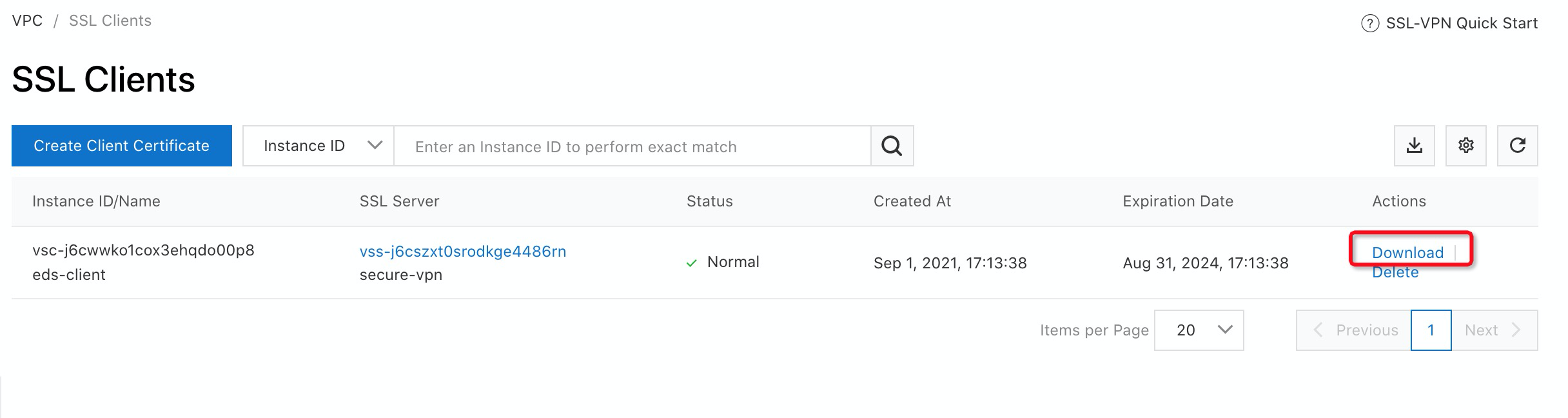
2. Depending on which operating system you are using, you need to download and install VPN software that supports the OpenVPN protocol. Since Cloud Desktop needs to communicate with gateway via domain name, you need to modify the .ovpn file and add DNS options that redirect to Alibaba Cloud Internal DNS (100.100.2.136 and 100.100.2.138).
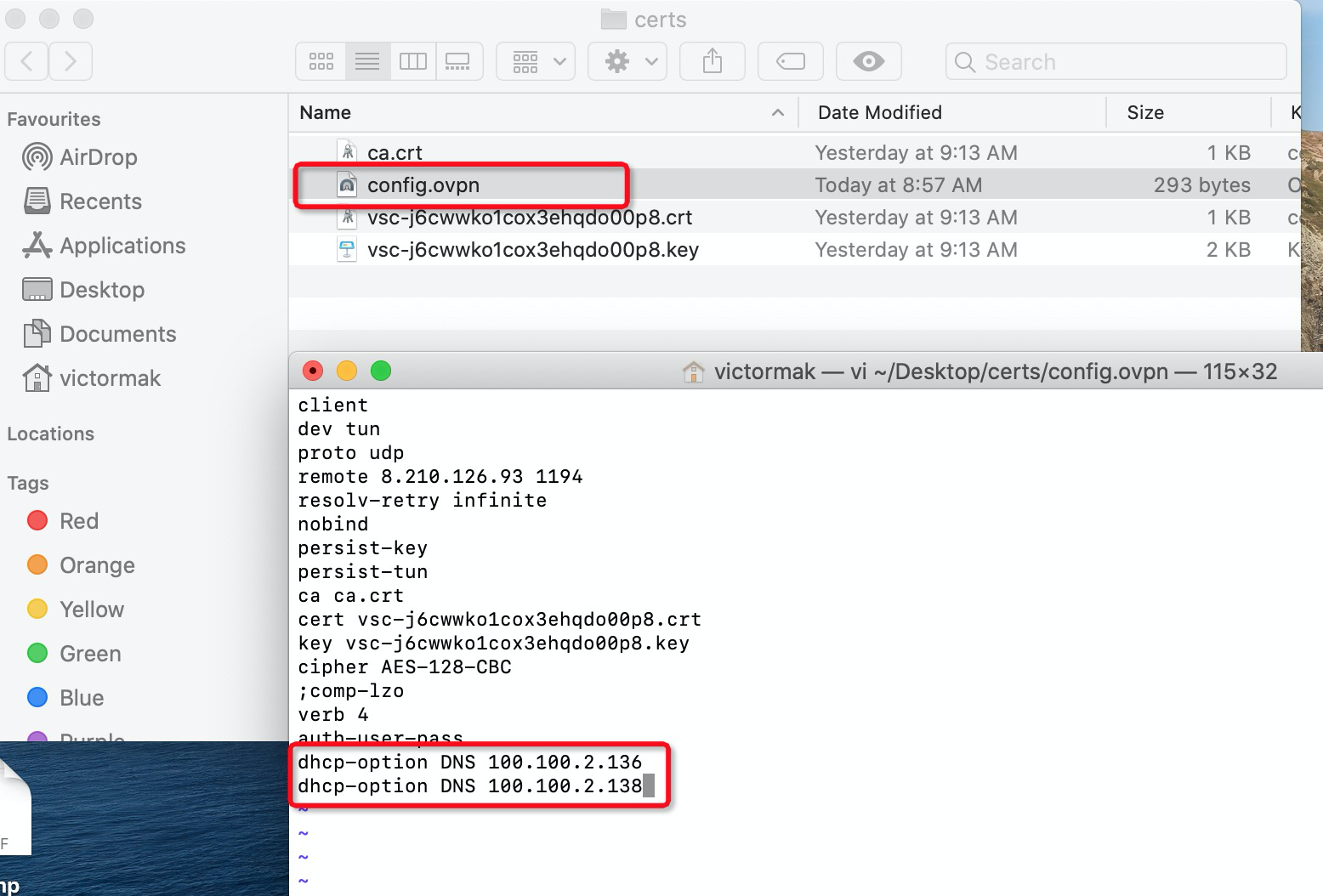
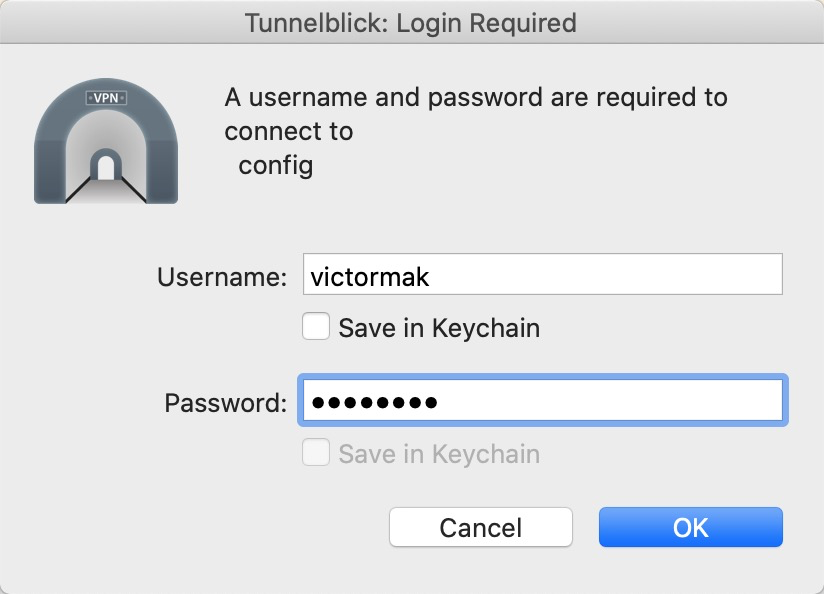
3. Double-check the .ovpn file to connect to Alibaba Cloud VPN Gateway. The VPN software will require you to log in before it establishes the VPN connection. Fill in the Active Directory username and password and click OK:
4. Download and install Cloud Desktop Soft Terminal from the EDS console:
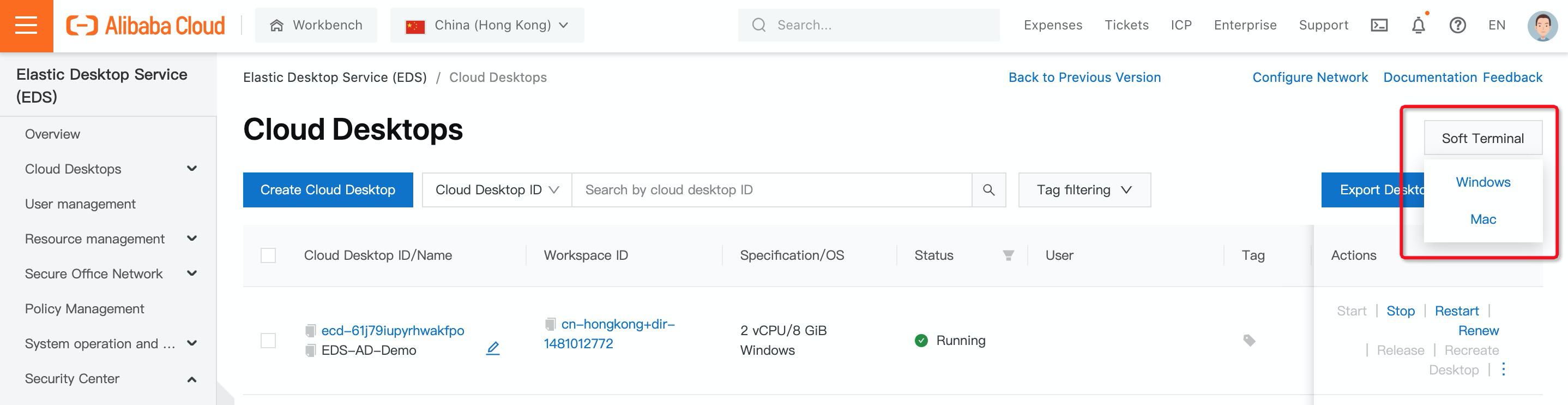
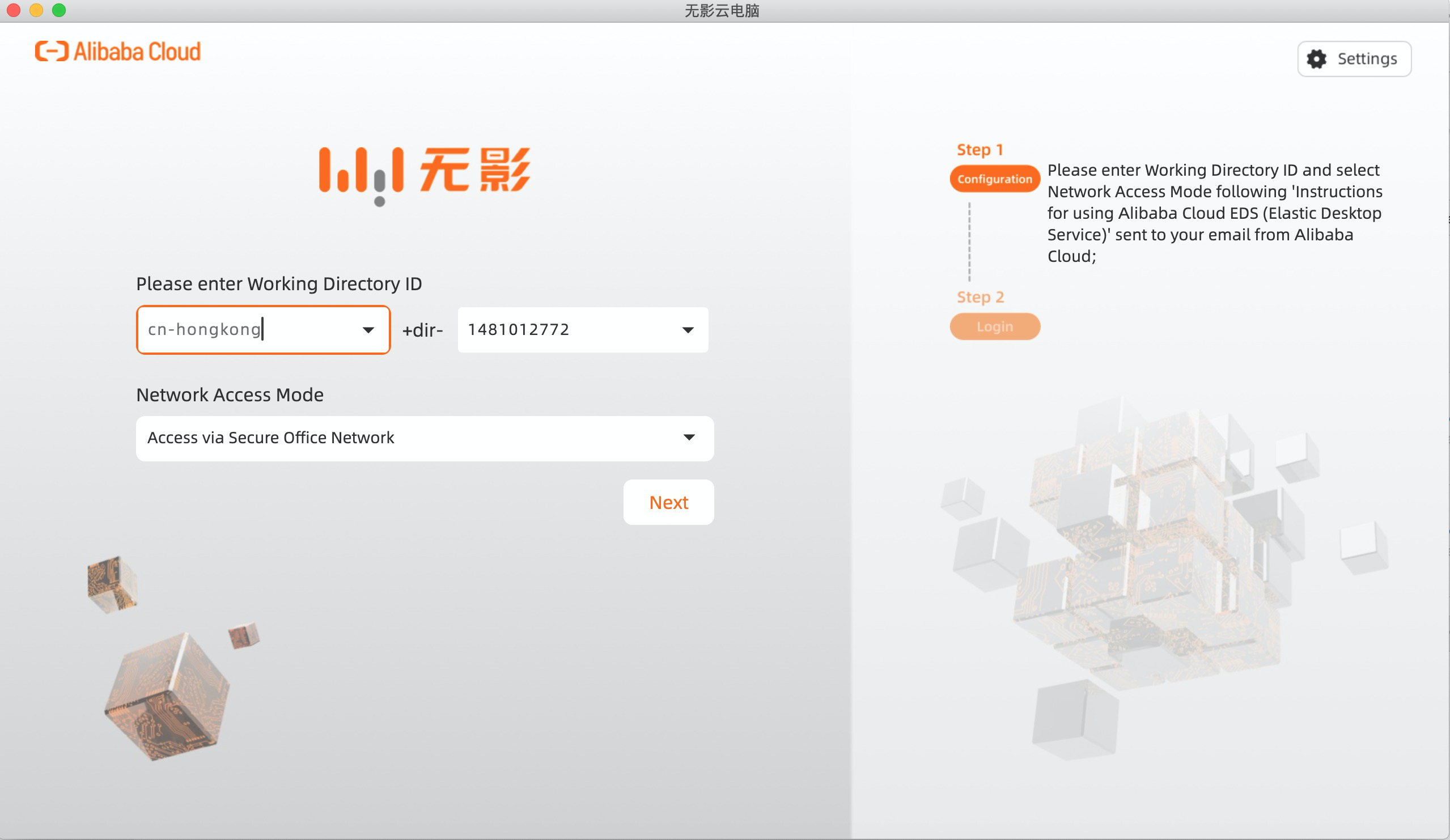
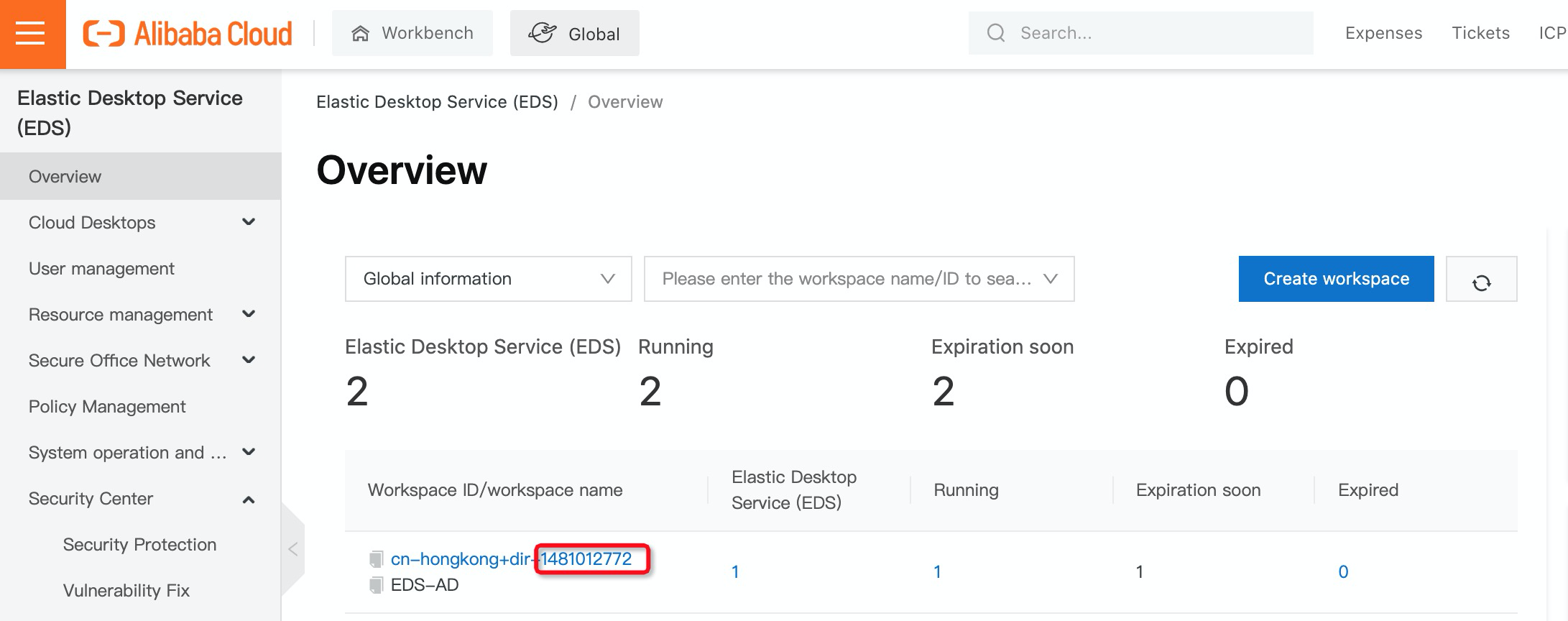
5. Once installed, you can connect to Cloud Desktop via a soft terminal. Now, select region and input working directory ID. You can find the working directory ID in the Cloud Desktop console:
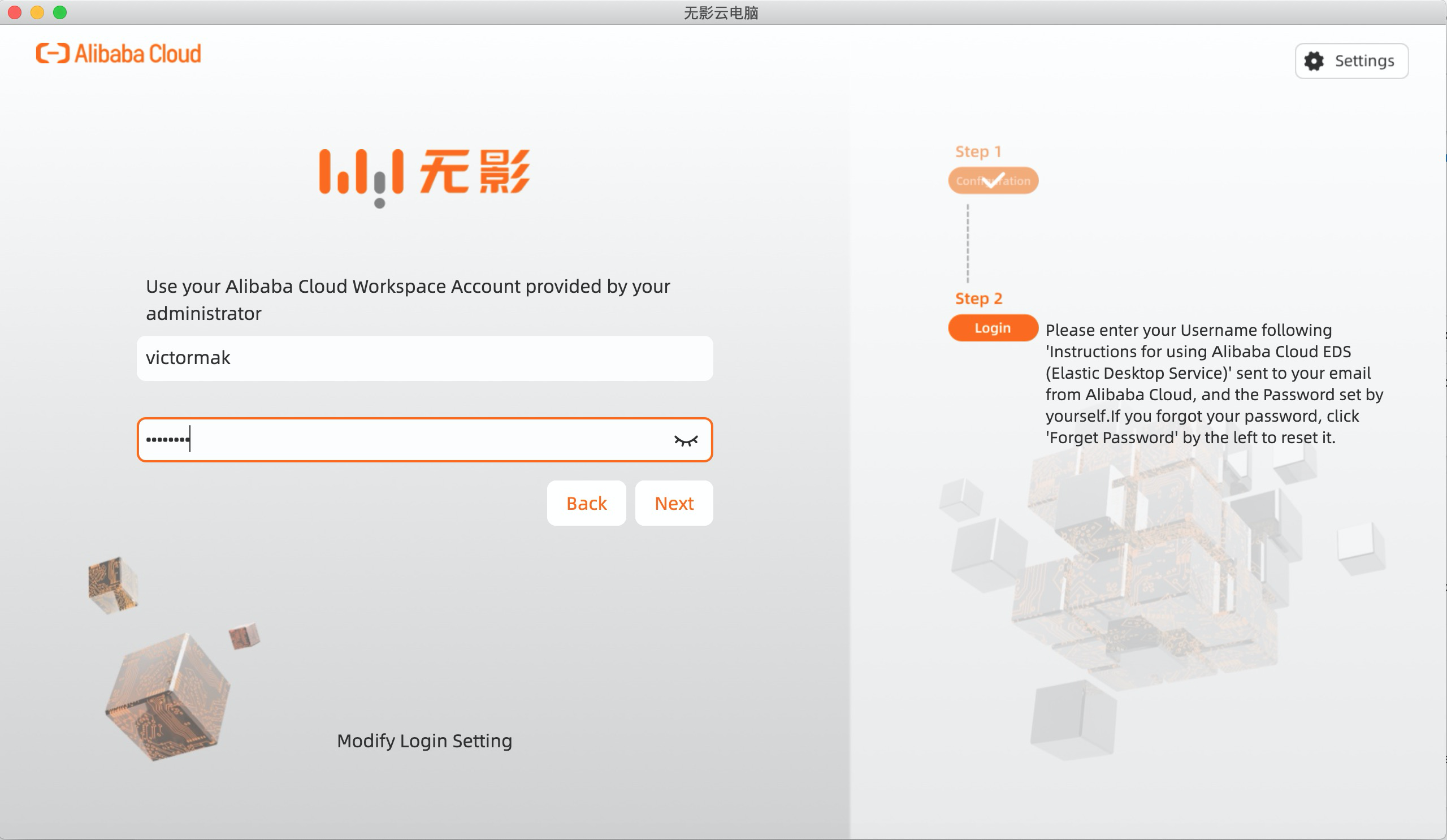
6. Use your Active Directory Account and Password to log in to Cloud Desktop:
7. Click Connect to log in to Cloud Desktop:
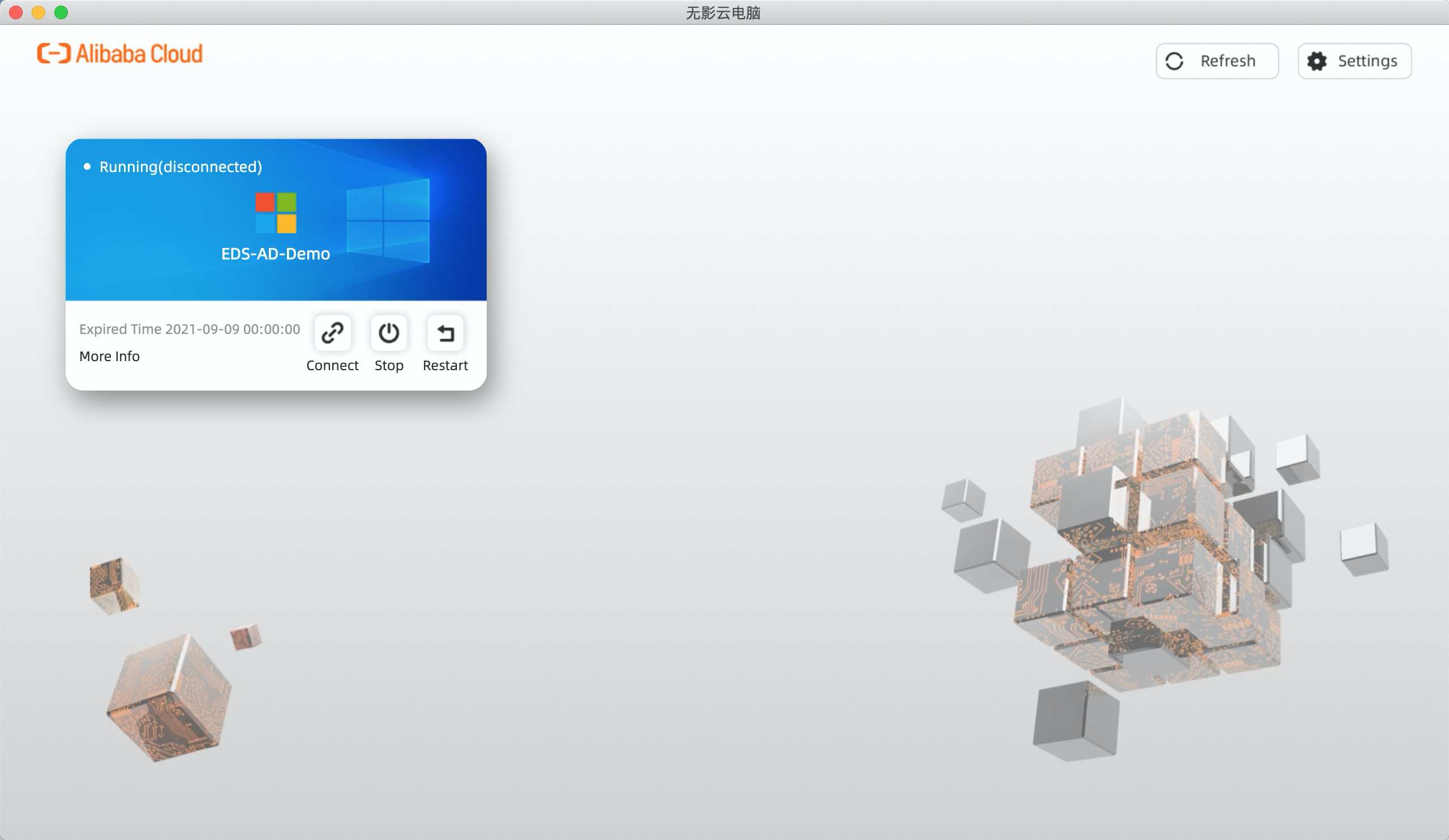
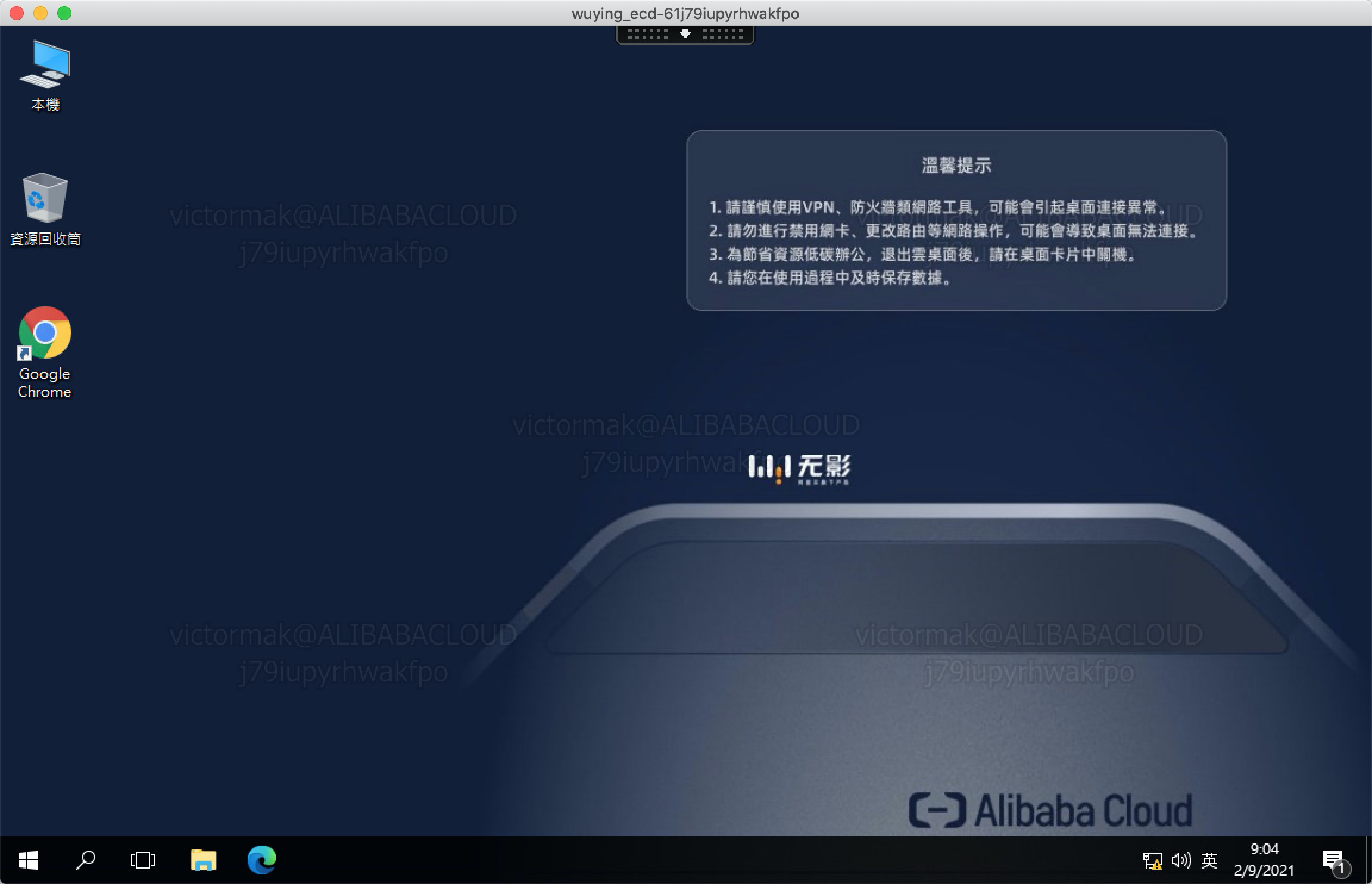
8. You are now logged on to Cloud Desktop via a secure network and applied secure policies, such as watermark:
What Is IaC? What Is the Relationship between IaC and DevOps? How Is IaC Implemented?

1,347 posts | 478 followers
FollowDikky Ryan Pratama - May 25, 2023
Alibaba Cloud Workspace - August 26, 2024
Alibaba Cloud Community - June 27, 2023
Alibaba Cloud Workspace - August 16, 2024
Alibaba Cloud Workspace - September 2, 2024
Alibaba Cloud Community - September 9, 2021

1,347 posts | 478 followers
Follow Accelerated Global Networking Solution for Distance Learning
Accelerated Global Networking Solution for Distance Learning
Alibaba Cloud offers an accelerated global networking solution that makes distance learning just the same as in-class teaching.
Learn More Networking Overview
Networking Overview
Connect your business globally with our stable network anytime anywhere.
Learn More CEN
CEN
A global network for rapidly building a distributed business system and hybrid cloud to help users create a network with enterprise level-scalability and the communication capabilities of a cloud network
Learn More Security Center
Security Center
A unified security management system that identifies, analyzes, and notifies you of security threats in real time
Learn MoreMore Posts by Alibaba Cloud Community